[This is Part III in a series on research conducted for a recent Hulu documentary on the 2015 hack of marital infidelity website AshleyMadison.com.]
In 2019, a Canadian firm known as Defiant Tech Inc. pleaded responsible to working LeakedSource[.]com, a service that bought entry to billions of passwords and different information uncovered in numerous information breaches. KrebsOnSecurity has discovered that the proprietor of Defiant Tech, a 32-year-old Ontario man named Jordan Evan Bloom, was employed in late 2014 as a developer for the marital infidelity web site AshleyMadison.com. Bloom resigned from AshleyMadison citing well being causes in June 2015 — lower than one month earlier than unidentified hackers stole information on 37 million customers — and launched LeakedSource three months later.

Jordan Evan Bloom, posing in entrance of his Lamborghini.
On Jan. 15, 2018, the Royal Canadian Mounted Police (RCMP) charged then 27-year-old Bloom, of Thornhill, Ontario, with promoting stolen private identities on-line by the web site LeakedSource[.]com.
LeakedSource was marketed on a lot of common cybercrime boards as a service that might assist hackers break into worthwhile or high-profile accounts. LeakedSource additionally tried to go itself off as a authorized, reputable enterprise that was advertising to safety corporations and professionals.
The RCMP arrested Bloom in December 2017, and mentioned he made roughly $250,000 promoting hacked information, which included data on 37 million person accounts leaked within the 2015 Ashley Madison breach.
Subsequent press releases from the RCMP concerning the LeakedSource investigation omitted any point out of Bloom, and referred to the defendant solely as Defiant Tech. In a authorized settlement that’s quintessentially Canadian, the matter was resolved in 2019 after Defiant Tech agreed to plead responsible. The RCMP didn’t reply to requests for remark.
A GREY MARKET
The Impression Workforce, the hacker group that claimed duty for stealing and leaking the AshleyMadison person information, additionally leaked a number of years value of electronic mail from then-CEO Noel Biderman. A evaluation of these messages reveals that Ashley Madison employed Jordan Evan Bloom as a PHP developer in December 2014 — despite the fact that the corporate understood that Bloom’s success as a programmer and businessman was tied to shady and legally murky enterprises.
Bloom’s suggestion got here to Biderman through Trevor Sykes, then chief expertise officer for Ashley Madison guardian agency Avid Life Media (ALM). The next is an electronic mail from Sykes to Biderman dated Nov. 14, 2014:
“Greetings Noel,
“We’d like to supply Jordan Bloom the place of PHP developer reporting to Mike Morris for 75k CAD/12 months. He did properly on the check, however he additionally has an awesome understanding of the enterprise facet of issues having run small companies himself. This was an inside referral.”
When Biderman responded that he wanted extra details about the candidate, Sykes replied that Bloom was independently rich on account of his forays into the shadowy world of “gold farming” — the semi-automated use of huge numbers of participant accounts to win some benefit that’s normally associated to cashing out recreation accounts or stock. Gold farming is especially prevalent in massively multiplayer on-line role-playing video games (MMORPGs), resembling RuneScape and World of Warcraft.
“In his earlier expertise he had been doing RMT (Actual Cash Buying and selling),” Sykes wrote. “That is the observe of promoting digital items in video games for actual world cash. It is a gray market, which is normally in opposition to the phrases and companies of the sport firms.” Right here’s the remainder of his message to Biderman:
“RMT sellers historically have numerous issues with chargebacks, and fee processor compliance. Throughout my interview with him, I spent a while focusing in on this. He needed to exhibit to the processor, Paypal, on the time he had a enterprise and technical technique to handle his cost again price.”
“He ran this firm himself, and did all of the coding, together with the mixing with the processors,” Sykes continued in his evaluation of Bloom. “Ultimately he was squeezed out by Chinese language gold farmers, and their capability to market with way more funding than he may. As well as the price of ‘farming’ the digital items was cheaper in China to do than in North America.”
COME, ABUSE WITH US
The gold farming reference is fascinating as a result of in 2017 KrebsOnSecurity printed Who Ran LeakedSource?, which examined clues suggesting that one of many directors of LeakedSource additionally was the admin of abusewith[.]us, a web site unabashedly devoted to serving to individuals hack electronic mail and on-line gaming accounts.

An administrator account Xerx3s on Abusewithus.
Abusewith[.]us started in September 2013 as a discussion board for studying and educating easy methods to hack accounts at Runescape, an MMORPG set in a medieval fantasy realm the place gamers battle for kingdoms and riches.
The foreign money with which Runescape gamers purchase and promote weapons, potions and different in-game gadgets are digital gold cash, and plenty of of Abusewith[dot]us’s early members traded in a handful of commodities: Phishing kits and exploits that might be used to steal Runescape usernames and passwords from fellow gamers; digital gold plundered from hacked accounts; and databases from hacked boards and web sites associated to Runescape and different on-line video games.
That 2017 report right here interviewed a Michigan man who acknowledged being administrator of Abusewith[.]us, however denied being the operator of LeakedSource. Nonetheless, the story famous that LeakedSource seemingly had a couple of operator, and breached information present Bloom was a prolific member of Abusewith[.]us.
In an electronic mail to all workers on Dec. 1, 2014, Ashley Madison’s director of HR mentioned Bloom graduated from York College in Toronto with a level in theoretical physics, and that he has been an lively programmer since highschool.
“He’s a proprietor of a excessive site visitors multiplayer recreation and developer/writer of utilities resembling PicTrace,” the HR director enthused. “He will likely be an awesome addition to the crew.”
PicTrace seems to have been a service that allowed customers to glean details about anybody who considered a picture hosted on the platform, resembling their Web handle, browser kind and model quantity. A replica of pictrace[.]com from Archive.org in 2012 redirects to the area qksnap.com, which DomainTools.com says was registered to a Jordan Bloom from Thornhill, ON that very same 12 months.
The road handle listed within the registration information for qksnap.com — 204 Beverley Glen Blvd — additionally reveals up within the registration information for leakadvisor[.]com, a website registered in 2017 simply months after Canadian authorities seized the servers working LeakedSource.
Pictrace, one in every of Jordan Bloom’s early IT successes.
A evaluation of passive DNS information from DomainTools signifies that in 2013 pictrace[.]com shared a server with only a handful of different domains, together with Close to-Actuality[.]com — a preferred RuneScape Personal Server (RSPS) recreation primarily based on the RuneScape MMORPG.
Copies of near-reality[.]com from 2013 through Archive.org present the highest of the neighborhood’s homepage was retrofitted with a message saying Close to Actuality was now not out there because of a copyright dispute. Though the positioning doesn’t specify the opposite social gathering to the copyright dispute, it seems Close to-Actuality acquired sued by Jagex, the proprietor of RuneScape.
The message goes on to say the web site will now not “encourage, facilitate, allow or condone (i) any infringement of copyright in RuneScape or another Jagex product; nor (ii) any breach of the phrases and circumstances of RuneScape or another Jagex product.”

A scene from the MMORPG RuneScape.
AGENTJAGS
Close to Actuality additionally has a Fb web page that was final up to date in 2019, when its proprietor posted a hyperlink to a information story about Defiant Tech’s responsible plea within the LeakedSource investigation. That Fb web page signifies Bloom additionally glided by the nickname “Agentjags.”
“Only a fast PSA,” reads a submit to the Close to Actuality Fb web page dated Jan. 21, 2018, which linked to a narrative concerning the expenses in opposition to Bloom and a photograph of Bloom standing in entrance of his lime-green Lamborghini. “Agentjags has acquired concerned in some shady shit that will have compromised your private particulars. I counsel anybody who’s utilizing an outdated NR [Near Reality] password for something remotely vital ought to change it ASAP.”
By the start of 2016, Bloom was nowhere to be discovered, and was suspected of getting fled his nation for the Caribbean, in line with the individuals commenting on the Close to Actuality Fb web page:
“Jordan aka Agentjags has gone lacking,” wrote a presumed co-owner of the Fb web page. “He’s supposedly hiding in St. Lucia, doing what he cherished, scuba-diving. Any data to his whereabouts will likely be appreciated.”
KrebsOnSecurity ran the bizarre nickname “AgentJags” by a search at Constella Intelligence, a business service that tracks breached information units. That search returned only a few dozen outcomes — and nearly all had been accounts at numerous RuneScape-themed websites, together with a half-dozen accounts at Abusewith[.]us.
Constella discovered different “AgentJags” accounts tied to the e-mail handle ownagegaming1@gmail.com. The advertising agency Apollo.io skilled an information breach a number of years again, and in line with Apollo the e-mail handle ownagegaming1@gmail.com belongs to Jordan Bloom in Ontario.
Constella additionally revealed that the password continuously utilized by ownagegaming1@gmail.com throughout many websites was some variation on “niggapls,” which my 2017 report discovered was additionally the password utilized by the administrator of LeakedSource.
Constella found that the e-mail eric.malek@rogers.com comes up when one searches for “AgentJags.” That is curious as a result of emails leaked from Ashley Madison’s then-CEO Biderman present that Eric Malek from Toronto was the Ashley Madison worker who initially really useful Bloom for the PHP developer job.
In response to DomainTools.com, Eric.Malek@rogers.com was used to register the area devjobs.ca, which beforehand marketed “essentially the most thrilling developer jobs in Canada, delivered to you weekly.” Constella says eric.malek@rogers.com additionally had an account at Abusewith[.]us — beneath the nickname “Jags.”
Biderman’s electronic mail information present Eric Malek was additionally a PHP developer for Ashley Madison, and that he was employed into this place only a few months earlier than Bloom — on Sept. 2, 2014.
The CEO’s leaked emails present Eric Malek resigned from his developer place at Ashley Madison on June 19, 2015 — simply 4 days earlier than Bloom would announce his departure. Each males left the corporate lower than a month earlier than the Impression Workforce introduced they’d hacked Ashley Madison, and each mentioned they had been leaving for health-related causes.
“Please observe that Eric Malek has resigned from this place with Avid and his final day will likely be June nineteenth,” learn a June 5, 2015 electronic mail from ALM’s HR director. “He’s resigning to cope with some private points which embrace well being points. As a result of he’s not certain how a lot time it can take to resolve, he’s not requesting a depart of absence (his time without work will likely be indefinite). Total, he likes the corporate and plans to succeed in out to Trevor or I when the problems are resolved to see what is offered at the moment.”
A follow-up electronic mail from Biderman demanded, “wish to know the place he’s actually going….,” and it’s unclear why there was friction with Malek’s departure. However ALM Common Counsel Avi Weisman replied indicating that Malek in all probability wouldn’t signal an “Exit Acknowledgment Type” previous to leaving, and that the corporate had unanswered questions for Malek.
“Aneka ought to dig throughout exit interview,” Weisman wrote. “Let’s see if he balks at signing the Acknowledgment.”
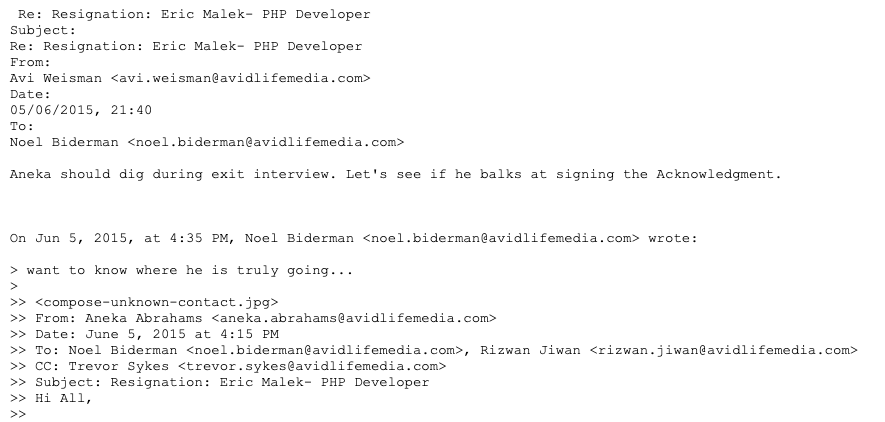
An electronic mail dated June 5, 2015, from ALM Common Counsel to Biderman, relating to an exit interview with Malek.
Bloom’s departure discover from Ashley Madison’s HR individual, dated June 23, 2015, learn:
“Please observe that Jordan Bloom has resigned from his place as PHP Developer with Avid. He’s leaving for private causes. He has a neck subject that can require surgical procedure within the upcoming months and due to his medical appointment schedule and the ache he’s experiencing he can now not decide to a full-time schedule. He could decide up contract work till he’s again to 100%.”
A follow-up observe to Biderman about this announcement learn:
“Be aware that he has disclosed that he’s independently rich so he can get by with out FT work till he’s on the mend. He has signed the Exit Acknowledgement Type already with out subject. He additionally says he would take into account reapplying to Avid sooner or later if we now have alternatives out there at the moment.”
Maybe Mr. Bloom harm his neck from craning it round blind spots in his Lamborghini. Perhaps it was from a foul scuba outing. Regardless of the ache in Bloom’s neck was, it didn’t cease him from launching himself absolutely into LeakedSource[.]com, which was registered roughly one month after the Impression Workforce leaked information on 37 million Ashley Madison accounts.
Mr. Malek didn’t reply to a number of requests for remark. A now-deleted LinkedIn profile for Malek from December 2018 listed him as a “technical recruiter” from Toronto who additionally attended Mr. Bloom’s alma mater — York College. That resume didn’t point out Mr. Malek’s transient stint as a PHP developer at Ashley Madison.
“Developer, entrepreneur, and now technical recruiter of essentially the most unusual selection!” Mr. Malek’s LinkedIn profile enthused. “Are you a developer, or different technical specialist, focused on working with a recruiter who can correctly perceive your considerations and aspirations, technical, environmental and monetary? Don’t accept a ‘hack’; that is your profession, let’s do it proper! Join with me on LinkedIn. Be aware: In case you are not a resident of Canada/Toronto, I can not assist you.”
INTERVIEW WITH BLOOM
Mr. Bloom advised KrebsOnSecurity he had no function in harming or hacking Ashley Madison. Bloom validated his identification by responding at one of many electronic mail addresses talked about above, and agreed to subject questions as long as KrebsOnSecurity agreed to publish our electronic mail dialog in full (PDF).
Bloom mentioned Mr. Malek did suggest him for the Ashley Madison job, however that Mr. Malek additionally obtained a $5,000 referral bonus for doing so. Given Mr. Malek’s acknowledged function as a technical recruiter, it appears seemingly he additionally really useful a number of different workers to Ashley Madison.
Bloom was requested whether or not anybody on the RCMP, Ashley Madison or any authority anyplace ever questioned him in reference to the July 2015 hack of Ashley Madison. He replied that he was known as as soon as by somebody claiming to be from the Toronto Police Service asking if he knew something concerning the Ashley Madison hack.
“The AM scenario was not one thing they pursued in line with the RCMP disclosure,” Bloom wrote. “Studying concerning the RCMP’s most superior cyber investigative methods and capabilities was very fascinating although. I used to be finally advised data by a 3rd social gathering which included information that legislation enforcement successfully knew who the hacker was, however didn’t have sufficient proof to proceed with a case. That’s the extent of my involvement with any authorities.”
As to his firm’s responsible plea for working LeakedSource, Bloom maintains that the decide at his preliminary inquiry discovered that even when every thing the Canadian authorities alleged was true it might not represent a violation of any legislation in Canada with respect the fees the RCMP leveled in opposition to him, which included unauthorized use of a pc and “mischief to information.”
“In Canada on the decrease court docket degree we’re allowed to own stolen data and manipulate our copies of them as we please,” Bloom mentioned. “The decide nonetheless determined {that a} trial was required to find out whether or not any actions of mine had been reckless, as the opposite qualifier of deliberately legal didn’t apply. I’ll observe right here that nothing I used to be accused of doing would have been unlawful if accomplished in the US of America in line with their District Lawyer. +1 free of charge speech in America vs freedom of expression in Canada.”
“Shortly after their having most of their case thrown out, the Authorities proposed a suggestion throughout a closed door assembly the place they’d drop all expenses in opposition to me, present full and full private immunity, and in alternate the Company which has since been dissolved would plead responsible,” Bloom continued. “The Company would additionally pay a modest superb.”
Bloom mentioned he left Ashley Madison as a result of he was bored, however he acknowledged beginning LeakedSource partly in response to the Ashley Madison hack.
“I supposed to leverage my gaming connections to get into safety work together with for different personal servers resembling Minecraft communities and others,” Bloom mentioned. “After months of asking administration for extra fascinating duties, I grew to become bored. Some days I had nearly nothing to do besides spin in my chair so I’d browse the supply code for safety holes to repair as a result of I discovered it gratifying.”
“I imagine the choice to begin LS [LeakedSource] was partly impressed by the AM hack itself, and the big variety of individuals from a former good friend group messaging me asking if XYZ individual was within the leak after I revealed to them that I downloaded a duplicate and had the power to browse it,” Bloom continued. “LS was by no means my concept – I used to be only a builder, and the one Canadian. In different international locations it was by no means considered unlawful on nearer examination of their legal guidelines.”
Bloom mentioned he nonetheless considers himself independently rich, and that also has the lime inexperienced Lambo. However he mentioned he’s presently unemployed and might’t appear to land a job in what he views as his most promising profession path: Info safety.
“As I’m certain you’re conscious, having unfavorable media consideration related to alleged (key phrase) legal exercise can have a detrimental impact on employment, banking and relationships,” Bloom wrote. “I’ve no present curiosity in being a enterprise proprietor, nor do I’ve any helpful enterprise concepts to be sincere. I used to be and am focused on fascinating Info Safety/programming work but it surely’s too massive of a threat for any enterprise to rent somebody who was previously accused of against the law.”
If you happen to appreciated this story, please take into account studying the primary two items on this collection:
High Suspect in 2015 Ashley Madison Hack Dedicated Suicide in 2014

