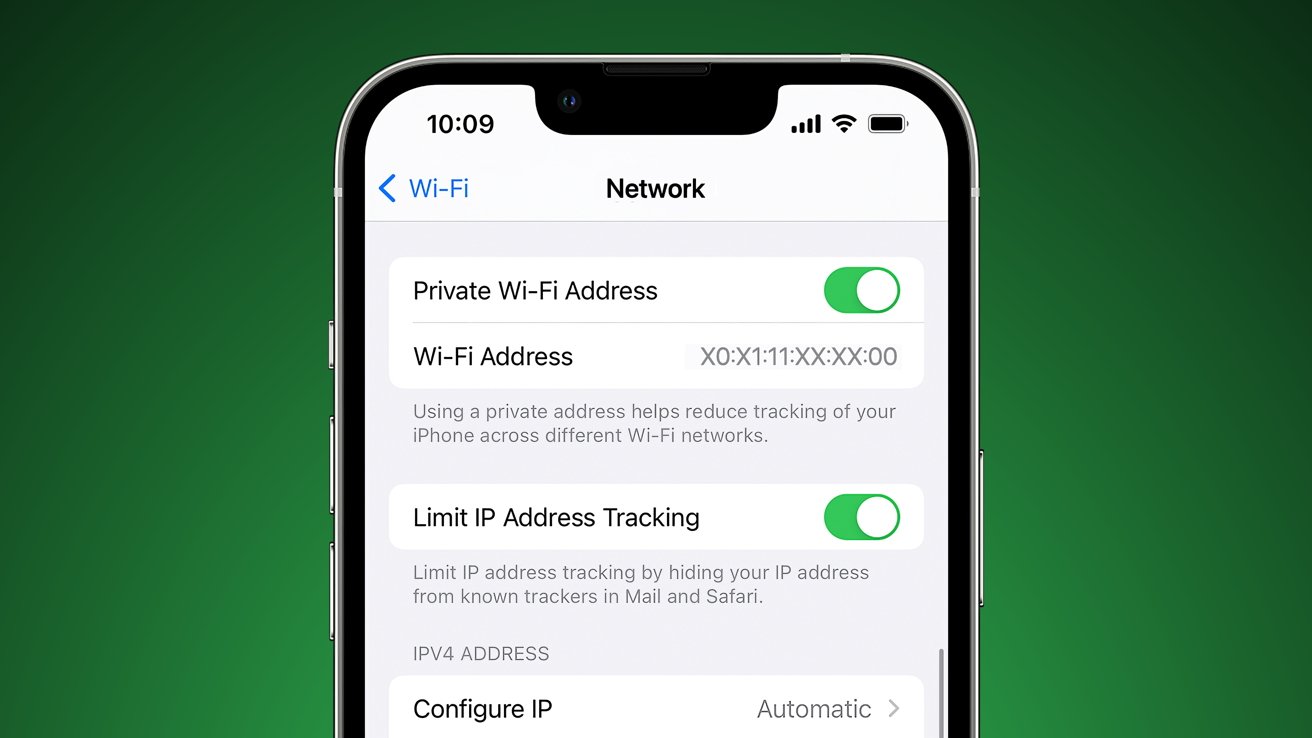
Apple launched a characteristic that may cover a consumer’s everlasting MAC tackle in 2020, but it surely’s been just about ineffective till iOS 17.1 due to a now patched vulnerability.
When a tool connects to a community, it performs a needed handshake, sharing its distinctive MAC tackle. If an entity can entry the MAC addresses accessing networks at a big sufficient scale, they may observe customers as they transfer between networks.
In keeping with a report from Ars Technica, Apple carried out a characteristic that may stop MAC tackle monitoring, however a vulnerability has rendered it just about ineffective since it debuted in iOS 14. The Non-public Wi-Fi Deal with characteristic is enabled by default and guarantees to assign a unique MAC tackle to each distinctive SSID, which it did in follow.
The issue is the everlasting MAC tackle that was supposedly being obfuscated by this characteristic was nonetheless being shared by port 5353/UDP. Primary MAC tackle sniffing was curtailed, however anybody wanting may simply discover the true MAC tackle, which presents an issue for these anticipating this characteristic to work.
The report means that this is able to have been a easy repair, and it is not clear why Apple took three years to implement it. Basic customers needn’t fear about this vulnerability, however anybody who wanted to cover their MAC tackle and anticipated the characteristic to work may have had their MAC tackle compromised.
Apple experiences that the vulnerability has been patched in iOS 17.1. It was tracked as CVE02923-42846 and credited to Talal Haj Bakry and Tommy Mysk.