Malware evaluation encompasses a broad vary of actions, together with inspecting the malware’s community visitors. To be efficient at it, it is essential to know the widespread challenges and easy methods to overcome them. Listed here are three prevalent points you could encounter and the instruments you may want to handle them.
Decrypting HTTPS visitors
Hypertext Switch Protocol Safe (HTTPS), the protocol for safe on-line communication, has turn into a instrument for malware to hide their malicious actions. By cloaking knowledge change between contaminated gadgets and command-and-control (C&C) servers, malware can function undetected, exfiltrating delicate knowledge, putting in extra payloads, and receiving directions from the operators.
But, with the fitting instrument, decrypting HTTPS visitors is a straightforward activity. For this goal, we are able to use a man-in-the-middle (MITM) proxy. The MITM proxy works as an middleman between the consumer and the server, intercepting their communication.
The MITM proxy aids analysts in real-time monitoring of the malware’s community visitors, offering them with a transparent view of its actions. Amongst different issues, analysts can entry content material of request and response packets, IPs, and URLs to view the small print of the malware’s communication and establish stolen knowledge. The instrument is especially helpful for extracting SSL keys utilized by the malware.
Use case
 |
| Details about AxileStealer supplied by the ANY.RUN sandbox |
In this instance, the preliminary file, 237.06 KB in measurement, drops AxilStealer’s executable file, 129.54 KB in measurement. As a typical stealer, it good points entry to passwords saved in internet browsers and begins to switch them to attackers by way of a Telegram messenger connection.
The malicious exercise is indicated by the rule “STEALER [ANY.RUN] Try to exfiltrate by way of Telegram”. Due to the MITM proxy function, the malware’s visitors is decrypted, revealing extra particulars in regards to the incident.
Use a MITM proxy and dozens of different superior options for in-depth malware evaluation within the ANY.RUN sandbox.
Discovering malware’s household
Malware household identification is a vital a part of any cyber investigation. Yara and Suricata guidelines are generally used instruments for this activity, however their effectiveness could also be restricted when coping with malware samples whose servers are not lively.
FakeNET presents an answer to this problem by making a pretend server connection that responds to malware requests. Tricking the malware to ship a request triggers a Suricata or YARA rule, which precisely identifies the malware household.
Use case
 |
| Inactive servers detected by the ANY.RUN sandbox |
When analyzing this pattern, the sandbox factors to the truth that the malware’s servers are unresponsive.
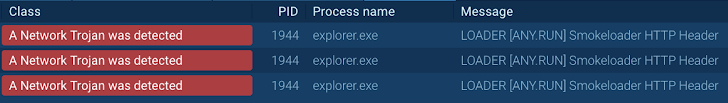 |
| Smoke Loader malware recognized utilizing FakeNET |
But, after enabling the FakeNET function, the malicious software program immediately sends a request to a pretend server, triggering the community rule that identifies it as Smoke Loader.
Catching geo-targeted and evasive malware
Many assaults and phishing campaigns give attention to particular geographic areas or international locations. Subsequently, they incorporate mechanisms like IP geolocation, language detection, or web site blocking which can restrict analysts’ capability to detect them.
Alongside geo-targeting, malware operators might leverage strategies to evade evaluation in sandbox environments. A typical method is to confirm whether or not the system is utilizing a datacenter IP deal with. If confirmed, the malicious software program stops execution.
To counter these obstacles, analysts use a residential proxy. This nifty instrument works by switching the IP deal with of the analyst’s gadget or digital machine to strange customers’ residential IPs from completely different components of the world.
This function empowers professionals to bypass geo-restrictions by mimicking native customers and examine malicious actions with out revealing their sandbox atmosphere.
Use case
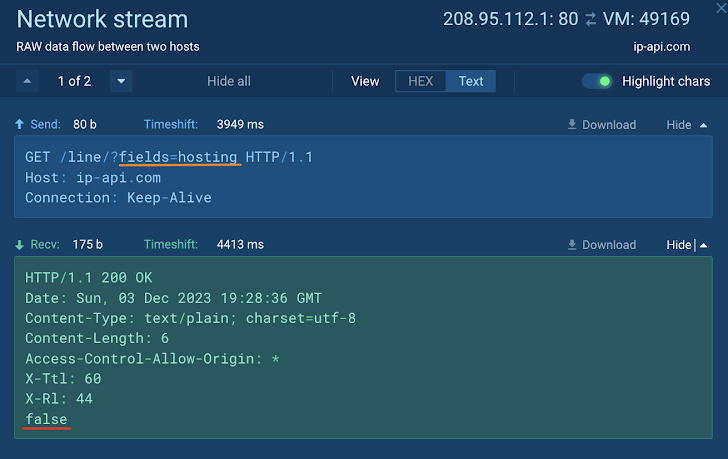 |
| Smoke Loader malware recognized utilizing FakeNET |
Right here, Xworm immediately checks for a internet hosting IP deal with as quickly as it’s uploaded to a sandbox. But, because the VM has a residential proxy, the malware continues to execute and connects to its command-and-control server.
Strive all of those instruments in ANY.RUN
Establishing and utilizing every of the aforementioned instruments individually can take numerous effort. To entry and make the most of all of them with ease, use the cloud-based ANY.RUN sandbox.
The important thing function of the service is interactivity, permitting you to securely interact with malware and the contaminated system identical to you’ll by yourself pc.
You’ll be able to discover these and quite a few different options of ANY.RUN, together with non-public house in your crew, Home windows 7, 8, 10, 11 VMs, and API integration utterly free of charge.
Simply use a 14-day trial, no strings connected.


