On this four-part weblog sequence “Classes discovered from constructing Cybersecurity Lakehouses,” we’re discussing numerous challenges organizations face with information engineering when constructing out a Lakehouse for cybersecurity information, and provide some options, suggestions, methods, and greatest practices that we have now used within the subject to beat them.
In half one, we started with uniform occasion timestamp extraction. In half two, we checked out the right way to spot and deal with delays in log ingestion. And in half three, we tackled the right way to parse semi-structured, machine-generated information. On this remaining a part of the sequence, we talk about probably the most essential points of cyber analytics: information normalization utilizing a typical info mannequin.
By the top of this weblog, you’ll have a stable understanding of a number of the points confronted when normalizing information right into a Cybersecurity Lakehouse and the strategies we are able to use to beat them.
What’s a Frequent Data Mannequin (CIM)?
A Frequent Data Mannequin (CIM) is required for cyber safety analytics engines to facilitate efficient communication, interoperability, and understanding of security-related information and occasions throughout disparate programs, purposes, and units inside a company.
Organizations have completely different programs and purposes that generate logs and occasions in several buildings and codecs. A CIM supplies a standardized mannequin that defines widespread information buildings, attributes, and relationships. This standardization permits analytics engines to normalize and harmonize information collected from disparate sources, making it simpler to course of, analyze, and correlate info successfully.
Why use a Frequent Data Mannequin?
Organizations use quite a lot of safety instruments, purposes, and units from completely different distributors, which generate logs particular to their respective applied sciences. Normalizing information right into a recognized set of buildings with constant and comprehensible naming conventions is essential to allow information correlation, menace detection, and incident response capabilities.
As a working instance, suppose we wished to know which programs and purposes person ‘Joe’ has efficiently authenticated towards throughout the final 30 days.
To reply this query with no single mannequin to interrogate, an analyst could be required to craft queries to go looking tens or a whole lot of logs. Every log file studies the username and the results of any authentication outcomes (success or failure) as completely different subject names with completely different values. The app subject title may be completely different in addition to the occasion time. This isn’t a workable answer. Enter the Frequent Data Mannequin and the normalization course of!
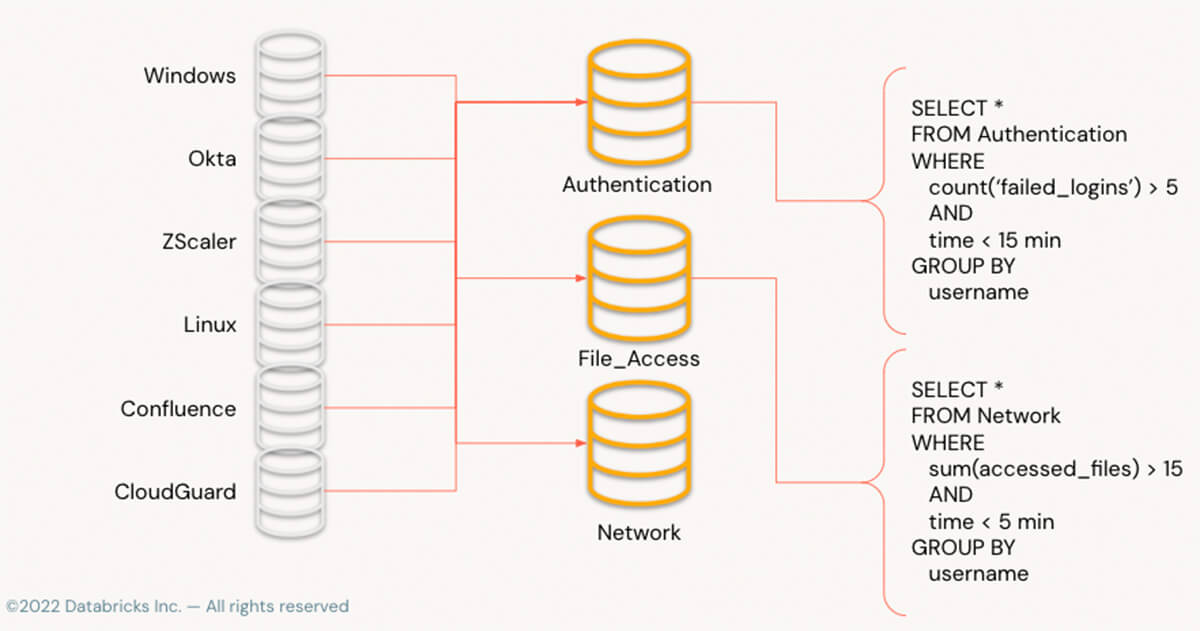
The picture above reveals how disparate logs from many sources filter occasions into event-specific tables, utilizing recognized column names, permitting a single easy question to reply the query as soon as information has been normalized.
Issues to think about when normalizing information
There are a variety of situations that needs to be accounted for when normalizing disparate information sources right into a single CIM-compliant desk:
Differing Column Sorts: Unifying disparate information sources and particular occasions into the CIM (event-driven) desk could have clashing information sorts.
Derived Fields: The normalization course of typically requires new fields to be derived from a number of supply columns.
Lacking Fields: Fields could unexpectedly not exist or include null values. Make sure the CIM caters to lacking or null worth information sorts.
Literal Fields: Information to assist a goal CIM subject could should be created, or the sector could should be set to a literal worth resembling “Success” or “Failure” to make sure a unified search functionality. For instance (the place motion=”Success”)
Schema Evolution: Each information and the CIM could evolve over time. Guarantee you might have a mechanism to supply backward compatibility, particularly throughout the CIM tables, to cater for adjustments in information.
Enrichment: CIM information is usually enriched with different context resembling menace information and asset info. Think about the right way to add this info to supply a complete view of the occasions collected.
Which mannequin ought to I select?
There are various widespread Data fashions to select from when constructing out a Cybersecurity Lakehouse, from open supply fashions to vendor-specific publically obtainable fashions. The choice on what to make use of relies upon primarily in your particular person use case.
Some concerns are:
- Are you augmenting Delta Lake with one other SIEM or SOAR product? Does it make sense to undertake that one for simpler integration?
- Are you solely constructing a Cybersecurity Lakehouse for a selected use case? For example, do you solely need to analyze Microsoft endpoint information? If that’s the case, does it make sense to align with Microsoft ASIM mannequin?
- Are you constructing out a Lakehouse as your group’s predominant cyber analytics platform? Does it make sense to align with an open supply mannequin like OCSF or OSSEM or construct your personal?
Finally, the selection is organizational-specific, relying in your wants. One other consideration is the completeness of the mannequin you select. Fashions are generic and can doubtless require some adaptation to suit your wants; nevertheless they need to primarily assist your information and necessities earlier than you start adopting the mannequin, as mannequin adjustments after the actual fact are time-consuming.
Ideas and greatest practices
Whatever the mannequin you select, there are a couple of suggestions to make sure gaps don’t exist in your total safety posture.
- Most queries rely closely on entities. Supply host, vacation spot host, supply person, and utility used are doubtless probably the most looked for columns in any desk. Guarantee these are well-mapped and normalized.
- Fashions sometimes present steerage on subject protection (necessary, really helpful, optionally available). Guarantee at a minimal that necessary fields are mapped and have information integrity checks utilized tfor a constant search setting.
Conclusion
Frequent Data Mannequin-based tables are a cornerstone of an efficient cyber analytics platform. The mannequin you undertake when constructing out a Cybersecurity Lakehouse is organization-specific, however any mannequin ought to largely be appropriate in your group’s wants earlier than you start. Databricks has beforehand solved this drawback for purchasers utilizing the rules outlined within the weblog.
Get in Contact
If you wish to be taught extra about how Databricks cyber options can empower your group to establish and mitigate cyber threats, contact [email protected] and take a look at our Lakehouse for Cybersecurity Functions webpage.


