Code-signing certificates are supposed to assist authenticate the id of software program publishers, and supply cryptographic assurance {that a} signed piece of software program has not been altered or tampered with. Each of those qualities make stolen or ill-gotten code-signing certificates engaging to cybercriminal teams, who prize their means so as to add stealth and longevity to malicious software program. This submit is a deep dive on “Megatraffer,” a veteran Russian hacker who has virtually cornered the underground marketplace for malware centered code-signing certificates since 2015.
A evaluation of Megatraffer’s posts on Russian crime boards reveals this consumer started peddling particular person stolen code-signing certs in 2015 on the Russian-language discussion board Exploit, and shortly expanded to promoting certificates for cryptographically signing purposes and recordsdata designed to run in Microsoft Home windows, Java, Adobe AIR, Mac and Microsoft Workplace.
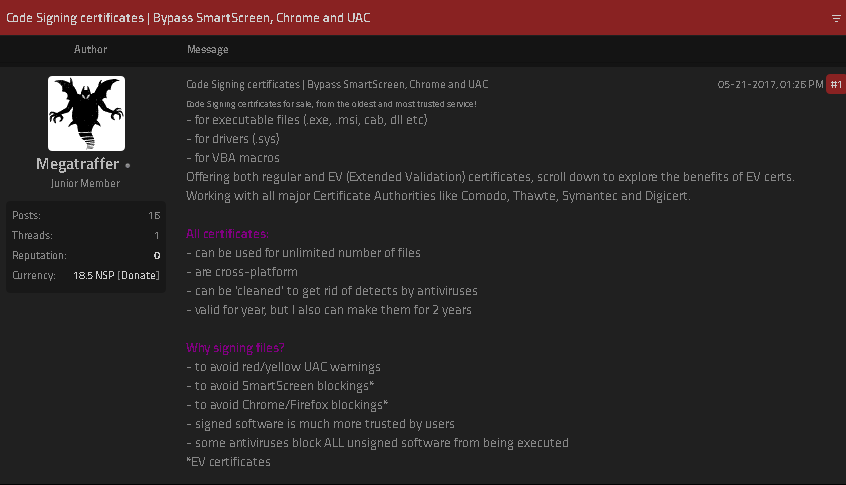
Megatraffer defined that malware purveyors want a certificates as a result of many antivirus merchandise will likely be way more taken with unsigned software program, and since signed recordsdata downloaded from the Web don’t are inclined to get blocked by security measures constructed into fashionable net browsers. Moreover, newer variations of Microsoft Home windows will complain with a brilliant yellow or purple alert message if customers attempt to set up a program that’s not signed.
“Why do I would like a certificates?” Megatraffer requested rhetorically of their Jan. 2016 gross sales thread on Exploit. “Antivirus software program trusts signed packages extra. For some forms of software program, a digital signature is necessary.”
On the time, Megatraffer was promoting distinctive code-signing certificates for $700 apiece, and charging greater than twice that quantity ($1,900) for an “prolonged validation” or EV code-signing cert, which is meant to solely include further id vetting of the certificates holder. In keeping with Megatraffer, EV certificates had been a “must-have” in the event you needed to signal malicious software program or {hardware} drivers that will reliably work in newer Home windows working methods.
A part of Megatraffer’s advert. Picture: Ke-la.com.
Megatraffer has continued to supply their code-signing providers throughout greater than a half-dozen different Russian-language cybercrime boards, principally within the type of sporadically out there EV and non-EV code-signing certificates from main distributors like Thawte and Comodo.
Extra not too long ago, it seems Megatraffer has been working with ransomware teams to assist enhance the stealth of their malware. Shortly after Russia invaded Ukraine in February 2022, somebody leaked a number of years of inside chat logs from the Conti ransomware gang, and people logs present Megatraffer was working with the group to assist code-sign their malware between July and October 2020.
WHO IS MEGATRAFFER?
In keeping with cyber intelligence agency Intel 471, Megatraffer has been energetic on greater than a half-dozen crime boards from September 2009 to the current day. And on most of those identities, Megatraffer has used the e-mail handle 774748@gmail.com. That very same e mail handle is also tied to 2 discussion board accounts for a consumer with the deal with “O.R.Z.”
Constella Intelligence, an organization that tracks uncovered databases, finds that 774748@gmail.com was utilized in reference to only a handful of passwords, however most regularly the password “featar24“. Pivoting off of that password reveals a handful of e mail addresses, together with akafitis@gmail.com.
Intel 471 reveals akafitis@gmail.com was used to register one other O.R.Z. consumer account — this one on Verified[.]ru in 2008. Previous to that, akafitis@gmail.com was used as the e-mail handle for the account “Fitis,” which was energetic on Exploit between September 2006 and Might 2007. Constella discovered the password “featar24” additionally was used along with the e-mail handle spampage@yandex.ru, which is tied to one more O.R.Z. account on Carder[.]su from 2008.
The e-mail handle akafitis@gmail.com was used to create a Livejournal weblog profile named Fitis that has a big bear as its avatar. In November 2009, Fitis wrote, “I’m the right legal. My fingerprints change past recognition each few days. Not less than my laptop computer is bound of it.”
Fitis’s Livejournal account. Picture: Archive.org.
Fitis’s real-life id was uncovered in 2010 after two of the most important sponsors of pharmaceutical spam went to warfare with one another, and enormous volumes of inside paperwork, emails and chat data seized from each spam empires had been leaked to this creator. That protracted and public battle shaped the backdrop of my 2014 guide — “Spam Nation: The Inside Story of Organized Cybercrime, from World Epidemic to Your Entrance Door.”
One of many leaked paperwork included a Microsoft Excel spreadsheet containing the actual names, addresses, telephone numbers, emails, road addresses and WebMoney addresses for dozens of high earners in Spamit — on the time probably the most profitable pharmaceutical spam associates program within the Russian hacking scene and one which employed most of the high Russian botmasters.
That doc reveals Fitis was one among Spamit’s most prolific recruiters, bringing greater than 75 associates to the Spamit program over a number of years previous to its implosion in 2010 (and incomes commissions on any future gross sales from all 75 associates).
The doc additionally says Fitis acquired paid utilizing a WebMoney account that was created when its proprietor introduced a sound Russian passport for a Konstantin Evgenievich Fetisov, born Nov. 16, 1982 and residing in Moscow. Russian motorcar data present two totally different automobiles are registered to this individual on the identical Moscow handle.
Essentially the most attention-grabbing area title registered to the e-mail handle spampage@yahoo.com, fittingly sufficient, is fitis[.]ru, which DomainTools.com says was registered in 2005 to a Konstantin E. Fetisov from Moscow.
The Wayback Machine at archive.org has a handful of principally clean pages listed for fitis[.]ru in its early years, however for a quick interval in 2007 it seems this web site was inadvertently exposing all of its file directories to the Web.
One of many uncovered recordsdata — Glavmed.html — is a basic invitation to the notorious Glavmed pharmacy associates program, a now-defunct scheme that paid tens of tens of millions of {dollars} to associates who marketed on-line tablet outlets primarily by hacking web sites and manipulating search engine outcomes. Glavmed was operated by the identical Russian cybercriminals who ran the Spamit program.

A Google translated advert circa 2007 recruiting for the pharmacy associates program Glavmed, which instructed candidates to contact the ICQ quantity utilized by Fitis, a.okay.a. MegaTraffer. Picture: Archive.org.
Archive.org reveals the fitis[.]ru webpage with the Glavmed invitation was constantly up to date with new invite codes. Of their message to would-be Glavmed associates, this system administrator requested candidates to contact them on the ICQ quantity 165540027, which Intel 471 discovered was an on the spot messenger handle beforehand utilized by Fitis on Exploit.
The uncovered recordsdata within the archived model of fitis[.]ru embrace supply code for malicious software program, lists of compromised web sites used for pharmacy spam, and a handful of what are apparently private recordsdata and photographs. Among the many photographs is a 2007 picture labeled merely “fitis.jpg,” which reveals a bespectacled, bearded younger man with a ponytail standing subsequent to what seems to be a newly-married couple at a marriage ceremony.
Mr. Fetisov didn’t reply to requests for remark.
As a veteran organizer of affiliate packages, Fitis didn’t waste a lot time constructing a brand new moneymaking collective after Spamit closed up store. New York Metropolis-based cyber intelligence agency Flashpoint discovered that Megatraffer’s ICQ was the contact quantity for Himba[.]ru, a cost-per-acquisition (CPA) program launched in 2012 that paid handsomely for accomplished utility kinds tied to quite a lot of monetary devices, together with shopper bank cards, insurance coverage insurance policies, and loans.
“Megatraffer’s entrenched presence on cybercrime boards strongly means that malicious means are used to supply no less than a portion of visitors delivered to HIMBA’s advertisers,” Flashpoint noticed in a menace report on the actor.
Intel 471 finds that Himba was an energetic associates program till round Might 2019, when it stopping paying its associates.

Fitis’s Himba associates program, circa February 2014. Picture: Archive.org.
Flashpoint notes that in September 2015, Megatraffer posted a job advert on Exploit in search of skilled coders to work on browser plugins, installers and “loaders” — mainly distant entry trojans (RATs) that set up communication between the attacker and a compromised system.
“The actor specified that he’s on the lookout for full-time, onsite assist both in his Moscow or Kiev places,” Flashpoint wrote.