
State-backed Chinese language hackers have developed a Linux variant for the SideWalk backdoor used in opposition to Home windows methods belonging to targets within the educational sector.
The malware is attributed with excessive confidence to the SparklingGoblin risk group, additionally tracked as Earth Baku, which is believed to be linked to the APT41 cyberespionage group.
Focusing on educational sector
The SideWalk Linux backdoor has been noticed previously, initially being tracked as StageClient by safety researchers at cybersecurity firm ESET.
An early variant of the malware was noticed by researchers at 360 Netlab, the risk intelligence workforce at Chinese language web safety firm Qihoo 360, and detailed two years in the past in a weblog put up concerning the Specter botnet hitting IP cameras.
After analyzing Specter and StageClient, ESET researchers decided that each malware items have the identical root and are Linux variants of SideWalk.
In 2021, researchers at Pattern Micro documented new instruments from a cyberespionage marketing campaign attributed to APT41/Earth Baku, together with the SideWalk backdoor, which they observe as ScrambleCross.
ESET notes in a report immediately that whereas SideWalk Linux has been used in opposition to a number of targets previously, their telemetry knowledge exhibits that the variant they found was deployed in opposition to just one sufferer in February 2021, a college in Hong Kong.
SparkGoblin targeted on the identical goal previously, compromising the identical college in Could 2020, throughout the college students’ protests.
“The group repeatedly focused this group over an extended time frame, efficiently compromising a number of key servers, together with a print server, an electronic mail server, and a server used to handle scholar schedules and course registrations” – ESET
Though SparklingGoblin is generally attacking targets in East and Southeast Asia, the group has additionally been hitting organizations outdoors these areas, its focus being on the tutorial sector.
SideWalk for Home windows prepared for Linux
Trying on the SideWalk variants for Linux and Home windows, ESET observed “hanging” similarities in the way in which they operate, the implementation of a number of elements, and the payloads dropped on the compromised system.
The researchers say that each variants carried out the ChaCha20 encryption algorithm to “use a counter with an preliminary worth of 0x0B,” one thing that’s specific to SideWalk.
On each Home windows and Linux, the malware makes use of the identical 5 threads, executed concurrently, for particular duties:
- [StageClient::ThreadNetworkReverse] – fetching proxy configurations for alternate connections to the command and management (C2) server
- [StageClient::ThreadHeartDetect] – shut connection to C2 server when instructions are usually not obtained within the specified time
- [StageClient::ThreadPollingDriven] – ship heartbeat instructions to C2 server if there is no such thing as a information to ship
- [StageClient::ThreadBizMsgSend] – test for knowledge to be despatched in message queues for all different threads and course of it
- [StageClient::ThreadBizMsgHandler] – test for pending messages from the C2 server
ESET researchers additionally discovered that each Linux and Home windows variants for SideWalk had the identical payload delivered by means of the dead-drop resolver string hosted in a Google Docs file.
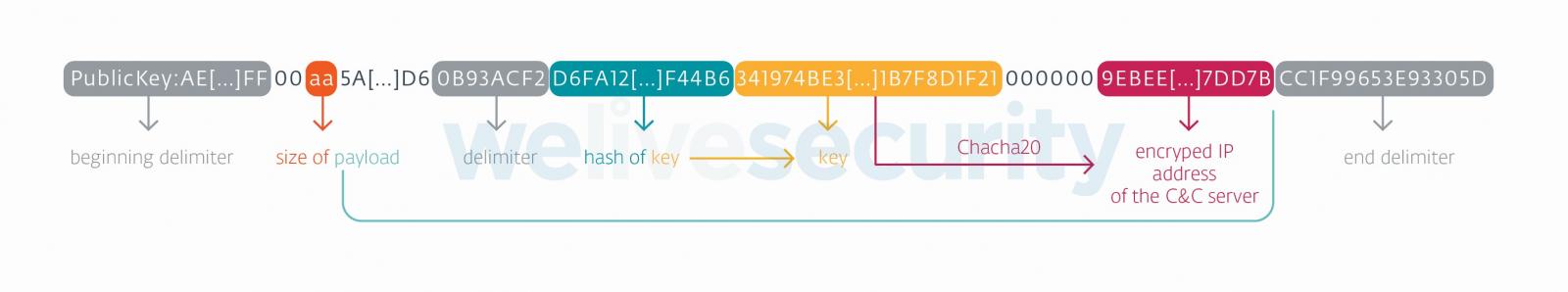
supply: ESET
One other piece of proof connecting the 2 SideWalk variants to the identical risk actor was that they each used the identical encryption key to move knowledge from the contaminated machine to the C2 server.
SparklingGoblin has the capabilities to develop malware tailored to its wants, as evidenced by the SideWalk Linux variant. Nonetheless, the group additionally has entry to implants noticed in operations attributed to different Chinese language hacking teams.
ESET researchers say that SparklingGoblin has entry to the ShadowPad backdoor and Winnti malware.

