ESET researchers found a Ballistic Bobcat marketing campaign focusing on varied entities in Brazil, Israel, and the United Arab Emirates, utilizing a novel backdoor we’ve named Sponsor.
We found Sponsor after we analyzed an fascinating pattern we detected on a sufferer’s system in Israel in Might 2022 and scoped the victim-set by nation. Upon examination, it turned evident to us that the pattern was a novel backdoor deployed by the Ballistic Bobcat APT group.
Ballistic Bobcat, beforehand tracked by ESET Analysis as APT35/APT42 (aka Charming Kitten, TA453, or PHOSPHORUS), is a suspected Iran-aligned superior persistent risk group that targets training, authorities, and healthcare organizations, in addition to human rights activists and journalists. It’s most energetic in Israel, the Center East, and the US. Notably, throughout the pandemic, it was focusing on COVID-19-related organizations, together with the World Well being Group and Gilead Prescription drugs, and medical analysis personnel.
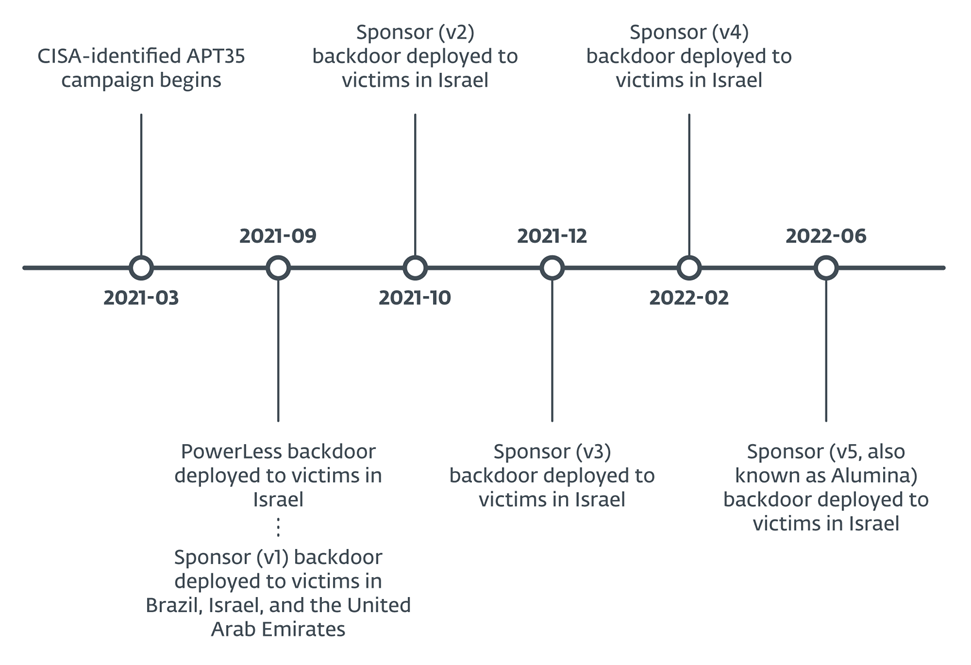
Overlaps between Ballistic Bobcat campaigns and Sponsor backdoor variations present a reasonably clear sample of software growth and deployment, with narrowly focused campaigns, every of restricted period. We subsequently found 4 different variations of the Sponsor backdoor. In complete, we noticed Sponsor deployed to at the very least 34 victims in Brazil, Israel, and the United Arab Emirates, as outlined in Determine 1.
Key factors of this blogpost:
- We found a brand new backdoor deployed by Ballistic Bobcat that we subsequently named Sponsor.
- Ballistic Bobcat deployed the brand new backdoor in September 2021, whereas it was wrapping up the marketing campaign documented in CISA Alert AA21-321A and the PowerLess marketing campaign.
- The Sponsor backdoor makes use of configuration recordsdata saved on disk. These recordsdata are discreetly deployed by batch recordsdata and intentionally designed to look innocuous, thereby making an attempt to evade detection by scanning engines.
- Sponsor was deployed to at the very least 34 victims in Brazil, Israel, and the United Arab Emirates; we’ve named this exercise the Sponsoring Entry marketing campaign.
Preliminary entry
Ballistic Bobcat obtained preliminary entry by exploiting identified vulnerabilities in internet-exposed Microsoft Change servers by first conducting meticulous scans of the system or community to determine potential weaknesses or vulnerabilities, and subsequently focusing on and exploiting these recognized weaknesses. The group has been identified to interact on this habits for a while. Nevertheless, lots of the 34 victims recognized in ESET telemetry may finest be described as victims of alternative moderately than preselected and researched victims, as we suspect Ballistic Bobcat engaged within the above-described scan-and-exploit habits as a result of it was not the one risk actor with entry to those techniques. Now we have named this Ballistic Bobcat exercise using the Sponsor backdoor the Sponsoring Entry marketing campaign.
The Sponsor backdoor makes use of configuration recordsdata on disk, dropped by batch recordsdata, and each are innocuous in order to bypass scanning engines. This modular method is one which Ballistic Bobcat has used very often and with modest success up to now two and a half years. On compromised techniques, Ballistic Bobcat additionally continues to make use of a wide range of open-source instruments, which we describe – along with the Sponsor backdoor – on this blogpost.
Victimology
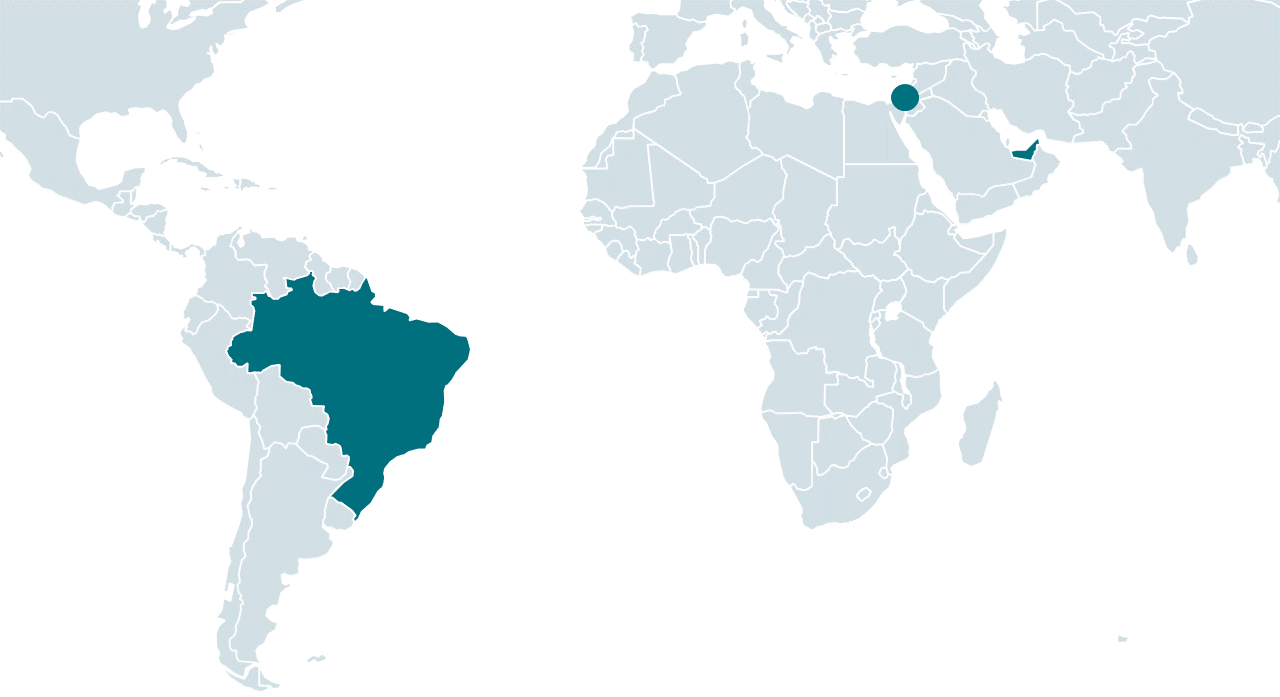
A major majority of the 34 victims had been positioned in Israel, with solely two positioned in different international locations:
- Brazil, at a medical cooperative and medical health insurance operator, and
- the United Arab Emirates, at an unidentified group.
Desk 1 describes the verticals, and organizational particulars, for victims in Israel.
Desk 1. Verticals and organizational particulars for victims in Israel
|
Vertical |
Particulars |
|
Automotive |
· An automotive firm specializing in customized modifications. · An automotive restore and upkeep firm. |
|
Communications |
· An Israeli media outlet. |
|
Engineering |
· A civil engineering agency. · An environmental engineering agency. · An architectural design agency. |
|
Monetary companies |
· A monetary companies firm that makes a speciality of funding counseling. · An organization that manages royalties. |
|
Healthcare |
· A medical care supplier. |
|
Insurance coverage |
· An insurance coverage firm that operates an insurance coverage market. · A business insurance coverage firm. |
|
Regulation |
· A agency specializing in medical legislation. |
|
Manufacturing |
· A number of electronics manufacturing corporations. · An organization that manufactures metal-based business merchandise. · A multinational know-how manufacturing firm. |
|
Retail |
· A meals retailer. · A multinational diamond retailer. · A skincare merchandise retailer. · A window remedy retailer and installer. · A world digital components provider. · A bodily entry management provider. |
|
Expertise |
· An IT companies know-how firm. · An IT options supplier. |
|
Telecommunications |
· A telecommunications firm. |
|
Unidentified |
· A number of unidentified organizations. |
Attribution
In August 2021, the Israeli sufferer above that operates an insurance coverage market was attacked by Ballistic Bobcat with the instruments CISA reported in November 2021. The symptoms of compromise we noticed are:
- MicrosoftOutlookUpdateSchedule,
- MicrosoftOutlookUpdateSchedule.xml,
- GoogleChangeManagement, and
- GoogleChangeManagement.xml.
Ballistic Bobcat instruments communicated with the identical command and management (C&C) server as within the CISA report: 162.55.137[.]20.
Then, in September 2021, the identical sufferer acquired the subsequent technology of Ballistic Bobcat instruments: the PowerLess backdoor and its supporting toolset. The symptoms of compromise we noticed had been:
- http://162.55.137[.]20/gsdhdDdfgA5sS/ff/dll.dll,
- windowsprocesses.exe, and
- http://162.55.137[.]20/gsdhdDdfgA5sS/ff/windowsprocesses.exe.
On November 18th, 2021, the group then deployed one other software (Plink) that was lined within the CISA report, as MicrosoftOutLookUpdater.exe. Ten days later, on November 28th, 2021, Ballistic Bobcat deployed the Merlin agent (the agent portion of an open-source post-exploitation C&C server and agent written in Go). On disk, this Merlin agent was named googleUpdate.exe, utilizing the identical naming conference as described within the CISA report to cover in plain sight.
The Merlin agent executed a Meterpreter reverse shell that referred to as again to a brand new C&C server, 37.120.222[.]168:80. On December 12th, 2021, the reverse shell dropped a batch file, set up.bat, and inside minutes of executing the batch file, Ballistic Bobcat operators pushed their latest backdoor, Sponsor. This could grow to be the third model of the backdoor.
Technical evaluation
Preliminary entry
We had been capable of determine a possible technique of preliminary entry for 23 of the 34 victims that we noticed in ESET telemetry. Just like what was reported within the PowerLess and CISA stories, Ballistic Bobcat in all probability exploited a identified vulnerability, CVE-2021-26855, in Microsoft Change servers to realize a foothold on these techniques.
For 16 of the 34 victims, it seems Ballistic Bobcat was not the one risk actor with entry to their techniques. This may occasionally point out, together with the big variety of victims and the obvious lack of apparent intelligence worth of some victims, that Ballistic Bobcat engaged in scan-and-exploit habits, versus a focused marketing campaign towards preselected victims.
Toolset
Open-source instruments
Ballistic Bobcat employed a lot of open-source instruments throughout the Sponsoring Entry marketing campaign. These instruments and their features are listed in Desk 2.
Desk 2. Open-source instruments utilized by Ballistic Bobcat
|
Filename |
Description |
|
Maps a hostname to an IP tackle inside the native community. |
|
RevSocks, a reverse tunnel software. |
|
Mimikatz, with an unique filename of midongle.exe and filled with the Armadillo PE packer. |
|
GO Easy Tunnel (GOST), a tunneling software written in Go. |
|
Chisel, a TCP/UDP tunnel over HTTP utilizing SSH layers. |
|
RevSocks tunnel, protected with the trial model of the Enigma Protector software program safety. |
|
Plink (PuTTY Hyperlink), a command line connection software. |
|
WebBrowserPassView.exe
|
|
|
A software for interacting with, and extracting information from, SQL databases. |
|
ProcDump, a Sysinternals command line utility for monitoring functions and producing crash dumps. |
Batch recordsdata
Ballistic Bobcat deployed batch recordsdata to victims’ techniques moments earlier than deploying the Sponsor backdoor. File paths we’re conscious of are:
- C:inetpubwwwrootaspnet_clientInstall.bat
- %USERPROFILEpercentDesktopInstall.bat
- %WINDOWSpercentTasksInstall.bat
Sadly, we had been unable to acquire any of those batch recordsdata. Nevertheless, we consider they write innocuous configuration recordsdata to disk, which the Sponsor backdoor requires to operate totally. These configuration filenames had been taken from the Sponsor backdoors however had been by no means collected:
- config.txt
- node.txt
- error.txt
- Uninstall.bat
We consider that the batch recordsdata and configuration recordsdata are a part of the modular growth course of that Ballistic Bobcat has favored over the previous few years.
Sponsor backdoor
Sponsor backdoors are written in C++ with compilation timestamps and Program Database (PDB) paths as proven in Desk 3. A observe on model numbers: the column Model represents the model that we monitor internally based mostly on the linear development of Sponsor backdoors the place adjustments are made out of one model to the subsequent. The Inside model column incorporates the model numbers noticed in every Sponsor backdoor and are included for ease of comparability when analyzing these and different potential Sponsor samples.
Desk 3. Sponsor compilation timestamps and PDBs
|
Model |
Inside model |
Compilation timestamp |
PDB |
|
1 |
1.0.0 |
2021-08-29 09:12:51 |
D:TempBD_Plus_SrvcReleaseBD_Plus_Srvc.pdb |
|
2 |
1.0.0 |
2021-10-09 12:39:15 |
D:TempSponsorReleaseSponsor.pdb |
|
3 |
1.4.0 |
2021-11-24 11:51:55 |
D:TempSponsorReleaseSponsor.pdb |
|
4 |
2.1.1 |
2022-02-19 13:12:07 |
D:TempSponsorReleaseSponsor.pdb |
|
5 |
1.2.3.0 |
2022-06-19 14:14:13 |
D:TempAluminaReleaseAlumina.pdb |
The preliminary execution of Sponsor requires the runtime argument set up, with out which Sponsor gracefully exits, probably a easy anti-emulation/anti-sandbox method. If handed that argument, Sponsor creates a service referred to as SystemNetwork (in v1) and Replace (in all the opposite variations). It units the service’s Startup Sort to Automated, and units it to run its personal Sponsor course of, and grants it full entry. It then begins the service.
Sponsor, now operating as a service, makes an attempt to open the aforementioned configuration recordsdata beforehand positioned on disk. It appears for config.txt and node.txt, each within the present working listing. If the primary is lacking, Sponsor units the service to Stopped and gracefully exits.
Backdoor configuration
Sponsor’s configuration, saved in config.txt, incorporates two fields:
- An replace interval, in seconds, to periodically contact the C&C server for instructions.
- A listing of C&C servers, known as relays in Sponsor’s binaries.
The C&C servers are saved encrypted (RC4), and the decryption secret’s current within the first line of config.txt. Every of the fields, together with the decryption key, have the format proven in Determine 3.
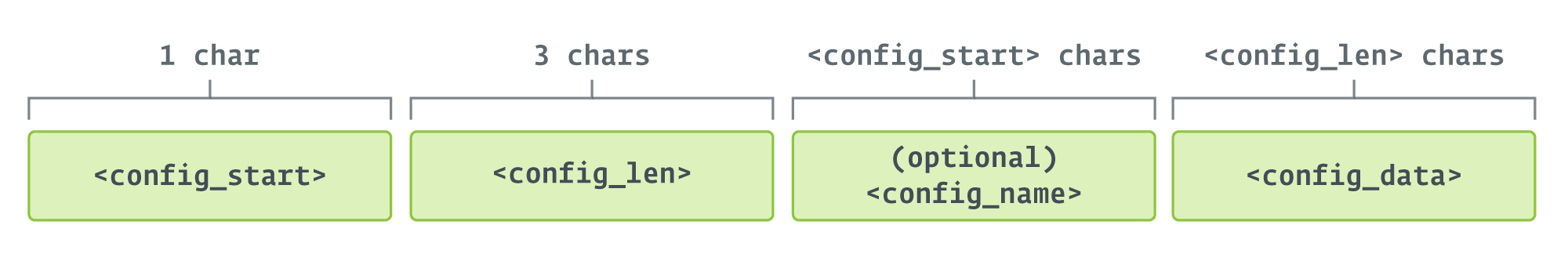
These subfields are:
- config_start: signifies the size of config_name, if current, or zero, if not. Utilized by the backdoor to know the place config_data begins.
- config_len: size of config_data.
- config_name: optionally available, incorporates a reputation given to the configuration area.
- config_data: the configuration itself, encrypted (within the case of C&C servers) or not (all the opposite fields).
Determine 4 reveals an instance with color-coded contents of a attainable config.txt file. Word that this isn’t an precise file we noticed, however a fabricated instance.
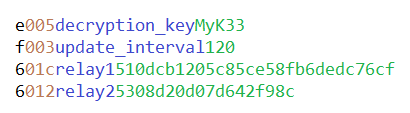
The final two fields in config.txt are encrypted with RC4, utilizing the string illustration of the SHA-256 hash of the desired decryption key, as the important thing to encrypt the info. We see that the encrypted bytes are saved hex-encoded as ASCII textual content.
Host info gathering
Sponsor gathers details about the host on which it’s operating, stories all the gathered info to the C&C server, and receives a node ID, which is written to node.txt. Desk 4 lists keys and values within the Home windows registry that Sponsor makes use of to get the knowledge, and supplies an instance of the info collected.
Desk 4. Data gathered by Sponsor
|
Registry key |
Worth |
Instance |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Consumer
|
Sponsor additionally collects the host’s Home windows area through the use of the next WMIC command:
wmic computersystem get area
Lastly, Sponsor makes use of Home windows APIs to gather the present username (GetUserNameW), decide if the present Sponsor course of is operating as a 32- or 64-bit software (GetCurrentProcess, then IsWow64Process(CurrentProcess)), and determines whether or not the system is operating on battery energy or related to an AC or DC energy supply (GetSystemPowerStatus).
One oddity relating to the 32- or 64-bit software test is that every one noticed samples of Sponsor had been 32-bit. This might imply that a number of the subsequent stage instruments require this info.
The collected info is shipped in a base64-encoded message that, earlier than encoding, begins with r and has the format proven in Determine 5.
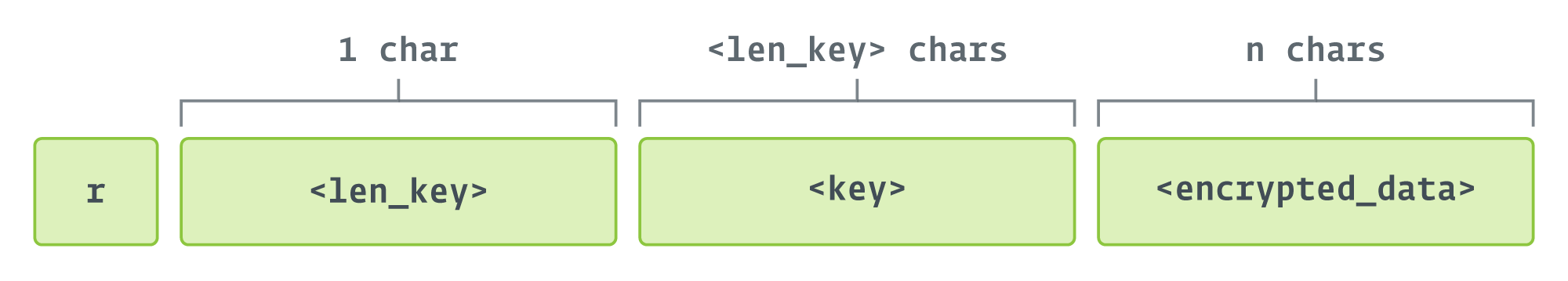
The data is encrypted with RC4, and the encryption secret’s a random quantity generated on the spot. The bottom line is hashed with the MD5 algorithm, not SHA-256 as beforehand talked about. That is the case for all communications the place Sponsor has to ship encrypted information.
The C&C server replies with a quantity used to determine the victimized pc in later communications, which is written to node.txt. Word that the C&C server is randomly chosen from the listing when the r message is shipped, and the identical server is utilized in all subsequent communications.
Command processing loop
Sponsor requests instructions in a loop, sleeping based on the interval outlined in config.txt. The steps are:
- Ship a chk=Take a look at message repeatedly, till the C&C server replies Okay.
- Ship a c (IS_CMD_AVAIL) message to the C&C server, and obtain an operator command.
- Course of the command.
- If there’s output to be despatched to the C&C server, ship an a (ACK) message, together with the output (encrypted), or
- If execution failed, ship an f
(FAILED) message. The error message will not be despatched.
- Sleep.
The c message is shipped to request a command to execute, and has the format (earlier than base64 encoding) proven in Determine 6.
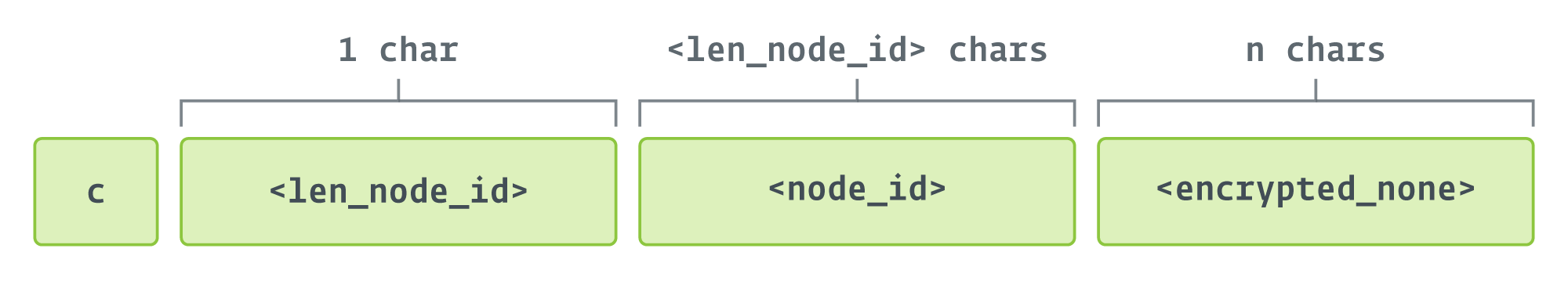
The encrypted_none area within the determine is the results of encrypting the hardcoded string None with RC4. The important thing for encryption is the MD5 hash of node_id.
The URL used to contact the C&C server is constructed as: http://<IP_or_domain>:80. This may occasionally point out that 37.120.222[.]168:80 is the one C&C server used all through the Sponsoring Entry marketing campaign, because it was the one IP tackle we noticed sufferer machines reaching out to on port 80.
Operator instructions
Operator instructions are delineated in Desk 5 and seem within the order during which they’re discovered within the code. Communication with the C&C server happens over port 80.
Desk 5. Operator instructions and descriptions
|
Command |
Description |
|
p |
Sends the method ID for the operating Sponsor course of. |
|
e |
Executes a command, as laid out in a subsequent further argument, on the Sponsor host utilizing the next string: c:windowssystem32cmd.exe /c <cmd> > outcome.txt 2>&1 Outcomes are saved in outcome.txt within the present working listing. Sends an a message with the encrypted output to the C&C server if efficiently executed. If failed, sends an f message (with out specifying the error). |
|
d |
Receives a file from the C&C server and executes it. This command has many arguments: the goal filename to write down the file into, the MD5 hash of the file, a listing to write down the file to (or the present working listing, by default), a Boolean to point whether or not to run the file or not, and the contents of the executable file, base64-encoded. If no errors happen, an a message is shipped to the C&C server with Add and execute file efficiently or Add file efficiently with out execute (encrypted). If errors happen throughout execution of the file, an f message is shipped. If the MD5 hash of the contents of the file doesn’t match the offered hash, an e (CRC_ERROR) message is shipped to the C&C server (together with solely the encryption key used, and no different info). The usage of the time period Add right here is probably complicated because the Ballistic Bobcat operators and coders take the perspective from the server aspect, whereas many may view this as a obtain based mostly on the pulling of the file (i.e., downloading it) by the system utilizing the Sponsor backdoor. |
|
u |
Makes an attempt to obtain a file utilizing the URLDownloadFileW Home windows API and execute it. Success sends an a message with the encryption key used, and no different info. Failure sends an f message with an identical construction. |
|
s |
Executes a file already on disk, Uninstall.bat within the present working listing, that most probably incorporates instructions to delete recordsdata associated to the backdoor. |
|
n |
This command might be explicitly provided by an operator or might be inferred by Sponsor because the command to execute within the absence of some other command. Referred to inside Sponsor as NO_CMD, it executes a randomized sleep earlier than checking again in with the C&C server. |
|
b |
Updates the listing of C&Cs saved in config.txt within the present working listing. The brand new C&C addresses exchange the earlier ones; they don’t seem to be added to the listing. It sends an a message with |
|
i |
Updates the predetermined check-in interval laid out in config.txt. It sends an a message with New interval changed efficiently to the C&C server if efficiently up to date. |
Updates to Sponsor
Ballistic Bobcat coders made code revisions between Sponsor v1 and v2. The 2 most vital adjustments within the latter are:
- Optimization of code the place a number of longer features had been minimized into features and subfunctions, and
- Disguising Sponsor as an updater program by together with the next message within the service configuration:
App updates are nice for each app customers and apps – updates imply that builders are all the time engaged on bettering the app, retaining in thoughts a greater buyer expertise with every replace.
Community infrastructure
Along with piggybacking on the C&C infrastructure used within the PowerLess marketing campaign, Ballistic Bobcat additionally launched a brand new C&C server. The group additionally utilized a number of IPs to retailer and ship help instruments throughout the Sponsoring Entry marketing campaign. Now we have confirmed that none of those IPs are in operation at the moment.
Conclusion
Ballistic Bobcat continues to function on a scan-and-exploit mannequin, in search of targets of alternative with unpatched vulnerabilities in internet-exposed Microsoft Change servers. The group continues to make use of a various open-source toolset supplemented with a number of customized functions, together with its Sponsor backdoor. Defenders could be nicely suggested to patch any internet-exposed gadgets and stay vigilant for brand spanking new functions popping up inside their organizations.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis presents personal APT intelligence stories and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
Information
|
SHA-1 |
Filename |
Detection |
Description |
|
N/A |
Win32/Agent.UXG |
Ballistic Bobcat backdoor, Sponsor (v1). |
|
N/A |
Win32/Agent.UXG |
Ballistic Bobcat backdoor, Sponsor (v2). |
|
N/A |
Win32/Agent.UXG |
Ballistic Bobcat backdoor, Sponsor (v3). |
|
N/A |
Win32/Agent.UXG |
Ballistic Bobcat backdoor, Sponsor (v4). |
|
N/A |
Win32/Agent.UXG |
Ballistic Bobcat backdoor, Sponsor (v5, aka Alumina). |
|
N/A |
WinGo/Agent.BT |
RevSocks reverse tunnel. |
|
N/A |
clear |
ProcDump, a command line utility for monitoring functions and producing crash dumps. |
|
N/A |
Generik.EYWYQYF |
Mimikatz. |
|
N/A |
WinGo/Riskware.Gost.D |
GO Easy Tunnel (GOST). |
|
N/A |
WinGo/HackTool.Chisel.A |
Chisel reverse tunnel. |
|
N/A |
N/A |
Host2IP discovery software. |
|
N/A |
Win64/Packed.Enigma.BV |
RevSocks tunnel, protected with the trial model of the Enigma Protector software program safety. |
|
N/A |
N/A |
Plink (PuTTY Hyperlink), a command line connection software. |
|
N/A |
Win32/PSWTool.WebBrowserPassView.I |
A password restoration software for passwords saved in net browsers. |
|
N/A |
MSIL/HackTool.SQLDump.A |
A software for interacting with, and extracting information from, SQL databases. |
File paths
The next is a listing of paths the place the Sponsor backdoor was deployed on victimized machines.
%SYSTEMDRIVEpercentinetpubwwwrootaspnet_client
%USERPROFILEpercentAppDataLocalTempfile
%USERPROFILEpercentAppDataLocalTemp2low
%USERPROFILEpercentDesktop
%USERPROFILEpercentDownloadsa
%WINDIR%
%WINDIRpercentINFMSExchange Supply DSN
%WINDIRpercentTasks
%WINDIRpercentTemppercentWINDIRpercentTempcrashpad1Files
Community
IP
Supplier
First seen
Final seen
Particulars
162.55.137[.]20
Hetzner On-line GMBH
2021-06-14
2021-06-15
PowerLess C&C.
37.120.222[.]168
M247 LTD
2021-11-28
2021-12-12
Sponsor C&C.
198.144.189[.]74
Colocrossing
2021-11-29
2021-11-29
Help instruments obtain website.
5.255.97[.]172
The Infrastructure Group B.V.
2021-09-05
2021-10-28
Help instruments obtain website.
IP
Supplier
First seen
Final seen
Particulars
162.55.137[.]20
Hetzner On-line GMBH
2021-06-14
2021-06-15
PowerLess C&C.
37.120.222[.]168
M247 LTD
2021-11-28
2021-12-12
Sponsor C&C.
198.144.189[.]74
Colocrossing
2021-11-29
2021-11-29
Help instruments obtain website.
5.255.97[.]172
The Infrastructure Group B.V.
2021-09-05
2021-10-28
Help instruments obtain website.
This desk was constructed utilizing model 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Identify |
Description |
|
Reconnaissance |
Energetic Scanning: Vulnerability Scanning |
Ballistic Bobcat scans for weak variations of Microsoft Change Servers to take advantage of. |
|
|
Useful resource Improvement |
Develop Capabilities: Malware |
Ballistic Bobcat designed and coded the Sponsor backdoor. |
|
|
Get hold of Capabilities: Software |
Ballistic Bobcat makes use of varied open-source instruments as a part of the Sponsoring Entry marketing campaign. |
||
|
Preliminary Entry |
Exploit Public-Dealing with Software |
Ballistic Bobcat targets internet-exposed Microsoft Change Servers. |
|
|
Execution |
Command and Scripting Interpreter: Home windows Command Shell |
The Sponsor backdoor makes use of the Home windows command shell to execute instructions on the sufferer’s system. |
|
|
System Providers: Service Execution |
The Sponsor backdoor units itself as a service and initiates its main features after the service is executed. |
||
|
Persistence |
Create or Modify System Course of: Home windows Service |
Sponsor maintains persistence by making a service with automated startup that executes its main features in a loop. |
|
|
Privilege Escalation |
Legitimate Accounts: Native Accounts |
Ballistic Bobcat operators try to steal credentials of legitimate customers after initially exploiting a system earlier than deploying the Sponsor backdoor. |
|
|
Protection Evasion |
Deobfuscate/Decode Information or Data |
Sponsor shops info on disk that’s encrypted and obfuscated, and deobfuscates it at runtime. |
|
|
Obfuscated Information or Data |
Configuration recordsdata that the Sponsor backdoor requires on disk are encrypted and obfuscated. |
||
|
Legitimate Accounts: Native Accounts |
Sponsor is executed with admin privileges, probably utilizing credentials that operators discovered on disk; together with Ballistic Bobcat’s innocuous naming conventions, this permits Sponsor to mix into the background. |
||
|
Credential Entry |
Credentials from Password Shops: Credentials from Internet Browsers |
Ballistic Bobcat operators use open-source instruments to steal credentials from password shops inside net browsers. |
|
|
Discovery |
Distant System Discovery |
Ballistic Bobcat makes use of the Host2IP software, beforehand utilized by Agrius, to find different techniques inside reachable networks and correlate their hostnames and IP addresses. |
|
|
Command and Management |
Knowledge Obfuscation |
The Sponsor backdoor obfuscates information earlier than sending it to the C&C server. |


