
New malware named HTTPSnoop and PipeSnoop are utilized in cyberattacks on telecommunication service suppliers within the Center East, permitting menace actors to remotely execute instructions on contaminated gadgets.
The HTTPSnoop malware interfaces with Home windows HTTP kernel drivers and gadgets to execute content material on the contaminated endpoint based mostly on particular HTTP(S) URLs, and the PipeSnoop accepts and executes arbitrary shellcode from a named pipe.
In response to a report by Cisco Talos, the 2 implants belong to the identical intrusion set named ‘ShroudedSnooper’ however serve totally different operational objectives by way of the extent of infiltration.
Each implants are masqueraded as safety elements of the Palo Alto Networks Cortex XDR product to evade detection.
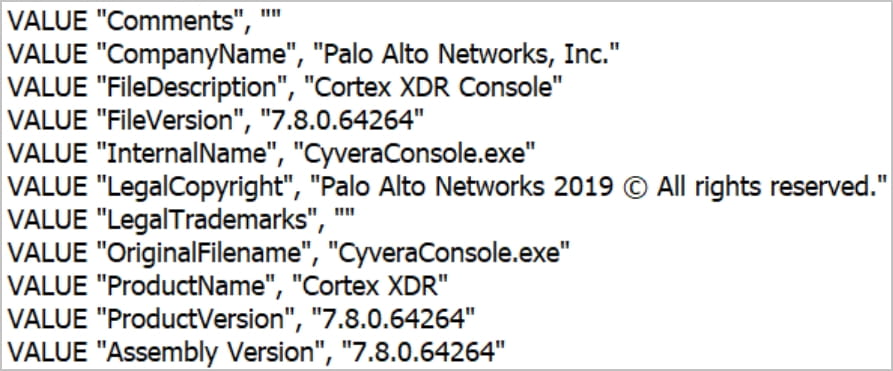
HTTPSnoop
HTTPSnoop makes use of low-level Home windows APIs to watch HTTP(S) site visitors on an contaminated system for particular URLs. When detected, the malware will decode incoming base64-encoded knowledge from these URLs and run it as a shellcode on the compromised host.
The implant, which prompts on the goal system through DLL hijacking, consists of two elements: the stage 2 shellcode that units up a backdoor internet server via kernel calls and its configuration.
HTTPSnoop establishes a listening loop that waits for incoming HTTP requests and processes legitimate knowledge upon arrival; in any other case, it returns an HTTP 302 redirect.
The acquired shellcode is decrypted and executed, and the execution result’s returned to the attackers as base64-encoded XOR-encoded blobs.
The implant additionally ensures no URL clashes with beforehand configured URLs on the server.
Cisco has seen three variants of HTTPSnoop, every utilizing totally different URL listening patterns. The primary hear for generic HTTP URL-based requests, the second for URLs imitating Microsoft Alternate Internet Service, and the third for URLs emulating OfficeCore’s LBS/OfficeTrack and telephony functions.
These variants have been sampled between April 17 and April 29, 2023, with the latest one having the least variety of URLs it listens for, possible for elevated stealth.
Mimicking authentic URL patterns from Microsoft Alternate Internet Companies and OfficeTrack makes malicious requests almost indistinguishable from benign site visitors.
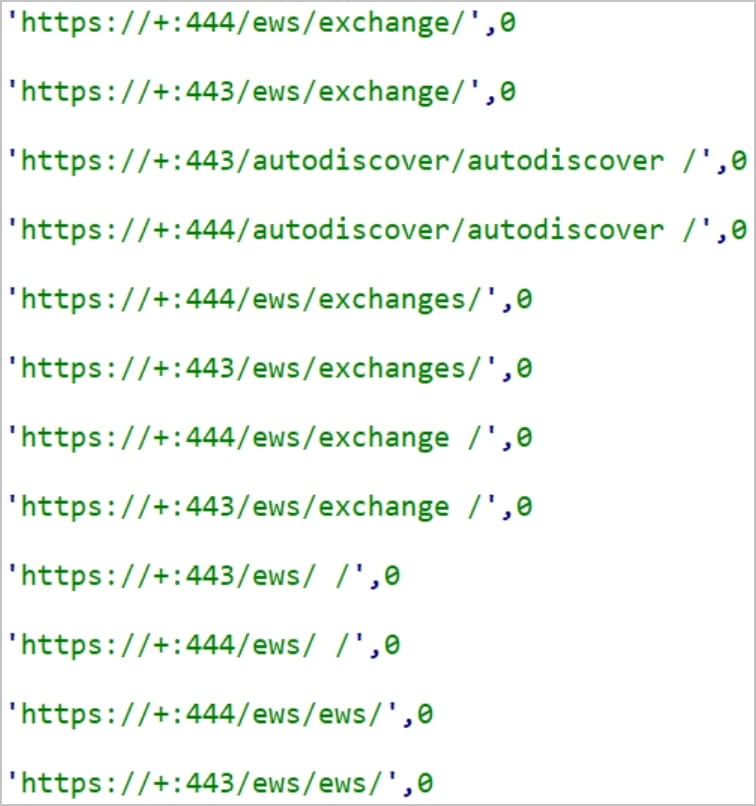
PipeSnoop
Cisco first noticed the PipeSnoop implant in Could 2023, appearing as a backdoor that executes shellcode payloads on breached endpoints via Home windows IPC (Inter-Course of Communication) pipes.
The analysts be aware that opposite to HTTPSnoop, which seems to focus on public-facing servers, PipeSnoop is extra fitted to operations deep inside compromised networks.
Cisco additionally notes that the implant wants a element that provides the shellcode. Nonetheless, its analysts haven’t been capable of determine it.
Telecommunication service suppliers usually grow to be targets of state-sponsored menace actors on account of their essential function in operating essential infrastructure and relaying extraordinarily delicate info via networks.
The latest surge in state-sponsored assaults towards telecom entities underscores the pressing want for enhanced safety measures and worldwide cooperation to safeguard them.

