Traditionally, software program safety has been addressed on the mission stage, emphasizing code scanning, penetration testing, and reactive approaches for incident response. Not too long ago, nonetheless, the dialogue has shifted to this system stage to align safety with enterprise aims. The best final result of such a shift is one wherein software program growth groups act in alignment with enterprise targets, organizational danger, and resolution architectures, and these groups perceive that safety practices are integral to enterprise success. DevSecOps, which builds on DevOps ideas and locations further give attention to safety actions all through all phases of the software program growth lifecycle (SDLC), will help organizations understand this excellent state. Nonetheless, the shift from project- to program-level considering raises quite a few challenges. In our expertise, we’ve noticed 5 frequent challenges to implementing DevSecOps. This SEI Weblog put up articulates these challenges and offers actions organizations can take to beat them.
Key Advantages of DevSecOps
The addition of safety to the observe means addressing safety all through the lifecycle, from the idea of a function to the deployment of a product. The necessity for frequent ideas and practices that span the group can itself current a problem. Along with ideas and practices that span the group and govern the lifecycle from idea to deployment, DevSecOps requires the next practices:
- iterative and incremental growth—This observe includes a cyclical method to breaking software program growth into smaller, extra manageable steps. Steady integration/steady deployment (CI/CD) practices present the automation obligatory to make sure high quality, safety, and performance.
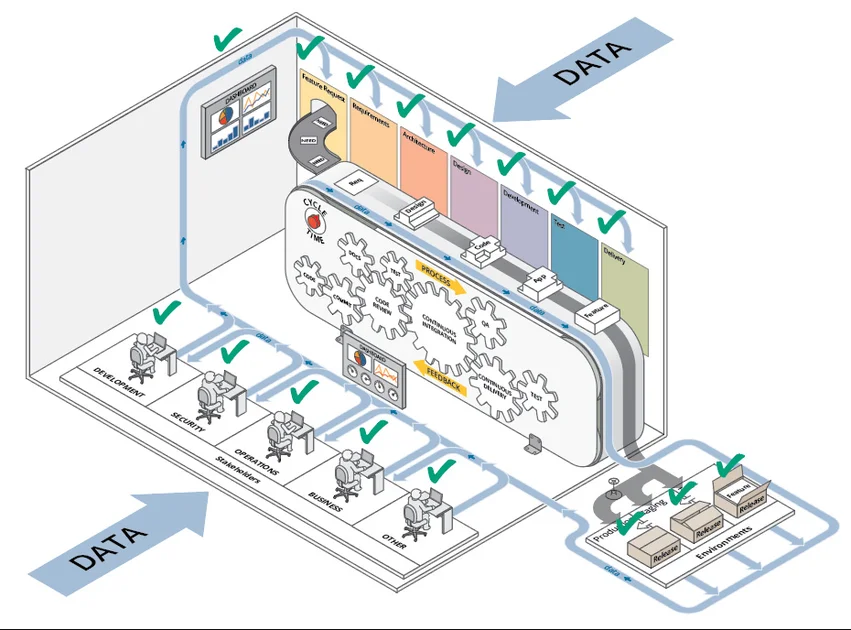
- steady suggestions—Suggestions needs to be collected all through each step of the lifecycle to permit for professional validation and basic observability. Each software used all through a DevSecOps pipeline creates some output that can be utilized for suggestions. Take a look at instances produce output that gives high quality suggestions, stakeholders and clients provide a supply of human suggestions. Determine 1 illustrates the sorts of information, and their sources, that may inform the suggestions and measurement cycle.
- metrics and measurement—Metrics are used to guage suggestions and decide how effectively the group is acting on measures, resembling productiveness and high quality.
- automation in each section of the Software program Improvement Lifecycle (SDLC)—Automation helps organizations profit from their suggestions mechanisms. CI/CD is the first automation mechanism of the SDLC.
- full engagement with all stakeholders—All stakeholders have to be engaged, not simply the Dev, Sec, and Ops elements. This engagement ought to produce consensus on what issues probably the most to the group.
- transparency and traceability throughout the lifecycle—Transparency helps construct the belief wanted among the many Dev, Sec, and Ops groups to make the method work, and traceability permits the digital path of the merchandise used to construct, deploy, and preserve software program.
These practices produce a number of advantages when utilized in DevSecOps. Maybe the 2 most necessary are the next:
- lowered safety error and related prices—By addressing safety points all through the event lifecycle somewhat than after launch, organizations can catch and deal with points earlier, when the time and price to resolve them is far decrease. These prices embrace misplaced {dollars}, further effort and rework, and buyer goodwill.
- lowered time to deploy—Catching flaws and vulnerabilities by means of fixed testing in the course of the lifecycle reduces time to deploy, reduces time spent after deployment on error response, and improves your readiness to deploy.
Along with fewer errors and vulnerabilities, lowered prices, and lowered time to market, DevSecOps additionally offers the next advantages:
- repeatable and/or automated steps
- steady availability of pipeline
and utility - elevated time for studying new ideas
- responsiveness to enterprise wants
- elevated stability and high quality
DevSecOps Challenges
Whereas DevSecOps can profit your group in some ways, we’ve noticed a number of challenges to its adoption, the commonest of that are the next:
- lack of safety assurance on the enterprise and mission ranges
- organizational limitations associated to collaboration, tooling, and tradition
- affect to high quality as a result of safety isn’t a precedence whereas programs are getting extra advanced
- lack of safety abilities for builders, enterprise stakeholders, and auditors
- inadequate safety steerage because of lack of sources, requirements, and knowledge
The remainder of this part examines every of those challenges and offers approaches for overcoming them.
CHALLENGE #1: Lack of Safety Assurance
How do we all know that the safety practices we’ve adopted for our growth lifecycle and constructed into our software program are sufficient and acceptable for the enterprise objective we’re making an attempt to handle? Addressing this problem could be arduous, particularly when your business, enterprise, and/or mission lacks safety assurance.
Your Trade Lacks Safety Assurance Fashions
The safety necessities to your business or area are completely different from these of different industries or domains. As an example, the well being care business has completely different safety necessities from the monetary sector. In case your business lacks assurance fashions, you may start by assessing your personal group’s safety posture and necessities, then interact with related organizations in your business or area to share data. As well as, we advocate the next:
- Don’t look ahead to an business commonplace to emerge.
- Be a part of or create casual working teams with business friends.
- Attend conferences and community with like organizations.
- Share your experiences and classes realized.
- Work with others to increase the physique of data and set up greatest practices.
Your Enterprise Lacks Safety Assurance
There’s typically a disconnect between enterprise wants, mission, and imaginative and prescient with regards to safety. Builders want to grasp the enterprise context of safety. They need to take into consideration the group’s safety insurance policies, its enterprise drivers, and the way these apply to the software program being developed. In so doing, they need to deal with safety as early as attainable within the lifecycle, ideally in the course of the necessities stage. As you do, preserve the next suggestions in thoughts:
- Concentrate on fundamentals: What are the threats? What are the enterprise drivers? Steadiness the 2.
- Align with growth with enterprise wants (time to market, value financial savings, resilience).
- Conduct exterior audits.
- Perceive the enterprise context.
- Establish, hyperlink, and rank enterprise and technical dangers.
- Establish safety necessities in early.
- Outline the danger mitigation technique.
- Educate prime administration and get them onboard.
- Interact extra senior technical individuals first to work with safety groups.
- Make safety a part of senior technical critiques; organically unfold the phrase.
Your Challenge Lacks Assurance of Safety
When you’ve recognized safety assurance wants inside your business or area (and maybe your particular enterprise inside that area), it’s good to map that knowledge to your mission. As an example, maybe your group is already following steerage, resembling Normal Information Safety Regulation (GDPR) or the Well being Insurance coverage Portability and Accountability Act (HIPAA). It is advisable to account for any safety actions stipulated in that steerage in your mission planning, and also you want to take action early within the lifecycle when there’s nonetheless time to handle it. As you do, take into accout the next suggestions:
- Map reporting knowledge from instruments to type a steady view of worth.
- Run safety instruments on all code to measure code high quality and requirements.
- Evaluation code modifications for safety and doc approval previous to launch.
- Use devoted testing sources within the case of serious modifications.
- Observe all modifications and approvals for incident functions.
- Conduct code critiques.
- Expose safety crew to your metrics and knowledge.
CHALLENGE #2: Organizational Boundaries
Should you’re not sharing your DevSecOps journey throughout the group, from idea to product, it’s best to anticipate issues because you gained’t have a transparent understanding of the enterprise wants your software program wants to handle. You won’t actually have a clear imaginative and prescient of the client’s wants and the atmosphere wherein the client operates. Communication is vital to breaking down organizational limitations, however typically completely different items inside a corporation use completely different communications instruments, constructions, and targets.
To start to interrupt down these limitations, briefly doc your journey from concept to product. Have a look at factors of interplay among the many numerous elements of your group. Educate executives who doubtless don’t know the small print of the DevSecOps course of. Construct connections and a tradition that reinforce the sharing of the identical targets and imaginative and prescient. Usually, poor stakeholder collaboration, problem integrating pipeline safety, and an unwillingness to make safety a precedence stand in the way in which of profitable DevSecOps implementation.
Poor Stakeholder Collaboration
The product you’re creating touches many different stakeholders in your group, together with advertising, IT, and authorized groups, however communication amongst them could be missing. For instance, you could have completely different instruments, might not share the identical infrastructures, and should not even share the identical imaginative and prescient and targets. To handle these points, it’s good to come collectively and doc your journey from idea to product. A easy cheat sheet will suffice, one which reminds all stakeholders of the imaginative and prescient, the mission, and the roles they are going to play within the lifecycle. Our suggestions for bettering stakeholder collaboration embrace the next:
- Doc your present state and determine silos (e.g., growth, infrastructure, and safety).
- Begin constructing collaboration between the Safety, Dev, and Ops groups.
- Be ready: individuals usually don’t wish to change their tradition and/or workflow.
- Be certain everybody will get on the identical web page relating to the significance of safety (from executives to DevSecOps groups).
- Instill a steady safety mindset.
- Concentrate on partnership, not unhealthy battle. Destroy the blame tradition.
- Get stakeholders to agree on a shared a imaginative and prescient for the mission.
- Steadiness workload amongst groups concerned.
- Put safety individuals into growth groups.
Integrating Pipeline Safety
The pipeline isn’t solely the infrastructure supporting DevSecOps. As a substitute, it’s the heartbeat of your total DevSecOps ecosystem, together with supply management, communications, subject monitoring programs, documentation programs, CI/CD, and code assessment. This infrastructure needs to be linked, i.e., all of the instruments ought to talk to one another, as proven in Determine 2.
As an example, your supply management ought to have the ability to talk together with your construct server, your communication programs, and your subject monitoring programs. When your infrastructure is linked this manner, you’ll be able to apply risk modeling, static evaluation, dynamic evaluation, mission administration, or interactive utility safety evaluation. Take into consideration software integrations to beat pipeline safety issues after which design your infrastructure to handle safety.
The pipeline is the place transparency occurs and the place all of the stakeholders implement their experience by way of automation. One solution to obtain this transparency is thru metrics dashboards fed by pipeline knowledge which might be straightforward to learn. The software needs to be tailor-made to the product. The larger you might be, the tougher that is to do, however the result’s value it. Suggestions for integrating pipeline safety embrace the next:
- Combine your course of with risk modeling (TM), static utility safety testing (SAST), dynamic utility safety testing (DAST), and interactive utility safety testing (IAST).
- Set up safety necessities traceability.
- Apply metrics: imply time to restore (MTTR), imply time to detect (MTTD), vulnerability escape fee, repeated incident root trigger, time to deploy the app from growth to manufacturing.
- Have a look at completely different approaches: abuse instances, architectural danger evaluation, utility penetration testing.
- Design for safety.
- fail securely and fail protected defaults
- least privilege
- protection in depth
- Automate the place attainable.
- infrastructure as code (IaC), virtualization, containers, and cargo balancing
- configuration administration
- steady utility and efficiency monitoring
Making Safety a Precedence
It is advisable to plan for safety if you wish to make it a precedence. Deal with safety as a function that your software program will need to have. In some instances, the selection is out of your palms: a software program invoice of supplies (SBOM), for example, may mandate constructing safety into the product. However how do you make safety a precedence? We advocate the next:
- Use evangelists to drive tradition change.
- Clarify why safety is a crucial, shared duty, and its affect.
- Embed safety into operations escalation.
- Invite the safety crew to postmortems.
- Create a plan in small elements; begin with a pilot and be aware of cross-team useful resource constraints.
- Preserve it easy; don’t overwhelm the system. If there are too many issues to do, the plan is prone to fail.
- Incrementally chase actual danger and threats first.
- Take a look at whether or not your group is prepared for the tradition change; no single know-how/software will get you DevSecOps.
CHALLENGE #3: Lack of High quality
Safety is integral to high quality. In our statement, lack of high quality is commonly related to the safety crew getting concerned too late, a insecurity within the launch, and system complexity.
Safety Crew Concerned Too Late
Too typically, builders make safety a secondary precedence, particularly when they’re underneath stress to maintain manufacturing transferring ahead. As we acknowledged earlier, safety is a key facet of high quality. When the safety crew engages in direction of the tip of the SDLC course of, it’s typically too late to keep away from the disruption and costly rework that flows from the safety flaws it identifies. Relying on the mission cadence, “too late” might imply two months, two weeks, and even two days.
Take into account a crew utilizing Agile growth with two-week sprints. Inside that dash, given a scrum day-after-day, the developer would want to know of any issues as early as attainable. Nonetheless, the Sec crew solely analyzes the code a month later (or possibly two months later or simply earlier than deployment to the manufacturing atmosphere). Any issues found by the Sec crew at this level would require large work, and builders will push again. Furthermore, the later issues are found within the SDLC, the dearer they’re to repair. To keep away from these points, we advocate the next:
- Begin getting safety and compliance necessities in early.
- Tie compliance aims into offering assurance again to the enterprise.
- Take a look at compliance towards safety insurance policies to determine gaps.
- Outline a danger mitigation technique early.
Lack of Confidence within the Launch
Correcting issues and patching safety vulnerabilities late within the growth lifecycle when the stress is on to get the product out the door opens room for doubt concerning the high quality of your launch. This insecurity hinders planning and efficient use of sources as it’s good to reserve sources to handle flaws and vulnerabilities found after launch. These flaws and vulnerabilities characterize a chance value, a greenback value, and a reputational value. However there are methods to enhance confidence in your launch, together with the next:
- Instill risk-based safety testing.
- Transfer the dialog from CABs and section gates to compliance pushed releases.
- Automate reporting for compliance violations and cease the pipeline when the brink is exceeded, or coverage not met.
- Transfer towards frequent, automated audits.
- Audit your self to show compliance with insurance policies or rules.
- Set up safety necessities traceability (a function DevOps offers) and hint all the things: code, artifacts, pipeline, take a look at instances, and many others.
System Complexity
Take into account a posh system with a number of utility programming interfaces (APIs) and microservices. How do you gauge its high quality? How have you learnt that every of the companies is following the precise safety controls? How have you learnt that every API is following centralized communications? How have you learnt that they’re following the safety insurance policies that you just implement in organizations? It is advisable to incorporate these insurance policies in your code, in your architectures, in your microservices. To take action, it’s good to acquire the precise knowledge and metrics that allow you to look at all of the elements all through your advanced system. The extra advanced your system, the extra you want a testing atmosphere that mirrors your manufacturing atmosphere. In brief, we recommend the next:
- Establish proxy metrics for complexity, such because the variety of points in manufacturing and the time to deploy an utility.
- Drive safety insurance policies into manufacturing by integrating safety duties in early levels of the DevSecOps pipeline.
CHALLENGE #4: Lack of Safety Expertise
Builders, architects, scrum masters, and different key gamers in a corporation ought to have the precise vocabularies and abilities. By vocabularies, we imply some frequent information or skillset, or a typical understanding, resembling a information of how one can write safe code. In our expertise, this lack of a typical vocabulary typically manifests in 3 ways: The enterprise lacks safety abilities, builders lack safety abilities, and/or auditors lack safety abilities.
The Enterprise Lacks Safety Expertise
Enterprise stakeholders want to make use of the vocabulary of safety. After all, not everybody could be an professional at all the things, however the enterprise stakeholders ought to have the ability to perceive and articulate safety necessities and join these safety necessities to organizational dangers. An acquisition crew, for example, ought to have the ability to comprehend it’s buying the precise safety practices when it’s buying a product. To enhance on this space, we advocate the next:
- Shift the dialog to danger and high quality.
- Service and shield the enterprise pursuits to decrease danger (determine danger and/or safety worth).
- Establish architectural danger and uncertainty and map these dangers to compliance, resiliency, and have supply.
Builders Lack Safety Expertise
We wish to suppose that builders know all the things wanted to carry out their duties efficiently. Builders actually know how one can write code, however they’re typically not skilled for safe coding in particular languages on the college stage or in abilities growth applications, the place the main focus stays on function growth. It takes time to be taught these abilities, and to observe utilizing them, however it’s worthwhile for the group to develop these safety abilities amongst its employees, to develop. This upskilling can take the type of safety coaching or different applications and sources that incentivize and inspire growth employees to accumulate and develop these abilities.
You can begin small with a slim focus. As an example, ask your self, “What are the highest 10 vulnerabilities we’ve addressed in our organizations? What are the highest 10 CVEs? What are the highest 10 CWEs?” Concentrate on coaching that addresses these points and widen your scope over time. Or begin with the programming language(s) utilized by your group and focus safety coaching on these languages. Different suggestions for constructing safety know-how amongst your growth employees embrace the next:
- Preserve the endgame in thoughts and construct a collaborative safety tradition.
- Implement compliance automation to drive enterprise considering into the SDLC.
- Don’t make safety coaching a checkbox. Safety coaching annually has restricted effectiveness.
- Goal for perspective and habits: Merely offering higher technical coaching alone gained’t change attitudes.
- Inspire and unblock the trail to your purpose: Take away job ambiguity, set clear position targets, and don’t overload.
- Goal for long-term retention and apply studying in context repeatedly.
- Rotate safety consultants on the crew, the place attainable.
Auditors Lack Safety Expertise
Auditors assessment code and merchandise, rendering a thumbs-up or a thumbs-down based mostly on established standards, however they typically don’t have the talents and information to supply an correct judgment about safety. To compensate, foster robust relationships amongst auditors and builders. Educate auditors in your structure and programs. As we famous earlier within the part on enterprise stakeholders, ensure your auditors perceive and use the identical vocabularies. Different suggestions embrace the next:
- Construct working relationships and collaboration throughout silos.
- Make safety part of casual discussions.
- Present cross-functional coaching for each technical and compliance domains.
- Combine low-disruption workflows.
- Get aware of some frequent requirements and frameworks (OWASP High 10, NIST 800-53, and ISO 27001).
CHALLENGE #5: Inadequate Safety Steering
Organizations must take inventory of their compliance practices and safety insurance policies and implement them of their merchandise or capabilities. As an example, you could have adopted zero belief insurance policies, however how will you implement them? Take into account the place your group is in its DevSecOps journey and map out your future: What are you doing for 12 months one? Yr two? Past? Bear in mind, if you wish to create a brand new commonplace to your group, you may suppose you’re distinctive, however you’re not. As a substitute of ranging from scratch, use an present commonplace or attempt to tailor one to your wants. As an example, you may begin with the OWASP High 10. How will you implement these frameworks in steerage underneath CI practices? Incorporate the insurance policies into the workflow from starting to finish.
In our expertise, issues on this space stem from three deficiencies: lack of safety sources, lack of safety requirements, and/or lack of proactive monitoring.
Lack of Safety Sources
You most likely don’t have sufficient safety individuals on the crew, but there are insurance policies and steerage to develop. Furthermore, there’s a lot else that should occur. Should you’re fortunate, you may need some unicorns in your crew, some overachievers, however it’s good to get past that. Listed here are some suggestions for organizations that wish to embark on a DevSecOps journey however lack safety sources:
- Begin small by introducing a coverage and assess your gaps. Develop from there.
- Map insurance policies to domain-specific procedures (e.g., growth and testing) and implement in product (e.g., zero belief).
- Goal for long-term sustainability: If you consider an upgraded functionality a few years after deployment, is the change nonetheless there?
- Unfold safety duty throughout a number of individuals.
Lack of Safety Requirements
Right here’s the excellent news: As we’ve famous, a number of safety requirements have already been developed. You don’t have to begin from scratch. You can begin with insurance policies derived from present requirements, tailor them to your wants, and incorporate them into your practices and merchandise. When doing so, preserve these suggestions in thoughts:
- Don’t go huge bang. Begin with one thing manageable, resembling static evaluation, and develop from there.
- Begin with a widely known framework like OWASP High 10 and create a couple of insurance policies derived from that.
- Goal at low hanging fruit (CI or testing, for instance) and measure safety towards your preliminary insurance policies.
- Develop by trying upstream and downstream for the next-easiest implementation.
- Bake insurance policies into the workflow to keep away from regression.
Lack of Proactive Monitoring
Proactive monitoring [DS1] identifies and addresses safety dangers earlier than an assault occurs. The important thing to growing extra proactive monitoring is to have a look at instances wherein you’ve been pressured to react, then plan methods to get in entrance of the issue. As an example, you could have found sure vulnerabilities, or courses of vulnerabilities, after previous releases. Take into consideration how one can deal with these sorts of vulnerabilities in your pipeline and develop a observe round that after which incorporate it as early as you’ll be able to in your SDLC.
There are nice open-source and industrial monitoring instruments obtainable. Whereas every of those instruments has a person dashboard, ideally pe the outcomes from all of them needs to be built-in into a typical dashboard. Doing so will present an overarching view into your DevSecOps journey for each the group and your particular person merchandise. We additionally advocate the next:
- Begin with Ops log monitoring earlier than making an attempt costly instruments.
- Create suggestions loop from Ops again to growth.
- Replace safety documentation, together with belief boundaries, new threats, and part verification.
Conclusion: Sustaining your DevSecOps atmosphere
Implementing DevSecOps could be daunting. Challenges abound. This weblog posting examined the 5 commonest challenges and approaches for overcoming them, however maybe the overarching problem is the scope of the duty. Specifically, you wish to understand the advantages of DevSecOps, however you are worried your group lacks the sources and know-how to attain a totally realized DevSecOps atmosphere. The prospect could be overwhelming, which is why all through this put up we’ve characterised the method as a journey and advisable beginning with small steps you’ll be able to handle and construct on. As you achieve this, preserve this cyclical course of in thoughts:
- Assess your gaps.
- Establish fast wins.
- Empower champions and spotlight accomplishments.
- Measure outcomes, reassess gaps, and construct on fast wins.
- Consider and repeat.