By the point modifications have made their strategy to the legacy database, then you would argue that it’s too late for
occasion interception.
That mentioned, “Pre-commit” triggers can be utilized to intercept a database write occasion and take completely different actions.
For instance a row might be inserted right into a separate Occasions desk to be learn/processed by a brand new part –
while continuing with the write as earlier than (or aborting it).
Be aware that important care needs to be taken in the event you change the present write behaviour as you might be breaking
a significant implicit contract.
Case Research: Incremental area extraction
Considered one of our groups was working for a shopper whose legacy system had stability points and had turn out to be troublesome to keep up and sluggish to replace.
The organisation was seeking to treatment this, and it had been determined that probably the most acceptable approach ahead for them was to displace the legacy system with capabilities realised by a Service Primarily based Structure.
The technique that the group adopted was to make use of the Strangler Fig sample and extract domains, separately, till there was little to not one of the authentic utility left.
Different issues that had been in play included:
- The necessity to proceed to make use of the legacy system with out interruption
- The necessity to proceed to permit upkeep and enhancement to the legacy system (although minimising modifications to domains being extracted was allowed)
- Modifications to the legacy utility had been to be minimised – there was an acute scarcity of retained data of the legacy system
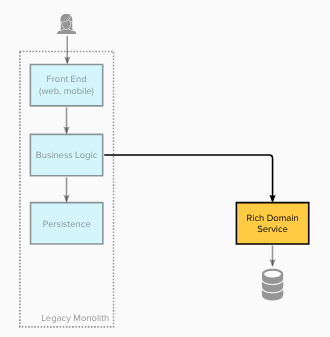
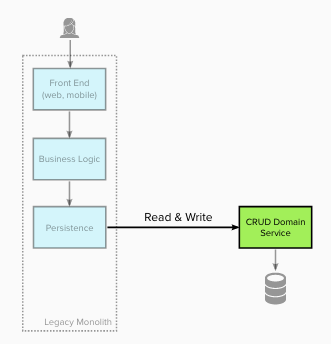
Legacy state
The diagram under exhibits the structure of the legacy
structure. The monolithic system’s
structure was primarily Presentation-Area-Knowledge Layers.
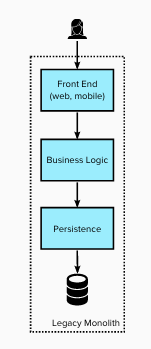
Stage 1 – Darkish launch service(s) for a single area
Firstly the group created a set of providers for a single enterprise area together with the potential for the info
uncovered by these providers to remain in sync with the legacy system.
The providers used Darkish Launching – i.e. not utilized by any customers, as a substitute the providers allowed the group to
validate that information migration and synchronisation achieved 100% parity with the legacy datastore.
The place there have been points with reconciliation checks, the group may purpose about, and repair them guaranteeing
consistency was achieved – with out enterprise affect.
The migration of historic information was achieved via a “single shot” information migration course of. While not strictly Occasion Interception, the continuing
synchronisation was achieved utilizing a Change Knowledge Seize (CDC) course of.
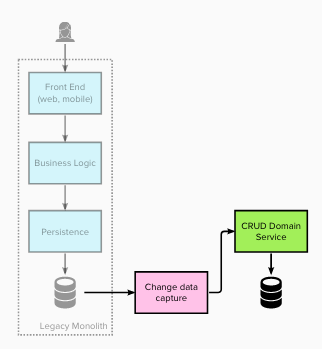
Stage 2 – Intercept all reads and redirect to the brand new service(s)
For stage 2 the group up to date the legacy Persistence Layer to intercept and redirect all of the learn operations (for this area) to
retrieve the info from the brand new area service(s). Write operations nonetheless utilised the legacy information retailer. That is
and instance of Department by Abstraction – the interface of the Persistence Layer stays unchanged and a brand new underlying implementation
put in place.
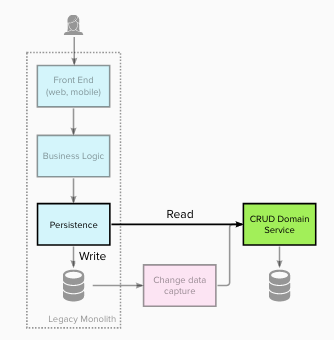
Stage 3 – Intercept all writes and redirect to the brand new service(s)
At stage 3 plenty of modifications occurred. Write operations (for the area) had been intercepted and redirected to create/replace/take away
information throughout the new area service(s).
This modification made the brand new area service the System of File for this information, because the legacy information retailer was now not up to date.
Any downstream utilization of that information, corresponding to studies, additionally needed to be migrated to turn out to be a part of or use the brand new
area service.
Stage 4 – Migrate area enterprise guidelines / logic to the brand new service(s)
At stage 4 enterprise logic was migrated into the brand new area providers (reworking them from anemic “information providers”
into true enterprise providers). The entrance finish remained unchanged, and was now utilizing a legacy facade which
redirected implementation to the brand new area service(s).