A brand new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is getting used as a covert knowledge switch community for superior persistent menace actors, together with the China-linked menace actor known as Volt Storm.
Dubbed KV-botnet by the Black Lotus Labs group at Lumen Applied sciences, the malicious community is an amalgamation of two complementary exercise clusters which were energetic since a minimum of February 2022.
“The marketing campaign infects units on the fringe of networks, a section that has emerged as a mushy spot within the defensive array of many enterprises, compounded by the shift to distant work lately,” the corporate mentioned.
Beat AI-Powered Threats with Zero Belief – Webinar for Safety Professionals
Conventional safety measures will not minimize it in at present’s world. It is time for Zero Belief Safety. Safe your knowledge like by no means earlier than.
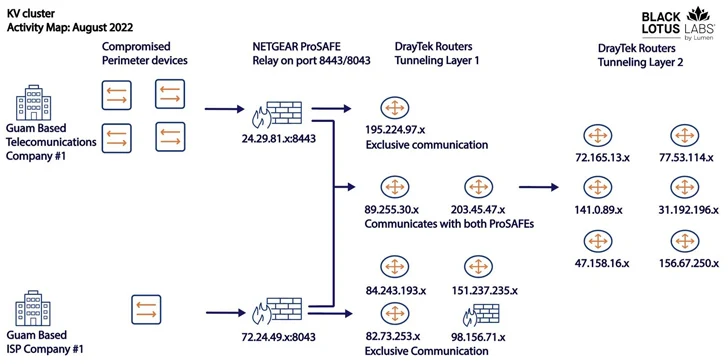
The 2 clusters – codenamed KY and JDY – are mentioned to be distinct but working in tandem to facilitate entry to high-profile victims in addition to set up covert infrastructure. Telemetry knowledge means that the botnet is commandeered from IP addresses based mostly in China.
Whereas the bots a part of JDY engages in broader scanning utilizing much less refined strategies, the KY element, that includes largely outdated and end-of-life merchandise, is assessed to be reserved for guide operations towards high-profile targets chosen by the previous.
It is suspected that Volt Storm is a minimum of one consumer of the KV-botnet and it encompasses a subset of their operational infrastructure, which is evidenced by the noticeable decline in operations in June and early July 2023, coinciding with the general public disclosure of the adversarial collective’s focusing on of important infrastructure within the U.S.
Microsoft, which first uncovered the menace actor’s ways, mentioned it “tries to mix into regular community exercise by routing site visitors by compromised small workplace and residential workplace (SOHO) community gear, together with routers, firewalls, and VPN {hardware}.”
The precise preliminary an infection mechanism course of used to breach the units is presently unknown. It is adopted by the first-stage malware taking steps to take away safety packages and different malware strains in order to make sure that it is the “solely presence” on these machines.
It is also designed to retrieve the principle payload from a distant server, which, along with beaconing again to the identical server, can be able to importing and downloading information, operating instructions, and executing extra modules.
Over the previous month, the botnet’s infrastructure has obtained a facelift, focusing on Axis IP cameras, indicating that the operators may very well be gearing up for a brand new wave of assaults.
“One of many somewhat attention-grabbing features of this marketing campaign is that each one the tooling seems to reside fully in-memory,” the researchers mentioned. “This makes detection extraordinarily tough, at the price of long-term persistence.”
“Because the malware resides fully in-memory, by merely power-cycling the machine the tip consumer can stop the an infection. Whereas that removes the approaching menace, re-infection is going on commonly.”