A brand new report for cybersecurity agency WithSecure suggests that almost all firms are investing in safety options which might be tactical and reactive, however not according to strategic goals of a corporation.

A brand new report by cybersecurity agency WithSecure, based mostly on a survey of greater than 400 international cybersecurity and IT decision-makers performed by Forrester Consulting, means that many organizations are reactive of their strategy to defending towards threats, and piecemeal in the case of cybersecurity investments.
The outcome? Safety targets change into indifferent from enterprise targets, leading to organizations investing in defenses towards threats that aren’t related to their enterprise or targets.
End result-based safety versus reactive safety
In line with Forrester, an outcome-based safety helps enterprise targets somewhat than merely reacting to perceived vulnerabilities. It permits enterprise leaders to simplify cybersecurity by “Cultivating solely these capabilities that measurably ship their desired outcomes versus conventional menace, activity-based, or ROI-based strategies,” mentioned WithSecure’s report.
The report mentioned a extra holistic strategy to cybersecurity ought to attempt for outcomes associated to danger administration, buyer expertise, resilience, and visibility of the menace floor and dangers. The outcomes must also pertain to expertise, sources and response velocity and agility (Determine A).
Determine A
Paul Brucciani, cybersecurity adviser and head of product advertising for options at WithSecure, mentioned that the idea of outcome-based cybersecurity constitutes each a strategy to make cybersecurity executions align with enterprise targets, and to scale back litter and redundancy of safety options and techniques. This can be a Marie Kondo-esque effort to throw objects on the ground and discard these layers of management that don’t strategically help enterprise targets.
SEE: Companies whose targets embrace extra clouds ought to count on rain.
“End result based mostly safety is a strategy to make choices about what you might want to defend and the way. However it’s a self-discipline: it’s very straightforward to purchase and implement a brand new instrument, rather more troublesome to modify off legacy methods. To show issues off [that aren’t useful],” Brucciani mentioned.
Although 83% of respondents to the survey mentioned they had been desirous about, planning to undertake, or increasing their adoption of outcome-based safety options and providers, 60% mentioned their organizations are reactive, not proactive; they reply to particular person cybersecurity issues as they come up.
One-fifth of firms align cybersecurity with enterprise priorities
The research, which aimed to know organizational cybersecurity priorities and enterprise targets, discovered:
- Solely 20% of respondents mentioned their group has full alignment between cybersecurity priorities and enterprise outcomes.
- 75% of respondents mentioned cyber-risk administration is receiving elevated consideration from the board of their organizations.
- 60% of corporations are keen to spend 6% or extra of their operational revenue to realize the advantages they see in adopting an outcome-based strategy for cybersecurity investments.
- 50% of corporations battle to measure cybersecurity worth and have hassle articulating the contribution of safety to enterprise outcomes.
‘Market of lemons’ paradigm complicates safety investments
Cybersecurity budgets are rising, however might the sheer dimension and scope of the cybersecurity service market be driving IT consumers to allocate budgets haphazardly?
SEE: In this Q&A, an IT professional and advisor talks about tips on how to prioritize safety in budgets.
Brucciani mentioned that is in all probability the case, as the present marketplace for cybersecurity Software program as a Service itself constitutes a “marketplace for lemons,” a time period coined by economist George Akerlof to explain a circumstance wherein the market is peppered by good and unhealthy merchandise and the client is hobbled by an incapacity to discern which is which.
“Cybersecurity is an enormous enterprise; relying on the way you outline the market there are 10,000 cybersecurity firms on the earth which creates a loud market, and lots of of these firms are enterprise capital backed, so their job is to get to market as quick as doable. As a consequence it creates a market that’s troublesome to navigate, with the added problem of measuring high quality: Patrons haven’t any manner of assessing the standard of what they’re being bought,” Brucciani mentioned.
What companies search from cybersecurity instruments and providers
Survey respondents cited a few of the greatest safety challenges: visibility into cyber dangers, discovering the required expertise and sources, and responding rapidly and successfully (Determine B).
Determine B
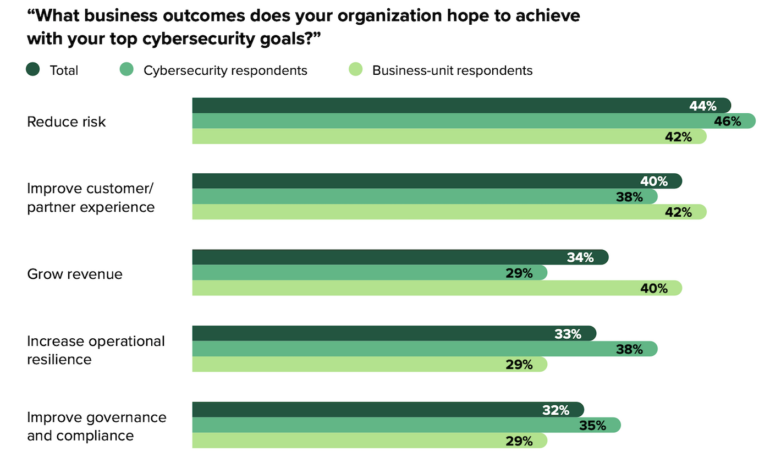
Outcomes that respondents mentioned they sought from cybersecurity efforts embrace:
- 44% of these polled need to cut back danger.
- 40% need safety to enhance buyer expertise.
- 34% need safety to help income development.
- 33% need to improve operational resilience.
- 32% need safety to be aimed toward governance and compliance.
Getting significant metrics tying safety to enterprise outcomes is one other problem
The executives polled by Forrester listed challenges to extracting helpful metrics that tie safety priorities to enterprise outcomes:
- 37% expressed difficulties in measuring cybersecurity worth.
- 36% mentioned they may not seize constant and significant knowledge.
- 28% discovered challenges in overcoming a paradox: funding in efficient safety leads to fewer alternatives to display worth.
- 23% encountered challenges in translating cybersecurity metrics into one thing significant to the board.
Moreover, 42% mentioned they’d an inadequate understanding of present and target-state maturity towards which safety worth ought to be assessed. Brucciani defined that focus on state, in a safety context, is an expression of an enterprise’s safety targets and will depend on such components as:
- Impression of a cyber safety assault on the enterprise.
- Threat tolerance — the affect an enterprise can soak up and performance.
- Willingness to take safety dangers.
- Safety that regulators and purchasers count on.
“Usually companies need a increased degree of safety than they’ve at current,” mentioned Brucciani. “The query is, how a lot safety is sufficient? Their cyber danger technique — whether it is coherent — will likely be pushed by these components.” He added that NIST provides a helpful framework to help safety decision-making.
Learn how to construct enterprise outcomes into safety
The research included suggestions on tips on how to convey cybersecurity investments into strategic alignment with enterprise targets:
- Enterprise outcomes ought to be agreed on with stakeholders and mapped to your safety investments, menace mannequin, and safety controls.
- Safety outcomes ought to embrace enterprise advantages (e.g. risk-based authentication in e-commerce improves CX by eliminating additional steps and friction from low-risk transactions).
- Safety priorities ought to correlate to enterprise outcomes, avoiding pointless investments in safety that enterprise outcomes don’t require.
- Procurement and authorized groups ought to be ready for outcome-based safety buying.


