Border Gateway Protocol (BGP) routing is a core a part of the mechanism by which packets are routed on the Web. BGP routing will get e mail to its vacation spot, permits area identify service (DNS) to work, and net pages to load. An vital facet of routing is that packets cross boundaries of the various autonomously managed networks that, collectively, comprise the Web. This permitting us to entry, for instance, the Amazon web site from a cellphone on the Verizon community. It permits navy commanders to see footage of troop transports in a single location and footage of tanks in one other. The BGP protocol, although much less well-known than low-level protocols comparable to IP, TCP, and UDP, has a crucial function in facilitating – and negotiating – the flows of packets among the many many autonomous networks that comprise the Web.
Consequently, vulnerabilities within the BGP protocol are a really large deal. We’ve got a long-standing expectation that the Web is strong, notably with regard to the actions of the various organizations that function parts of the community – and subsequently {that a} system designed to maintain the visitors flowing may solely be disrupted by a really giant occasion. On this SEI Weblog put up, we’ll look at how a small challenge, a deprecated path attribute, could cause a serious interruption to visitors.
BGP: A Path Vector Working Protocol
BGP is a path vector routing protocol that was outlined by the Web Engineering Job Power (IETF) in RFC 1654. As with many Web protocols, there are a lot of different Requests for Feedback (RFC) related to BGP strategies and processes. For instance, RFC 4271 covers BGP path attributes, which can be utilized when making path choice and constructing routing tables to help in routing selections. In keeping with RFC 4271, there are well-known obligatory attributes that have to be supported on all BGP implementations. Nonetheless, these attributes are extensible and permit for personalized bulletins as RFC 4271 explains: Effectively-known obligatory attributes have to be included with each prefix commercial, whereas well-known discretionary attributes might or is probably not included. The customized attributes can be utilized internally by your group or externally (to speak vital data to different organizations). Additionally they might stay unused however accessible. Attributes can comprise details about updates and community origin or weight an autonomous system quantity (ASN) to prioritize it in routing.
The Menace of A number of BGP Implementations
The CERT/CC just lately handled a related case, Vulnerability Be aware VU#347067 (A number of BGP implementations are weak to improperly formatted BGP updates. On this case, a researcher noticed a major outage stemming from an improperly formatted path attribute BGP UPDATE that brought about weak routers, after they obtained an replace, to de-peer (i.e., terminate a peering relationship that permits packets to move from one community to a different). Unaffected routers may additionally go the crafted updates throughout the community, probably resulting in the replace arriving at an affected router from a number of sources, inflicting a number of hyperlinks to fail. The flaw was that, as a substitute of ignoring the improperly formatted attributes, the receiving router dropped the routing replace and misplaced the data being offered about different routes. This case resulted in a real-world de-peering of routers and lack of visitors handed between them.
Briefly, this vulnerability disrupted the move of data that BGP routing was designed to make sure.
Routers which might be designed for resiliency ought to nonetheless perform in the event that they ignore a deprecated attribute. They don’t seem to be anticipated to make use of the attribute because it was initially designed, since it’s now not a part of the official protocol. Including to the issue is inconsistent updating – there are a lot of older variations of the BGP protocol specification deployed on the Web as a result of not everybody can improve to the most recent and greatest model each time one is launched. Nonetheless, all implementations of any Web protocol ought to be capable of perform if new attributes present up as a result of the protocols are at all times altering. Bear in mind, the Web was designed for survivability: a number of errors in attributes shouldn’t interrupt it. Sadly, the response to unspecified attributes is surprising: one group’s router would possibly deal with the attribute with out downside whereas one other one won’t.
Consciousness of the deprecated attributes getting used is step one to figuring out whether or not a selected set up is weak. The inconsistency of updates implies that the organizations asserting routes don’t know what software program different organizations are utilizing. They assume all core routers can deal with the visitors. On this circumstance, verifying that your software program isn’t affected is an effective strategy to keep linked on the Web. This means that organizations contact their router distributors to find out how they deal with deprecated attributes and whether or not responses are strong. They need to be capable of inform you if the response will be modified and what steps to take.
An Evaluation of BGP Information
The SEI CERT Division collects BGP information, so we regarded on the final two years of knowledge to search out out what deprecated attributes are nonetheless introduced. To take action, we used the record of deprecated attributes revealed by the Web Assigned Numbers Authority (IANA).
The three attributes we discovered are listed in Desk 1:
|
Attribute |
Use |
|
|---|---|---|
|
AS_PATHLIMIT |
Designed to assist restrict the distribution of path data |
|
|
CONNECTOR |
Utilized in VPN4 bulletins |
|
|
ENTROPY_LEVEL |
Used to assist with load balancing |
The deprecated attribute that brought about the issue in VU#347067 was ENTROPY_LEVEL. That is the attribute explicit to this occasion, however different deprecated attributes would possibly trigger points later. To scale back this danger and keep away from additional vulnerabilities is to grasp extra concerning the circumstances that might trigger it. On this case, it’s how the router handles deprecated attributes (or doesn’t).
We regarded on the variety of BGP bulletins every day that used these deprecated attributes (Determine 1).
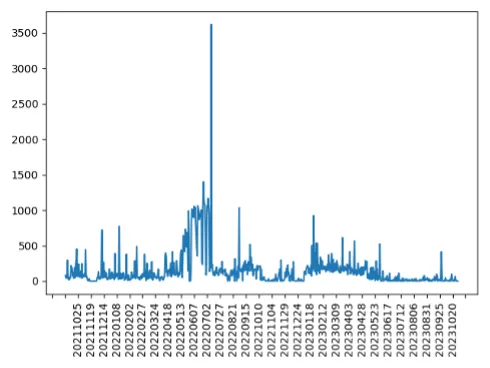
Determine 1: Variety of Bulletins of the Deprecated Attribute ENTROPY_LEVEL
The best variety of bulletins (3,620) occurred on July 7, 2022. That doesn’t appear to be very many within the context of hundreds of thousands and hundreds of thousands of route bulletins a day, however a small attribute, mishandled by the improper router, could cause havoc, as we noticed beforehand.
An vital function of this example is that routers that announce the deprecated attribute can’t sense that they’re inflicting an issue. The configuration or software program nonetheless makes use of these deprecated attributes, and consequently the router will freely share it with the Web as they’re designed to do. The actual troublemakers are the routers that obtain the routes.
Deprecated Attribute Use Over Time
In routing, as with many issues on the Web, we all know who did it, when they did it, how they did it, and even most definitely the place they did it. We simply don’t know why these organizations are utilizing these deprecated attributes. It’s their inside resolution to make use of them and normally it isn’t related.
With regard to the who, we examined the time collection of this information, which exhibits, on the vertical axis, the variety of ASNs (autonomous system numbers, that are identifiers for the assorted networks that comprise the Web) asserting a deprecated attribute every day over a span of 9 days (Determine 2).
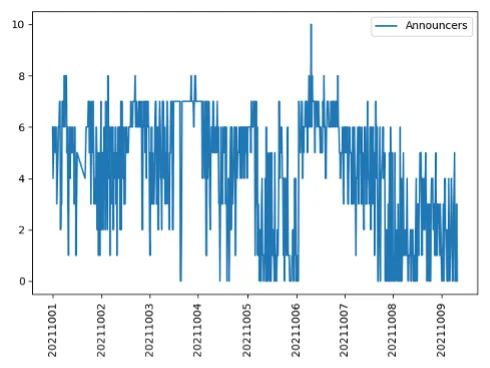
Determine 2: Time Collection of AS Saying Deprecated Attributes
Determine 2 illustrates a time collection with a dip adopted by a peak, which was adopted by one other dip. That’s, the overall variety of ASNs asserting deprecated attributes dropped, then elevated. Slightly than guessing when that occurred, we used an algorithm to search out these change factors (Determine 3).
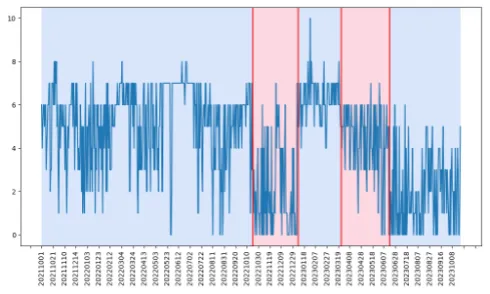
Determine 3: Change Level Evaluation of ASNs Saying Deprecated Attributes
On this case, change level evaluation regarded for shifts within the common worth throughout time. Beginning at 20221020, the common variety of announcers dips, then recovers briefly at 20230108. It dips once more and 20230324 after which, lastly, beginning at 20230618, the common variety of announcers goes down once more. The variety of autonomous methods that used these deprecated attributes, on common, decreased over time. The change of the bulletins over time tells us that at sure factors, abrupt modifications had been made within the variety of organizations that used the attributes. The excellent news is that fewer are utilizing them. The dangerous information is we don’t know why those who use them proceed to take action.
Avoiding the Havoc of Deprecated Attributes
Now we now have a greater concept of when one thing occurred. We have no idea what brought about organizations to begin or cease asserting the deprecated attributes. We do know, nevertheless, that organizations receiving routes on the stay Web ought to pay attention to the potential downside and be certain that they aren’t weak to bulletins utilizing deprecated attributes. Due to the importance of BGP in managing “cross-border” flows within the Web, the potential penalties could possibly be giant.
In conclusion, we advise that organizations work with distributors to confirm and perceive their course of for dealing with deprecated attributes.


