A brand new Android backdoor has been found with potent capabilities to hold out a spread of malicious actions on contaminated units.
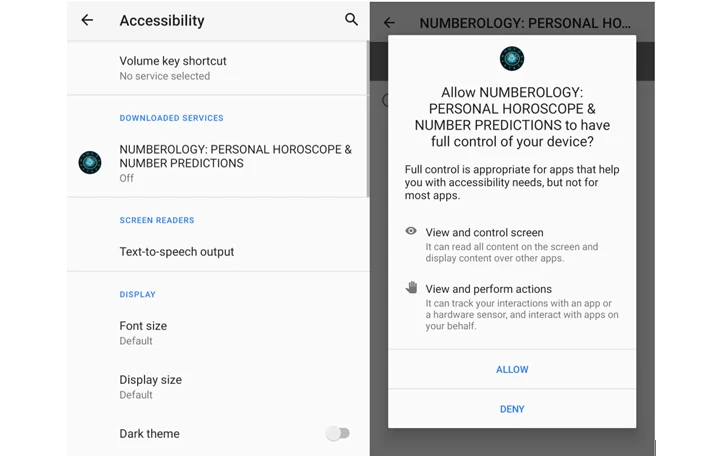
Dubbed Xamalicious by the McAfee Cellular Analysis Crew, the malware is so named for the truth that it is developed utilizing an open-source cellular app framework referred to as Xamarin and abuses the working system’s accessibility permissions to meet its goals.
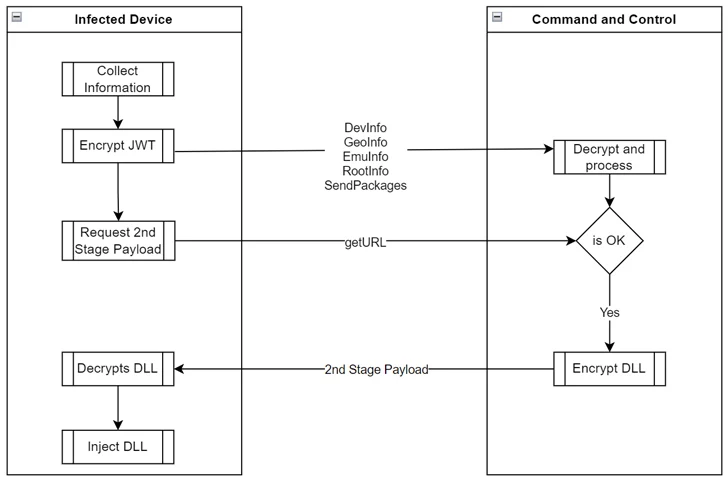
It is also able to gathering metadata in regards to the compromised gadget and contacting a command-and-control (C2) server to fetch a second-stage payload, however solely after figuring out if it suits the invoice.
The second stage is “dynamically injected as an meeting DLL at runtime degree to take full management of the gadget and probably carry out fraudulent actions equivalent to clicking on advertisements, putting in apps, amongst different actions financially motivated with out consumer consent,” safety researcher Fernando Ruiz stated.
The cybersecurity agency stated it recognized 25 apps that include this lively risk, a few of which had been distributed on the official Google Play Retailer since mid-2020. The apps are estimated to have been put in not less than 327,000 instances.
From USER to ADMIN: Be taught How Hackers Acquire Full Management
Uncover the key ways hackers use to grow to be admins, the right way to detect and block it earlier than it is too late. Register for our webinar right now.
A majority of the infections have been reported in Brazil, Argentina, the U.Okay., Australia, the U.S., Mexico, and different elements of Europe and the Americas. A number of the apps are listed under –
- Important Horoscope for Android (com.anomenforyou.essentialhoroscope)
- 3D Pores and skin Editor for PE Minecraft (com.littleray.skineditorforpeminecraft)
- Emblem Maker Professional (com.vyblystudio.dotslinkpuzzles)
- Auto Click on Repeater (com.autoclickrepeater.free)
- Depend Straightforward Calorie Calculator (com.lakhinstudio.counteasycaloriecalculator)
- Sound Quantity Extender (com.muranogames.easyworkoutsathome)
- LetterLink (com.regaliusgames.llinkgame)
- NUMEROLOGY: PERSONAL HOROSCOPE &NUMBER PREDICTIONS (com.Ushak.NPHOROSCOPENUMBER)
- Step Keeper: Straightforward Pedometer (com.browgames.stepkeepereasymeter)
- Monitor Your Sleep (com.shvetsStudio.trackYourSleep)
- Sound Quantity Booster (com.devapps.soundvolumebooster)
- Astrological Navigator: Each day Horoscope & Tarot (com.Osinko.HoroscopeTaro)
- Common Calculator (com.Potap64.universalcalculator)
Xamalicious, which usually masquerades as well being, video games, horoscope, and productiveness apps, is the newest in a lengthy listing of malware households that abuse Android’s accessibility companies, requesting customers’ entry to it upon set up to hold out its duties.
“To evade evaluation and detection, malware authors encrypted all communication and knowledge transmitted between the C2 and the contaminated gadget, not solely protected by HTTPS, it is encrypted as a JSON Internet Encryption (JWE) token utilizing RSA-OAEP with a 128CBC-HS256 algorithm,” Ruiz famous.
Much more troublingly, the first-stage dropper incorporates features to self-update the primary Android package deal (APK) file, that means it may be weaponized to behave as spy ware or banking trojan with none consumer interplay.
McAfee stated it recognized a hyperlink between Xamalicious and an ad-fraud app named Money Magnet, which facilitates app obtain and automatic clicker exercise to illicitly earn income by clicking on advertisements.
“Android functions written in non-java code with frameworks equivalent to Flutter, react native and Xamarin can present an extra layer of obfuscation to malware authors that deliberately choose these instruments to keep away from detection and attempt to keep underneath the radar of safety distributors and maintain their presence on apps markets,” Ruiz stated.
Android Phishing Marketing campaign Targets India With Banker Malware
The disclosure comes because the cybersecurity firm detailed a phishing marketing campaign that employs social messaging apps like WhatsApp to distribute rogue APK recordsdata that impersonate official banks such because the State Financial institution of India (SBI) and immediate the consumer to put in them to finish a compulsory Know Your Buyer (KYC) process.
As soon as put in, the app asks the consumer to grant it SMS-related permissions and redirects to a pretend web page that solely captures the sufferer’s credentials but additionally their account, credit score/debit card, and nationwide id info.
The harvested knowledge, alongside the intercepted SMS messages, are forwarded to an actor-controlled server, thereby permitting the adversary to finish unauthorized transactions.
It is price noting that Microsoft final month warned of an identical marketing campaign that makes use of WhatsApp and Telegram as distribution vectors to focus on Indian on-line banking customers.
“India underscores the acute risk posed by this banking malware inside the nation’s digital panorama, with a couple of hits discovered elsewhere on the earth, presumably from Indian SBI customers residing in different international locations,” researchers Neil Tyagi and Ruiz stated.