The content material of this submit is solely the accountability of the creator. AT&T doesn’t undertake or endorse any of the views, positions, or data supplied by the creator on this article.
Within the realm of data safety and covert communication, picture steganography serves as a robust method for hiding delicate knowledge inside innocent-looking photographs. By embedding secret messages or recordsdata inside the pixels of a picture, steganography permits covert transmission with out arousing suspicion. This text goals to delve into the world of picture steganography, exploring its ideas, strategies, and real-world purposes.
Understanding picture steganography
- Picture steganography is the observe of concealing data inside the knowledge of digital photographs with out altering their visible look. The hidden knowledge can embrace textual content, photographs, audio, or another type of binary data.
- Picture steganography serves as a clandestine communication technique, offering a way to transmit delicate data with out arousing the suspicion of adversaries or unauthorized people. It presents a further layer of safety and confidentiality in digital communication.
- Steganography vs. Cryptography: Whereas cryptography focuses on encrypting knowledge to render it unreadable, steganography goals to cover the existence of the information itself, making it inconspicuous inside a picture. Steganography can be utilized at the side of encryption to additional improve the safety of covert communication.
Strategies of picture steganography
- LSB substitution: The Least Important Bit (LSB) substitution technique entails changing the least important bits of pixel values with secret knowledge. Because the least important bits have minimal influence on the visible look of the picture, this method permits for the hiding of data with out noticeably altering the picture.
- Spatial area strategies: Varied spatial area strategies contain modifying the pixel values on to embed secret knowledge. These strategies embrace modifying pixel intensities, colour values, or rearranging pixels based mostly on a predefined sample.
- Remodel area strategies: Remodel area strategies, akin to Discrete Cosine Remodel (DCT) or Discrete Fourier Remodel (DFT), manipulate the frequency area illustration of a picture to embed secret knowledge. This permits for the concealment of data inside the frequency parts of a picture.
- Unfold spectrum strategies: Impressed by radio frequency communication, unfold spectrum strategies unfold the key knowledge throughout a number of pixels by barely modifying their values. This technique makes the hidden knowledge extra strong in opposition to detection and extraction makes an attempt.
- Adaptive steganography: Adaptive strategies dynamically modify the embedding course of based mostly on the picture content material and native traits, making the hidden knowledge much more proof against detection. This strategy enhances safety and makes it more durable for adversaries to establish stego photographs.
Let’s see a working instance of picture steganography utilizing a free software known as OpenStego, the identical may be downloaded from right here. You can be required to have Java Runtime Setting for OpenStego to work in your system.
As soon as, you’ve put in OpenStego, you will notice its interface as proven under:
It has a number of choices together with Disguise Knowledge and Extract Knowledge – extra about these choices may be discovered at official documentation of the software.
We have to have two recordsdata, Message File (Which shall be hidden knowledge or knowledge we need to conceal) and Cowl File (The file which we are going to use as a canopy to cover the message file.)
I’ve downloaded two picture recordsdata for a similar.
Now, let’s conceal the message file which is a quote inside the duvet file which is “Hey” picture.
After that, you’ll have to present the listing and identify for the output file. The identical may be seen within the snapshot under:
You may as well select to encrypt the hidden knowledge in order that it isn’t accessible with no password. Click on Disguise knowledge after you have adopted all of the steps.
After the method is accomplished, a hit popup will seem on Openstego display screen.
Now, now we have 3 recordsdata and output file is the one which has the hidden picture.
If we evaluate the properties of the output file and canopy file, we are going to discover sure variations – like the dimensions worth shall be totally different.
Now, let’s delete the duvet file and message file and attempt to extract the information. In case you open the output file you received’t discover any distinction because it seems the identical as another picture file. Nevertheless, let’s attempt to extract knowledge utilizing OpenStego.
We’ve to pick out the trail of the file we want to extract knowledge from and supply a vacation spot folder for extraction. We even have to offer the password if any was chosen on the time of hiding the information.
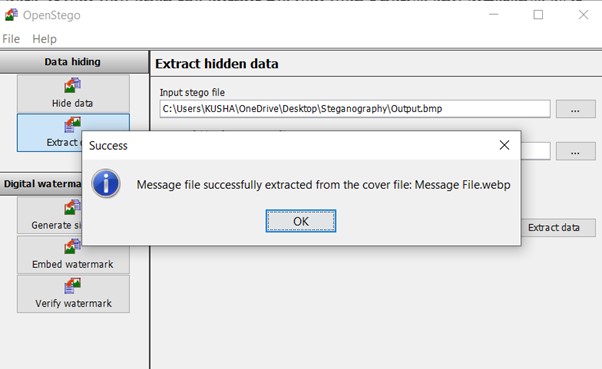
Let’s choose Extract knowledge. As soon as, the extraction is completed, a affirmation pop-up will seem in your display screen.
Allow us to test the extracted file by going to the vacation spot folder we assigned for the extraction of the message file.
As seen within the snapshot above, the message file is efficiently extracted.
Actual-world purposes of steganography
- Covert communication: Picture steganography finds purposes in covert communication the place events have to change delicate data discreetly. This contains intelligence companies, legislation enforcement, and whistleblowers who require safe channels for sharing categorised or confidential knowledge.
- Digital watermarking: Steganography strategies may be employed for digital watermarking to embed copyright data, possession particulars, or authentication codes inside photographs. This permits for monitoring and defending mental property rights.
- Data hiding in multimedia: Picture steganography may be prolonged to different types of multimedia, together with audio and video, permitting for the concealment of data inside these media codecs. This can be utilized for copyright safety, digital rights administration, or covert messaging.
- Steganalysis and forensics: Picture steganalysis focuses on detecting the presence of hidden data inside photographs. Forensic investigators can make use of steganalysis strategies to establish potential steganographic content material, aiding in digital investigations.
Conclusion
Picture steganography has emerged as a classy technique for covert communication and safe knowledge transmission. By exploiting the delicate nuances of digital photographs, delicate data may be hidden from prying eyes. As know-how advances, the sphere of steganography continues to evolve, with new strategies and algorithms being developed to reinforce the safety and robustness of information hiding.
Nevertheless, it’s important to stability using steganography with moral issues and cling to authorized frameworks to make sure its accountable and lawful software. As data safety stays a vital concern within the digital age, picture steganography serves as a priceless software in safeguarding delicate knowledge and enabling safe communications.