
The favored KeePass password supervisor is susceptible to extracting the grasp password from the appliance’s reminiscence, permitting attackers who compromise a tool to retrieve the password even with the database is locked.
The difficulty was found by a safety researcher referred to as ‘vdohney,’ who printed a proof-of-concept device permitting attackers to extract the KeePass grasp password from reminiscence as a proof-of-concept (PoC).
Password managers enable customers to create distinctive passwords for each on-line account and retailer the credentials in an easy-to-search database, or password vault, so that you do not need to recollect every one. Nevertheless, to correctly safe this password vault, customers should keep in mind the one grasp password used to unlock it and entry saved credentials.
This grasp password encrypts the KeePass password database, stopping it from being opened or learn with out first getting into the password. Nevertheless, as soon as that grasp password is compromised, a risk actor can entry all of the credentials saved within the database.
Subsequently, for a password supervisor to be correctly secured, it’s important that customers guard the grasp password and never share it with anybody else.
A brand new KeePass vulnerability tracked as CVE-2023-3278 makes it doable to get better the KeePass grasp password, other than the primary one or two characters, in cleartext type, no matter whether or not the KeePass workspace is locked, or presumably, even when this system is closed.
“KeePass Grasp Password Dumper is a straightforward proof-of-concept device used to dump the grasp password from KeePass’s reminiscence. Other than the primary password character, it’s principally capable of get better the password in plaintext,” warns the safety researcher on the GitHub web page for the exploit device.
“No code execution on the goal system is required, only a reminiscence dump. It does not matter the place the reminiscence comes from – may be the course of dump, swap file (pagefile.sys), hibernation file (hiberfil.sys) or RAM dump of your complete system. It does not matter whether or not or not the workspace is locked.”
The flaw exists as a result of the software program makes use of a {custom} password entry field named “SecureTextBoxEx,” which leaves traces of every character the person varieties within the reminiscence.
“KeePass 2.X makes use of a custom-developed textual content field for password entry, SecureTextBoxEx. This textual content field shouldn’t be solely used for the grasp password entry, however elsewhere in KeePass as properly, like password edit packing containers (so the assault can be used to get better their contents),” explains vdohney.
The vulnerability impacts the newest model of KeePass, 2.53.1, and because the program is open-source, any mission forks are doubtless affected.
KeePass 1.X, KeePassXC, and Strongbox don’t look like impacted by CVE-2023-32784, in keeping with the developer of the password dumping device.
Additionally, whereas the PoC was examined on Home windows, the exploit must also work for Linux and macOS, with some modifications, as the issue is not particular to the OS however how KeePass handles person enter.

Supply: vdohney
Simple to take advantage of
Since reminiscence dumps should be retrieved for the KeePass grasp password to be recovered, the exploitation of CVE-2023-32784 requires bodily entry or malware an infection on the goal machine.
Nevertheless, information-stealing malware may rapidly verify if KeePass exists on a pc or is working, and if that’s the case, dump this system’s reminiscence and ship it and the KeePass database again to the attacker for offline retrieval of the cleartext password from the reminiscence dump.
BleepingComputer examined vdohney’s ‘keepass-password-dumper’ device by putting in KeePass on a take a look at system and creating a brand new database with the grasp password ‘password123,’ as proven beneath.
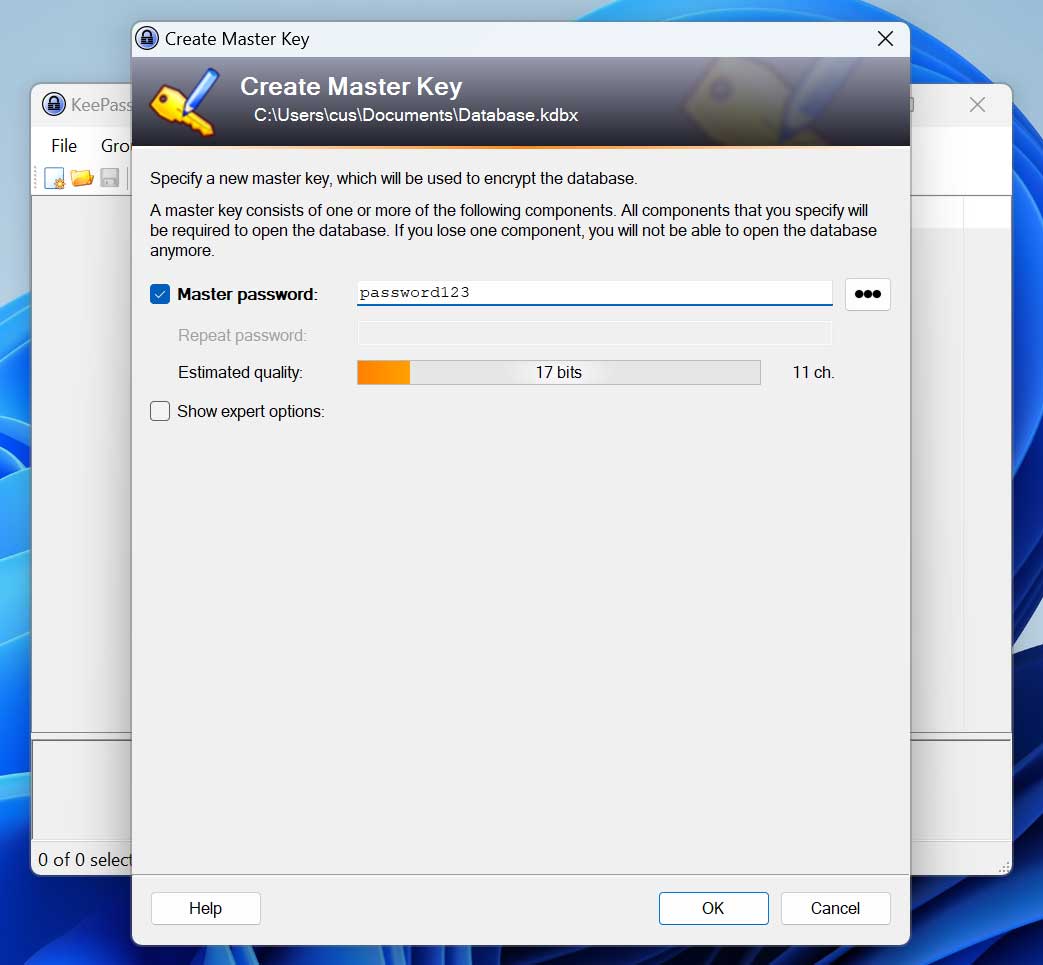
Supply: BleepingComputer
We then locked our KeePass workspace, which prevents entry to it except you enter the grasp password once more.
In our checks, you should use Course of Explorer to dump the reminiscence of the KeePass mission, but it surely requires a full reminiscence dump, and never a minidump, to work accurately. No elevated privileges are wanted to dump the processes’ reminiscence.
After compiling vdohney’s device utilizing Visible Studio, we executed it in opposition to our reminiscence dump, and it rapidly recovered most of our cleartext password, with simply the primary two letters lacking.
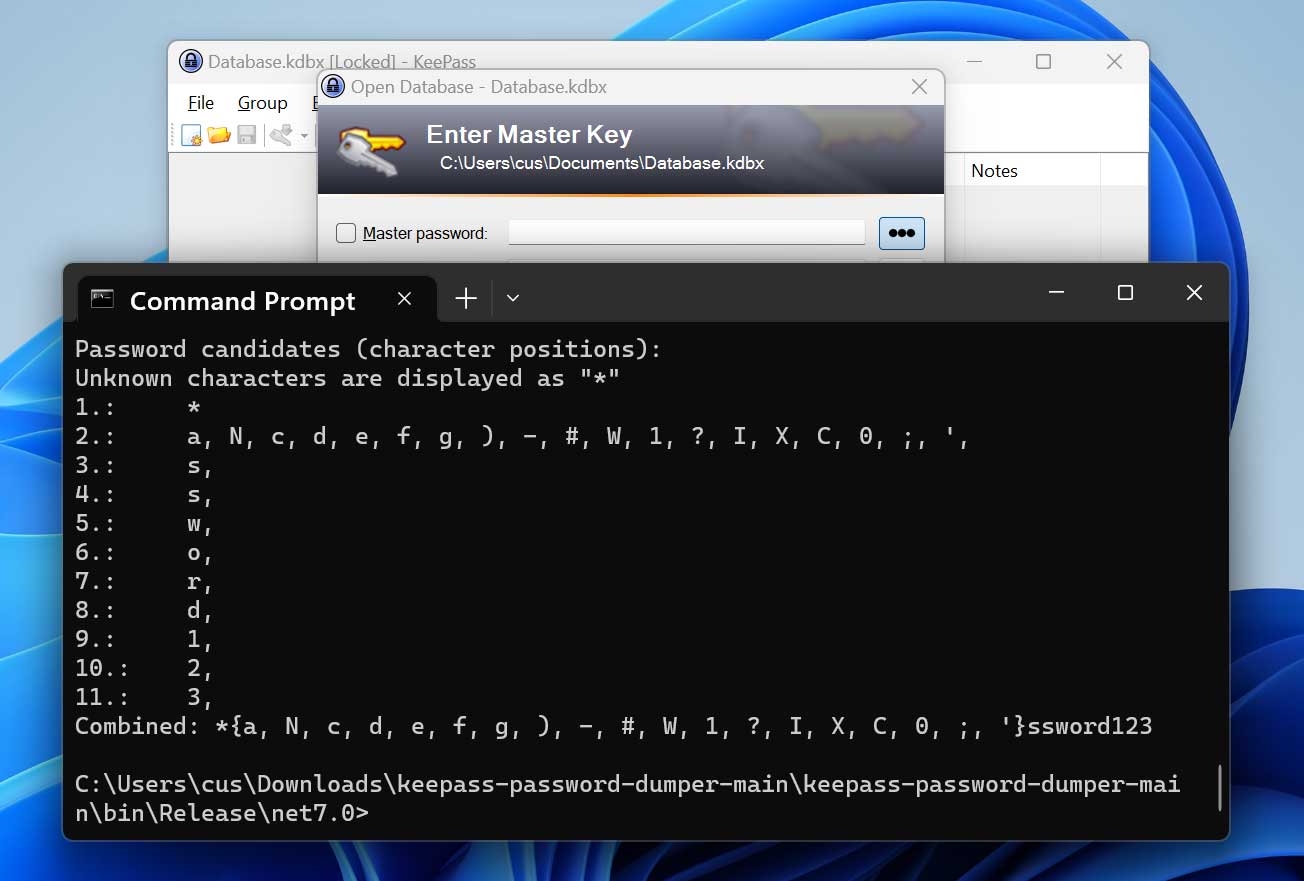
Supply: BleepingComputer
Whereas this isn’t the whole password, figuring out what characters are lacking could be pretty simple.
The researcher additionally warns that grasp passwords used prior to now can stay in reminiscence, to allow them to be retrieved even when KeePass is not working on the breached pc.
Repair coming quickly
The developer of KeePass, Dominik Reichl, obtained the bug report and promised to roll out a repair for CVE-2023-32784 on model 2.54, anticipated someday in July 2023.
Nevertheless, Reichl instructed BleepingComputer that KeePass model 2.54 is extra prone to be launched to customers in about two weeks, so it needs to be out by early June.
Based mostly on a dialogue the place Reichl developed his ideas on the safety flaw and the potential mitigation methods, two safety enhancements are talked about for the upcoming KeePass model:
- Carry out direct API requires getting/setting the textual content of the textual content field, avoiding the creation of managed strings in reminiscence that may leak secrets and techniques.
- Create dummy fragments containing random characters within the course of reminiscence that may have roughly the identical size because the person’s grasp password, obfuscating the true key.
KeePass 2.54 for Home windows can have each, whereas macOS and Linux variations will solely get the second enhancement.
The developer has launched a take a look at model with the brand new safety enhancements that mitigate the difficulty, so those that can settle for unstable conduct can supply it from right here.
The creator of the PoC has confirmed that he can not reproduce the assault with the 2 safety enhancements in place, so the repair seems to be efficient.
Even after the brand new model is launched, the grasp password should be saved in reminiscence information. The researcher warns that to be 100% secure that it isn’t lurking on the system, you would wish to delete your system’s swap and hibernation information, format your laborious drive utilizing the “overwrite information” mode to stop information restoration, and do a contemporary OS set up.
For many, although, restarting the pc, clearing your swap file and hibernation information, and never utilizing KeePass till the brand new model is launched are cheap security measures in the intervening time.
Even then, for the very best safety, be tremendous vigilant about not downloading packages from untrusted websites and watch out for phishing assaults that will infect your units, giving risk actors distant entry to your system and your KeePass database.

