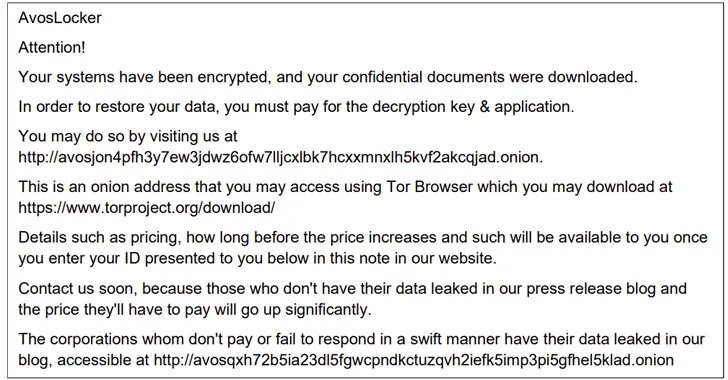
The AvosLocker ransomware gang has been linked to assaults in opposition to vital infrastructure sectors within the U.S., with a few of them detected as not too long ago as Could 2023.
That is in keeping with a brand new joint cybersecurity advisory launched by the U.S. Cybersecurity and Infrastructure Safety Company (CISA) and the Federal Bureau of Investigation (FBI) detailing the ransomware-as-a-service (RaaS) operation’s techniques, methods, and procedures (TTPs).
“AvosLocker associates compromise organizations’ networks by utilizing legit software program and open-source distant system administration instruments,” the businesses mentioned. “AvosLocker associates then use exfiltration-based knowledge extortion techniques with threats of leaking and/or publishing stolen knowledge.”
The ransomware pressure first emerged on the scene in mid-2021, and has since leveraged subtle methods to disable antivirus safety as a detection evasion measure. It impacts Home windows, Linux, and VMware ESXi environments.
A key hallmark of AvosLocker assaults is the reliance on open-source instruments and living-off-the-land (LotL) techniques, leaving no traces that would result in attribution. Additionally used are legit utilities like FileZilla and Rclone for knowledge exfiltration in addition to tunneling instruments akin to Chisel and Ligolo.
Command-and-control (C2) is achieved via Cobalt Strike and Sliver, whereas Lazagne and Mimikatz are used for credential theft. The assaults additionally make use of customized PowerShell and Home windows Batch scripts for lateral motion, privilege escalation, and disarming safety software program.
“AvosLocker associates have uploaded and used customized net shells to allow community entry,” the businesses famous. One other new element is an executable named NetMonitor.exe that masquerades as a community monitoring instrument however truly capabilities as a reverse proxy to permit the menace actors to connect with the host from exterior the sufferer’s community.
CISA and FBI are recommending vital infrastructure organizations to implement obligatory mitigations to cut back the probability and affect of AvosLocker ransomware and different ransomware incidents.
This consists of adopting software controls, limiting the usage of RDP and different distant desktop providers, limiting PowerShell use, requiring phishing-resistant multi-factor authentication, segmenting networks, protecting all programs up-to-date, and sustaining periodic offline backups.
The event comes as Mozilla warned of ransomware assaults leveraging malvertising campaigns that trick customers into putting in trojanized variations of Thunderbird, in the end resulting in the deployment of file-encrypting malware and commodity malware households akin to IcedID.
Ransomware assaults in 2023 have witnessed a significant surge, at the same time as menace actors are shifting swiftly to deploy ransomware inside someday of preliminary entry in additional than 50% of engagements, in keeping with Secureworks, dropping from the earlier median dwell time of 4.5 days in 2022.
What’s extra, in additional than 10 p.c of incidents, ransomware was deployed inside 5 hours.
“The motive force for the discount in median dwell time is probably going as a result of cybercriminals’ need for a decrease likelihood of detection,” Don Smith, vp of menace intelligence at Secureworks Counter Menace Unit, mentioned.
“Consequently, menace actors are specializing in easier and faster to implement operations, moderately than large, multi-site enterprise-wide encryption occasions which are considerably extra advanced. However the danger from these assaults remains to be excessive.”
Exploitation of public going through functions, stolen credentials, off-the-shelf malware, and exterior distant providers have emerged because the three largest preliminary entry vectors for ransomware assaults.
Per newest steering from CISA, distant desktop protocol (RDP), file switch protocol (FTP), TELNET, Server Message Block (SMB), and Digital Community Computing (VNC) are a few of the misconfigurations and weaknesses which are recognized to have been generally weaponized in ransomware campaigns.
To rub salt into the wound, the RaaS mannequin and the prepared availability of leaked ransomware code have lowered the barrier to entry for even novice criminals, making it a profitable avenue to make illicit earnings.
“Whereas we nonetheless see acquainted names as probably the most lively menace actors, the emergence of a number of new and really lively menace teams is fuelling a major rise in sufferer and knowledge leaks,” Smith added. “Regardless of excessive profile takedowns and sanctions, cybercriminals are masters of adaptation, and so the menace continues to collect tempo.”
Microsoft, in its annual Digital Protection Report, mentioned 70% of organizations encountering human-operated ransomware had fewer than 500 staff, and that 80 to 90 p.c of all compromises originate from unmanaged units.
Telemetry knowledge gathered by the corporate reveals that human-operated ransomware assaults have gone up greater than 200 p.c since September 2022. Magniber, LockBit, Hive, and BlackCat comprised nearly 65 p.c of all ransomware encounters.
On prime of that, roughly 16 p.c of current profitable human-operated ransomware assaults concerned each encryption and exfiltration, whereas a 13 p.c used exfiltration solely.
“Ransomware operators are additionally more and more exploiting vulnerabilities in much less widespread software program, making it tougher to foretell and defend in opposition to their assaults,” the tech large mentioned. “This reinforces the significance of a holistic safety strategy.”
Redmond mentioned it additionally noticed a “sharp enhance” in the usage of distant encryption throughout human-operated ransomware assaults, accounting for 60 p.c on common over the previous 12 months.
“As an alternative of deploying malicious recordsdata on the sufferer system, encryption is completed remotely, with the system course of performing the encryption, which renders process-based remediation ineffective,” Microsoft defined. “This can be a signal of attackers evolving to additional reduce their footprint.”