Ukrainian navy entities are the goal of a phishing marketing campaign that leverages drone manuals as lures to ship a Go-based open-source post-exploitation toolkit known as Merlin.
“Since drones or Unmanned Aerial Autos (UAVs) have been an integral software utilized by the Ukrainian navy, malware-laced lure information themed as UAVs service manuals have begun to floor,” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in a report shared with The Hacker Information.
The cybersecurity firm is monitoring the marketing campaign underneath the title STARK#VORTEX.
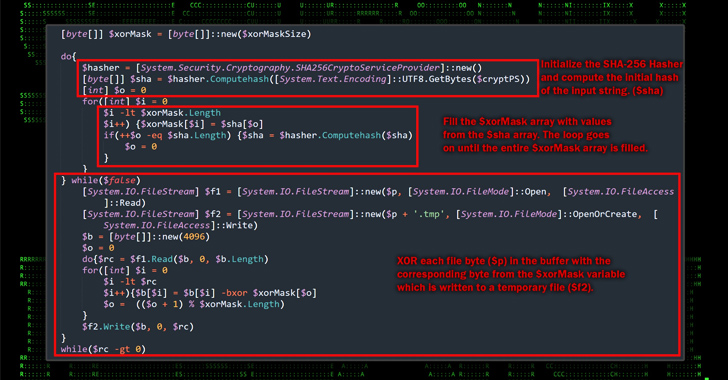
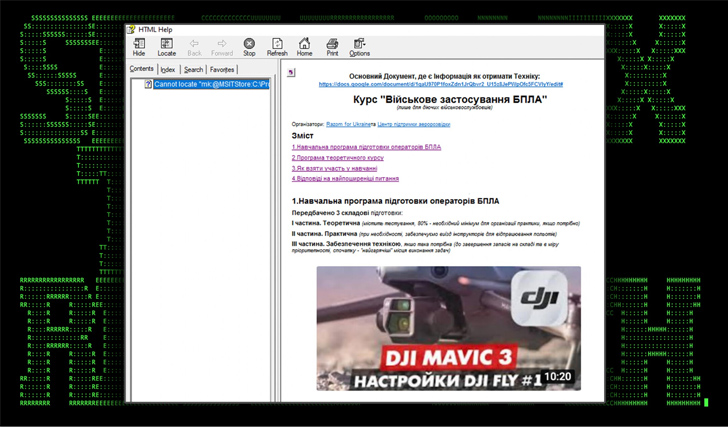
The place to begin of the assault is a Microsoft Compiled HTML Assist (CHM) file that, when opened, runs malicious JavaScript embedded inside one of many HTML pages to execute PowerShell code designed to contact a distant server to fetch an obfuscated binary.

The Home windows-based payload is decoded to extract the Merlin Agent, which, in flip, is configured to speak with a command-and-control (C2) server for post-exploitation actions, successfully seizing management over the host.
“Whereas the assault chain is kind of easy, the attackers leveraged some fairly advanced TTPs and obfuscation strategies with a purpose to evade detection,” the researchers mentioned.
That is the primary time Ukrainian authorities organizations have been focused utilizing Merlin. In early August 2023, the Laptop Emergency Response Workforce of Ukraine (CERT-UA) disclosed an analogous assault chain that employs CHM information as decoys to contaminate the computer systems with the open-source software.
CERT-UA attributed the intrusions to a risk actor it displays underneath the title UAC-0154.
“Recordsdata and paperwork used within the assault chain are very able to bypassing defenses,” the researchers defined.
Battle AI with AI — Battling Cyber Threats with Subsequent-Gen AI Instruments
Able to deal with new AI-driven cybersecurity challenges? Be a part of our insightful webinar with Zscaler to deal with the rising risk of generative AI in cybersecurity.
“Sometimes receiving a Microsoft assist file over the web can be thought of uncommon. Nonetheless, the attackers framed the lure paperwork to seem as one thing an unsuspecting sufferer may anticipate to seem in a help-themed doc or file.”
The event arrives weeks after the CERT-UA mentioned it detected an unsuccessful cyber assault towards an unnamed crucial vitality infrastructure facility within the nation undertaken by the Russian state-sponsored crew known as APT28.