The content material of this publish is solely the accountability of the creator. AT&T doesn’t undertake or endorse any of the views, positions, or info supplied by the creator on this article.
Within the discipline of Digital Forensics and Incident Response (DFIR), buying a forensic copy of a suspect’s storage machine is a crucial first step. This course of entails both disk imaging or disk cloning, every with its personal distinct functions and methodologies. On this weblog, we’ll delve into the variations between disk imaging and disk cloning, when to make use of every methodology, and supply step-by-step steering on how you can create a forensic disk picture utilizing FTK Imager.
Disk imaging vs. disk cloning
Disk imaging
Disk imaging is the method of making a bit-for-bit copy or snapshot of a complete storage machine or a particular partition. In forensic imaging, the purpose is to create a precise, bit-for-bit copy of the supply disk with out making any modifications to the unique information. The important thing traits of disk imaging embody:
Non-destructive: Disk imaging is a non-destructive course of that does not alter the unique information on the supply machine. It preserves the integrity of the proof.
File-level entry: After imaging, forensic examiners can entry and analyze the information and folders inside the picture utilizing specialised forensic software program. This permits for focused evaluation and information restoration.
Metadata preservation: Disk imaging retains crucial metadata reminiscent of file timestamps, permissions, and attributes, which may be essential in investigations.
Versatile storage: Disk photos may be saved in varied codecs (e.g., E01, DD, AFF) and on totally different media, reminiscent of exterior exhausting drives or community storage.
Disk cloning
Disk cloning, alternatively, entails creating a precise duplicate of the supply storage machine, together with all partitions and unallocated house. Not like file copying, disk cloning additionally duplicates the filesystems, partitions, drive meta information and slack house on the drive. The traits of disk cloning embody:
Precise copy: Disk cloning produces an similar copy of the supply machine. It replicates every thing, together with empty house and hidden partitions.
Fast duplication: Cloning is often quicker than imaging as a result of it does not contain the creation of a separate picture file. It is basically a sector-by-sector copy.
Cloning is like making a precise photocopy of a e book, smudges and all. It copies every thing, even the empty pages. So, if we’re coping with a complete laptop, it copies the working system, software program, and each file, whether or not it is helpful or not.
Making a forensic disk picture with FTK Imager
FTK Imager is a broadly used and trusted software for creating forensic disk photos. Listed here are the steps to create a disk picture utilizing FTK Imager:
Obtain and Set up FTK Imager, make certain to make use of newest steady model out there as nicely point out the model and vendor particulars in case notes. This can be a good observe in digital forensics and incident response (DFIR) because it ensures that you’re utilizing essentially the most up-to-date and safe model of the software program, and it supplies necessary documentation concerning the instruments and their configurations utilized in your investigations. Conserving software program up to date is crucial for sustaining the integrity and reliability of your forensic processes.
Obtain and Set up FTK Imager in your forensic workstation. It may be downloaded from right here. You’ll want to offer some info like title, enterprise e mail and so forth., and after you fill within the kind the obtain will begin robotically. You need to use privateness centric providers whereas filling out the data. Start the set up.
As soon as, FTK Imager is put in, launch FTK Imager by clicking on the applying icon.
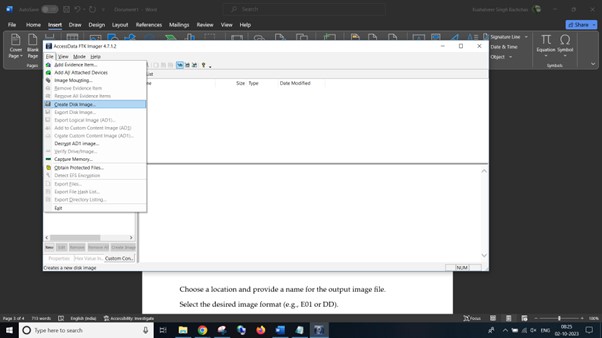
- Within the “File” menu, select “Create Disk Picture.”
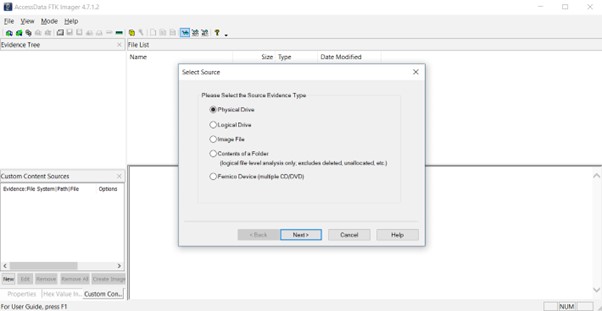
Choose the supply machine (the drive you need to picture) from the record.
Specify picture vacation spot:
Select a location and supply a reputation for the output picture file.
Choose the specified picture format (e.g., E01 or DD).
Configure choices:
Configure imaging choices reminiscent of compression, verification, and hash algorithm as wanted.
Begin imaging:
Click on the “Begin” button to start the imaging course of.
FTK Imager will create a forensic disk picture of the supply machine.
Verification and validation:
After imaging is full, use FTK Imager to confirm the integrity of the picture utilizing hash values.
Evaluation:
Open the forensic picture in FTK Imager or different forensic evaluation instruments to look at the info and conduct investigations.
Keep in mind to observe correct chain of custody procedures, doc your actions, and cling to authorized and moral requirements when conducting digital forensics investigations.
Conclusion
In conclusion, the method of buying digital proof within the discipline of digital forensics is a meticulous and significant endeavor. Whether or not you select to clone or picture a storage machine, every methodology serves its function in preserving the integrity of the proof.
Cloning, with its capability to create a precise duplicate of a system or drive, is invaluable for eventualities the place replication is critical, reminiscent of organising backup methods or rescuing information from failing {hardware}. Its velocity and precision make it an indispensable software within the digital investigator’s toolkit.
Alternatively, imaging, akin to taking snapshots of the related information, excels when you’ll want to protect proof in a forensically sound method. It permits investigators to deal with particular items of data with out the burden of redundant or irrelevant information.
Whichever methodology you select, it is paramount to stick to greatest practices, doc your actions meticulously, and make sure that the integrity of the unique proof is maintained all through the method. With an intensive understanding of when and how you can make use of these methods, digital forensic specialists can uncover the reality whereas safeguarding the integrity of digital proof.