Cybersecurity researchers have uncovered weaknesses in a software program implementation of the Border Gateway Protocol (BGP) that could possibly be weaponized to attain a denial-of-service (DoS) situation on susceptible BGP friends.
The three vulnerabilities reside in model 8.4 of FRRouting, a preferred open supply web routing protocol suite for Linux and Unix platforms. It is at present utilized by a number of distributors like NVIDIA Cumulus, DENT, and SONiC, posing provide chain dangers.
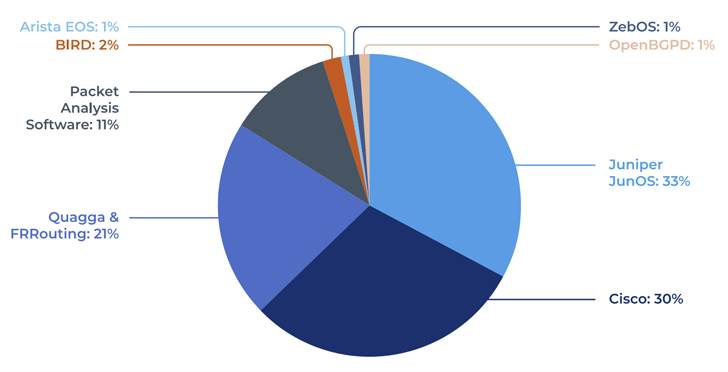
The invention is the results of an evaluation of seven totally different implementations of BGP carried out by Forescout Vedere Labs: FRRouting, BIRD, OpenBGPd, Mikrotik RouterOS, Juniper JunOS, Cisco IOS, and Arista EOS.
BGP is a gateway protocol that is designed to alternate routing and reachability data between autonomous programs. It is used to seek out probably the most environment friendly routes for delivering web visitors.
The listing of three flaws is as follows –
- CVE-2022-40302 (CVSS rating: 6.5) – Out-of-bounds learn when processing a malformed BGP OPEN message with an Prolonged Optionally available Parameters Size choice.
- CVE-2022-40318 (CVSS rating: 6.5) – Out-of-bounds learn when processing a malformed BGP OPEN message with an Prolonged Optionally available Parameters Size choice.
- CVE-2022-43681 (CVSS rating: 6.5) – Out-of-bounds learn when processing a malformed BGP OPEN message that abruptly ends with the choice size octet.
The problems “could possibly be exploited by attackers to attain a DoS situation on susceptible BGP friends, thus dropping all BGP classes and routing tables and rendering the peer unresponsive,” the corporate mentioned in a report shared with The Hacker Information.
“The DoS situation could also be extended indefinitely by repeatedly sending malformed packets. The primary root trigger is identical susceptible code sample copied into a number of features associated to totally different phases of parsing OPEN messages.”
A risk actor may spoof a legitimate IP tackle of a trusted BGP peer or exploit different flaws and misconfigurations to compromise a authentic peer after which problem a specially-crafted unsolicited BGP OPEN message.
That is achieved by making the most of the truth that “FRRouting begins to course of OPEN messages (e.g., decapsulating non-obligatory parameters) earlier than it will get an opportunity to confirm the BGP Identifier and ASN fields of the originating router.”
Study to Cease Ransomware with Actual-Time Safety
Be a part of our webinar and discover ways to cease ransomware assaults of their tracks with real-time MFA and repair account safety.
Forescout has additionally made obtainable an open supply instrument referred to as bgp_boofuzzer that permits organizations to check the safety of the BGP suites used internally in addition to discover new flaws in BGP implementations.
“Trendy BGP implementations nonetheless have low-hanging fruits that may be abused by attackers,” Forescout mentioned. “To mitigate the chance of susceptible BGP implementations, […] one of the best suggestion is to patch community infrastructure gadgets as usually as potential.”
The findings come weeks after ESET discovered that secondhand routers beforehand utilized in enterprise networking environments harbored delicate knowledge, together with company credentials, VPN particulars, cryptographic keys, and different very important buyer data.
“Within the improper arms, the information gleaned from the gadgets – together with buyer knowledge, router-to-router authentication keys, utility lists, and way more – is sufficient to launch a cyberattack,” the Slovak cybersecurity agency mentioned.