Ransomware is among the most vital threats dealing with organizations immediately. Battling it’s no simple job, notably on condition that risk actors are regularly refining their strategies and approaches. Latest shifts, for instance, embrace tweaks to ransomware-as-a-service (RaaS) fashions; the adoption of latest programming languages; evolutions in concentrating on and deployment; and more and more launching assaults after enterprise hours and at weekends to hinder detection and incident response efforts.
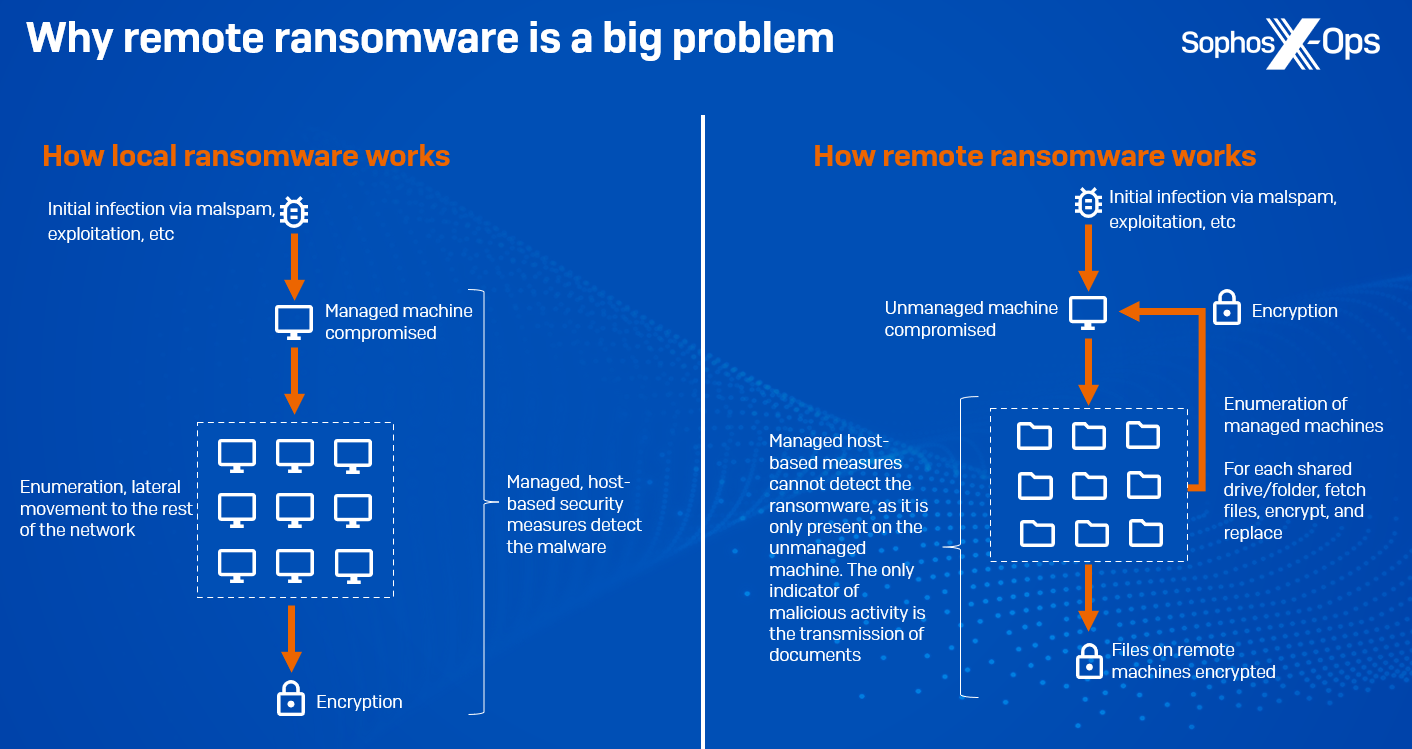
One of many extra substantial developments is a rise in distant ransomware: leveraging a company’s area structure to encrypt knowledge on managed domain-joined machines. All of the malicious exercise – ingress, payload execution, and encryption – happens on an unmanaged machine, due to this fact bypassing trendy safety stacks, with the one indication of compromise being the transmission of paperwork to and from different machines. Our telemetry signifies that there was a 62% year-on-year enhance in intentional distant encryption assaults since 2022. And Microsoft’s 2023 Digital Protection Report states that round 60% of human-operated ransomware assaults contain distant encryption, with 80% of all compromises originating from unmanaged gadgets, indicating an absence of lively asset administration. Ransomware households recognized to assist distant encryption embrace Akira, ALPHV/BlackCat, BlackMatter, LockBit, and Royal, and it’s a method that’s been round for a while – way back to 2013, CryptoLocker was concentrating on community shares.
Determine 1: A simplified rationalization of how distant ransomware works
Unsurprisingly, the rise and persevering with improvement of ransomware has led to a plethora of analysis geared toward detecting and stopping it – with teachers, safety researchers, and distributors all proposing varied options. Ransomware, as a type of malware, presents distinctive sensible and mental challenges, and the vary of options displays this. Many such options goal a number of of ransomware’s distinct behavioral traits: enumerating filesystems, accessing and encrypting recordsdata, and producing ransom notes. Others are extra generic, making use of widespread anti-malware strategies to ransomware.
On this, the second challenge of our new technical thought management collection (the primary, on reminiscence scanning, is offered right here), we’ll present a short overview of a few of these strategies and their benefits and downsides, earlier than taking an in-depth have a look at our personal contribution to the sphere: CryptoGuard.
Earlier than we begin, one factor to notice: a ransomware assault has a number of phases, and nearly all of these will happen earlier than the options we focus on on this article come into play. A well-defended enterprise can have a number of layers of safety which ought to cease assaults at varied factors, that means that in lots of circumstances particular anti-ransomware options shouldn’t be required. However when all else fails, and a decided adversary reaches the encryption stage, we’d like a know-how to stop irreparable harm. Different phases of an assault – preliminary an infection, persistence, lateral motion, and so forth – are reversible, however encryption is just not.
Anti-ransomware strategies
Static options
Static strategies (i.e., these which might be carried out passively, with out requiring execution of the malware) for ransomware detection usually are not markedly totally different from these used to detect another type of malware. Options on this vein embrace signature-matching, evaluating strings; evaluating file operations; inspecting behavioral traits; deep studying strategies; and inspecting PE headers.
Whereas static strategies have the benefit of being comparatively speedy and low-cost, decided attackers may evade them by modifying code till signature detections are damaged. They’re additionally much less efficient towards new variants, packers, obfuscators, and in-memory threats, in addition to distant ransomware.
Dynamic options
Dynamic options, however, are usually extra computationally costly, however provide better protection. Dynamic anti-ransomware options on this vein embrace the next:
Filesystem interactions
Some safety options will monitor for modifications to file extensions, high-frequency learn/write and renaming operations, or new recordsdata which have extensions related to ransomware variants. However, some options leverage different interactions; the open-source venture Raccine, for instance, is predicated on the premise that many ransomware variants delete shadow copies utilizing vssadmin. Raccine works by intercepting requests to vssadmin and killing the method accountable.
Since ransomware targets recordsdata, it appears logical that quite a few approaches ought to deal with filesystem interactions. Nevertheless, lots of them are reliant on evaluation inside a sandboxed atmosphere; are predicated on anomalous patterns which risk actors could attempt to keep away from producing; or might be resource-intensive because of the quantity of monitoring concerned (though it’s attainable to dynamically adapt the diploma of monitoring) Some filesystem-based strategies may additionally not be efficient relating to distant ransomware.
Folder shielding
Whereas options like Managed Folder Entry (CAF) in Home windows Defender restrict entry to folders to particular functions, such an strategy is primarily geared in the direction of particular person customers. CAF helps shield towards ransomware by proscribing unauthorized entry to designated folders, permitting solely trusted functions to change recordsdata inside them. Nevertheless, for enterprise networks, this technique could also be much less sensible because of the ongoing want for meticulous administration of folders and functions. Moreover, it doesn’t handle the chance of assaults seizing management of trusted apps, a prevalent tactic in ransomware assaults
API calls
Some safety options will assess API calls invoked by a course of, both by flagging suspicious and seldom-seen calls or by figuring out probably malicious name sequences.
Most ransomware employs API calls, though some variants use evasive measures to disguise these (notably for API calls that are recognized to be suspicious, similar to CreateRemoteThread or VirtualAllocEx, generally utilized in course of injection; or API calls associated to encryption). Monitoring API calls on the kernel stage actually appears to be a worthwhile strategy, however such monitoring is resource-intensive, can generate false positives, and is difficult to implement at scale. Moreover, relating to distant ransomware, the method itself might not be on the host being attacked, which may frustrate this strategy.
Honeyfiles
Many safety merchandise make use of ‘honeyfiles’, ‘decoy recordsdata’, ‘bait recordsdata’, or ‘canary recordsdata’ as an anti-ransomware resolution – inconspicuous recordsdata that are positioned in a listing and which official customers are requested to not contact. A separate monitoring system, both on the user-level or the kernel-level, is triggered if these recordsdata are accessed or modified by any course of, at which level an alert is generated.
Honeyfiles are light-weight, low-effort, and may present an early warning that an assault could also be in progress. Nevertheless, they do include some caveats. Defenders should be certain that any alert is acquired and acted upon shortly sufficient, as by design an assault will already be in progress when a honeyfile is triggered. In addition they need to be strategically positioned – deep sufficient inside filesystems to make sure that regular, official customers and processes gained’t by accident journey them, however not so deep that essential paperwork are encrypted earlier than they’re accessed.
Fingerprinting
A much less widespread approach is to ‘fingerprint’ sure malicious patterns – in community (C2) visitors, CPU consumption, or CPU alerts.
Close to community visitors, it’s value noting that in trendy human-led ransomware assaults, risk actors tailor and compile the ransomware binary uniquely for every sufferer, a strategic transfer supposed to impede detection and complicate the decryption course of. This practice-built ransomware sometimes accommodates a victim-specific ransom be aware and is deployed in a ‘fire-and-forget’ method, omitting the necessity for direct communication again to the risk actor, because the encryption course of is self-contained inside the malware, leveraging a victim-specific embedded public key.
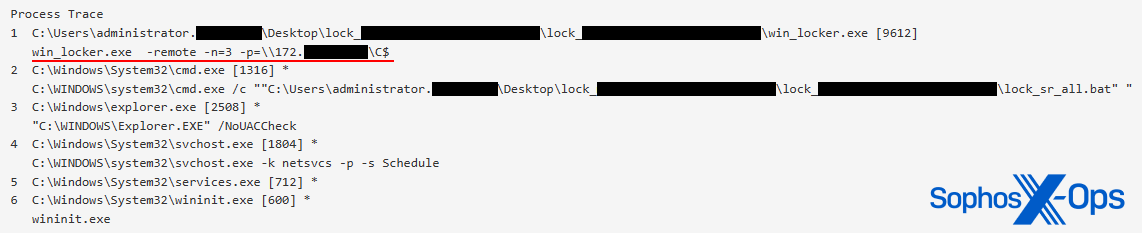
An rising know-how from Intel known as TDT (Menace Detection Know-how) provides the flexibility to detect ransomware on the {hardware} stage. A evaluate by SE Labs demonstrates a exceptional effectiveness towards a various array of encryption schemes. Nevertheless, that is confined to particular Intel CPUs, excluding ARM and AMD architectures. This limitation stems from TDT’s reliance on a machine studying mannequin educated on CPU efficiency alerts from particular ransomware households’ encryption profiles. The mannequin, educated by Intel, relies on vendor assist and doesn’t work with distant encryption. An obstacle of this know-how is that some ransomware strains, similar to LockBit and Akira, are intentionally configured to encrypt solely a portion of every file. This accelerates the influence of the assault, affecting extra recordsdata in much less time. It additionally signifies that detection by Intel TDT happens after a big variety of recordsdata have already been compromised.
Determine 2: Akira ransomware, particularly attacking solely distant knowledge, and encrypting solely 3% of every file
Automated telemetry-driven containment
Most trendy endpoint safety options transmit knowledge to the cloud for incident response and alert evaluation. Nevertheless, mechanically piecing collectively the small print of an lively human-led ransomware assault from alert telemetry can take anyplace from a couple of minutes to a number of hours. This latency depends upon the configured telemetry reporting frequency, the presence of different alert alerts, and the cloud’s processing capability to assemble and correlate particular occasions from a number of protected machines.
Following detection, an automatic response can contain deploying a containment coverage to managed gadgets, to isolate a particular consumer account suspected of compromise by the attacker. Whereas this motion goals to stop an imminent or ongoing (distant) ransomware encryption assault originating from the recognized account, you will need to be aware that the distribution of this coverage additionally requires time (as much as hours). Furthermore, in situations the place the attacker begins encryption with out triggering prior alerts on managed machines (as famous above, 80% of assaults contain unmanaged machines) or opts to start the encryption course of from an alternate consumer account, the situations don’t at all times favour an efficient cloud-driven dynamic containment technique. However it may be useful in some situations.
Rollback
Usually, dynamic anti-ransomware options generally require some stage of encryption or knowledge manipulation to have taken place earlier than detecting the assault. Consequently, a sure variety of recordsdata will seemingly develop into encrypted, necessitating a backup and restore perform to get well affected recordsdata.
To revert unencrypted file variations, some endpoint safety merchandise leverage Quantity Shadow Copies, a Home windows function that generates knowledge snapshots at particular time factors. These ‘shadow copies’ seize file or quantity states, even whereas they’re in use. Nonetheless, this technique has its limitations: attackers generally delete the shadow copies; they don’t shield recordsdata on community mapped drives; and efficient rollback depends on detecting and addressing the ransomware incident earlier than the next scheduled snapshot (which generally happens each 4 hours). And, as famous beforehand, most assaults occur after workplace hours, which may complicate restoration makes an attempt utilizing this technique.
Abstract
Usually, many of those approaches deal with on the lookout for ‘badness’: characterizing and figuring out behavioral traits that are indicative of ransomware exercise. Whereas this looks like a rational determination, it does have an important weak point, in that risk actors have an incentive to disguise or obfuscate these traits and due to this fact evade detection. CryptoGuard, however, takes a distinct strategy.
CryptoGuard
CryptoGuard – previously often called HitmanPro.Alert, and a part of Intercept X since 2016 – was first developed in 2013, and is meant to be a final layer of defence towards each native and distant ransomware, when decided risk actors have evaded all different protections and are ready to start encryption. Its notable successes embrace blocking WannaCry, LockBit, and REvil ransomware. Whereas we preserve a really watchful eye on developments within the ransomware area, CryptoGuard hasn’t modified considerably through the years, primarily as a result of it hasn’t wanted to.
An uneven strategy
Not like nearly all of the approaches described above, CryptoGuard doesn’t search for attackers, ransomware executables, or malicious behavioral patterns in any respect. Different safety options, together with Sophos merchandise, do these items, after all – it’s a elementary a part of a layered defence, which ideally prevents attackers from attending to the encryption stage – however CryptoGuard itself employs a extra uneven strategy, for when these layers have been circumvented.
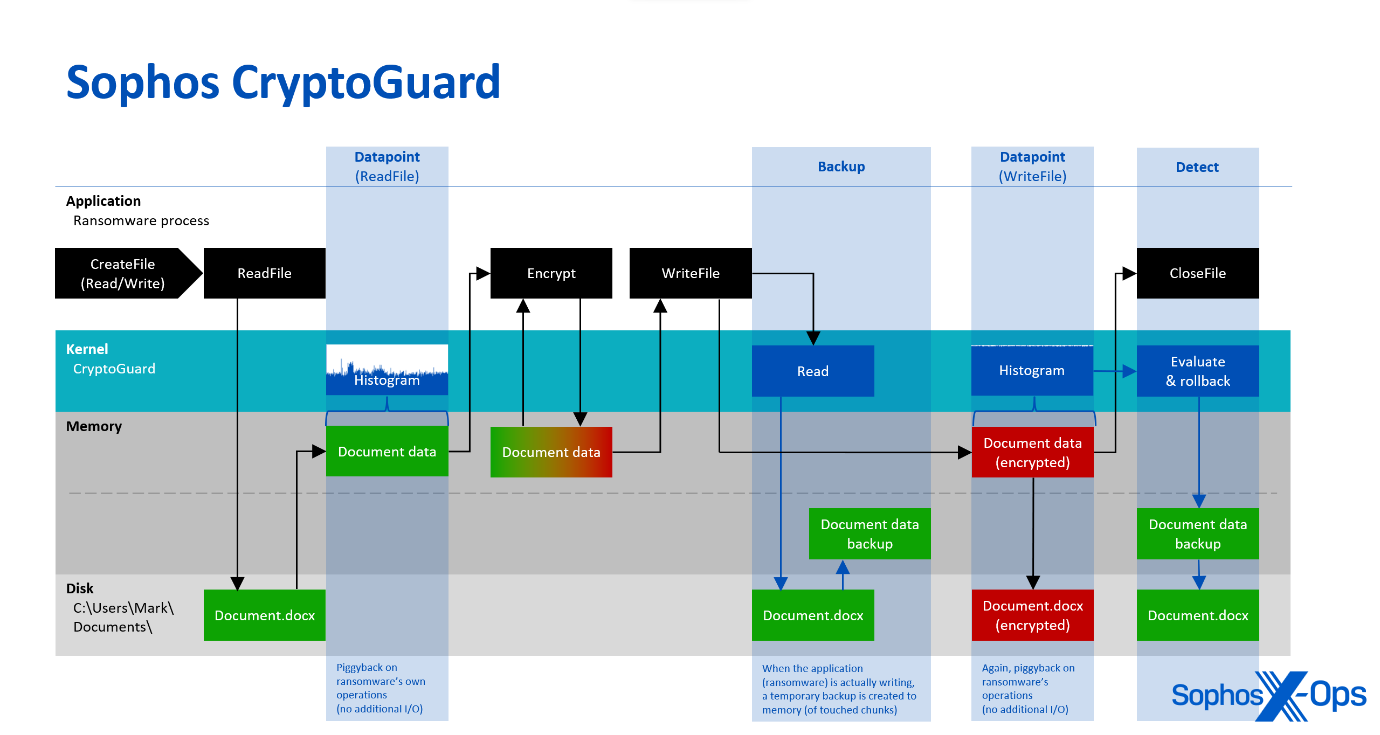
Reasonably than on the lookout for ‘badness,’ CryptoGuard focuses on the contents of recordsdata, by analyzing their patterns with a mathematical algorithm. At any time when a course of opens a file for studying and writing, CryptoGuard’s minifilter driver – which operates inside the Home windows working system kernel – constantly generates histograms of the learn and written knowledge. These histograms serve to know the general sample and traits of the info. They endure analysis to find out their entropy and statistically analyze whether or not the learn and written knowledge is unencrypted, compressed, or encrypted. The built-in evaluators make use of mathematical fashions to categorise knowledge. For the reason that evaluation makes use of the identical reminiscence buffers supplied by the working system for the requesting course of, it is vitally environment friendly because it doesn’t trigger extra disk enter/output (I/O).
Determine 3: An summary of CryptoGuard’s operations
This functionality offers uneven safety, even in situations the place an unprotected distant machine on the community is attacking shared paperwork on a Sophos-protected file server, for instance. As famous above, most human-led ransomware assaults goal to additionally encrypt shared knowledge on distant machines. In such circumstances, the ransomware itself is just not executed on the protected distant machine (both as a result of it wasn’t deployed there by the attacker or was blocked by endpoint safety). In consequence, the ransomware binary itself or the attacker-controlled course of (that performs the encryption) can’t be noticed from the machine that holds the focused knowledge.
So, as a result of there is no such thing as a malicious code to be detected on the attacked machine, applied sciences like antivirus, machine studying, indicators of breach, and so on.—all targeted on figuring out adversaries and their malicious code—are utterly sidelined and never in play (even when it’s a well-known years-old pattern accountable for the encryption). Nevertheless, CryptoGuard can acknowledge when a distant machine replaces paperwork within the shared folder with encrypted variations, and mechanically takes motion by blocking the IP handle of the distant machine and reversing the modifications it made. It creates short-term backups of any modified recordsdata, in order that the modifications might be rolled again if mass encryption is detected, and may detect the deployment of ransom notes inside the folders the place the ransomware has encrypted recordsdata. Consequently, it typically identifies situations of information exfiltration, though it was not explicitly designed for that goal.
Zero-trust
Adversaries will typically abuse an current course of, or package deal a usually benign course of that masses a malicious DLL (often called DLL side-loading), as a way to carry out encryption. The encryption exercise is carried out below the id of the benign course of, now working attacker-code, and encrypting paperwork.
An actual-world instance of that is the Kaseya VSA incident, the place the REvil risk actor embedded a malicious DLL to be side-loaded in an outdated however susceptible Home windows Defender executable. The risk actor purposely selected Defender, as a result of protections sometimes belief code signed by Microsoft. Moreover, a DLL can’t be examined as totally as an executable in a sandbox atmosphere, that means it might be ‘accepted’ sooner.
On that event, Sophos detected each the REvil payload itself, in addition to an REvil-specific code certificates. And whereas Kayesa’s safety exclusions allowed the REvil dropper to be put in on machines, CryptoGuard detected the ransomware, as a result of it’s not constrained by such exclusions and blocks file encryption anyplace on protected drives.
A walkthrough
Conclusion
There isn’t any panacea relating to battling ransomware. An efficient defence ought to embrace a myriad of layers, from vulnerability remediation and configuration critiques to consumer schooling and safety options. However, no matter which layers organizations make use of, and what number of, an essential facet to think about is the robustness and effectiveness of the final layer, when all different measures have failed and risk actors are ready to execute their ransomware. At that time, the options we’ve coated right here come into their very own.
These options are numerous, masking quite a few totally different behavioral traits and exercise. Many range broadly when it comes to their scalability, versatility, and cost-benefit ratios, and have distinct strengths and weaknesses. A key commonality is that almost all options deal with ‘detecting badness’ not directly – whether or not by means of API name evaluation, honeyfiles, or some form of fingerprinting. That’s not essentially an obstacle, and a layered and numerous defence stack is a stable strategy. However, as we’ve proven, the CryptoGuard strategy inside Intercept X is barely totally different, and extra uneven: specializing in file contents relatively than the behaviors of ransomware or its operators.
Ransomware continues to evolve, and an increasing number of options and strategies are more likely to seem in response. As we’ve been doing for the final ten years, we’ll proceed to trace modifications in each ransomware and the options designed to detect and stop it.