The Azov Ransomware continues to be closely distributed worldwide, now confirmed to be an information wiper that deliberately destroys victims’ knowledge and infects different applications.
Final month, a risk actor started distributing malware referred to as ‘Azov Ransomware‘ by way of cracks and pirated software program that pretended to encrypt victims’ information.
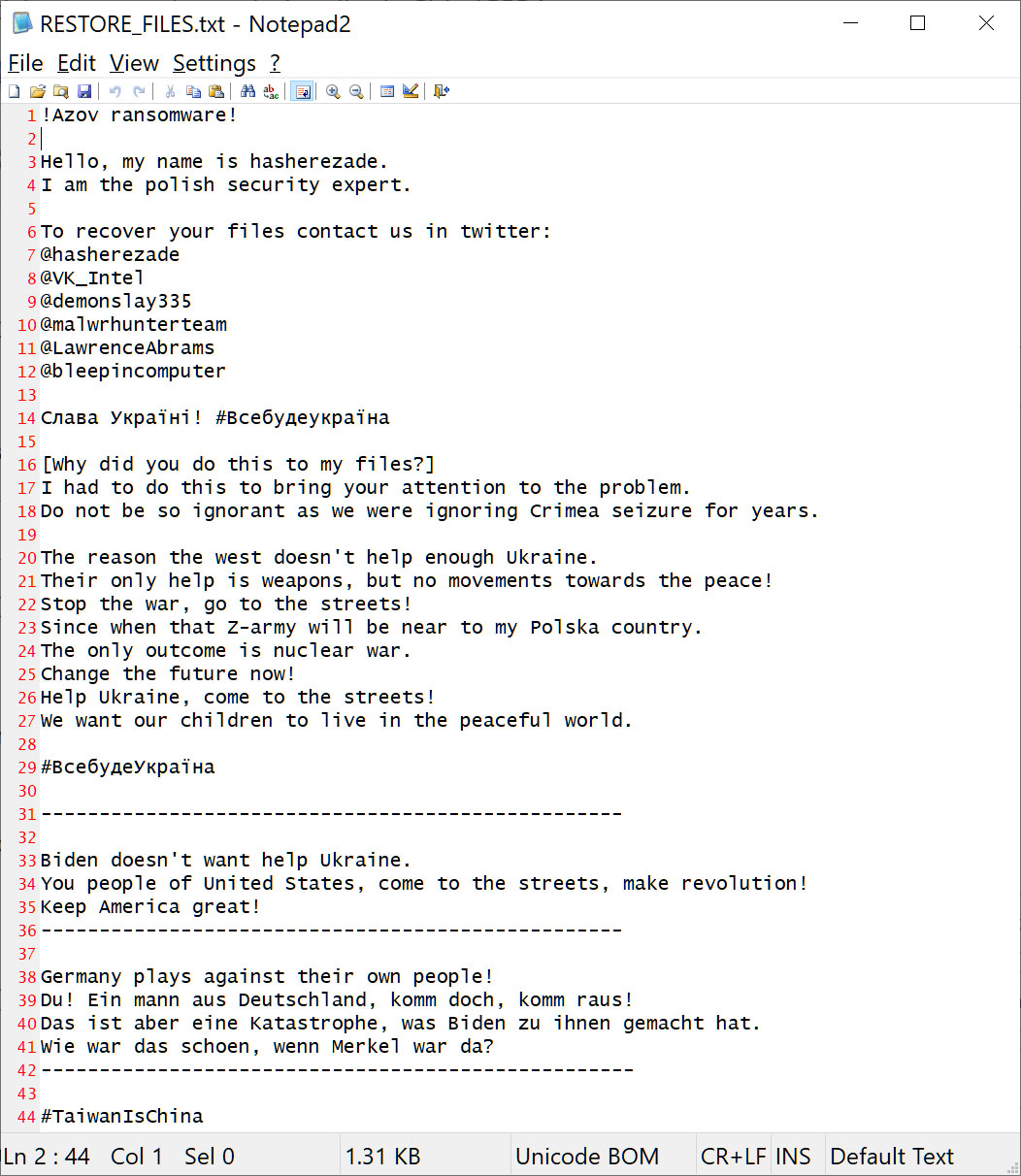
Nonetheless, as an alternative of offering contact information to barter a ransom, the ransom notice instructed victims to contact safety researchers and journalists to border them because the builders of the ransomware.
Supply: BleepingComputer
As there was no contact information, and the listed contacts had no means of serving to victims, we assumed that the malware was an information wiper.
A diabolical knowledge wiper
Final week, Checkpoint safety researcher Jiří Vinopal analyzed the Azov Ransomware and confirmed to BleepingComputer that the malware was specifically crafted to deprave knowledge.
The malware included a set off time that might trigger it to sit down dormant on the sufferer’s gadgets till October twenty seventh, 2022, at 10:14:30 AM UTC, which might then set off the corruption of all knowledge on the gadget.
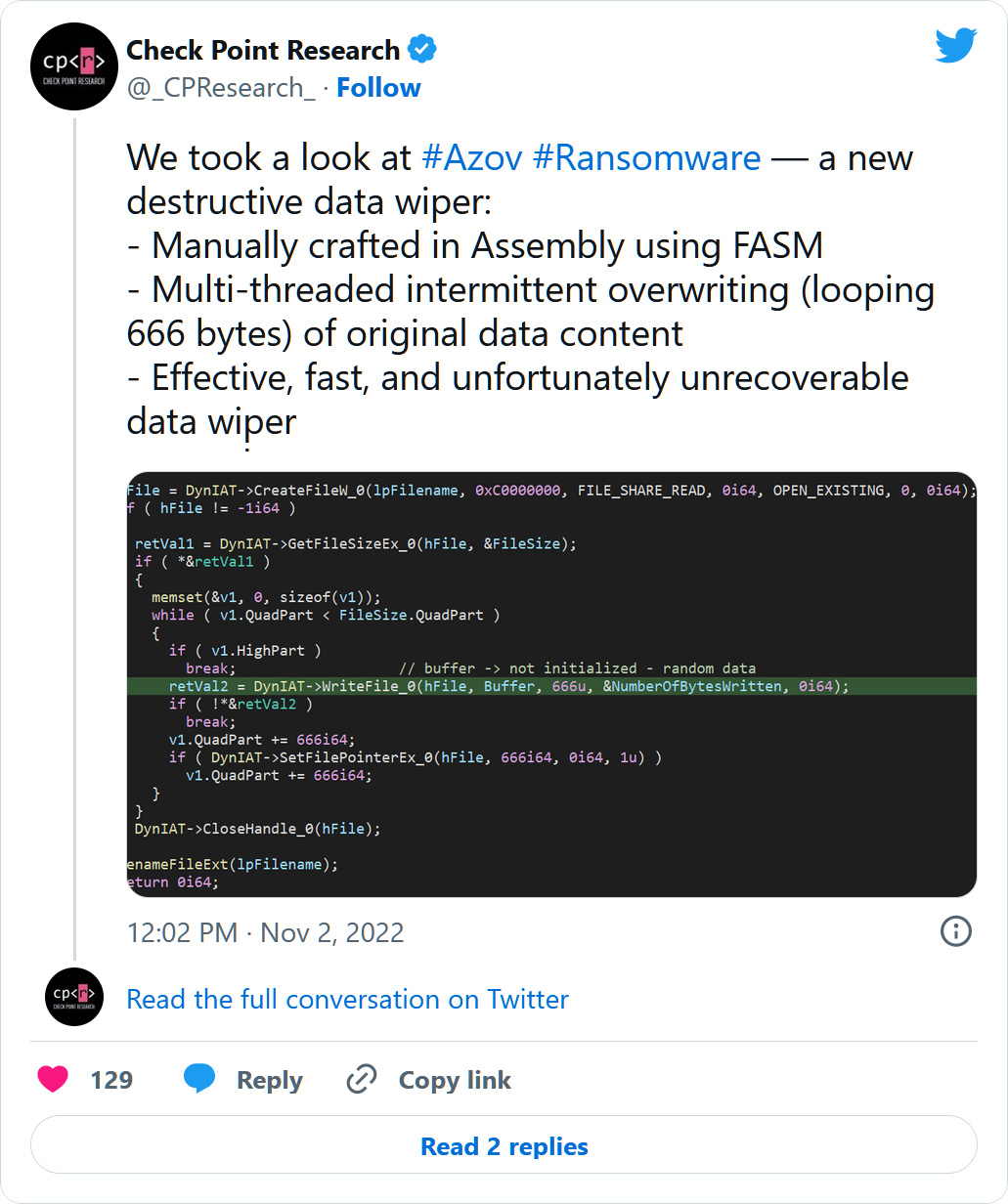
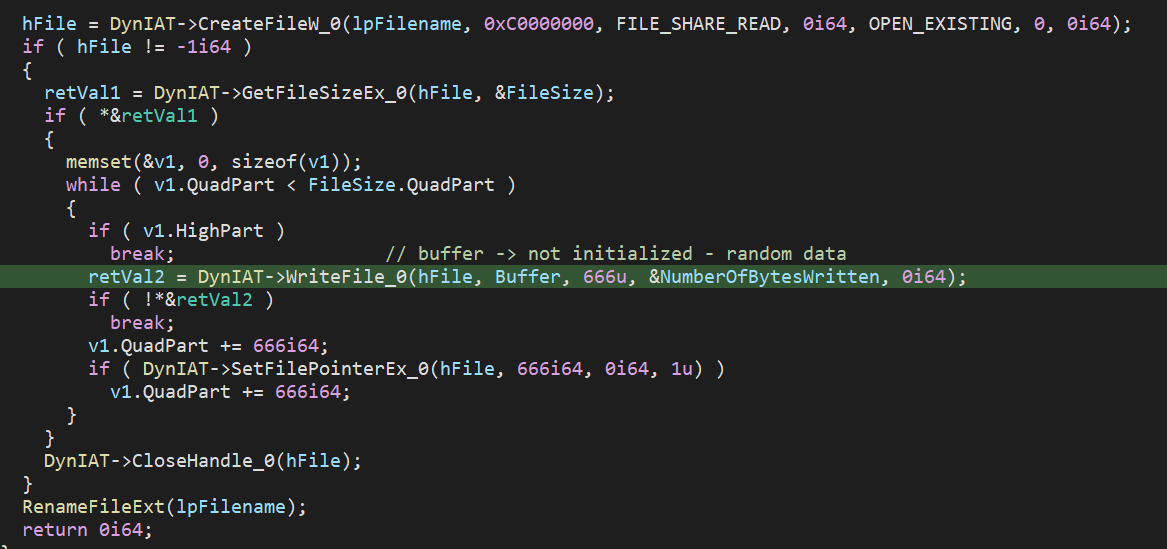
Vinopal says it could overwrite a file’s contents and corrupt knowledge in alternating 666-byte chunks of rubbish knowledge. The quantity 666 is often related to the biblical ‘Satan,’ clearly displaying the malicious intent of the risk actor.
“Every cycle precisely 666 bytes are being overwritten with random (uninitialized knowledge) and the following 666 bytes are left unique,” Vinopal instructed BleepingComputer.
“This works in a loop, so wiped file construction would appear like this: 666 bytes of rubbish, 666 bytes unique, 666bytes of rubbish, 666 bytes unique, and so forth…”
Supply: Jiří Vinopal
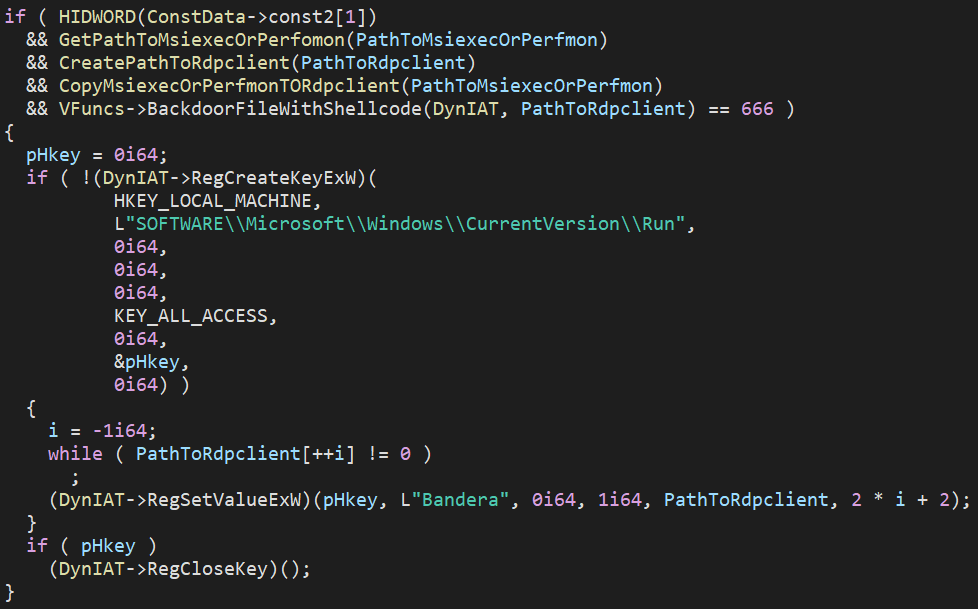
To make issues even worse, the info wiper will infect, or ‘backdoor,’ different 64-bit executables on the Home windows gadget whose file path doesn’t comprise the next strings:
:Home windows
ProgramData
cache2entries
LowContent.IE5
Consumer DataDefaultCache
Paperwork and Settings
All CustomersWhen backdooring an executable, the malware will inject code that can trigger the info wiper to launch when a seemingly innocent executable is launched.
“Backdooring of the information works in a polymorphic means, which suggests the identical shellcodes used to backdoor information are each time encoded in a different way,” defined Vinopal.
“(ex. if the identical file A could be backdoored 2 instances to file B1 and B2, B1 and B2 shellcode components are completely different so B1 and B2 are additionally completely different on the disk) – that is used in all probability to keep away from static AV detection.”
Supply: Jiří Vinopal
At the moment, the risk actor continues distributing the malware by way of the Smokeloader botnet, generally present in pretend pirated software program and crack websites.
On the time of this writing, there are already pages of submissions of this malware to VirusTotal for right this moment alone, displaying what number of victims have been affected by this malware over the previous two weeks.
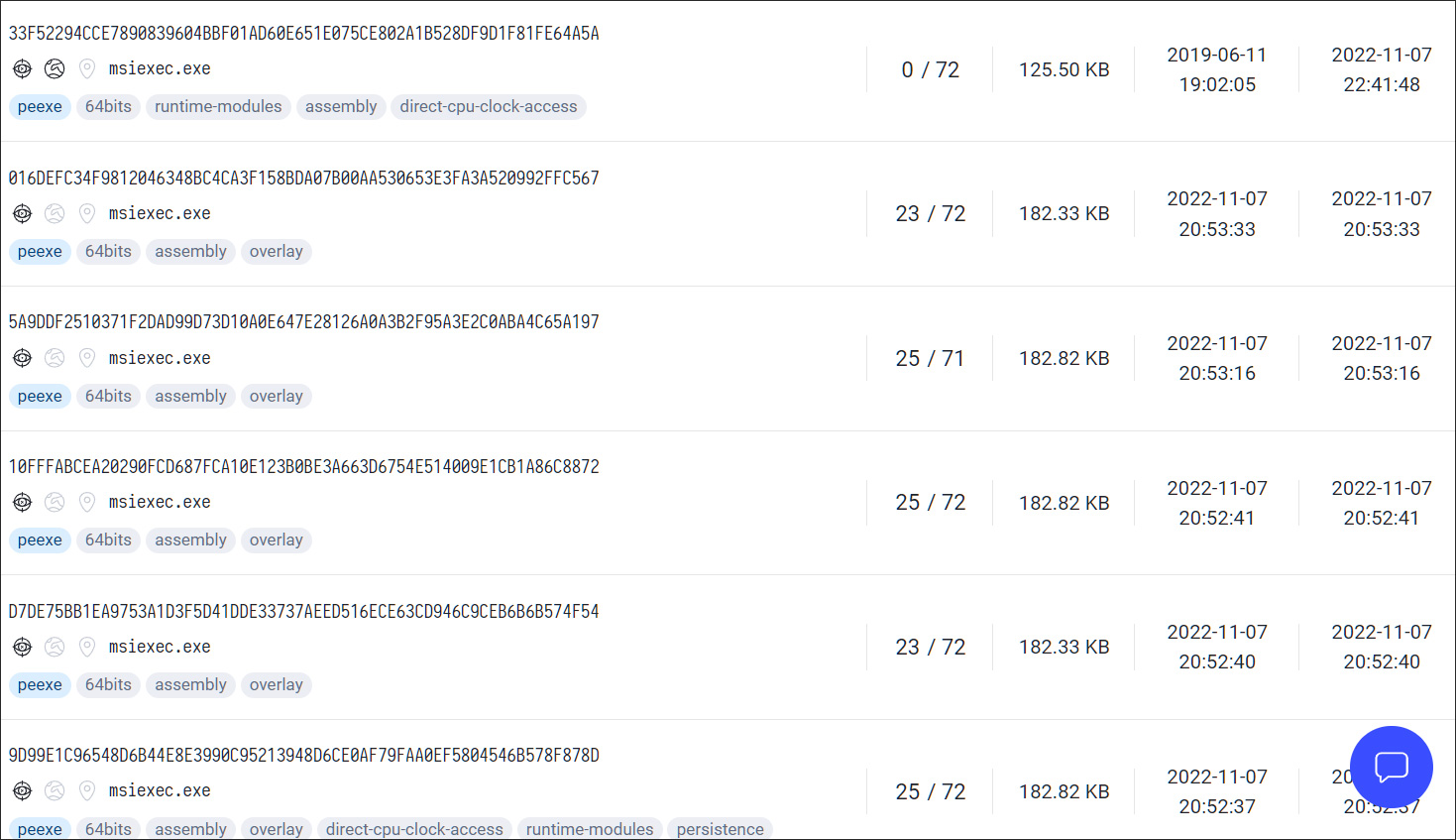
Supply: BleepingComputer
It’s unclear why the risk actor is spending cash to distribute an information wiper. Nonetheless, theories vary from it being performed to cowl up different malicious habits or just to ‘troll’ the cybersecurity group.
Whatever the cause, victims who’re contaminated with Azov Ransomware could have no means of recovering their information, and as different executables are contaminated, they need to reinstall Home windows to be secure.
Moreover, as Smokeloader is getting used to distribute the Azov knowledge wiper, it’s seemingly additionally put in with different malware, comparable to password-stealing malware. Due to this fact, it’s important to reset any passwords to e mail accounts, monetary providers, or different delicate data.
Lastly, whereas the ransomware is known as after the Ukrainian ‘Azov’ navy regiment, this malware is probably going not affiliated with the nation and is simply utilizing the title as a false flag.