Scams
The AI race is on! It’s straightforward to lose observe of the most recent developments and potentialities, and but everybody needs to see firsthand what the hype is about. Heydays for cybercriminals!
21 Aug 2023
•
,
4 min. learn

My first “huh?” second was that the shortened URL didn’t embody any Google reference however quite a hyperlink to rebrand.ly – a service with no apparent ties to Google and with places of work in Dublin, Eire. It appeared odd for an web large to be utilizing the providers of one other supplier and my suspicion was triggered. I then re-read the textual content of the commercial and though I’m not a local English speaker, I discovered it laborious to imagine that nobody appeared to have proofread that quite complicated content material.
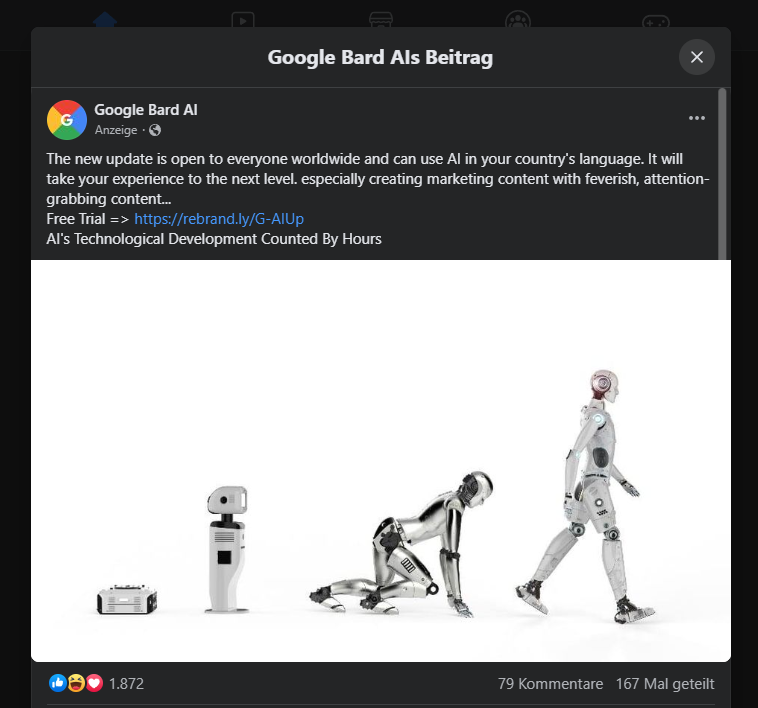
Did you say “Bots”?
I then proceeded to test the feedback part beneath the advert in pursuit of hints in the direction of doable fraud, however to my (little) shock, all of them appeared to like “the app”. Referring to only “the app” appeared quite common, whereas others praised the “AI”, by no means mentioning Google in any respect. Some have been giving “a 5 Star score” (sic) – in a remark part?! One way or the other, miraculously, it appeared like everybody within the feedback had downloaded and examined the app on the identical time, solely to be writing their feedback at precisely the identical second – which in my case was “6 hours in the past” – solely including as much as my suspicions.
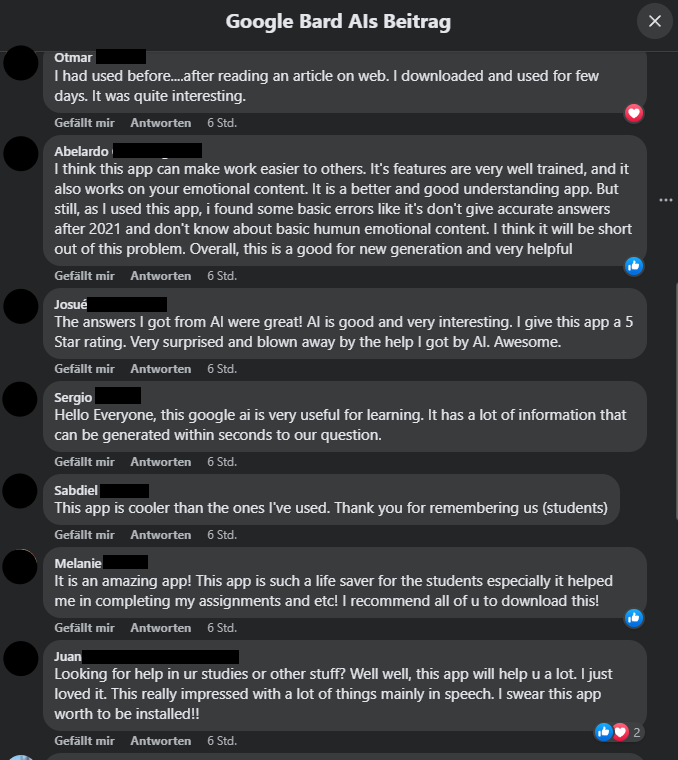
Following the path
I selected to fireside up my protected surroundings to analyze slightly additional. First, I checked the rebrandly-Hyperlink at VirusTotal, which was flagged as malicious by 3/90 distributors. This can be a first indicator, however no proof in any respect, as this may increasingly even be a false optimistic.
So I went for it and opened the hyperlink in an nameless browser window – which turned out to be an ideal concept because the hyperlink led to an precise Google web site – hxxps://websites.google.com/view/12345328?fbclid=IwAR2V87sG77nklWVC1tLS-R-fjrL_nNNDhjtDorxKHkN56g8oNVV09Edjgwo
Had I been accessing the positioning whereas logged-in to my browser, particularly with my Google account in Chrome, the criminals would have probably gained far more details about me than I’d wished!
Whereas the positioning is hosted at Google’s cloud infrastructure, the content material is, after all, not associated nor offered by Google themselves. It additionally offers away a number of extra hints that one thing shady is about to occur, right here. First, let’s have a look at the web page title on the browser tab: “Trang chủ” (Vietnamese for “house web page”). Moreover, it appears apparent, as soon as once more, that the textual content on the positioning hasn’t been created by a local or a proficient English speaker. This means that the attackers behind this marketing campaign are primarily based in Vietnam, however after all, on no account that is adequate proof.
The “Obtain” button then results in hxxps://drive.google.com/u/0/uc?id=1sn-Lzt-2vJ_i-6I9lkbGgr_-IN2TVcA-&export=obtain – a private Google Drive house, making an attempt to create the phantasm the marketing campaign was an official providing by Google, although it merely was an affordable imply of distribution for the attackers.
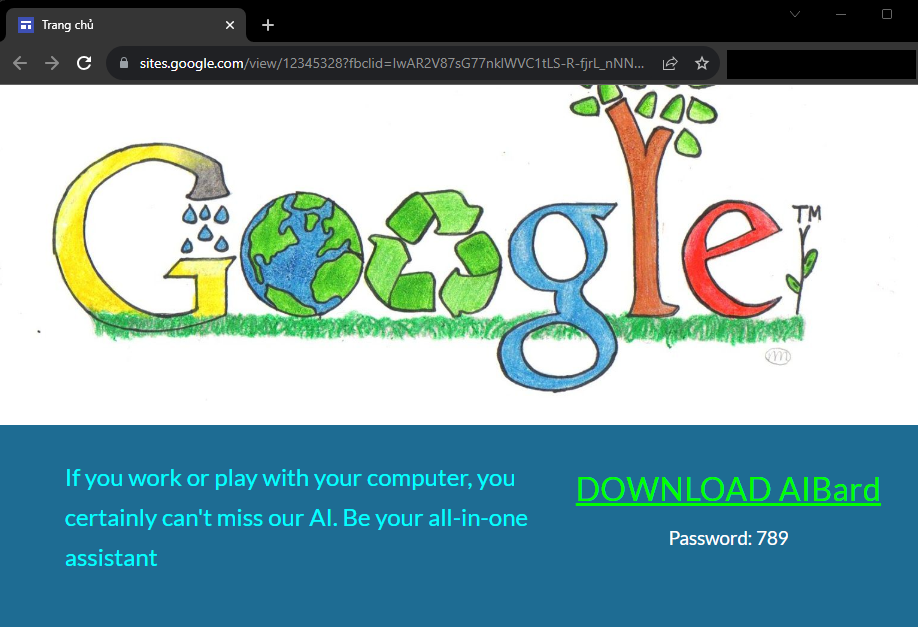
There’s no intelligence, not even synthetic
The file downloaded is a RAR archive – GoogleAIUpdata.rar. Scanning it or importing it to VirusTotal doesn’t result in something helpful as it’s “protected” with a password. One may marvel why if it was a real obtain from Google, you say? Effectively, this password “safety” acts solely as a simple manner for the attackers to get previous malware scanners – nothing else. Should you open the archive (with out unpacking it!) with the password “789” as offered on the obtain web page, you’ll see that the archive incorporates an installer within the MSI (Microsoft Software program Installer) format – Google Bard AI setup.msi. Fortunately, unarchiving instruments like 7-zip present the choice to create SHA-256 (and different) file hashes, which then might be looked for on VirusTotal, once more, with out the necessity to unpack a probably dangerous file.
Wanting up the file supplies the final proof that it is a malicious marketing campaign. 26/59 distributors flag the file as malicious, with ESET gifting away slightly extra data within the detection title. JS/ExtenBro.Agent.EK is a JavaScript agent which is able to attempt to alter your (browser) settings, stopping entry to sure safety vendor websites to do away with it after an an infection, however principally it serves as Adware, displaying annoying and undesirable adverts on principally any web site you attempt to entry and promising the attackers cash with every advert displayed on a sufferer’s machine.
Conclusion
On the time of writing the marketing campaign was nonetheless seen in several variations, however I reported it and can most actually not be the one one doing so. Sadly, it appears that evidently this is likely to be an even bigger marketing campaign as I’ve now encountered different examples as “meta AI” or different pretend “Google AI” adverts. In spite of everything, this marketing campaign might be thought-about a determined try to make a “fast buck” out of the present and ongoing AI hype, spreading ever so annoying Adware to make much more cash. Certainly not this has been a complicated marketing campaign by any means. However the unhappy actuality is that individuals will fall for such scams within the hopes of getting their arms on the most recent applied sciences. One other unhappy reality is that we will not depend on tech giants resembling Fb and Google to supply 100% clear and secure environments.
I hope this weblog put up helps slightly in recognizing the chances and hints and examine a possible rip-off or malware assault with out the necessity for costly instruments, proper from house.


