There are many phish within the sea.
Tens of millions of bogus phishing emails land in hundreds of thousands of inboxes every day with one goal in thoughts—to tear off the recipient. Whether or not they’re out to crack your checking account, steal private info, or each, you’ll be able to learn to spot phishing emails and hold your self protected.
And a few of at the moment’s phishing emails are certainly getting more durable to identify.
They appear like they arrive from firms you already know and belief, like your financial institution, your bank card firm, or providers like Netflix, PayPal, and Amazon. And a few of them look convincing. The writing and the structure are crisp, and the general presentation appears skilled. But nonetheless, there’s nonetheless one thing off about them.
And there’s definitely one thing unsuitable with that electronic mail. It was written by a scammer. Phishing emails make use of a bait-and-hook tactic, the place an pressing or attractive message is the bait and malware or a hyperlink to a phony login web page is the hook.
As soon as the hook will get set, a number of issues would possibly occur. That phony login web page could steal account and private info. Or that malware would possibly set up keylogging software program that steals info, viruses that open a again door by way of which information can get hijacked, or ransomware that holds a tool and its information hostage till a payment is paid.
Once more, you’ll be able to sidestep these assaults if you know the way to identify them. There are indicators.
Let’s have a look at how prolific these assaults are, decide aside a couple of examples, after which break down the issues it’s best to search for.
<h2>Phishing assault statistics—the hundreds of thousands of makes an attempt made annually.
Within the U.S. alone, greater than 300,000 victims reported a phishing assault to the FBI in 2022. Phishing assaults topped the record of reported complaints, roughly six instances larger than the second high offender, private information breaches. The precise determine is undoubtedly greater, on condition that not all assaults get reported.
Taking a look at phishing assaults worldwide, one research means that greater than 255 million phishing makes an attempt had been made within the second half of 2022 alone. That marks a 61% improve over the earlier yr. One other research concluded that 1 in each 99 mails despatched contained a phishing assault.
But scammers received’t at all times forged such a large internet. Statistics level to an increase in focused spear phishing, the place the attacker goes after a particular individual. They’ll usually goal folks at companies who’ve the authority to switch funds or make funds. Different targets embrace individuals who have entry to delicate info like passwords, proprietary information, and account info.
As such, the value of those assaults can get expensive. In 2022, the FBI obtained 21,832 complaints from companies that mentioned they fell sufferer to a spear phishing assault. The adjusted losses had been over $2.7 billion—a median value of $123,671 per assault.
So whereas exacting phishing assault statistics stay considerably elusive, there’s no query that phishing assaults are prolific. And expensive.
<h2>What does a phishing assault appear to be?
Practically each phishing assault sends an pressing message. One designed to get you to behave.
Some examples …
- “You’ve received our money prize drawing! Ship us your banking info so we are able to deposit your winnings!”
- “You owe again taxes. Ship cost instantly utilizing this hyperlink or we’ll refer your case to regulation enforcement.”
- “We noticed what would possibly be uncommon exercise in your bank card. Observe this hyperlink to substantiate your account info.”
- “There was an unauthorized try to entry your streaming account. Click on right here to confirm your id.”
- “Your package deal was undeliverable. Click on the connected doc to offer supply directions.”
When set inside a pleasant design and paired some official-looking logos, it’s straightforward to see why loads of folks click on the hyperlink or attachment that comes with messages like these.
And that’s the tough factor with phishing assaults. Scammers have leveled up their sport lately. Their phishing emails can look convincing. Not way back, you can level to misspellings, awful grammar, poor design, and logos that seemed stretched or that used the unsuitable colours. Poorly executed phishing assaults like that also make their approach into the world. Nonetheless, it’s more and more frequent to see much more refined assaults at the moment. Assaults that appear as if a real message or discover.
Living proof:
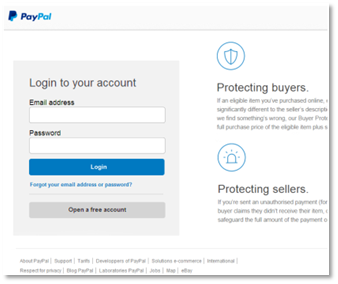
Say you bought an electronic mail that mentioned your PayPal account had a difficulty. Would you kind your account info right here in the event you discovered your self on this web page? In that case, you’ll have handed over your info to a scammer.
We took the screenshot above as a part of following a phishing assault to its finish—with out getting into any respectable data, after all. Actually, we entered a rubbish electronic mail tackle and password, and it nonetheless allow us to in. That’s as a result of the scammers had been after different info, as you’ll quickly see.
As we dug into the location extra deeply, it seemed fairly spot on. The design mirrored PayPal’s fashion, and the footer hyperlinks appeared official sufficient. But then we seemed extra intently.
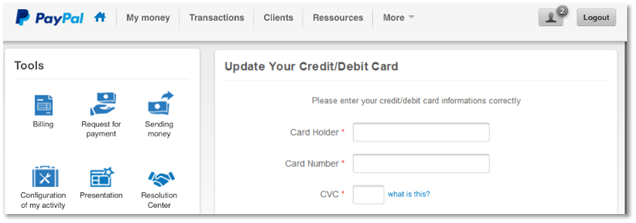
Word the refined errors, like “card informations” and “Configuration of my exercise.” Whereas firms make grammatical errors every now and then, recognizing them in an interface ought to hoist an enormous purple flag. Plus, the location asks for bank card info very early within the course of. All suspicious.
Right here’s the place the attackers actually obtained daring.
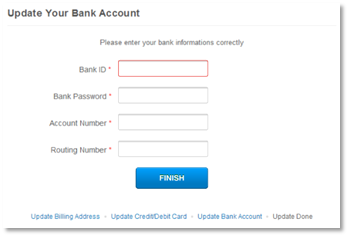
They ask for financial institution “informations,” which not solely consists of routing and account numbers, however they ask for the account password too. As mentioned, daring. And fully bogus.
Taken all collectively, the refined errors and the bald-faced seize for exacting account info clearly mark this as a rip-off.
Let’s take a couple of steps again, although. Who despatched the phishing electronic mail that directed us to this malicious website? None apart from “paypal at inc dot-com.”
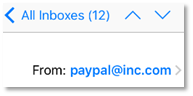
Clearly, that’s a phony electronic mail. And typical of a phishing assault the place an attacker shoehorns a well-recognized title into an unassociated electronic mail tackle, on this case “inc dot-com.” Attackers might also gin up phony addresses that mimic official addresses, like “paypalcustsv dot-com.” Something to trick you.
Likewise, the malicious website that the phishing electronic mail despatched us to used a spoofed tackle as properly. It had no official affiliation with PayPal in any respect—which is proof constructive of a phishing assault.
Word that firms solely ship emails from their official domains, simply as their websites solely use their official domains. A number of firms and organizations will record these official domains on their web sites to assist curb phishing assaults.
For instance, PayPal has a web page that clearly states the way it will and won’t contact you. At McAfee, we now have a whole web page devoted to stopping phishing assaults, which additionally lists the official electronic mail addresses we use.
Different examples of phishing assaults
Not each scammer is so refined, no less than in the way in which that they design their phishing emails. We are able to level to a couple phishing emails that posed as respectable communication from McAfee as examples.
There’s rather a lot occurring on this first electronic mail instance. The scammers attempt to mimic the McAfee model, but don’t pull it off. Nonetheless, they do a number of issues to attempt to act convincing.

Word the usage of pictures and the field shot of our software program, paired with a outstanding “act now” headline. It’s not the fashion of pictures we use. Not that folks would usually know this. Nonetheless, some may need a passing thought like, “Huh. That doesn’t actually appear to be what McAfee often sends me.”
Past that, there are a couple of capitalization errors, some misplaced punctuation, and the “order now” and “60% off” icons look moderately slapped on. Additionally word the little sprint of worry it throws in with a point out of “There are (42) viruses in your pc …”
Taken all collectively, somebody can readily spot that it is a rip-off with a more in-depth look.
This subsequent advert falls into the much less refined class. It’s virtually all textual content and goes heavy on the purple ink. As soon as once more, it hosts loads of capitalization errors, with a couple of gaffes in grammar as properly. In all, it doesn’t learn easily. Neither is it straightforward on the attention, as a correct electronic mail about your account ought to be.

What units this instance aside is the “commercial” disclaimer beneath, which tries to lend the assault some legitimacy. Additionally word the phony “unsubscribe” hyperlink, plus the (scratched out) mailing tackle and telephone, which all attempt to do the identical.
This final instance doesn’t get our font proper, and the trademark image is awkwardly positioned. The standard grammar and capitalization errors crop up once more, but this piece of phishing takes a barely totally different method. 
The scammers positioned slightly timer on the backside of the e-mail. That provides a level of shortage. They need you to assume that you’ve about half an hour earlier than you might be unable to register for defense. That’s bogus, after all.
Seeing any recurring themes? There are a couple of for certain. With these examples in thoughts, get into the main points—how one can spot phishing assaults and how one can keep away from them altogether.
Learn how to spot and forestall phishing assaults.
Simply as we noticed, some phishing assaults certainly seem fishy from the beginning. But generally it takes a little bit of time and a very important eye to identify.
And that’s what scammers rely on. They hope that you just’re transferring shortly or in any other case slightly preoccupied if you’re going by way of your electronic mail or messages. Distracted sufficient so that you just would possibly not pause to assume, is this message actually legit?
Top-of-the-line methods to beat scammers is to take a second to scrutinize that message whereas maintaining the next in thoughts …
They play in your feelings.
Worry. That’s an enormous one. Perhaps it’s an angry-sounding electronic mail from a authorities company saying that you just owe again taxes. Or possibly it’s one other from a member of the family asking for cash as a result of there’s an emergency. Both approach, scammers will lean closely on worry as a motivator.
When you obtain such a message, assume twice. Think about if it’s real. As an example, take into account that tax electronic mail instance. Within the U.S., the Inside Income Service (IRS) has particular tips as to how and when they’ll contact you. As a rule, they’ll doubtless contact you through bodily mail delivered by the U.S. Postal Service. (They received’t name or apply strain ways—solely scammers do this.) Likewise, different nations may have comparable requirements as properly.
They ask you to behave—NOW.
Scammers additionally love urgency. Phishing assaults start by stirring up your feelings and getting you to behave shortly. Scammers would possibly use threats or overly excitable language to create that sense of urgency, each of that are clear indicators of a possible rip-off.
Granted, respectable companies and organizations would possibly attain out to inform you of a late cost or attainable illicit exercise on one among your accounts. But they’ll take a much more skilled and even-handed tone than a scammer would. For instance, it’s extremely unlikely that your native electrical utility will angrily shut off your service in the event you don’t pay your overdue invoice instantly.
They need you to pay a sure approach.
Present playing cards, cryptocurrency, cash orders—these types of cost are one other signal that you just would possibly be taking a look at a phishing assault. Scammers choose these strategies of cost as a result of they’re troublesome to hint. Moreover, shoppers have little or no strategy to get better misplaced funds from these cost strategies.
Official companies and organizations received’t ask for funds in these types. When you get a message asking for cost in a type of types, you’ll be able to guess it’s a rip-off.
They use mismatched addresses.
Right here’s one other approach you’ll be able to spot a phishing assault. Take an in depth have a look at the addresses the message is utilizing. If it’s an electronic mail, have a look at the e-mail tackle. Perhaps the tackle doesn’t match the corporate or group in any respect. Or possibly it does considerably, but it provides a couple of letters or phrases to the title. This marks one more signal that you just would possibly have a phishing assault in your arms.
Likewise, if the message incorporates an internet hyperlink, intently study that as properly. If the title appears in any respect unfamiliar or altered from the way in which you’ve seen it earlier than, that would possibly additionally imply you’re taking a look at a phishing try.
Shield your self from phishing assaults
- Go on to the supply. Some phishing assaults can look convincing. A lot so that you just’ll wish to comply with up on them, like in case your financial institution stories irregular exercise in your account or a invoice seems to be overdue. In these instances, don’t click on on the hyperlink within the message. Go straight to the web site of the enterprise or group in query and entry your account from there. Likewise, when you’ve got questions, you’ll be able to at all times attain out to their customer support quantity or internet web page.
- Observe up with the sender. Preserve an eye fixed out for emails that could be a spear phishing assault. If an electronic mail that appears prefer it got here from a member of the family, good friend, or enterprise affiliate, comply with up with them to see in the event that they despatched it. Notably if asks for cash, incorporates a questionable attachment or hyperlink, or just doesn’t sound fairly like them. Textual content, telephone, or test in with them in individual. Don’t comply with up by replying to the e-mail, as it could have been compromised.
- Don’t obtain attachments. Some phishing assaults ship attachments full of malware just like the ransomware, viruses, and keyloggers we talked about earlier. Scammers could cross them off as an bill, a report, and even a suggestion for coupons. When you obtain a message with such an attachment, delete it. And most definitely don’t open it. Even in the event you obtain an electronic mail with an attachment from somebody you already know, comply with up with that individual. Notably in the event you weren’t anticipating an attachment from them. Scammers will usually hijack or spoof electronic mail accounts of on a regular basis folks to unfold malware.
- Hover over hyperlinks to confirm the URL. On computer systems and laptops, you’ll be able to hover your cursor over hyperlinks with out clicking on them to see the net tackle. If the URL appears suspicious in any of the methods we talked about simply above, delete the message, and don’t ever click on.
Shield your self from electronic mail assaults even additional
On-line safety software program can shield you from phishing assaults in a number of methods.
For starters, it presents internet safety that warns you when hyperlinks result in malicious web sites, akin to those utilized in phishing assaults. In the identical approach, on-line safety software program can warn you about malicious downloads and electronic mail attachments so that you just don’t find yourself with malware in your gadget. And, if the unlucky does occur, antivirus can block and take away malware.
On-line safety software program like ours also can tackle the foundation of the issue. Scammers should get your electronic mail tackle from someplace. Typically, they get it from on-line information brokers, websites that collect and promote private info to any purchaser—scammers included.
Knowledge brokers supply this info from public data and third events alike that they promote in bulk, offering scammers with huge mailing lists that may goal 1000’s of potential victims. You’ll be able to take away your private data from among the riskiest information dealer websites with our Private Knowledge Cleanup, which might decrease your publicity to scammers by maintaining your electronic mail tackle out of their arms.
In all, phishing emails have telltale indicators, some tougher to see than others. But you’ll be able to spot them when you already know what to search for and take the time to search for them. With these assaults so prevalent and on the rise, taking a look at your electronic mail with a important eye is a should at the moment.


