
ConnectWise has launched safety updates to deal with a important vulnerability within the ConnectWise Get better and R1Soft Server Backup Supervisor (SBM) safe backup options.
The safety flaw is because of an injection weak point described by the corporate in an advisory issued right this moment as “Improper Neutralization of Particular Parts in Output Utilized by a Downstream Part.”
Affected software program variations embrace ConnectWise Get better or earlier and R1Soft SBM v6.16.3 or earlier.
Connectwise added that this can be a important severity vulnerability that would allow attackers to entry confidential information or execute code remotely.
It additionally tagged it as a high-priority concern, as a flaw that is both exploited in assaults or at a excessive danger of being focused within the wild.
Found by Code White safety researcher Florian Hauser and expanded by Huntress Labs safety researchers John Hammond and Caleb Stewart, the vulnerability can be utilized to “push ransomware” by means of hundreds of R1Soft servers uncovered on the Web, in keeping with Huntress Labs CEO Kyle Hanslovan.
In line with a Shodan scan, greater than 4,800 Web-exposed R1Soft servers are possible uncovered to assaults in the event that they have not been patched since ConnectWise has launched patches for this RCE bug.
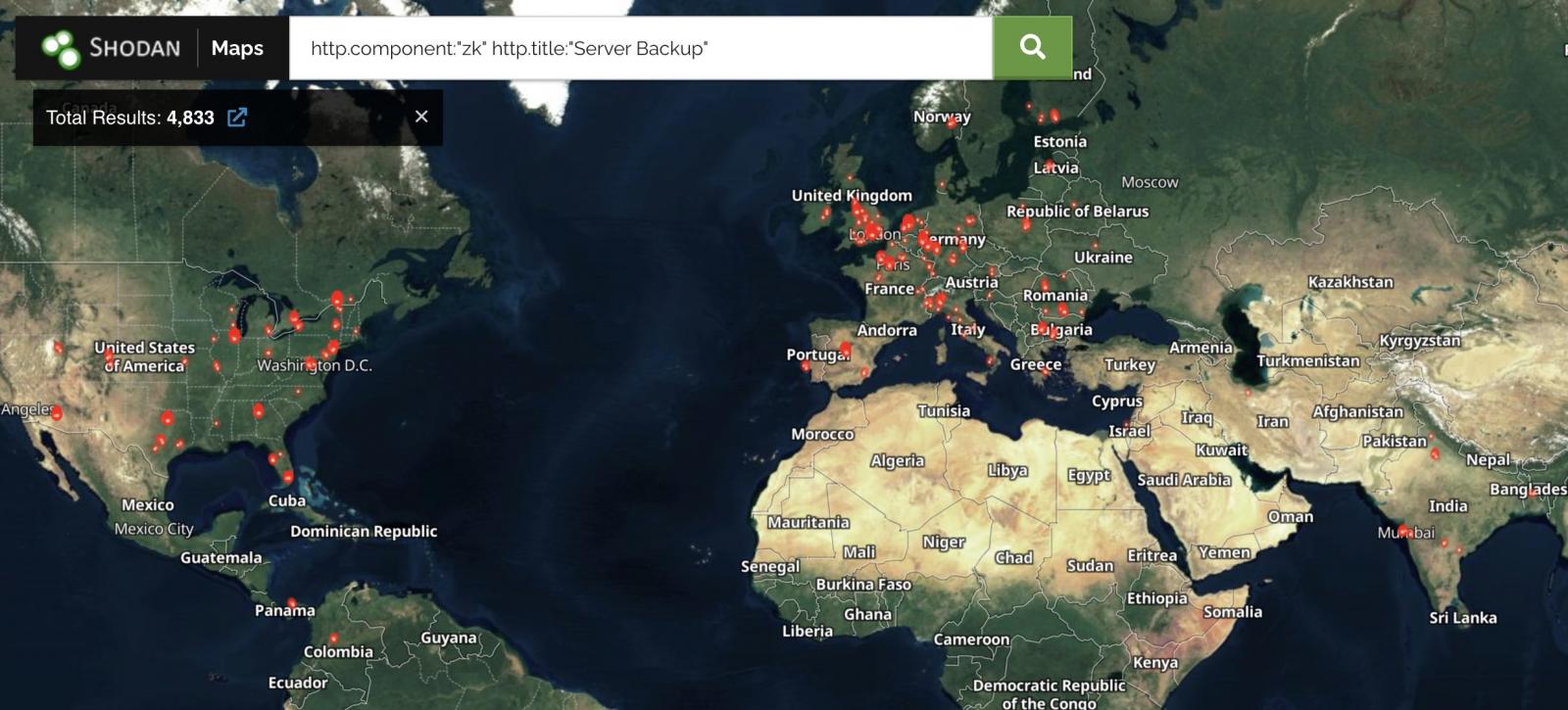
”Affected ConnectWise Get better SBMs have mechanically been up to date to the newest model of Get better (v2.9.9),” ConnectWise stated.
However, R1Soft customers had been suggested to “improve the server backup supervisor to SBM v6.16.4 launched October 28, 2022 utilizing the R1Soft improve wiki.”
The corporate additionally really helpful patching all impacted R1Soft backup servers as quickly as doable.
Whereas patching important vulnerabilities is at all times commendable, doing it on the finish of the week, on a Friday night, is unlucky, if not harmful, timing.
It’s because risk actors will leap on the event to develop exploits and compromise any Web-exposed servers left unpatched.
Weekends are additionally when attackers are essentially the most lively, given that almost all IT and safety groups aren’t round to detect and cease their malicious actions.
The patch simply dropped so I’d guess nearly all of them are nonetheless susceptible. I don’t consider there’s any auto-updating performance.
— Kyle Hanslovan (@KyleHanslovan) October 28, 2022
An end-of-the-week launch additionally makes it more durable to patch any susceptible servers earlier than the weekend, exposing extra programs to assault for a minimum of just a few days.
To prime all of it off, the R1Soft SBM backup answer is a well-liked device amongst managed service suppliers and cloud internet hosting suppliers.
An MSP’s R1Soft compromised server might result in a safety incident with a large affect, making ConnectWise’s timing much more unlucky.

