
The operator of the Nokoyawa ransomware-as-a-service (RaaS), a menace actor generally known as ‘farnetwork’, constructed expertise over time by serving to the JSWORM, Nefilim, Karma, and Nemty affiliate applications with malware growth and operation administration.
A report from cybersecurity firm Group-IB offers perception into farnetwork’s exercise and the way they step by step constructed their profile as a extremely energetic participant within the ransomware enterprise.
In interactions with menace intelligence analysts, farnetwork shared beneficial particulars that hyperlink them to ransomware operations beginning 2019 and a botnet with entry to a number of company networks.
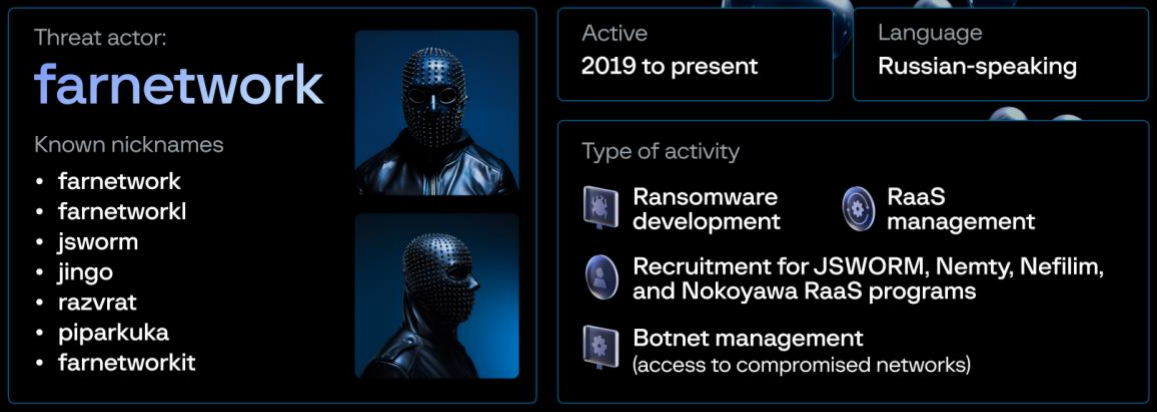
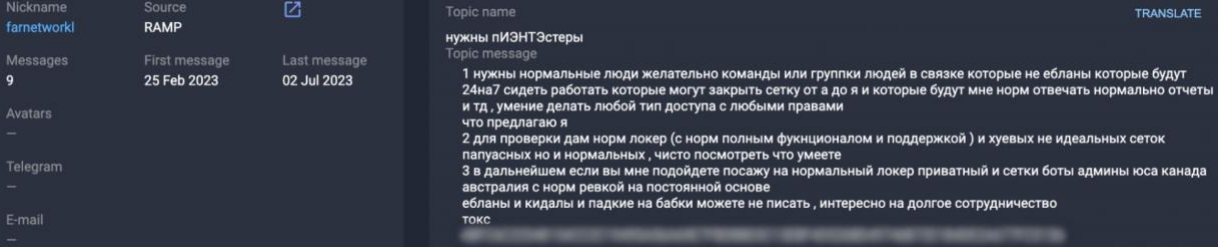
In line with a report Group-IB shared with BleepingComputer, the menace actor has a number of usernames (e.g. farnetworkl, jingo, jsworm, razvrat, piparkuka, and farnetworkitand) and has been energetic on a number of Russian-speaking hacker boards attempting to recruit associates for varied ransomware operations.
In March, although, farnetwork began searching for associates for his or her ransomware-as-a-service program based mostly on the Nokoyawa locker. Nevertheless, Group-IB’s menace intelligence analysts say that the actor made it clear that they weren’t concerned within the growth of Nokoyawa.
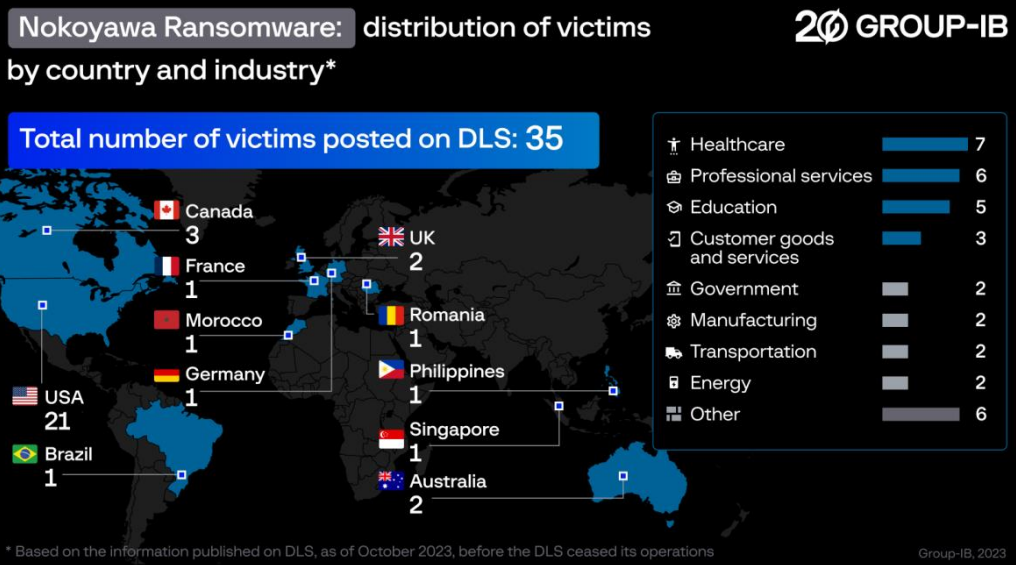
Working the RaaS enterprise did not final very lengthy as farnetwork introduced lately that they might retire from the scene and in October they shut down the Nokoyawa RaaS program, after leaking knowledge of 35 victims.
Nevertheless, Group-IB believes that this transfer is a part of the menace actor’s technique to lose their tracks and begin afresh underneath a brand new model
Operations supervisor
In Nokoyawa ransomware, farnetwork acted as a undertaking chief, affiliate recruiter, promoter of the RaaS on darknet boards, and botnet supervisor.
The botnet enabled associates direct entry to already compromised networks. For this perk, they might pay the botnet proprietor 20% from the collected ransom and the ransomware proprietor would get 15%.
A 65% minimize for the ransomware affiliate might look like a foul deal, contemplating that different applications pay as much as 85% of the ransom, however the price lined the hassle of discovering an acceptable goal and breaching it.
Farnetwork examined affiliate candidates by offering them with a number of company account credentials sourced from the Underground Cloud of Logs (UCL) service, which sells logs stolen by info-stealers resembling RedLine, Vidar, and Raccoon.
The associates had been anticipated to escalate their privileges on the community, steal information, run the encryptor, and demand a ransom cost.
Timeline of previous actions
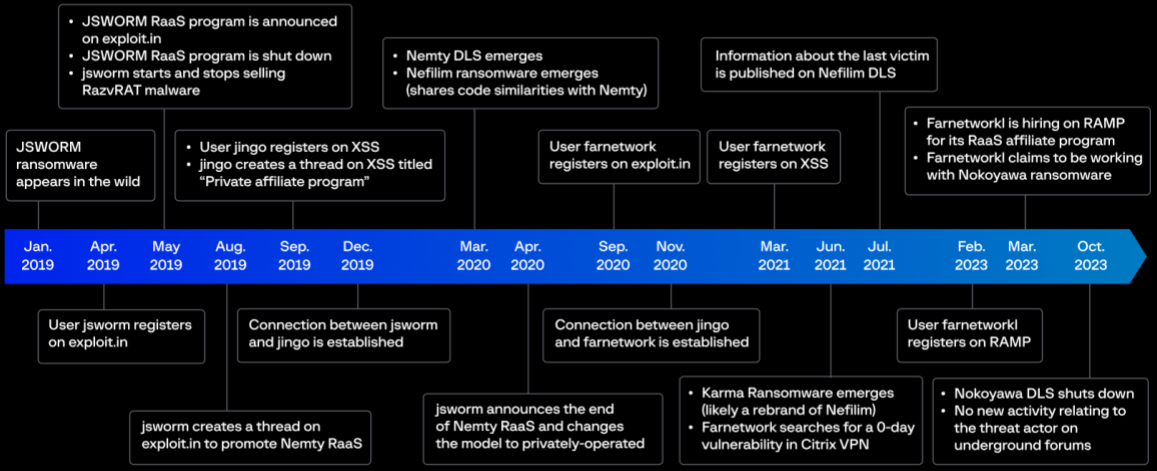
Group-IB has been capable of observe farnetwork’s actions way back to January 2019 and located connections to the JSWORM, Nemty, Nefilim, and Karma ransomware strains.
In April 2019, farnetwork promoted the JSWORM RaaS program on the Exploit hacker discussion board, the place the menace actor marketed the RazvRAT malware.
In August 2019, after JSWORM shut down, the menace actor switched to selling Nemty on at the least two Russian-speaking underground boards.
In March 2020, Nefilim ransomware emerged as a brand new associates program with a knowledge leak web site known as Company Leaks. The subsequent month, farnetwork introduced that Nemty would go non-public.
In June 2021, a doubtless rebrand of Nefilim known as Karma appeared, and in July 2021, Nefilim went silent. Throughout that point, farnetwork was searching for details about a zero-day vulnerability in Citrix VPN.
In February 2023, farnetwork pivoted to the RAMP discussion board saying they had been working with the Nokoyawa ransomware as a recruiter and entry supervisor.
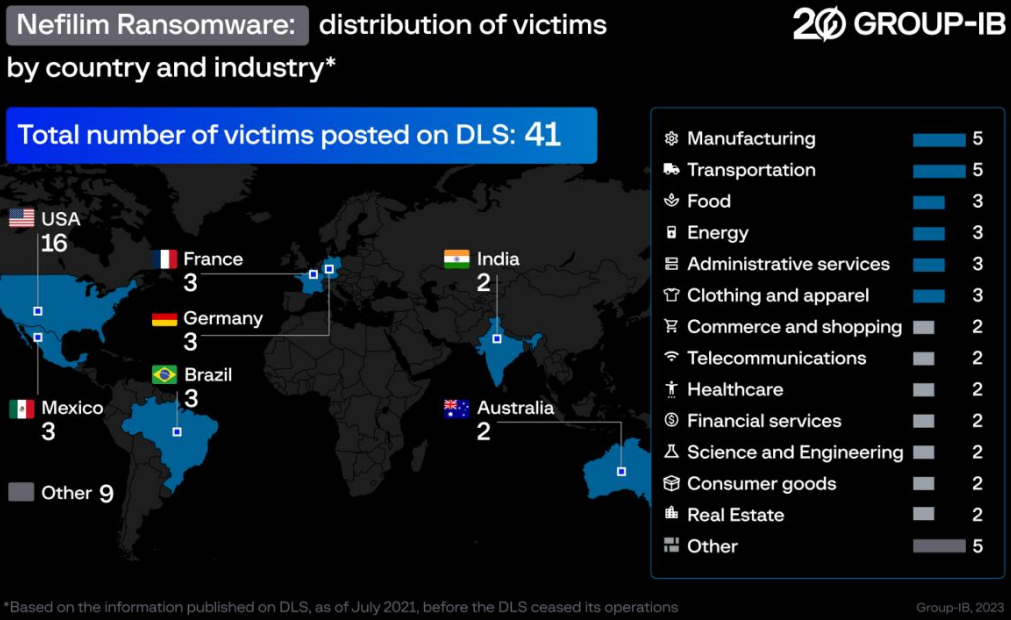
Based mostly on Group-IB’s findings, farnetwork is suspected to have been concerned in growing or at the least within the evolution and administration of the talked about ransomware strains. The strongest ties are with Nefilim and Karma, each thought of evolutions of Nemty.
Group-IB managed to attach the completely different usernames to the identical menace actor, displaying that ransomware operations can come and go however behind them are seasoned people that hold the enterprise going underneath new names.

