
Microsoft has added command-and-control (C2) visitors detection capabilities to its Microsoft Defender for Endpoint (MDE) enterprise endpoint safety platform.
Accessible in public preview in the meanwhile, this new MDE characteristic will permit safety admins to detect malware trying to speak with attacker-controlled servers on the community layer.
The C2 connections are detected by the Defender for Endpoint’s Community Safety (NP) agent by mapping the outbound connection’s IP tackle, port, hostname, and different values with information from Microsoft Cloud.
If the connection is evaluated as malicious by Microsoft’s cloud-powered AI and scoring engines, MDE will routinely block the connection and roll again the malware binaries to a earlier clear state.
After the malicious connection is detected, a “Community Safety blocked a possible C2 connection” alert can be added to the Microsoft 365 Defender portal, offering SecOps staff members with particulars, together with the severity degree and the impacted belongings, and the exercise timespan.
Extra data, such because the assault circulate and a full timeline, is obtainable after opening the C2 connection alert, as proven within the screenshot under.
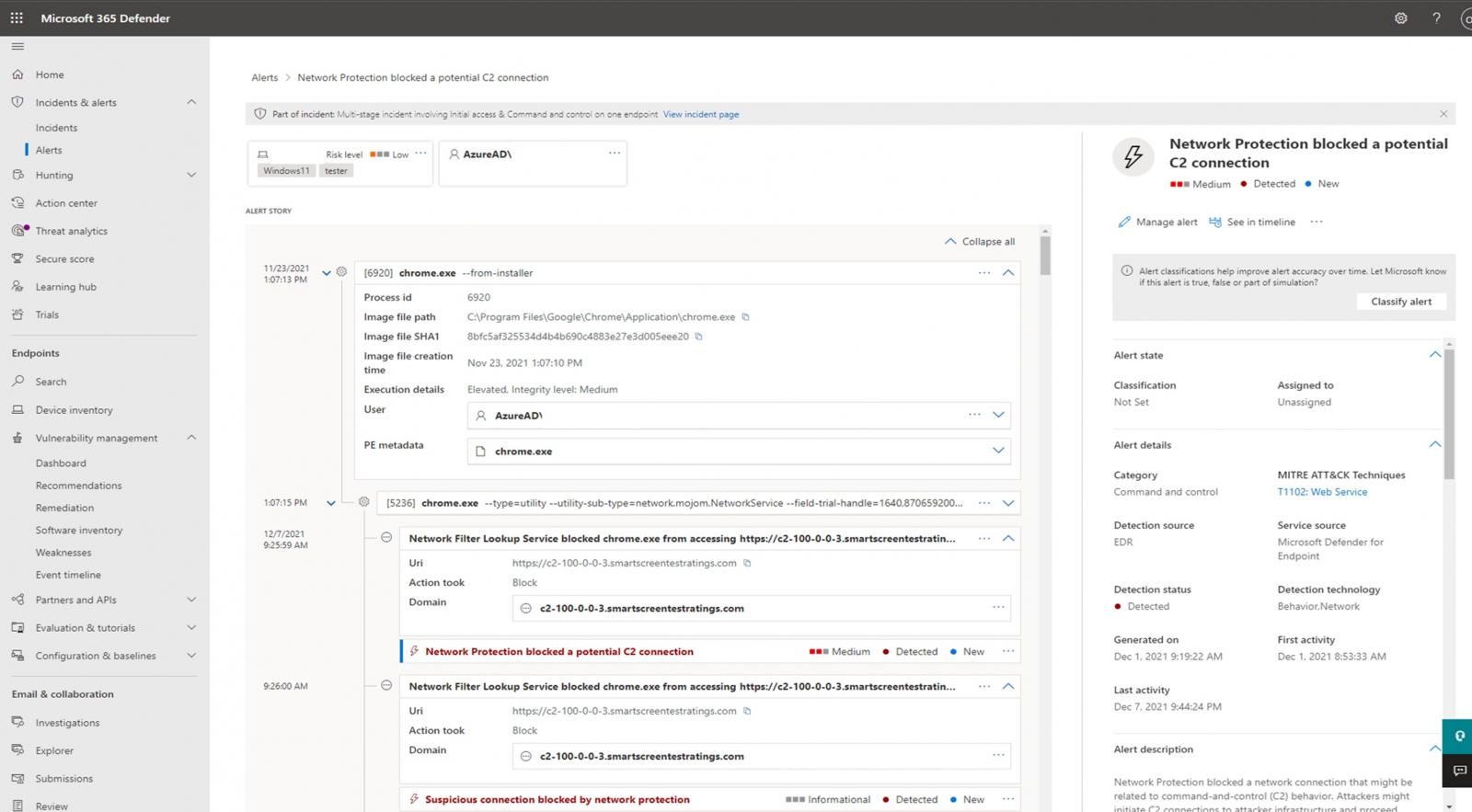
”SecOps groups want exact alerts that may precisely outline areas of compromise and former connections to identified malicious IPs,” MDE senior program supervisor Oludele Ogunrinde stated.
“With the brand new capabilities in Microsoft Defender for Endpoint, SecOps groups can detect community C2 assaults earlier within the assault chain, decrease the unfold by quickly blocking any additional assault propagation, and scale back the time it takes to mitigate by simply eradicating malicious binaries.”
The conditions embrace Microsoft Defender Antivirus with lively real-time safety and cloud-delivered safety, MDE in lively mode, community safety in block mode, and engine model 1.1.17300.4 or later put in.
It really works with each shopper (Home windows 10 model 1709 or later) and server (Home windows Server 1803, Home windows Server 2019 or later) platforms.
The brand new functionality can be progressively and routinely utilized in environments the place Community Safety (NP) is enabled when you’ve already signed up for the general public preview.
Final month, Microsoft additionally stated tamper safety would quickly be turned on by default in Microsoft Defender for Endpoint for higher protection in opposition to ransomware assaults.

