Within the final 20 years, community site visitors has elevated greater than 100-fold. Consequently, detecting at this time’s most regarding cyber assaults, reminiscent of phishing, drive-by downloads, and ransomware, from that big stream of site visitors has grow to be a lot tougher. In essence, community situational consciousness and safety have grow to be big-data issues, particularly on giant networks.
For years, safety evaluation on giant networks has relied on using community site visitors stream knowledge, reminiscent of Cisco’s NetFlow. Netflow was designed to pattern and retain an important attributes of community conversations between TCP/IP endpoints on giant networks with out having to gather, retailer, and analyze all community knowledge. The SEI launched its device for analyzing community stream data, SiLK (System for Web-Stage Data), 18 years in the past. Nonetheless, the rising quantity of community site visitors, and therefore the quantity of associated stream knowledge, has outgrown SiLK’s capability. To shut this hole, the SEI launched Mothra earlier this 12 months.
This SEI Weblog publish will introduce you to Mothra and summarize our current analysis on enhancements to Mothra designed to deal with large-scale environments. This publish additionally describes analysis aimed toward demonstrating Mothra’s effectiveness at “cloud scale” within the Amazon Net Providers (AWS) GovCloud atmosphere.
Managing the Flood of Community Circulation Information
As general community site visitors has grown, community stream data, reminiscent of Cisco NetFlow, have additionally grown. Detecting essentially the most critical community assaults requires deep packet inspection (DPI) on these community flows. The DPI course of inspects the info traversing a pc community and might alert, block, re-route, or log this knowledge as required. Nonetheless, whereas DPI extracts extra info on a stream’s security-critical elements, it additionally generates a report at the least 5 occasions larger than a non-DPI stream report.
The SEI device But One other Flowmeter (YAF) can carry out DPI, amongst different capabilities. YAF is the info assortment part of the SEI’s CERT NetSA Safety Suite. It transforms packets into community flows and exports the flows to Web Protocol Circulation Data Export (IPFIX) gathering processes or an IPFIX-based file format for processing by downstream instruments, particularly the SEI’s SiLK device. SiLK, nonetheless, was not designed to research DPI knowledge nor course of the quantity of stream knowledge generated by organizations on the scale of Web service suppliers.
We sensed we had a big-data downside on our palms, and in 2017 a authorities sponsor requested the SEI to make YAF work with a big-data evaluation device. In response, we created the Mothra evaluation platform to allow scalable analytical workflows that stretch past the restrictions of typical stream data and the power of our present instruments to course of them. Mothra is a set of open-source libraries for working with community stream knowledge (reminiscent of Cisco’s Netflow) within the Apache Spark large-scale knowledge analytics engine.
Mothra bridges the beforehand stand-alone instruments of the CERT Community Situational Consciousness (NetSA) Safety Suite and Spark. Different safety options, reminiscent of antivirus purposes or intrusion detection and prevention techniques, may also export knowledge to Spark. Mothra permits analysts to entry community stream knowledge alongside these different sources, all inside a standard big-data evaluation atmosphere. With all these knowledge sources obtainable for evaluation, organizations with very giant networks can obtain extra complete community situational consciousness.
Just like the SEI’s pre-existing evaluation device, SiLK Mothra was designed to research community stream data, particularly these produced by the SEI’s YAF (But One other Flowmeter) device. Mothra transforms YAF output right into a format readable by Apache Spark, and the Mothra platform and likewise
- facilitates bulk storage and evaluation of cybersecurity knowledge with excessive ranges of flexibility, efficiency, and interoperability
- reduces the engineering effort concerned in growing, transitioning, and operationalizing new analytics
- serves all main constituencies inside the community safety neighborhood, together with knowledge scientists, first-tier incident responders, system directors, and hobbyists
Mothra immediately processes the binary IPFIX format, a typical of the Web Engineering Job Power (IETF). Analysts can effectively pull out simply the items they need, and so they can then use the Spark evaluation engine on the IPFIX knowledge. Mothra allows you to merely drop the info proper in with out having assume forward about find out how to rework it. These transformations change the collected knowledge as little as potential, preserving it for future evaluation.
Analysts can use Mothra to deliver the programming energy of Spark to bear on community stream knowledge from the NetSA Safety Suite. SiLK’s filters enable restricted queries on pure stream datasets. Mothra and Spark allow a lot deeper, versatile queries over DPI-enriched stream to seek out rather more knowledge of curiosity. For instance, analysts can now pull any sort of knowledge they’ll specific as a program and might carry out iterative pulls during which the info pulled modifications throughout the iterations. They will additionally pull knowledge that consists of packets larger than the typical variety of packets inside the matching set of standards. One thing that might take you lots of scripting in SiLK can now be condensed right down to a half web page of code.
Evaluation of all that stream knowledge requires loads of storage and programming experience. Mothra permits organizations with the infrastructure and personnel to help Apache Spark, use their experience, and apply DPI analytics to community stream knowledge. This perception can assist them consider their present defenses and uncover safety gaps, particularly on infrastructure-level enterprise networks.
Prototyping Mothra at Cloud Scale
Having developed Mothra and proven it to be helpful in on-premises community environments, we subsequent set our sights on answering the next questions:
- Can Mothra be deployed in a cloud atmosphere?
- Can a cloud-based deployment work as successfully as Mothra does in an on-premises atmosphere?
- How can cloud deployment be greatest completed to optimize Mothra’s efficiency?
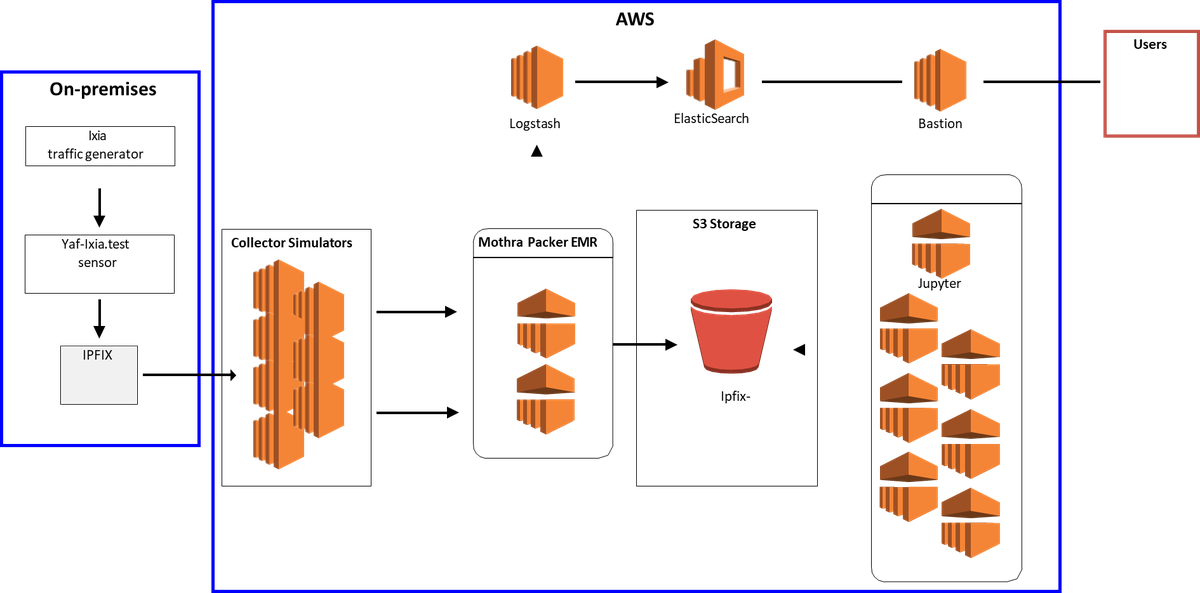
To reply these questions, we researched strategies for deploying Mothra and its associated system elements within the AWS GovCloud atmosphere. Our mission concerned a number of groups that collaborated to handle code improvement, system engineering, and testing. We constructed prototypes of accelerating functionality that progressed towards goal system efficiency. These prototypes ingested billions of stream data per day with applicable content material distributed by means of the info and made that knowledge obtainable for evaluation in an appropriate period of time.
Determine 1 depicts one of many prototypes we developed, which deployed Mothra to Amazon Elastic Map Scale back (EMR) working Spark and backed by the EMR File System (EMRFS) with storage in Amazon S3. EMRFS is an implementation of the Hadoop Distributed File System (HDFS) that every one Amazon EMR clusters use for studying and writing common recordsdata from EMR on to S3. EMRFS supplies the comfort of storing persistent knowledge in S3 to be used with Hadoop whereas additionally offering options like constant viewing, knowledge encryption, and elasticity.
In conducting our analysis, we rapidly decided that Mothra might be simply put in and operated at speeds that clearly met consumer wants when deployed within the cloud. Question efficiency within the cloud atmosphere, nonetheless, was suboptimal. To sort out that downside, we undertook the next work:
- applied a number of system designs within the SEI’s hybrid prototyping atmosphere (particularly, we used our Ixia site visitors generator to create an artificial knowledge stream that resulted in a large knowledge repository inside AWS)
- modified configurations as take a look at outcomes are examined to handle noticed issues
- developed simulators to supply stream volumes that match these noticed on manufacturing techniques
- executed take a look at plans to judge the info ingest course of and consultant question operations
- developed new code to optimize knowledge learn operations
- tuned system companies (e.g., Spark)
Our work confirmed that Mothra might efficiently combine with AWS GovCloud and led us to supply a set of levers that can be utilized for tuning system companies to particular knowledge traits. These levers embrace file-read parameters and desired file dimension, that are saved in a system repository. To find out the optimum settings for working within the AWS GovCloud atmosphere systematically, we generated a number of Mothra repositories with totally different file eventualities and executed a collection of checks utilizing a spread of parameter settings.