
A set of 38 Minecraft copycat video games on Google Play contaminated units with the Android adware ‘HiddenAds’ to stealthily load advertisements within the background to generate income for its operators.
Minecraft is a well-liked sandbox sport with 140 million month-to-month lively gamers, which quite a few sport publishers have tried to recreate.
The Minecraft-like video games hiding adware had been downloaded by roughly 35 million Android customers worldwide, primarily from america, Canada, South Korea, and Brazil.
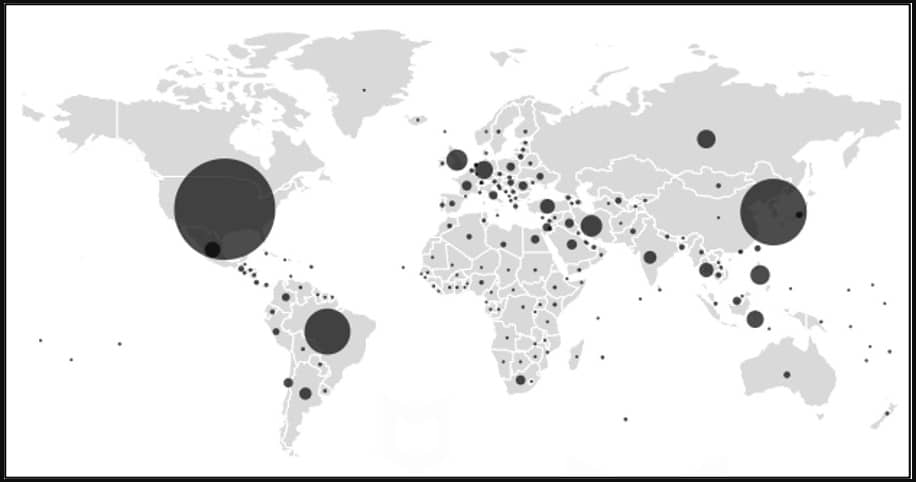
These customers did not discover the malicious adware exercise performed within the background, as they might play the video games as promised. Moreover, any attainable overheating, elevated community information, or battery consumption attributable to loading many advertisements could also be perceived as attributable to the sport.
The adware set was found by McAfee’s Cellular Analysis Crew, a member of the App Protection Alliance created to guard Google Play from all kinds of threats.
After reporting and all apps have been reported and subsequently faraway from the shop now, with essentially the most downloaded apps from this malicious set listed under:
- Block Field Grasp Diamond – 10 million downloads
- Craft Sword Mini Enjoyable – 5 million downloads
- Block Field Skyland Sword – 5 million downloads
- Craft Monster Loopy Sword – 5 million downloads
- Block Professional Forrest Diamond – 1 million downloads
- Block Recreation Skyland Forrest – 1 million downloads
- Block Rainbow Sword Dragon – 1 million downloads
- Craft Rainbow Mini Builder – 1 million downloads
- Block Forrest Tree Loopy – 1 million downloads
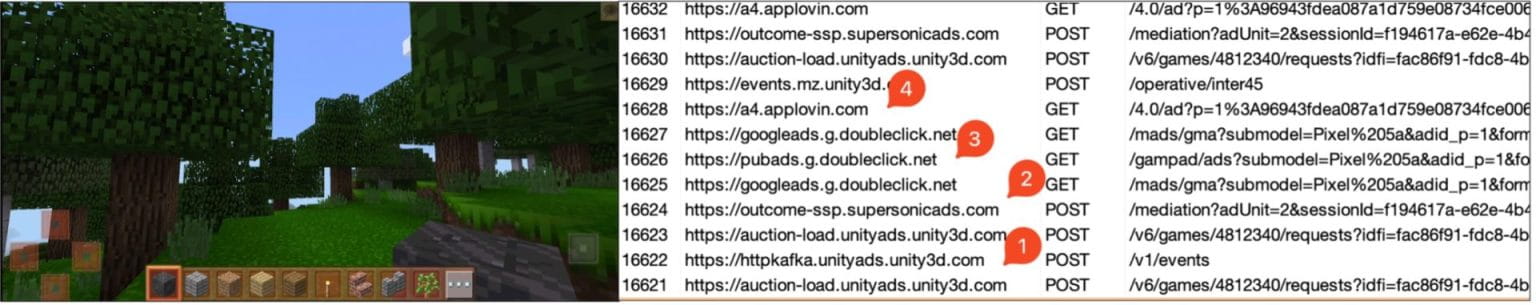
The commercials are loaded within the background as soon as the consumer launches the sport, however nothing is displayed on the sport display screen.
Community site visitors evaluation, although, exhibits the change of a number of questionable packets generated by advert libraries of Google, AppLovin, Unity, and Supersonic, amongst others.
McAfee studies that the preliminary community packets on a number of of the apps share related constructions, utilizing “3.txt” as the trail within the type of “https://(random).netlify.app/3.txt,” though the domains in every app are totally different.
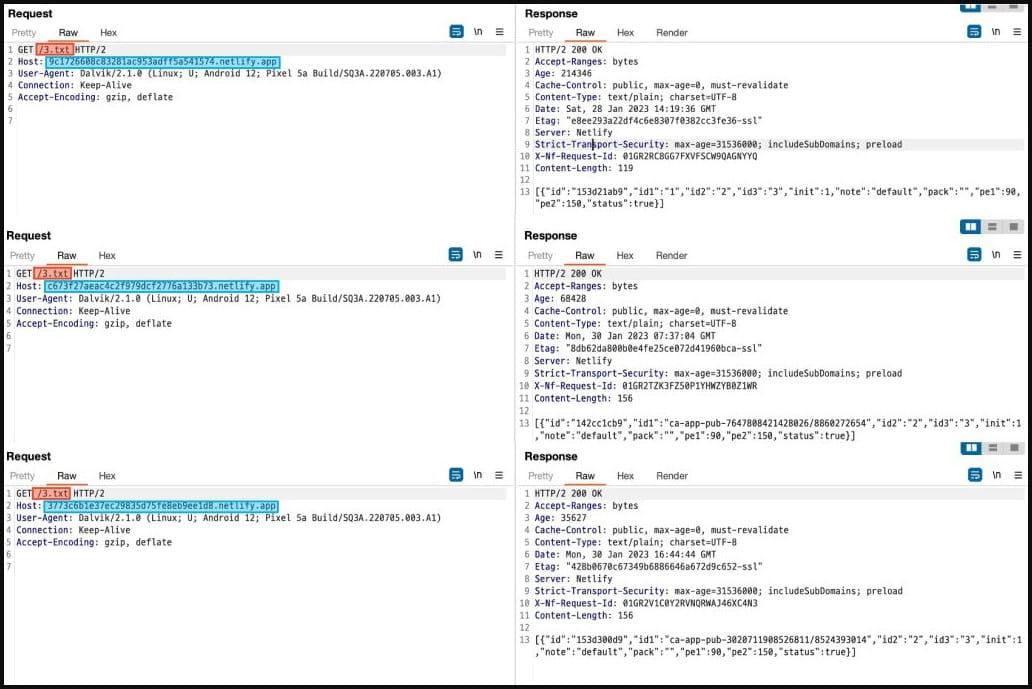
This, together with the same names of the video games, suggests a attainable connection between them, making it probably that the identical writer created the apps. Nonetheless, McAfee doesn’t explicitly point out any definitive hyperlinks.
Whereas adware apps aren’t thought-about significantly harmful for customers, it could actually scale back the efficiency of a cell gadget, elevate privateness considerations, and even doubtlessly create safety loopholes which may expose customers to nastier infections.
Android customers ought to verify McAfee’s report for a whole checklist of affected apps and manually take away them in the event that they haven’t been eliminated already.


