Hunters researchers famous the vulnerability might result in privilege escalation. Google mentioned the report “doesn’t establish an underlying safety challenge in our merchandise.”
Cybersecurity researchers from the agency Hunters found a vulnerability in Google Workspace that might enable undesirable entry to Workspace APIs. The flaw is important in that it might let attackers use privilege escalation to achieve entry that will in any other case solely be obtainable to customers with Tremendous Admin entry. Hunters named this safety flaw DeleFriend.
Leap to:
Vulnerability uncovered in Google’s domain-wide delegation
In response to the Hunters crew, the vulnerability is predicated on Google Workspace’s position in managing person identities throughout Google Cloud providers. Area-wide delegation (DWD) connects identification objects from both Google Workspace Market or a Google Cloud Platform Service Account to Workspace.
Area-wide delegation can be utilized by attackers in two major methods: to create a brand new delegation after having gained entry to a Tremendous Admin privilege on the goal Workspace surroundings via one other assault, or to “enumerate profitable mixtures of service account keys and OAuth scopes,” Hunters mentioned. This second approach is the novel methodology the researchers have found. Yonatan Khanashvilli, menace searching knowledgeable at Crew Axon at Hunters, posted a way more detailed clarification of DeleFriend.
Response from Google
Hunters disclosed this flaw to Google in August 2023 and wrote, “Google is presently reviewing the difficulty with their Product crew to evaluate potential actions based mostly on our suggestions.”
An nameless Google consultant instructed The Hacker Information in November 2023, “This report doesn’t establish an underlying safety challenge in our merchandise. As a greatest apply, we encourage customers to verify all accounts have the least quantity of privilege potential (see steerage right here). Doing so is vital to combating a lot of these assaults.”
Why this Google Workspace vulnerability is especially harmful
Hunters mentioned this vulnerability is especially harmful as a result of it’s long-term (GCP Service account keys should not have expiry dates by default), straightforward to cover and laborious to detect. As soon as inside an account with Tremendous Admin privileges, attackers might probably view emails in Gmail, view somebody’s schedule in Google Calendar or exfiltrate information from Google Drive.
“The potential penalties of malicious actors misusing domain-wide delegation are extreme. As an alternative of affecting only a single identification, as with particular person OAuth consent, exploiting DWD with current delegation can affect each identification throughout the Workspace area,” mentioned Khanashvili within the press launch.
SEE: Overworked IT execs in Australian small companies have a number of choices for coping with cyber safety. (TechRepublic)
The way to detect and defend towards DeleFriend
Along with guaranteeing privileges are arrange correctly, as Google notes, IT admins might create every service account in a separate challenge if potential, Hunters mentioned. Different suggestions from Hunters to guard towards DeleFriend exploitation are:
- Restrict OAuth scopes in delegations as a lot as potential, utilizing the precept of least privilege.
- Keep away from administrative scopes comparable to https://www.googleapis.com/auth/admin.
- Focus detection engineering and menace searching practices on suspicious delegations and a number of non-public key creations over a brief period of time.
- Preserve safety posture and hygiene greatest practices.
Google suggests the next:
- Please examine in case you are presently utilizing area huge delegation by visiting the Admin Console web page. In case you are not utilizing DWD at the moment then there isn’t any present danger and future DWD utilization ought to comply with the upcoming greatest practices information.
- When you have Service Accounts that you’ve arrange for DWD, it is best to evaluate every setup and safe entry to these service accounts by:
- Making certain the Service Accounts have least privileges by way of API scopes granted to them by visiting this web page on the Admin Console and revoking Service Account entry to unused scopes.
- Guarantee solely Tremendous Admins or equal safety roles in GCP console have the flexibility to create/replace these service accounts and related keys.
Hunters created a proof-of-concept device for operating the DeleFriend exploitation methodology manually. The device works by enumerating GCP Initiatives utilizing the Useful resource Supervisor API, iterating and enumerating on GCP Service account sources and challenge sources, and investigating particular roles and permissions from there, together with extracting non-public key worth from a privateKeyData attribute key (Determine A). The tip result’s a JWT object, which could be exchanged with a short lived entry token to permit entry to Google APIs. Konanshvili’s weblog submit accommodates extra element.
Determine A
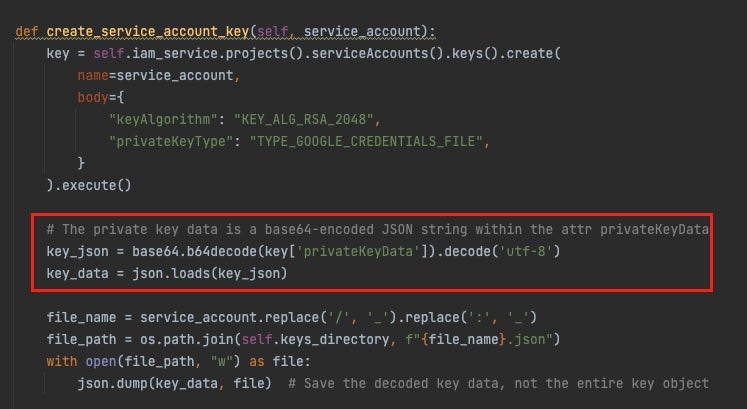
The device is meant for researchers with a purpose to detect misconfigurations, and “enhance consciousness round OAuth delegation assaults in GCP and Google Workspace and to enhance the safety posture of organizations that use the Area-Broad-Delegation characteristic,” Hunters wrote.
Word: This story was up to date with suggestions from Google.