The risk actor generally known as UAC-0099 has been linked to continued assaults aimed toward Ukraine, a few of which leverage a high-severity flaw within the WinRAR software program to ship a malware pressure referred to as LONEPAGE.
“The risk actor targets Ukrainian workers working for firms exterior of Ukraine,” cybersecurity agency Deep Intuition mentioned in a Thursday evaluation.
UAC-0099 was first documented by the Laptop Emergency Response Crew of Ukraine (CERT-UA) in June 2023, detailing its assaults in opposition to state organizations and media entities for espionage motives.
Beat AI-Powered Threats with Zero Belief – Webinar for Safety Professionals
Conventional safety measures will not reduce it in as we speak’s world. It is time for Zero Belief Safety. Safe your information like by no means earlier than.
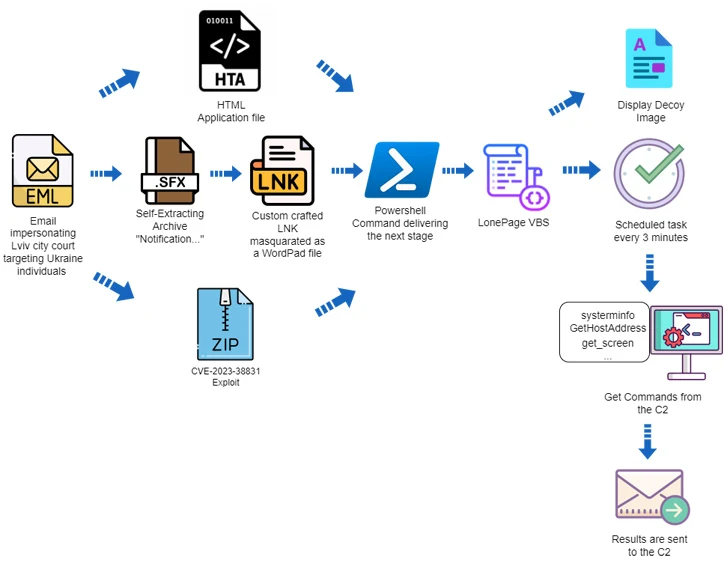
The assault chains leveraged phishing messages containing HTA, RAR, and LNK file attachments that led to the deployment of LONEPAGE, a Visible Fundamental Script (VBS) malware that is able to contacting a command-and-control (C2) server to retrieve further payloads equivalent to keyloggers, stealers, and screenshot malware.
“Throughout 2022-2023, the talked about group acquired unauthorized distant entry to a number of dozen computer systems in Ukraine,” CERT-UA mentioned on the time.
The newest evaluation from Deep Intuition reveals that using HTA attachments is only one of three completely different an infection chains, the opposite two of which leverage self-extracting (SFX) archives and bobby-trapped ZIP recordsdata. The ZIP recordsdata exploit the WinRAR vulnerability (CVE-2023-38831, CVSS rating: 7.8) to distribute LONEPAGE.
Within the former, the SFX file homes an LNK shortcut that is disguised as a DOCX file for a court docket summons whereas utilizing the icon for Microsoft WordPad to entice the sufferer into opening it, ensuing within the execution of malicious PowerShell code that drops the LONEPAGE malware.
The opposite assault sequence makes use of a specifically crafted ZIP archive that is inclined to CVE-2023-38831, with Deep Intuition discovering two such artifacts created by UAC-0099 on August 5, 2023, three days after WinRAR maintainers launched a patch for the bug.
“The techniques utilized by ‘UAC-0099’ are easy, but efficient,” the corporate mentioned. “Regardless of the completely different preliminary an infection vectors, the core an infection is identical — they depend on PowerShell and the creation of a scheduled job that executes a VBS file.”
The event comes as CERT-UA warned of a brand new wave of phishing messages purporting to be excellent Kyivstar dues to propagate a distant entry trojan generally known as Remcos RAT. The company attributed the marketing campaign to UAC-0050.