
Findings in community intelligence agency Gigamon’s Hybrid Cloud Safety Survey report recommend there’s a disconnect between notion and actuality in terms of vulnerabilities within the hybrid cloud: 94% of CISOs and different cybersecurity leaders mentioned their instruments give them complete visibility of their belongings and hybrid cloud infrastructure, but 90% admitted to having been breached prior to now 18 months, and over half (56%) concern assaults coming from darkish corners of their net enterprises.
The report is an annual survey of greater than 1,000 IT and safety leaders from throughout the U.S., EMEA, Singapore and Australia.
Leap to:
Key to understanding hybrid cloud safety
Whereas practically all respondents (96%) to Gigamon’s ballot mentioned cloud safety relies on gaining visibility throughout all knowledge in movement, 70% of the CISOs and safety operators queried mentioned they lack visibility into encrypted knowledge. One-third of CISOs lack confidence about how their delicate knowledge is secured.
Chaim Mazal, chief safety officer at Gigamon, mentioned most corporations exist within the hybrid cloud. “As of in the present day, I’d enterprise to say 90% of the worldwide Fortune 5,000 are working in hybrid cloud environments,” he mentioned. “They might have began with non-public clouds first, then the general public cloud, then AWS, GCP and/or Azure for various purpose-driven use circumstances.”
Mazal mentioned the important thing to understanding what is occurring to safety throughout hybrid clouds is deep observability.
“Visibility is a key drawback throughout the board — you may’t safe what you don’t have insights into,” Mazal mentioned. “In case you take a look at the most important causes of breaches, they’re programs which have existed for a very long time at enterprises that aren’t a part of a monitoring regime. So having end-to-end visibility is one thing CISOs try for each day.”
SEE: Palo Alto Networks’ Ankur Shah on the risks of a standard strategy to cloud safety (TechRepublic)
What’s deep observability?
Mazal defined that deep observability, a time period coined by Gigamon, denotes network-level intelligence that’s immutable: “We take metadata from throughout network-level environments and route that knowledge into observability instruments via good workflows and routing.”
He added that the net is within the early phases of making end-to-end visibility, no matter asset lessons.
“With network-level metadata, you get 100% validated knowledge sources that may’t be altered,” Mazal mentioned. “We all know that safety logs are a terrific supply of information; [however,] they’re topic to such exploits as log forging, whereby a nefarious actor tampers with safety logs to cowl their tracks. With network-level intelligence, you may’t do this as a result of it contains knowledge validated from starting to finish being fed to your toolsets.”
Extra cybersecurity collaboration wanted to guard hybrid cloud environments
Whereas 97% of respondents mentioned they’re able to collaborate throughout IT groups for vulnerability detection and response, one in six mentioned they don’t observe collective accountability as a result of their safety operations are siloed. Moreover, the ballot suggests CISOs/CIOs aren’t feeling supported within the boardroom: 87% of respondents within the U.S. and 95% in Australia mentioned they’re anxious their boardrooms nonetheless don’t perceive the shared accountability mannequin for the cloud.
Many respondents mentioned attaining collective accountability is troublesome as a result of they will’t see crucial knowledge from their cloud environments:
- Greater than 1 / 4 (26%) of respondents conceded they don’t have the best instruments or visibility (Determine A).
- 52% mentioned they don’t have any visibility into east-west visitors — community visitors amongst units inside a selected knowledge middle.
- 35% (38% in France and 43% in Singapore) mentioned they’ve restricted visibility into container visitors.
Determine A

Regardless of these statistics, 50% of these polled mentioned they’re assured they’re sufficiently safe throughout their complete IT infrastructure, from on-premises to the cloud. Mazal mentioned this latter level was stunning.
“These two issues don’t align,” Mazal defined. “Based mostly on the research, there’s a false sense of safety however, once more, we are able to’t account for these blind spots – with the ability to clear up for them is a key to discovering a path ahead. Sure, you may need quite a lot of confidence however not the complete image; should you did, you may go forward and take acceptable actions and construct professional confidence. However sadly, you don’t know what you don’t know, and typically ignorance is bliss.”
SEE: Cybersecurity unaligned with enterprise objectives is reactive … and flawed (TechRepublic)
The survey discovered a number of factors of concern protecting CISOs up at evening, with 56% of respondents saying assaults coming from unknown vulnerabilities had been prime stressors (Determine B).
Determine B
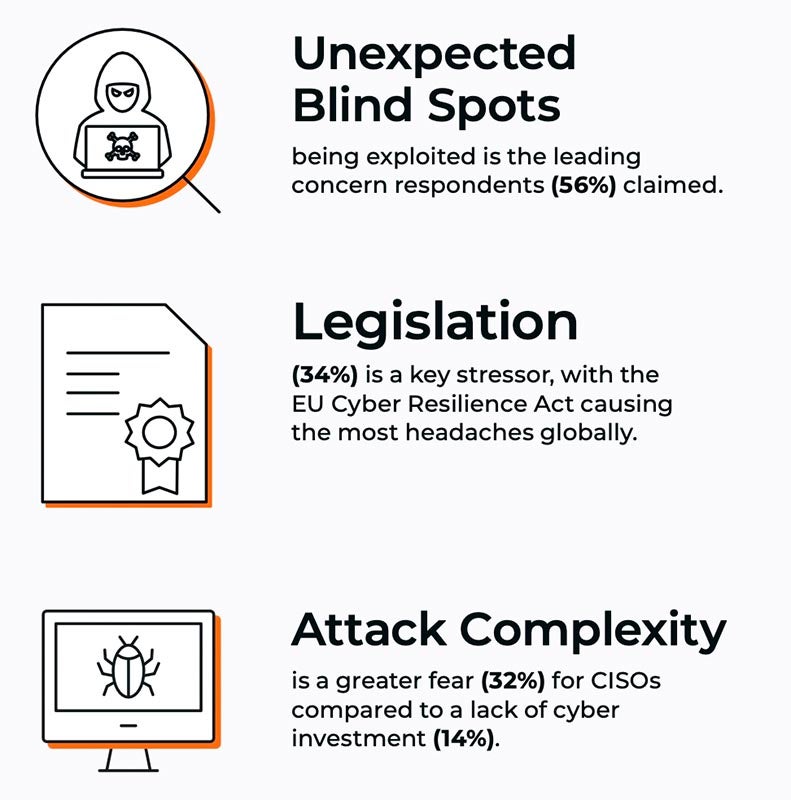
34% of respondents to the Gigamon survey mentioned laws was a prime stressor for them, particularly the EU Cyber Resilience Act. 32% of CISOs mentioned assault complexity was a key concern. One-fifth of respondents mentioned their groups had been unable to determine the foundation causes of breaches.
Moreover, solely 24% of worldwide enterprises have banned or are trying into banning ChatGPT, 100% are involved about TikTok and the metaverse, and 60% have banned the usage of WhatsApp attributable to cybersecurity considerations.
Training and funding considerations? Not a lot
What isn’t worrying safety groups is a scarcity of cyber funding – solely 14% of respondents articulated this concern in Gigamon’s survey. As well as, solely 19% mentioned safety schooling for workers was crucial.
Safety leaders in France and Germany, nonetheless, bemoaned the shortage of hybrid cloud cybersecurity abilities of their workforces: 23% and 25% of respondents, respectively, mentioned they require extra folks with these abilities. Lastly, laws is a specific subject for leaders within the U.Ok. and Australia: 41% within the U.Ok. and 59% in Australia mentioned they had been involved with adjustments in cyber legal guidelines and compliance.
Zero belief consciousness on the rise
The zero belief framework, as Deloitte defined in a 2021 white paper, applies throughout an enterprise’s community and consumer authentication processes a primary precept of “by no means belief, at all times confirm.” In Gigamon’s State of Ransomware for 2022 Report, 80% of CISOs/CIOs mentioned zero belief can be a significant pattern. On this new research, 96% now imagine the identical for 2023 and past. Additionally, 87% of respondents mentioned zero belief is spoken about overtly by their boards, a 29% improve in comparison with 2022.
“Zero belief isn’t a product – it’s a technique,” mentioned Mazal. “For a very long time, we didn’t have a transparent concept of what that was, however structured outlines by the federal authorities have given us a very good understanding of what that layered strategy is in the present day round belongings, identification and perimeter, blended in a single strategy.”
He mentioned network-level insights which might be validated throughout the board and might be fed to IT instruments are essential pillars. “Immutable knowledge streams throughout instruments is essential to zero belief implementation on the enterprise degree.”
How one can shut the notion/actuality hole
The Gigamon research’s authors mentioned making certain knowledge that gives deep observability is fed to conventional safety and monitoring instruments will help get rid of blind spots and shut the hole between what safety leaders imagine about their organizations’ safety postures and actuality.
“The primary stage to bolstering hybrid cloud safety is recognizing that many organizations are affected by a notion vs. actuality hole,” famous the report.
A guidelines manifesto for IT
As a part of a visibility technique, IT groups ought to commonly replace community documentation to higher administer upkeep, help and safety routines. Common audits garnering info from each node on the community represent a robust protection in opposition to patch and replace lapses.
TechRepublic Premium’s community documentation guidelines exhibits how checklists might be built-in with every audit. Out there as a PDF and Phrase doc, it can provide help to doc your key belongings, from voice tools to storage infrastructure to battery backups. Study extra about it right here.

