
A brand new Go-based multi-platform malware recognized as ‘NKAbuse’ is the primary malware abusing NKN (New Sort of Community) know-how for knowledge change, making it a stealthy menace.
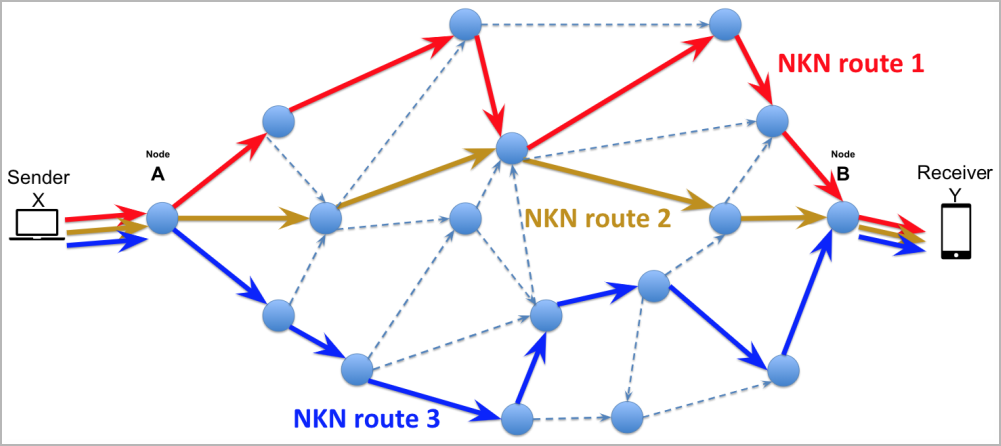
NKN is a comparatively new decentralized peer-to-peer community protocol leveraging blockchain know-how to handle assets and preserve a safe and clear mannequin for community operations.
One of many objectives of NKN is to optimize knowledge transmission pace and latency throughout the community, which is achievable by calculating environment friendly knowledge packet journey paths.
People can take part within the NKN community by operating nodes, just like the Tor community, and presently, there are roughly 60,710 nodes in it.
This comparatively massive variety of nodes contributes to robustness, decentralization, and talent to deal with considerably excessive volumes of information.
NKAbuse particulars
Kaspersky stories the invention of a novel malware named NKAbuse, which primarily targets Linux desktops in Mexico, Colombia, and Vietnam.
One NKAbuse an infection noticed by Kaspersky entails the exploitation of an previous Apache Struts flaw (CVE-2017-5638) to assault a monetary firm.
Though most assaults goal Linux computer systems, the malware can compromise IoTs and helps MIPS, ARM, and 386 architectures.
NKAbuse abuses NKN to launch DDoS (distributed denial of service) assaults which might be arduous to hint again to a particular infrastructure and unlikely to be flagged as a result of originating from a novel protocol not actively monitored by most safety instruments.
“This menace (ab)makes use of the NKN public blockchain protocol to hold out a big set of flooding assaults and act as a backdoor inside Linux programs.” explains Kaspersky
Particularly, the malware shopper communicates with the bot grasp by NKN to ship and obtain knowledge. On the similar time, its capacity to maintain a number of concurrent channels alive provides resilience to its communication line.
The payload instructions despatched by the C2 embody HTTP, TCP, UDP, PING, ICMP, and SSL flood assaults aimed toward a specified goal.
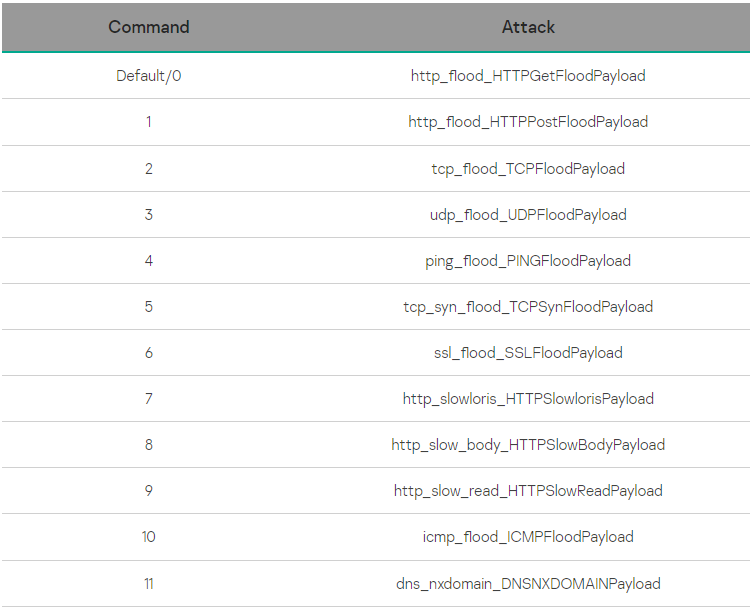
“All these payloads traditionally have been utilized by botnets, so, when mixed with the NKN because the communication protocol, the malware can asynchronously anticipate the grasp to launch a mixed assault,” Kaspersky says.
Along with the DDoS capabilities, NKAbuse additionally acts as a distant entry trojan (RAT) on compromised programs, permitting its operators to carry out command execution, knowledge exfiltration, and snap screenshots.
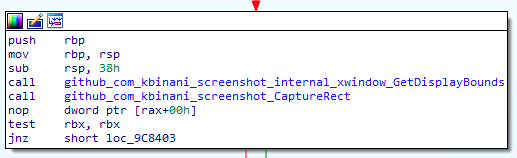
This plethora of capabilities that make NKAbuse extremely versatile and adaptive is not typical within the DDoS botnet house.
Moreover, utilizing blockchain know-how that ensures availability and obfuscates the supply of the assaults makes defending towards this menace very difficult.

