Coordinated vulnerability disclosure (CVD) begins when a minimum of one particular person turns into conscious of a vulnerability. It might’t proceed, nevertheless, with out the cooperation of many. Software program provide chains, software program libraries, and part vulnerabilities have advanced in complexity and have grow to be as a lot part of the CVD course of as vulnerabilities in distributors’ proprietary code. Many CVD instances now require coordination throughout a number of distributors. This put up, which relies on a just lately printed particular report, introduces Vultron, a protocol for multi-party coordinated vulnerability disclosure (MPCVD).
Foundations in Coordinated Vulnerability Disclosure
Since releasing our first advisory in 1988, CERT/CC has sought to enhance the professionalization of the world’s CVD practices. Drawing on work throughout the a long time, our method has been to distill and formalize what we find out about this course of. This work grew out of quite a few advert hoc particular person efforts to teach software program distributors and the safety analysis group as they engaged our companies in coordinating, analyzing, and publishing vulnerability stories, together with the next:
Along with our personal efforts, we now have additionally participated in (and at occasions led) the event of associated ISO/IEC requirements round vulnerability disclosure, together with
- ISO/IEC 29147:2018 Data know-how—Safety strategies—Vulnerability disclosure
- ISO/IEC 30111:2019 Data know-how—Safety strategies—Vulnerability dealing with processes
The Vultron Protocol
In September 2022, we launched Vultron, a proposed protocol for MPCVD. The total report, Designing Vultron: A Protocol for Multi-Social gathering Coordinated Vulnerability Disclosure (MPCVD), describes a high-level protocol that we consider supplies a basis for course of interoperability amongst CVD stakeholders and factors the best way towards technical implementation in instruments like VINCE and different CVD service platforms.
Whereas I’ve led efforts to develop the Vultron protocol, it represents solely a bit of a broader effort to enhance CVD practices. The report wouldn’t have been attainable with out ongoing dialogue with my CERT Division colleagues together with Eric Hatleback, Artwork Manion, Brad Runyon, Vijay Sarvepalli, Sam Perl, Jonathan Spring, Laurie Tyzenhaus, and Chuck Yarbrough.
The Vultron protocol begins with semantic interoperability as a result of CVD individuals have to first agree on what they imply once they discuss their processes. No quantity of syntactic interoperability (e.g., information alternate format specs or APIs) will help if the interpretation of that information differs for the sender and the receiver. The Vultron protocol is designed to deal with each CVD and MPCVD instances. In reality, the protocol doesn’t discriminate between them; it merely treats “regular” CVD as a particular case of MPCVD through which the variety of distributors is 1.
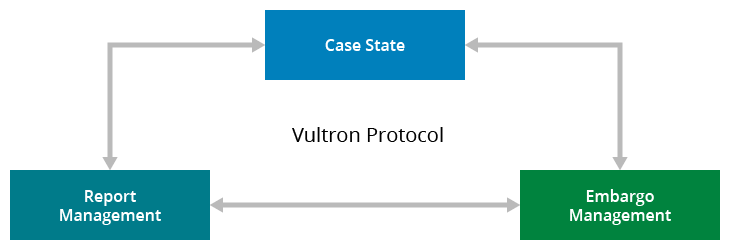
Particularly, the Vultron protocol is constructed round three distinct however interacting processes, which we describe within the report as deterministic finite automata (DFAs):
- Report administration—A course of rooted in IT service administration (ITSM) that describes a high-level workflow by which particular person CVD case individuals can deal with and observe stories from preliminary receipt by means of validation, prioritization, and work completion.
- Embargo administration—A course of based mostly on calendaring and schedule coordination that comprises a workflow for proposing, accepting, revising, and exiting a interval of personal coordination previous to public disclosure of vulnerability info. Embargoes in CVD are supposed to offer a chance to permit the distributors of affected merchandise ample time to arrange a repair or mitigation recommendation previous to public consciousness of the vulnerability in query.
- Case state—A course of that describes the lifecycle of a CVD case by means of its main milestones: vendor consciousness, repair prepared, repair deployed, public consciousness, exploit public, and assaults noticed. We described this mannequin beforehand in “Are We Skillful or Simply Fortunate? Deciphering the Potential Histories of Vulnerability Disclosures” and expanded the concept in our 2021 particular report.
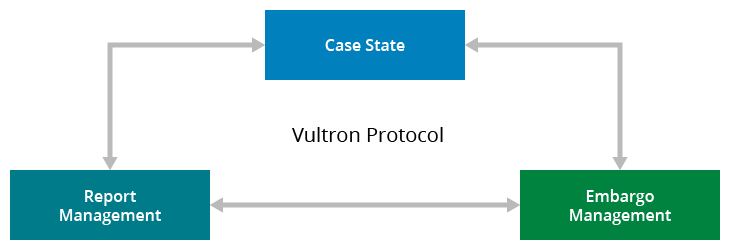
Determine 1: Three processes (case state, embargo administration, and report administration) work together to type the Vultron Protocol.
The Vultron protocol encompasses each native and world points of the CVD course of. For instance, whereas the report administration course of is native to a particular case participant, the embargo administration course of is predicted to be shared throughout all case individuals. Equally, parts of the case state mannequin are world to the case, whereas others are particular to particular person individuals. Our intent, nevertheless, is to depart loads of room for stakeholders to implement their very own inside processes to go well with their particular person wants. Our aim with the Vultron protocol is to offer a set of related abstractions to map numerous organizations’ inside processes onto a generalized workflow that promotes coordination of effort and improves the communication of case standing throughout stakeholders.
Our report on Vultron contains detailed commentary on how the Vultron protocol is perhaps carried out and descriptions future work. Appendices are supplied that map the Vultron protocol onto current work together with SSVC v2, ISO/IEC 30111:2019, ISO/IEC 29147:2018, and ISO/IEC TR 5895:2022 (Cybersecurity—Multi-party coordinated vulnerability disclosure and dealing with).
And sure, followers of a sure colourful anime big mecha composed of 5 discrete robots with human pilots may observe greater than a passing metaphor in the concept it takes a cooperative and coordinated effort for a posh human/machine partnership to realize some defensive objectives.
The place Do We Go Subsequent?
Though we now have executed some inside proof-of-concept growth to discover points of the Vultron protocol, it has not been absolutely carried out but. Nor have we accomplished our evaluation of its properties. As a result of measurement and scope of what we expect it would grow to be, nevertheless, we wished to share it now as a proposal so we are able to start growing a group of curiosity amongst related stakeholders, together with, however not restricted to
- software program distributors and PSIRTs
- safety researchers
- CSIRTs and different third-party coordinators
- vulnerability disclosure and bug bounty platform suppliers
When you can anticipate to listen to extra from us concerning the Vultron protocol sooner or later, we’re taken with your suggestions on the protocol we now have proposed within the report. Some questions to contemplate in your suggestions embody the next:
- With the proviso that all fashions are flawed however some are helpful, how can we make the Vultron protocol extra helpful to your CVD observe?
- What did we miss?
- What could possibly be clearer?
- Do you’ve essential edge instances you suppose we must always contemplate?
- What assumptions did we make that you simply disagree with or discover questionable or odd within the context of your personal surroundings and expertise?
Additionally, as a result of Vultron touches on each the human course of and technical work of CVD, we anticipate that future work shall be wanted to combine Vultron into higher-level vendor processes, reminiscent of these described within the FIRST PSIRT Providers Framework.
Lastly, we acknowledge that the Vultron protocol effort will ultimately want to handle syntactic interoperability, reminiscent of message and information alternate codecs. We anticipate that this exercise will take some type of engagement with related efforts, such because the Frequent Safety Advisory Framework (CSAF), Open Supply Vulnerability Format, and varied CVE working teams such because the Automation Working Group (AWG).
It’s not our intent to supplant current format work. In reality, our desire is for Vultron to ultimately accommodate quite a lot of vulnerability information alternate codecs. Whereas we respect that incident and malware information alternate codecs exist and are associated to vulnerability information alternate, we’re primarily taken with vulnerability-specific codecs for now. In case you are conscious of energetic vulnerability information alternate format efforts that we haven’t talked about right here, please tell us.