The examine exhibits attackers are utilizing extra bots and doing extra subtle phishing exploits and server assaults, particularly focusing on retail.

Assaults on commerce are booming, in accordance with a brand new examine by safety agency Akamai. The corporate’s 15-month evaluate starting in January 2022 discovered that commerce was probably the most focused net vertical, with retail being the main subvertical inside it.
Leap to:
Bots raining on retail drive flood in commerce assaults
In its new report, Coming into via the Present Store: Assaults on Commerce, Akamai decided that 14 billion or 34% of all incursions have been towards commerce websites, pushed by bots, API assaults, distant code execution via native file inclusion assaults and server-side exploits. The migration to cloud, availability of darkish web apps and the proliferation of IoT gadgets have additionally pushed an enormous enhance in assaults.
The examine reported that:
- The variety of whole malicious bot assaults in all classes zoomed previous 5 trillion between the start of 2022 and March 2023 and continues to develop.
- Native file inclusion assaults for gaining entry and information exfiltration elevated 314% between the third quarter of 2021 — through the prior 12 months’s examine interval — and the identical quarter final 12 months.
- Half of the JavaScript for commerce comes from third-party distributors, growing the client-side assault risk floor.
Trailing the commerce sector in quantity of assaults have been excessive expertise at 21.66% of all assaults, monetary providers at 15.4%, adopted by video media, manufacturing, the general public sector and gaming (Determine A).
Determine A
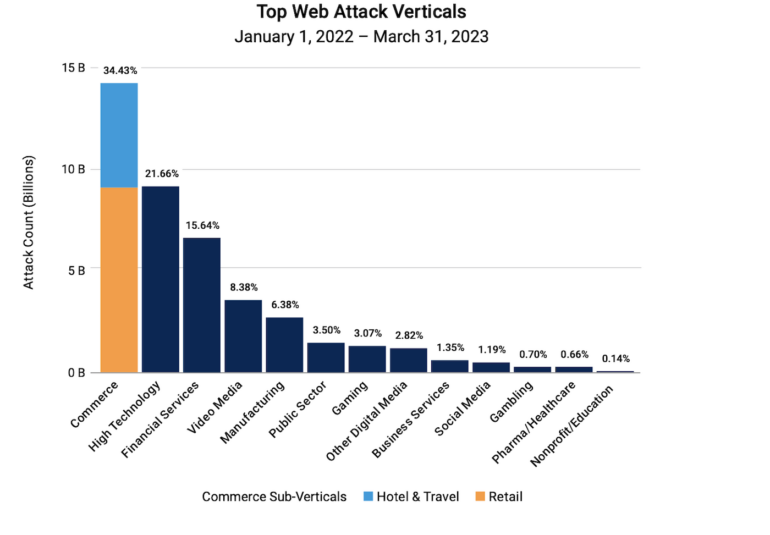
The examine, primarily based on petabytes monthly of knowledge drawn from Akamai Linked Cloud, a community of roughly 340,000 servers on 1,300 networks in additional than 130 nations, discovered that assaults in Europe, Center East, Asia and Africa are closely skewed towards the retail subvertical, which accounts for 96.5% of assaults versus 3.3% for lodge and journey, in accordance with the agency.
Led by LFI assaults, net server exploits are on the rise
The report honed in on native file inclusion: An online server assault that hits weak spots in how a server shops information. The examine discovered that LFI has changed SQL Injection as the most typical assault vector used towards the commerce sector. There have been greater than twice the variety of LFI assaults than the subsequent most prevalent assault, that are these aiming for cross-site scripting, or XSS vulnerabilities. Such weaknesses enable attackers to inject scripts into net pages and can be utilized to bypass entry controls.
SEE: Verizon examine warns of extra DDoS, electronic mail exploits (TechRepublic)
Solely 12.24% of assaults that Akamai tracked concerned SQL Injections by which attackers can steal entry to databases (Determine B).
Determine B
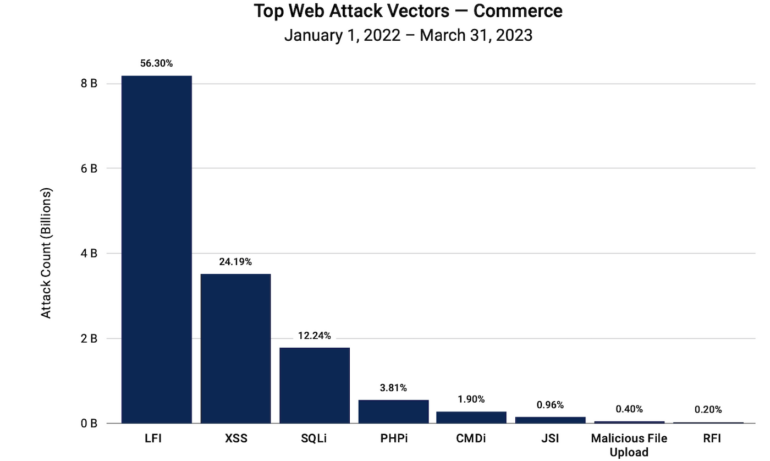
Akamai stated the expansion of LFI exploits exhibits that attackers are favoring quiet insurgency geared toward enabling distant code execution to extract information. Doing so permits lateral motion into firm networks, a mode of incursion that might, in accordance with the report, allow a pathway for criminals to infiltrate larger, profitable targets in provide chains.
Third-party scripts weaken safety perimeters
Knowledge from the examine confirmed that fifty% of the scripts used within the commerce vertical come from third-party assets, greater than in all different verticals. The report famous that “Though utilizing third-party scripts doesn’t essentially imply that they’re much less trusted or malicious in nature, it places organizations susceptible to safety flaws inside these third-party scripts.”
Bot assaults and phishing campaigns are booming
Akamai reported risk actors utilizing a file variety of bots for fraud and different exploits, noting that even benign bots can harm the expertise by jamming net efficiency. The examine checked out scalpers who’re starting to construct their very own botnets, or they’re shopping for bots in the marketplace for scalpers.
The examine experiences that scalpers searching for discounted merchandise use botnets to scrape web sites for stock or good offers. Akamai’s report famous that a number of so-called “scraper as a service” choices that may be purchased are able to analyzing information and producing a buying record that matches sure standards that meets a predefined revenue margin.
SEE: Half of corporations have been hit with focused spearphishing assaults final 12 months (TechRepublic)
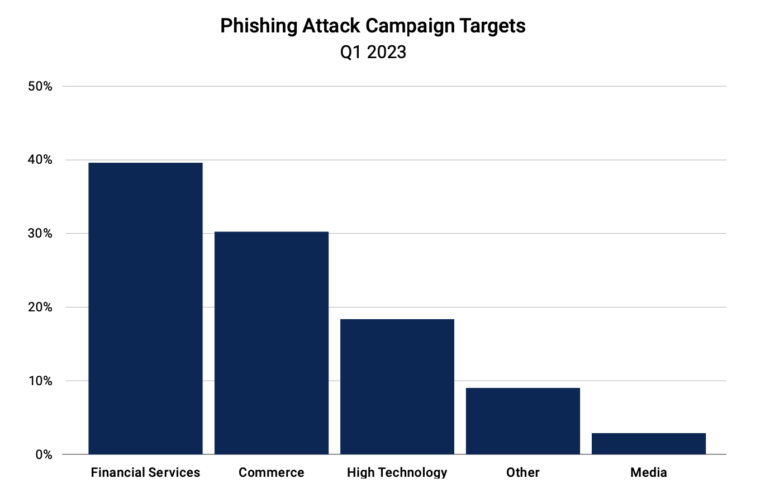
Phishing can be up, because the agency reported that within the first quarter this 12 months 30% of phishing campaigns have been activated towards commerce clients. “Though we noticed extra campaigns than precise victims, it’s also price noting that attackers are focusing on this trade.”
Within the first quarter this 12 months, Akamai noticed commerce trailing solely monetary providers in phishing assaults (Determine C).
Determine C
Final 12 months, Akamai discovered a phishing exploit emblematic of how practitioners of the social engineering assault have gotten higher at subterfuge: A for-sale phishing equipment that mimics manufacturers that embrace well-designed dummy websites and robust infrastructure utilizing cloud providers. The techniques use redirects that embrace URL shorteners to cover visually identifiable malicious hyperlinks. “Our evaluation exhibits that 89% of affected victims are from the US and Canada, as cybercriminals created campaigns that focus on particular geographic places,” stated the agency.
Steve Winterfeld, advisory chief info safety officer at Akamai, stated safe coding as a key method to hardening APIs and different surfaces is vital to lowering threats. “If I have been to speculate, the very first thing can be shifting left to catch errors at first. Pen testing is vital, however corporations ought to ask themselves if their return on funding is best with safe coding,” he stated.
Community safety guidelines: A must have for juggling cyberthreats
Each group is totally different in relation to safety wants, and the threats have gotten extra various and arriving from new instructions. There are safety fundamentals, nevertheless, that needs to be utilized as normal strategies.
When these fundamentals are pared right down to a guidelines, safety is simpler to execute and fewer annoying to prepare. This free to obtain Community and Techniques Safety guidelines from TechRepublic Premium affords a superb template for constructing a powerful cybersecurity posture.


