The zero-day exploitation of a now-patched medium-severity safety flaw within the Fortinet FortiOS working system has been linked to a suspected Chinese language hacking group.
Risk intelligence agency Mandiant, which made the attribution, stated the exercise cluster is a part of a broader marketing campaign designed to deploy backdoors onto Fortinet and VMware options and preserve persistent entry to sufferer environments.
The Google-owned risk intelligence and incident response agency is monitoring the malicious operation beneath its uncategorized moniker UNC3886, a China-nexus risk actor.
“UNC3886 is a complicated cyber espionage group with distinctive capabilities in how they function on-network in addition to the instruments they make the most of of their campaigns,” Mandiant researchers stated in a technical evaluation.
“UNC3886 has been noticed concentrating on firewall and virtualization applied sciences which lack EDR assist. Their means to govern firewall firmware and exploit a zero-day signifies they’ve curated a deeper-level of understanding of such applied sciences.”
It is value noting that the adversary was beforehand tied to a different intrusion set concentrating on VMware ESXi and Linux vCenter servers as a part of a hyperjacking marketing campaign designed to drop backdoors comparable to VIRTUALPITA and VIRTUALPIE.
The newest disclosure from Mandiant comes as Fortinet revealed that authorities entities and enormous organizations had been victimized by an unidentified risk actor by leveraging a zero-day bug in Fortinet FortiOS software program to end in knowledge loss and OS and file corruption.
The vulnerability, tracked as CVE-2022-41328 (CVSS rating: 6.5), issues a path traversal bug in FortiOS that might result in arbitrary code execution. It was patched by Fortinet on March 7, 2023.
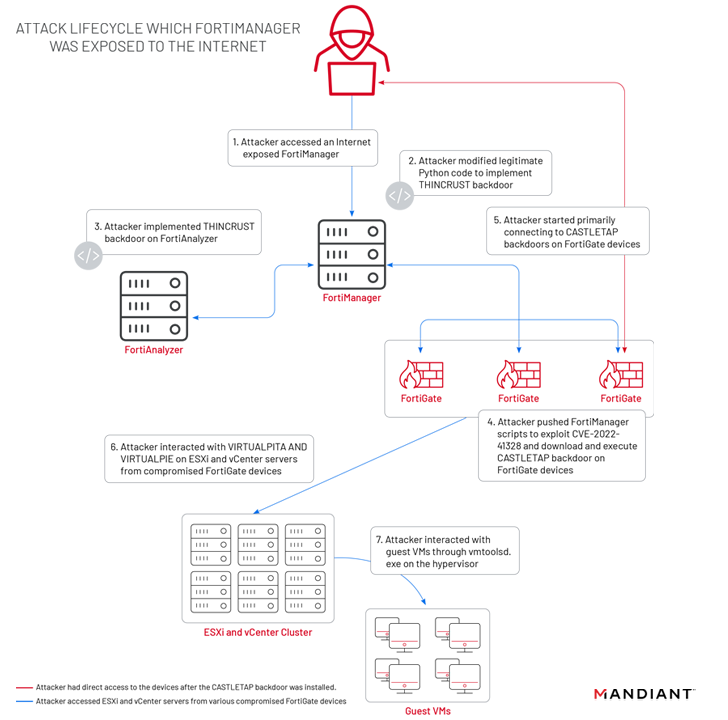
In accordance with Mandiant, the assaults mounted by UNC3886 focused Fortinet’s FortiGate, FortiManager, and FortiAnalyzer home equipment to deploy two totally different implants comparable to THINCRUST and CASTLETAP. This, in flip, was made doable owing to the truth that the FortiManager gadget was uncovered to the web.
THINCRUST is a Python backdoor able to executing arbitrary instructions in addition to studying and writing from and to information on disk.
The persistence afforded by THINCRUST is subsequently leveraged to ship FortiManager scripts that weaponize the FortiOS path traversal flaw to overwrite respectable information and modify firmware photos.
This features a newly added payload referred to as “/bin/fgfm” (known as CASTLETAP) that beacons out to an actor-controlled server in order to just accept incoming directions that enable it to run instructions, fetch payloads, and exfiltrate knowledge from the compromised host.
“As soon as CASTLETAP was deployed to the FortiGate firewalls, the risk actor related to ESXi and vCenter machines,” the researchers defined. “The risk actor deployed VIRTUALPITA and VIRTUALPIE to ascertain persistence, permitting for continued entry to the hypervisors and the visitor machines.”
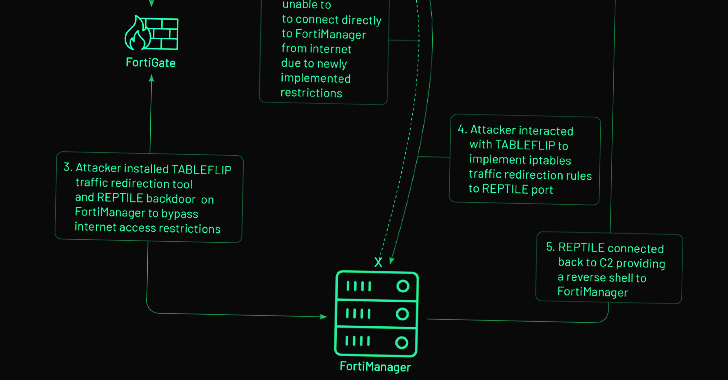
Alternatively, on FortiManager gadgets that implement web entry restrictions, the risk actor is alleged to have pivoted from a FortiGate firewall compromised with CASTLETAP to drop a reverse shell backdoor named REPTILE (“/bin/klogd”) on the community administration system to regain entry.
Uncover the Hidden Risks of Third-Occasion SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to be taught in regards to the sorts of permissions being granted and learn how to reduce threat.
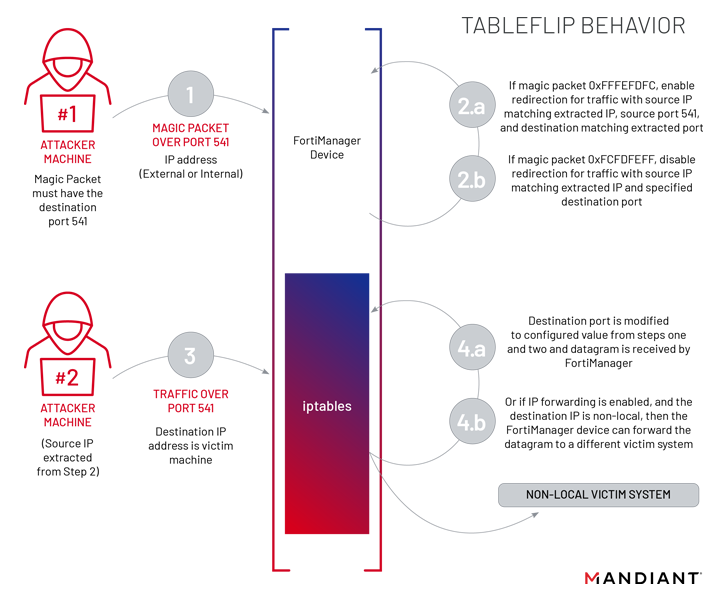
Additionally employed by UNC3886 at this stage is a utility dubbed TABLEFLIP, a community site visitors redirection software program to attach on to the FortiManager gadget whatever the access-control record (ACL) guidelines put in place.
That is removed from the primary time Chinese language adversarial collectives have focused networking gear to distribute bespoke malware, with current assaults benefiting from different vulnerabilities in Fortinet and SonicWall gadgets.
The revelation additionally comes as risk actors are growing and deploying exploits sooner than ever earlier than, with as many as 28 vulnerabilities exploited inside seven days of public disclosure — a 12% rise over 2021 and an 87% rise over 2020, in response to Rapid7.
That is additionally vital, not least as a result of China-aligned hacking crews have change into “notably proficient” at exploiting zero-day vulnerabilities and deploying customized malware to steal person credentials and preserve long-term entry to focus on networks.
“The exercise […] is additional proof that superior cyber espionage risk actors are benefiting from any know-how obtainable to persist and traverse a goal setting, particularly these applied sciences that don’t assist EDR options,” Mandiant stated.