
Chinese language state-sponsored hackers have been focusing on industrial organizations with new malware that may steal knowledge from air-gapped programs.
Air-gapped programs sometimes fulfill important roles and are remoted from the enterprise community and the general public web both bodily or via software program and community units.
Researchers at cybersecurity firm Kaspersky found the brand new malware and attributed it to the cyber-espionage group APT31, a.ok.a. Zirconium.
In line with the findings, the hackers used at the least 15 distinct implants in assaults in Jap Europe, every for a definite stage of the operation, in addition to their signature ‘FourteenHi’ malware household.
Multi-stage assaults
Kaspesky says that the assaults began in April final 12 months and concerned three separate phases. The implants within the initial-phase established persistence and distant entry to the compromised programs and picked up knowledge helpful for reconnaissance.
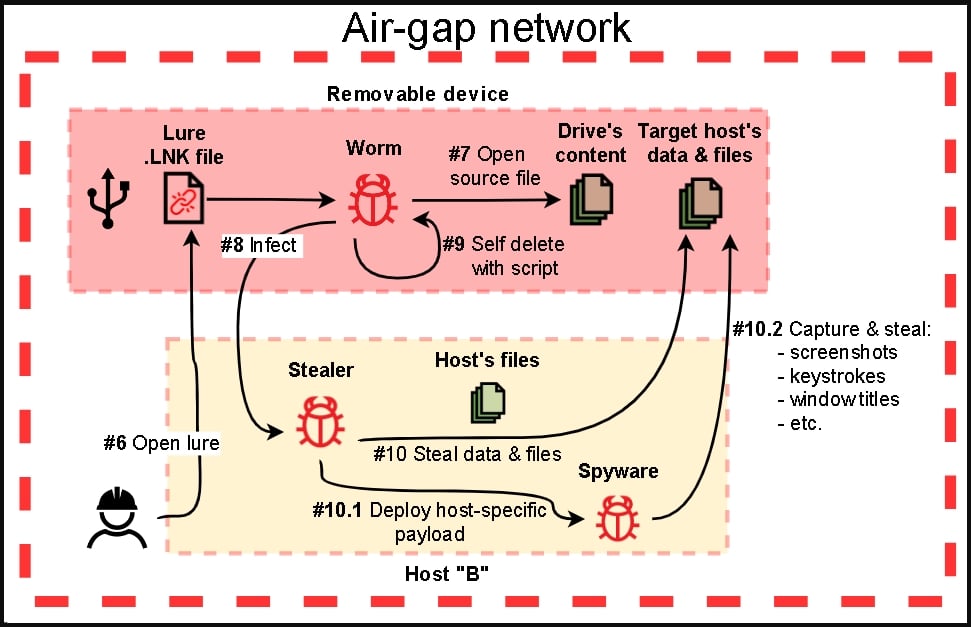
Within the second stage, APT31 drops extra specialised malware that may steal knowledge from remoted (air-gapped) programs utilizing USB propagation.
Lastly, within the third stage of the assault, the hackers use implants that may add the collected knowledge to their command and management (C2) servers.
The malware that targets remoted programs consists of 4 modules described beneath.
- First module: Profiles detachable drives related to the system, collects recordsdata, captures screenshots and window titles, and drops extra payloads on the contaminated gadget.
- Second module: Infects detachable drives by copying a reliable McAfee executable which is susceptible to DLL hijacking, and a malicious DLL payload onto the basis listing of the gadget, and units them as “hidden.” The software additionally creates a lure LNK file that triggers the an infection if the sufferer launches it.
- Third module: Executes a batch script to gather knowledge from the gadget and save the output to the “$RECYCLE.BIN” folder, from the place the primary module will gather it.
- Fourth module: Variant of the primary module seen in some assaults, acts as a payload dropper, keylogger, screenshot-capturing software, and file stealer.
In Might 2022, Kaspersky observed a further implant used within the APT31 assaults, designed to gather native recordsdata from breached programs.
That implant decrypts and injects its payload into the reminiscence of a reliable course of to evade malware detection, then sleeps for 10 minutes and ultimately copies all recordsdata that match the file sort extensions outlined in its configuration.
The stolen recordsdata are archived utilizing WinRAR (if not obtainable, the malware exits) after which saved in non permanent native folders created by the malware below “C:ProgramDataNetWorks.” In the end, the archives are exfiltrated to Dropbox.
Kaspersky underlines that the assaults have been stealthy and listed the next techniques, strategies, and procedures (TTPs): DLL order hijacking to load malicious payloads into reminiscence and conceal payloads in encrypted type in separate binary knowledge recordsdata.
The corporate offers a technical report that features extra knowledge comparable to malware hashes, a full set of indicators of compromise, and particulars in regards to the exercise of the malware from begin to end.
Air-gapped programs are a beautiful goal for APT teams, who sometimes flip to USB drives to ship malware and exfiltrate knowledge from the remoted surroundings.

