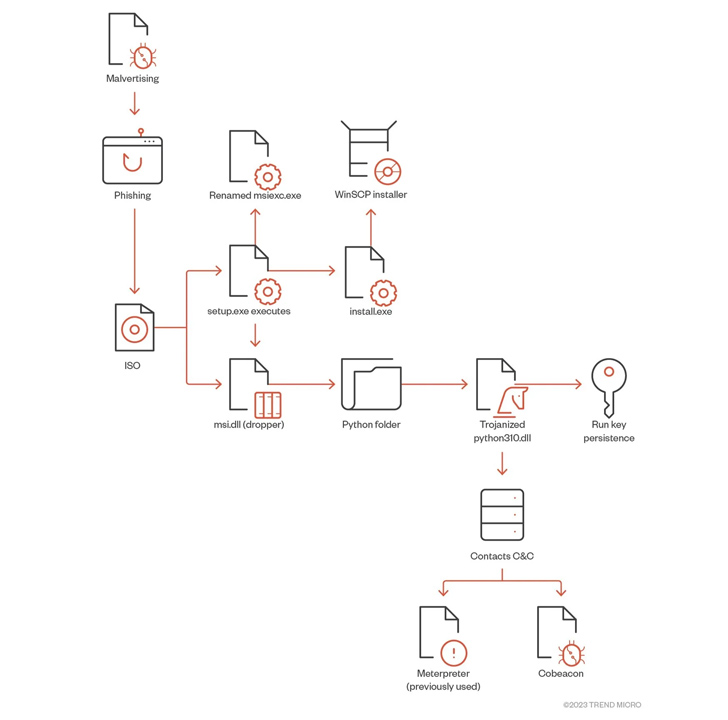
Menace actors related to the BlackCat ransomware have been noticed using malvertising methods to distribute rogue installers of the WinSCP file switch software.
“Malicious actors used malvertising to distribute a chunk of malware by way of cloned webpages of respectable organizations,” Development Micro researchers mentioned in an evaluation printed final week. “On this case, the distribution concerned a webpage of the well-known software WinSCP, an open-source Home windows software for file switch.”
Malvertising refers to the usage of search engine optimization poisoning strategies to unfold malware by way of internet advertising. It sometimes includes hijacking a selected set of key phrases to show bogus advertisements on Bing and Google search outcomes pages with the purpose of redirecting unsuspecting customers to sketchy pages.
The thought is to trick customers looking for functions like WinSCP into downloading malware, on this occasion, a backdoor that incorporates a Cobalt Strike Beacon that connects to a distant server for follow-on operations, whereas additionally using respectable instruments like AdFind to facilitate community discovery.
The entry afforded by Cobalt Strike is additional abused to obtain a lot of packages to conduct reconnaissance, enumeration (PowerView), lateral motion (PsExec), bypass antivirus software program (KillAV BAT), and exfiltrate buyer information (PuTTY Safe Copy shopper). Additionally noticed is the usage of the Terminator protection evasion device to tamper with safety software program by the use of a Convey Your Personal Susceptible Driver (BYOVD) assault.
Within the assault chain detailed by the cybersecurity firm, the risk actors managed to steal top-level administrator privileges to conduct post-exploitation actions and tried to arrange persistence utilizing distant monitoring and administration instruments like AnyDesk in addition to entry backup servers.
“It’s extremely seemingly that the enterprise would have been considerably affected by the assault if intervention had been sought later, particularly because the risk actors had already succeeded in gaining preliminary entry to area administrator privileges and began establishing backdoors and persistence,” Development Micro mentioned.
The event is simply the newest instance of risk actors leveraging the Google Advertisements platform to serve malware. In November 2022, Microsoft disclosed an assault marketing campaign that leverages the promoting service to deploy BATLOADER, which is then used to drop Royal ransomware.
It additionally comes as Czech cybersecurity firm Avast launched a free decryptor for the fledgling Akira ransomware to assist victims recuperate their information with out having to pay the operators. Akira, which first appeared in March 2023, has since expanded its goal footprint to incorporate Linux techniques.
“Akira has a number of similarities to the Conti v2 ransomware, which can point out that the malware authors had been at the least impressed by the leaked Conti sources,” Avast researchers mentioned. The corporate didn’t disclose the way it cracked the ransomware’s encryption algorithm.
The Conti/TrickBot syndicate, aka Gold Ulrick or ITG23, shut down in Might 2022 after struggling a collection of disruptive occasions triggered by the onset of the Russian invasion of Ukraine. However the e-crime group continues to exist to this date, albeit as smaller entities and utilizing shared crypters and infrastructure to distribute their warez.
IBM Safety X-Drive, in a latest deep dive, mentioned the gang’s crypters, that are functions designed to encrypt and obfuscate malware to evade detection by antivirus scanners and hinder evaluation, are getting used to additionally disseminate new malware strains resembling Aresloader, Canyon, CargoBay, DICELOADER, Lumma C2, Matanbuchus, Minodo (previously Domino), Pikabot, SVCReady, Vidar.
“Beforehand, the crypters had been used predominantly with the core malware households related to ITG23 and their shut companions,” safety researchers Charlotte Hammond and Ole Villadsen mentioned. “Nonetheless, the fracturing of ITG23 and emergence of latest factions, relationships, and strategies, have affected how the crypters are used.”
Regardless of the dynamic nature of the cybercrime ecosystem, as nefarious cyber actors come and go, and a few operations companion collectively, shut down, or rebrand their financially motivated schemes, ransomware continues to be a fixed risk.
This consists of the emergence of a brand new ransomware-as-a-service (RaaS) group referred to as Rhysida, which has primarily singled out schooling, authorities, manufacturing, and expertise sectors throughout Western Europe, North and South America, and Australia.
“Rhysida is a 64-bit Moveable Executable (PE) Home windows cryptographic ransomware software compiled utilizing MINGW/GCC,” SentinelOne mentioned in a technical write-up. “In every pattern analyzed, the appliance’s program identify is ready to Rhysida-0.1, suggesting the device is in early levels of improvement.”