The operators behind the BazaCall name again phishing technique have continued to evolve with up to date social engineering techniques to deploy malware on focused networks.
The scheme ultimately acts as an entry level to conduct monetary fraud or the supply of next-stage payloads akin to ransomware, cybersecurity firm Trellix mentioned in a report printed final week.
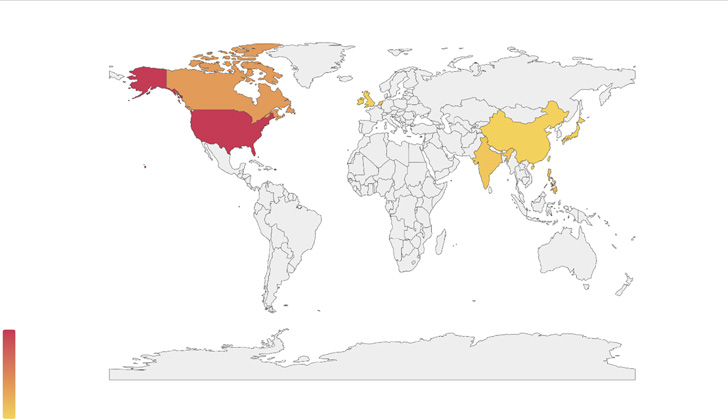
Major targets of the most recent assault waves embody the U.S., Canada, China, India, Japan, Taiwan, the Philippines, and the U.Ok.
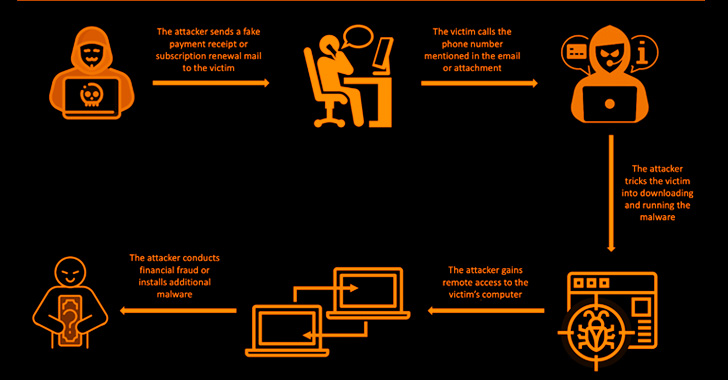
BazaCall, additionally known as BazarCall, first gained reputation in 2020 for its novel strategy of distributing the BazarBackdoor (aka BazarLoader) malware by manipulating potential victims into calling a telephone quantity laid out in decoy electronic mail messages.
These electronic mail baits intention to create a false sense of urgency, informing the recipients about renewal of a trial subscription for, say, an antivirus service. The messages additionally urge them to contact their assist desk to cancel the plan, or threat getting routinely charged for the premium model of the software program.
The last word objective of the assaults is to allow distant entry to the endpoint underneath the guise of terminating the supposed subscription or putting in a safety resolution to rid the machine of malware, successfully paving the best way for follow-on actions.
One other tactic embraced by the operators includes masquerading as incident responders in PayPal-themed campaigns to deceive the caller into pondering that their accounts had been accessed from eight or extra gadgets unfold throughout random places the world over.
Whatever the situation employed, the sufferer is prompted to launch a particular URL – a specifically crafted web site designed to obtain and execute a malicious executable that, amongst different recordsdata, additionally drops the reliable ScreenConnect distant desktop software program.
A profitable persistent entry is adopted by the attacker opening faux cancellation types that ask the victims to fill out private particulars and sign up to their financial institution accounts to finish the refund, however in actuality are fooled into sending the cash to the scammer.
The event comes as not less than three completely different spinoff teams from the Conti ransomware cartel have embraced the decision again phishing method as an preliminary intrusion vector to breach enterprise networks.
The ties to Conti do not finish there. BazarBackdoor, for its half, is the creation of a cybercrime group often called TrickBot, which was taken over by Conti earlier this 12 months earlier than the latter’s shutdown in Could-June 2022 over its allegiance to Russia in its assault on Ukraine.