
A brand new wave of BazarCall assaults makes use of Google Kinds to generate and ship fee receipts to victims, trying to make the phishing try seem extra legit.
BazarCall, first documented in 2021, is a phishing assault using an e mail resembling a fee notification or subscription affirmation to safety software program, laptop assist, streaming platforms, and different well-known manufacturers.
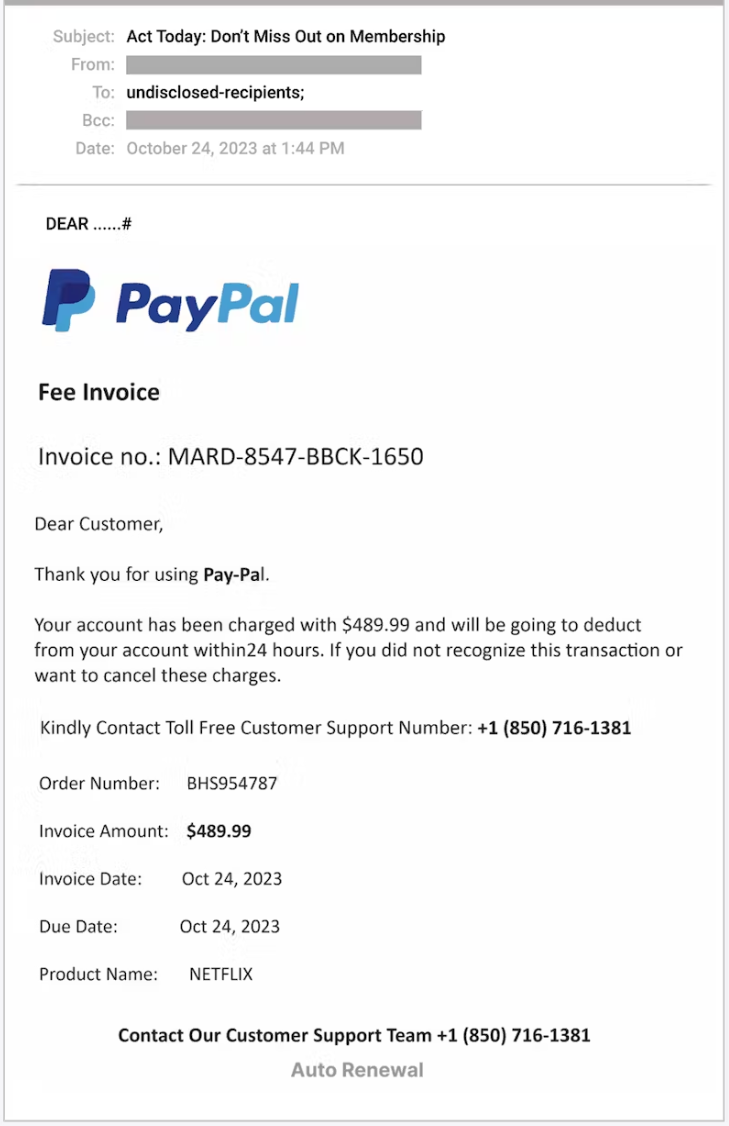
These emails state that the recipient is being auto-renewed into an outrageously costly subscription and may cancel it if they don’t wish to be charged.
Nonetheless, as an alternative of containing a hyperlink to a web site, the e-mail traditionally included a cellphone quantity to an alleged customer support agent of that model, who could also be contacted to dispute prices or cancel the subscription.
The calls are answered by a cybercriminal pretending to be buyer assist, tricking the victims into putting in malware on their computer systems by guiding them via a misleading course of.
The malware is called BazarLoader, and because the identify suggests, it’s a software for putting in further payloads on the sufferer’s system.
Abuse of Google Kinds
E mail safety agency Irregular stories that it has encountered a brand new variant of the BazarCall assault, which now abuses Google Kinds.
Google Kinds is a free on-line software that enables customers to create customized types and quizzes, combine them on websites, share them with others, and so on.
The attacker creates a Google Kind with the main points of a faux transaction, such because the bill quantity, date, fee methodology, and miscellaneous details about the services or products used as bait.
Subsequent, they permit the “response receipt” choice within the settings, which sends a duplicate of the finished kind to the submitted e mail tackle.
Utilizing the goal’s e mail tackle, a duplicate of the finished kind, which appears to be like like a fee affirmation, is distributed to the goal from Google’s servers.
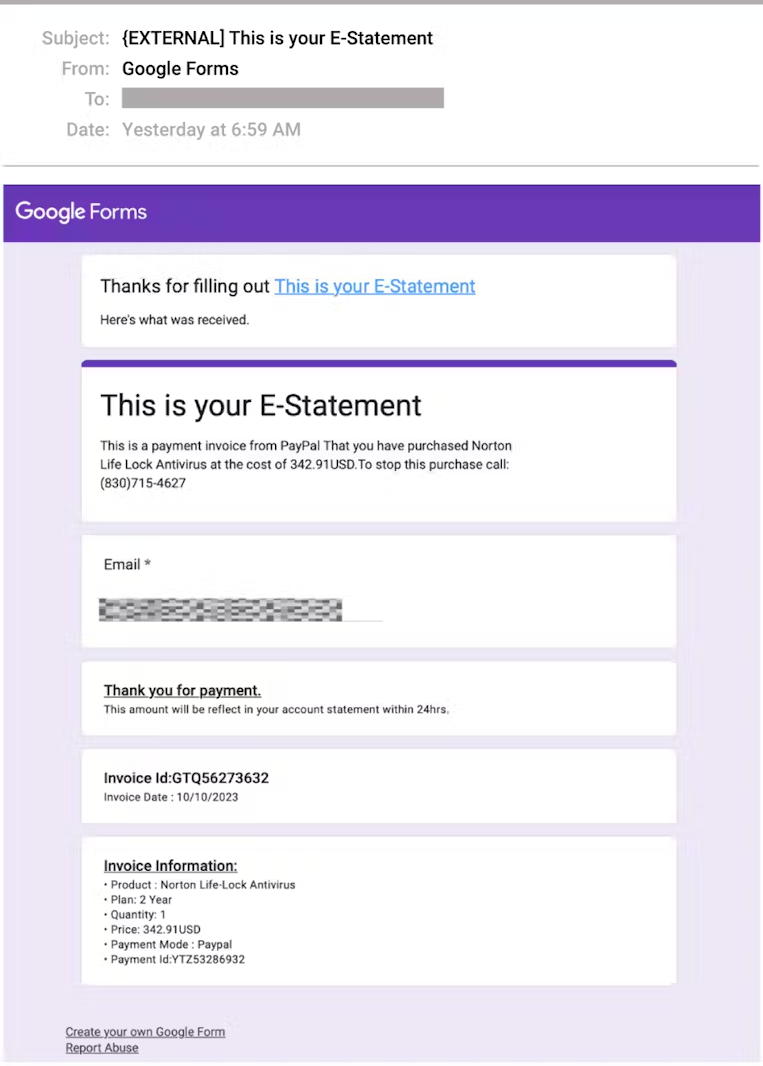
As Google Kinds is a legit service, e mail safety instruments won’t flag or block the phishing e mail, so supply to the meant recipients is assured.
Additionally, the truth that the e-mail originates from a Google tackle (“noreply@google.com”) lends it further legitimacy.
The bill copy contains the menace actor’s cellphone quantity, which recipients are informed to name inside 24 hours from the reception of the e-mail to make any disputes, so the component of urgency is current.
Irregular’s report doesn’t delve into the later levels of the assault. Nonetheless, BazarCall was used prior to now to realize preliminary entry to company networks, often resulting in ransomware assaults.

