
A reverse-proxy Phishing-as-a-Service (PaaS) platform known as EvilProxy has emerged, promising to steal authentication tokens to bypass multi-factor authentication (MFA) on Apple, Google, Fb, Microsoft, Twitter, GitHub, GoDaddy, and even PyPI.
The service permits low-skill risk actors who do not know easy methods to arrange reverse proxies to steal on-line accounts which can be in any other case well-protected.
Reverse proxies are servers that sit between the focused sufferer and a reputable authentication endpoint, reminiscent of an organization’s login type. When the sufferer connects to a phishing web page, the reverse proxy shows the reputable login type, forwards requests, and returns responses from the corporate’s web site.
When the sufferer enters their credentials and MFA to the phishing web page, they’re forwarded to the precise platform’s server, the place the person is logged in, and a session cookie is returned.
Nevertheless, because the risk actor’s proxy sits within the center, it might additionally steal the session cookie containing the authentication token. The risk actors can then use this authentication cookie to log in to the location because the person, bypassing configured multi-factor authentication protections.
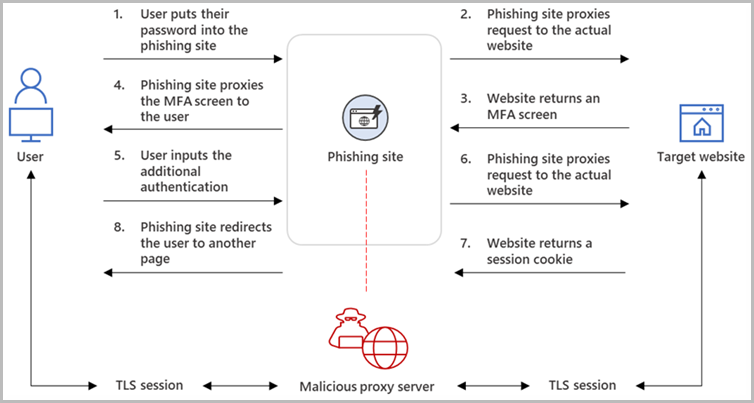
Refined APT teams have been using reverse proxies for some time now to bypass MFA protections on track accounts, some utilizing their very own customized instruments whereas others utilizing extra readily-deployable kits like Modlishka, Necrobrowser, and Evilginx2.
The distinction between these phishing frameworks and EvilProxy is that the latter is much less complicated to deploy, affords detailed tutorial movies and tutorials, a user-friendly graphical interface, and a wealthy number of cloned phishing pages for standard web providers.
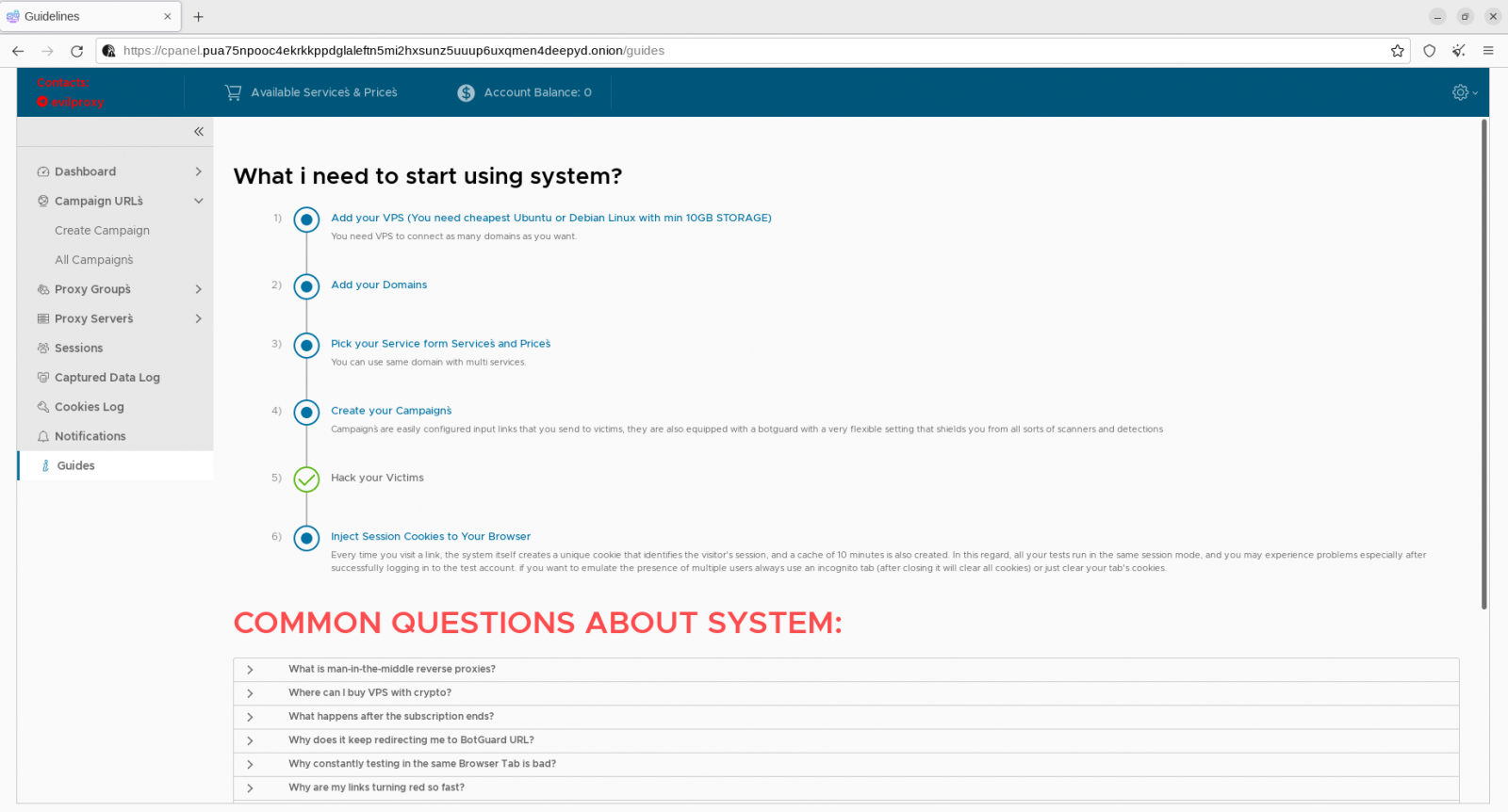
A deeper have a look at EvilProxy
Cybersecurity agency Resecurity reviews that EvilProxy affords an easy-to-use GUI the place risk actors can arrange and handle phishing campaigns and all the small print that underpin them.
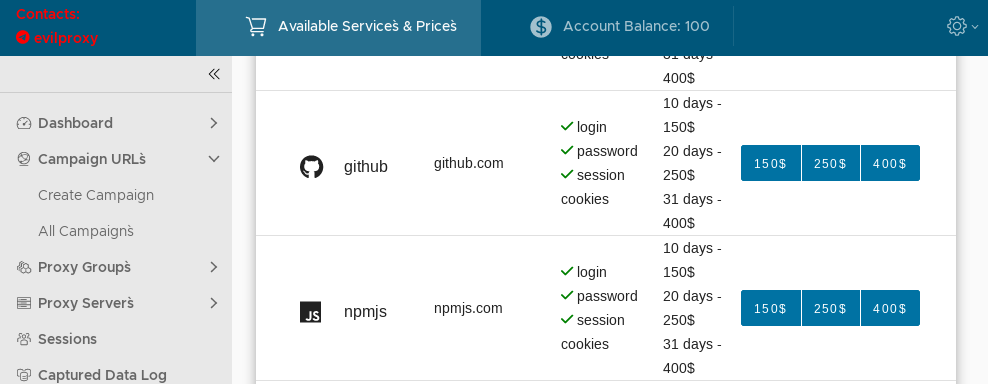
The service guarantees to steal usernames, passwords, and session cookies, for a value of $150 for ten days, $250 for 20 days, or $400 for a month-long marketing campaign. Assaults in opposition to Google accounts value extra, at $250/450/600.
Within the following video, Resecurity demonstrates how an assault in opposition to a Google account would unfold by way of EvilProxy.
Whereas the service is actively promoted on varied clearnet and darkish net hacking boards, the operators vet the purchasers, so some potential patrons are possible rejected.
In accordance with Resecurity, the fee for the service is organized individually on Telegram. As soon as the deposit is made, the client will get entry to the portal hosted within the onion community (TOR).
Resecurity’s take a look at of the platform confirmed that EvilProxy additionally affords VM, anti-analysis, and anti-bot safety to filter out invalid or undesirable guests on the phishing websites hosted by the platform.
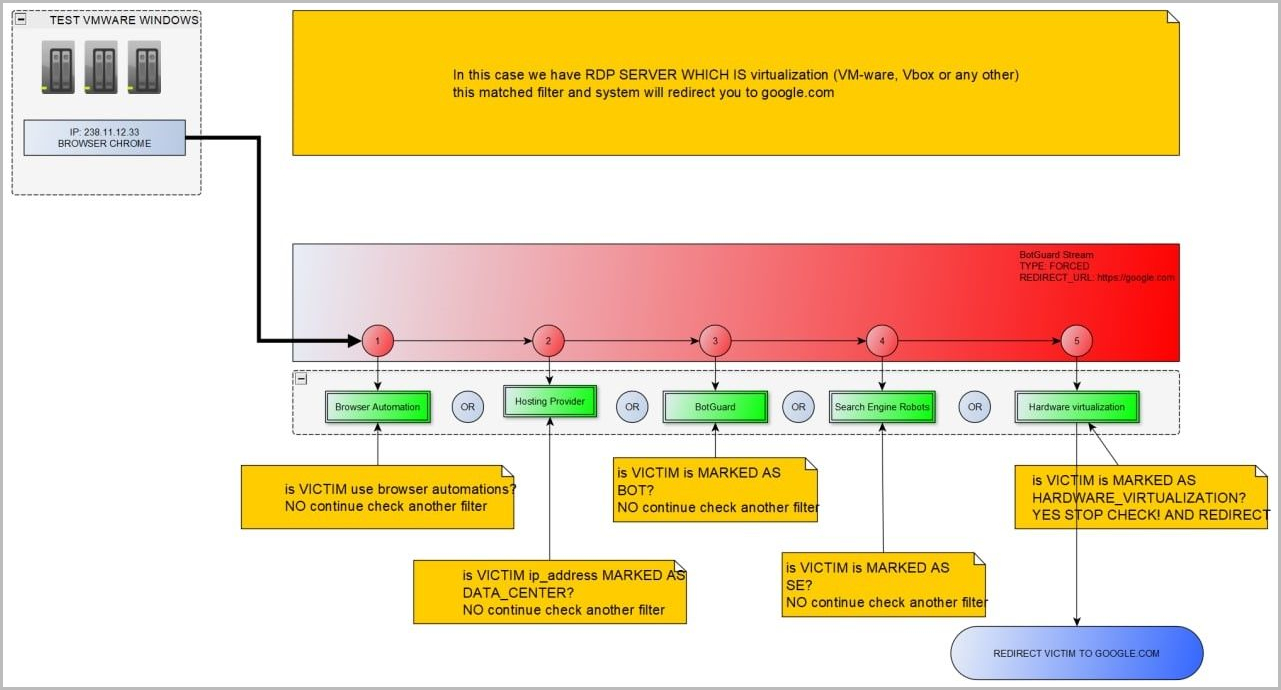
“The unhealthy actors are utilizing a number of strategies and approaches to acknowledge victims and to guard the phishing-kit code from being detected,” explains Resecurity within the report.
“Like fraud prevention and cyber risk intelligence (CTI) options, they mixture information about identified VPN providers, Proxies, TOR exit nodes and different hosts which can be used for IP repute evaluation (of potential victims).”
A service to look out for
As MFA adoption continues to extend, extra risk actors flip to reverse-proxy instruments, and the looks of a platform that automates every thing for the crooks isn’t excellent news for safety professionals and community admins.
.png)
For now, this drawback stays addressable solely by implementing client-side TLS fingerprinting to determine and filter out man-in-the-middle requests. Nevertheless, the standing of this implementation within the trade isn’t in sync with the developments.
Therefore, platforms like EvilProxy primarily bridge the ability hole and supply low-tier risk actors a cost-efficient technique to steal helpful accounts.


