Posted by Sandeep Patil – Principal Software program Engineer, and Irene Ang – Product Supervisor
The Android Virtualization Framework (AVF) will probably be obtainable on upcoming choose Android 14 gadgets. The AVF, first launched in Android 13 on Pixel gadgets, supplies new capabilities for platform builders engaged on privileged purposes.
With AVF, we’re extra broadly supporting virtualization to Android. Virtualization is broadly used and deployed to isolate workloads and working methods from one another. It allows environment friendly scaling of infrastructure, testing environments, legacy software program compatibility, creating digital desktops and far more.
With AVF digital machines change into a core assemble of the Android working system, much like the best way Android makes use of Linux processes. Builders have the flexibleness to decide on the extent of isolation for a digital machine:
- One-way isolation: Android (the host) can management and examine the contents of the VM. These are mostly used for sandboxing and separation, enabling a number of working methods to run on the identical machine / machine, with one working system host (Android) controlling and watching over all others.
- Two-way isolation (Remoted VM): Android (the host) and the digital machine (the visitor) are utterly remoted from one another. Builders who cope with or retailer delicate knowledge could profit from an remoted digital machine. An remoted digital machine has a two-way barrier, the place neither the host (Android) nor the VM have entry to one another, besides through explicitly-agreed-upon communication channels. This has 2 important properties:
- The workload and knowledge contained in the VM is inaccessible (confidential) from the host (Android).
- Even when Android is compromised all the best way as much as (and together with) the host kernel, the remoted VM stays uncompromised.
Advantages of AVF
Isolation
With an remoted VM, builders now have an alternative choice to Trustzone to be used instances that want isolation from Android with out escalated privilege.
Portability
Digital machines and the purposes operating inside them are way more transportable than trusted applets. For instance, a Linux-based digital machine with a Linux-application payload will work on all gadgets that help AVF. Which means that builders can construct an utility as soon as and deploy it in every single place. VMs additionally make porting of current Linux primarily based purposes seamless and simple, in comparison with porting right into a Trustzone working system.
Efficiency
AVF is designed to be light-weight, environment friendly and versatile. Digital machines can:
- be as small as a single C program and as massive as a whole working system relying on the developer’s want;
- be persistent or intermittent;
- develop in reminiscence or shrink relying on the general system well being; and
- honor Android’s scheduler hints and low-memory warnings.
Extensibility
AVF is designed with builders in thoughts. Digital machines will be custom-made to fulfill particular use-case wants. Builders can deploy any VM payload so long as it conforms to sure boot and communication protocols specified by AVF.
Along with bringing the ability of virtualization to Android and enabling all the probabilities of digital desktops, sandboxing, AVF’s use of remoted digital machines can profit the next frequent Android use instances (and lots of extra):
- Biometrics: By deploying biometric trusted applets in an remoted digital machine, builders may have the isolation assure, entry to extra compute energy for biometric algorithms, simple updatability whatever the Trustzone working system, and a extra streamlined deployment.
- DRM: Widevine allows streaming DRM on Android gadgets. As soon as deployed in an remoted Digital Machine, updates to Widevine change into a lot simpler throughout Android gadgets, whatever the particulars of the varied Trustzone working methods being deployed on these gadgets.
AVF Utilization
AVF supplies simple APIs to question the machine’s capability to create digital machines and their supported sorts, and to arrange safe communication channels with these digital machines from purposes and companies that create them.
For instance, to test for the supply of the AVF APIs, and of remoted and common VM:
VirtualMachineManager supervisor =
(VirtualMachineManager)context.
getSystemService(VirtualMachineManager.class);
if (supervisor == null) {
// AVF not supported
} else {
int capabilities = supervisor.getCapabilities();
if ((capabilities & CAPABILITY_PROTECTED_VM) != 0) {
// protected VM is supported
}
if ((capabilities & CAPABILITY_NON_PROTECTED_VM) != 0) {
// non protected VM is supported
}
}
Please discover further documentation on AVF and its APIs right here.
AVF Elements
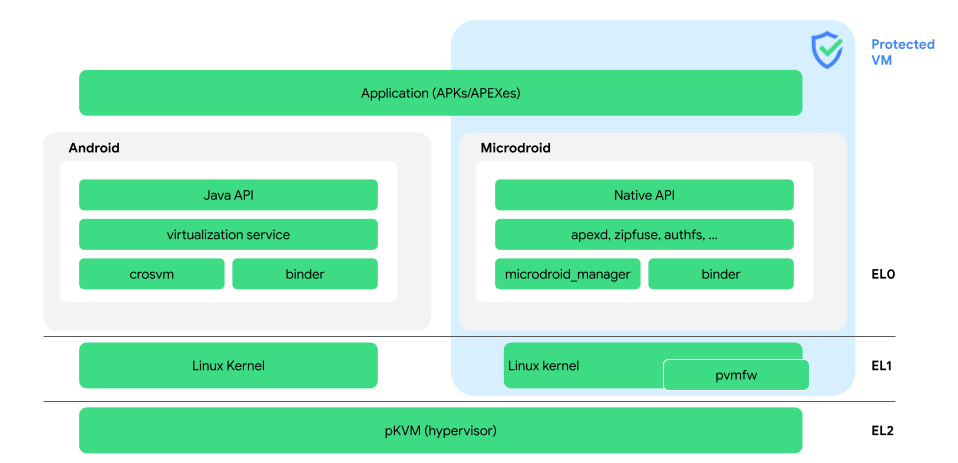
AVF consists of the framework APIs, the hypervisor, and the Digital Machine Supervisor. The hypervisor ensures digital machines (together with Android) are remoted from one another, very like how the Linux kernel does it for processes. The AVF hypervisor (pKVM), nonetheless, does that with a considerably smaller (~50x) code base in comparison with the Linux kernel.
The Hypervisor (pKVM)
The hypervisor is concentrated on open supply availability, safety, machine task to VMs and safety by isolation between digital machines. It has a small assault floor that meets a better safety assurance degree. AVF APIs and options are totally supported by the protected KVM hypervisor (pKVM).
pKVM is constructed on prime of the business normal Kernel-based Digital Machine (KVM) in Linux. It means all current working methods and workloads that depend on KVM-based digital machines can work seamlessly on Android gadgets with pKVM.
Digital Machine Supervisor (crosvm)
crosvm, a Rust-based Digital Machine Supervisor (VMM), supplies the glue between the hypervisor and the AVF framework. It’s liable for creating, managing and destroying digital machines. As well as, it supplies an abstraction layer throughout a number of hypervisor implementations.
Remoted Digital Machines
Remoted digital machines are invisible to Android i.e. any course of operating in Android can’t examine, see, tamper with the content material of such a digital machine. This assure is supplied by the hypervisor.
Digital Machines
Digital machines are the identical as remoted VMs, besides they’re accessible to Android processes with the appropriate permissions and privilege.
Microdroid
Microdroid is a trimmed down Android OS bundle that’s created to function a template for beginning a digital machine (VM). It supplies builders with a well-recognized surroundings to construct and run their workloads in a VM. Microdroid makes use of acquainted Android instruments and libraries, reminiscent of Bionic, Binder IPC and keystore help.
Virtualization Service
VirtualizationService manages all visitor VMs, remoted or in any other case. It does so, primarily by managing cases of crosvm. It additionally exposes an AIDL API, which system companies or privileged apps can use to begin, monitor, and cease VMs.
RpcBinder
RpcBinder is an all-new backend developed for the Android Interface Definition Language (AIDL). RpcBinder allows communication to and from digital machines utilizing the prevailing binder wire protocol. This implies:
- Builders can write interfaces to digital machines utilizing the language and infrastructure they’re already accustomed to – AIDL.
- Merely proceed utilizing current AIDL interfaces even when the binder endpoint strikes right into a digital machine.
What’s new in Android 14?
Android 14, not solely makes AVF obtainable on extra gadgets, it additionally supplies a brand new toolkit to allow constructing extra with AVF and its elements:
- Android System API for AVF
Privileged purposes can now use VMs for executing their vital workload needing isolation;
- Hypervisor DevEx toolkit
Added tracing functionality, improved debuggability and monitoring capabilities to supply insights and help platform builders in creating inside Remoted VMs;
- Hypervisor Vendor Modules
With vendor module extensions, our companions can customise Google’s hypervisor (pKVM) to fulfill their particular want and differentiate themselves;
- System Well being Enhancements
With Android 14, a microdroid primarily based VM boots 2 occasions sooner in comparison with Android 13 whereas utilizing half the reminiscence.


