Distant Entry Trojans (RATs) have taken the third main place in ANY. RUN’s Q1 2023 report on essentially the most prevalent malware varieties, making it extremely possible that your group could face this risk.
Although LimeRAT won’t be essentially the most well-known RAT household, its versatility is what units it aside. Able to finishing up a broad spectrum of malicious actions, it excels not solely in information exfiltration, but additionally in creating DDoS botnets and facilitating crypto mining. Its compact footprint permits it to elude endpoint detection methods, making it a stealthy adversary. Curiously, LimeRAT shares similarities with njRAT, which ANY.RUN ranks because the third hottest malware household by way of uploads throughout Q1 2023.
ANY.RUN researchers have not too long ago carried out an in-depth evaluation of a LimeRAT pattern and efficiently extracted its configuration. On this article, we’ll present a short overview of that evaluation.
Collected artifacts
| SHA1 | 14836dd608efb4a0c552a4f370e5aafb340e2a5d |
| SHA256 | 6d08ed6acac230f41d9d6fe2a26245eeaf08c84bc7a66fddc764d82d6786d334 |
| MD5 | d36f15bef276fd447e91af6ee9e38b28 |
| SSDEEP | 3072:DDiv2GSyn88sH888wQ2wmVgMk/211h36vEcIyNTY4WZd/w1UwIwEoTqPMinXHx+i:XOayy |
IPv4:
| IOC | Description |
| 20[.]199.13.167:8080 | LimeRAT’s Command and Management server |
Domains:
| IOC | Description |
| https://pastebin[.]com/uncooked/sxNJt2ek | PasteBin utilized by LimeRAT to cover its authentic Command and Management server |
MITRE ATT&CK®
| Tactic | Method | Description |
| TA0005: Protection Evasion | T1027: Obfuscated Recordsdata or Info | Malware is utilizing obfuscator to strip its technique names, class names, and so forth. |
| TA0005: Protection Evasion | T1027: Obfuscated Recordsdata or Info | Malware makes use of Base64 algorithm to encode and decode information |
| TA0005: Protection Evasion | T1027: Obfuscated Recordsdata or Info | Malware makes use of AES algorithm to encrypt and decrypt information |
ANY.RUN is operating a limited-time supply, celebrating the seventh Cyberbirthdsay
ANY.RUN is an interactive cloud malware sandbox that may extract malware configs robotically for quite a few households, saving researchers hours of effort.
The service is celebrating its seventh anniversary and inviting all researchers to check out superior evaluation options usually reserved for professional plans, fully free till Might fifth. This contains configuring the execution setting with Home windows 8, 10, or 11.
If you happen to uncover that ANY.RUN enhances your malware evaluation workflow, they’re additionally providing a restricted promotion, out there till Might fifth: obtain 6 or 12 months of free utilization if you join a yearly or two-year subscription, respectively.
Breaking down LimeRAT’s decryption algorithm
We’ll share a condensed model of the article right here. For an entire walkthrough and the prolonged evaluation, head over to ANY. RUN’s weblog should you’re fascinated with studying extra concerning the workflow they employed.
For the reason that pattern beneath evaluation was written in .NET, researchers utilized DnSpy to look at the code. Instantly, it was apparent that obfuscation strategies had been being employed:
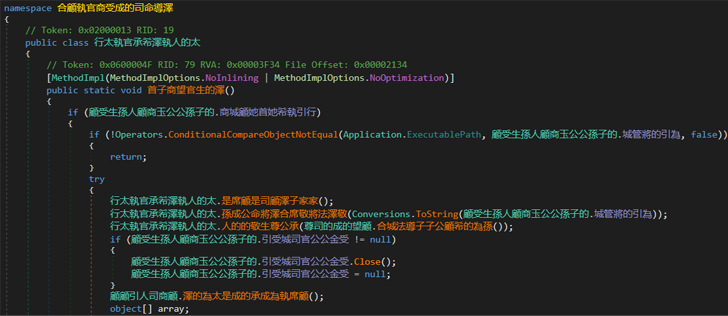 |
| Pattern overview in DnSpy; notice that use of obfuscation strategies |
Nearer examination of the code revealed a category resembling the malware configuration. Inside this class, was a area containing a string that was each base64 encoded and encrypted.
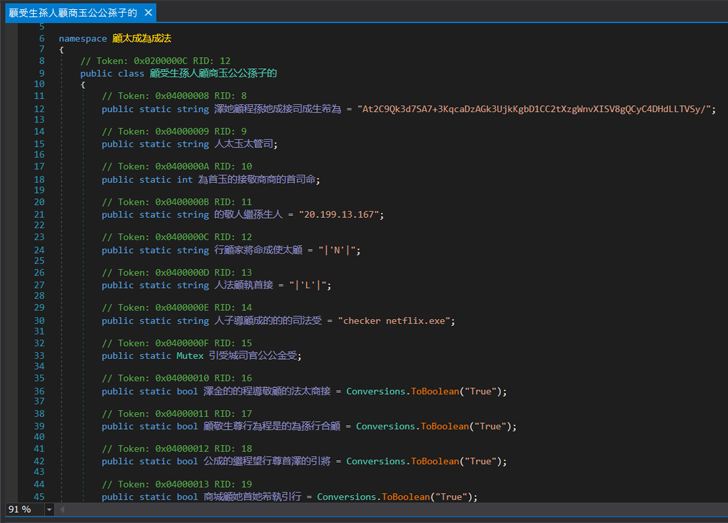 |
| Probably, malware configuration class |
Persevering with the code inspection, ANY.RUN researchers pinpointed a perform answerable for decrypting the string. By using the “Learn by” filter in DnSpy, they tracked down strategies the place the string was being learn, which led to a complete of two strategies. The primary technique proved unfruitful, however the second seemed fascinating:
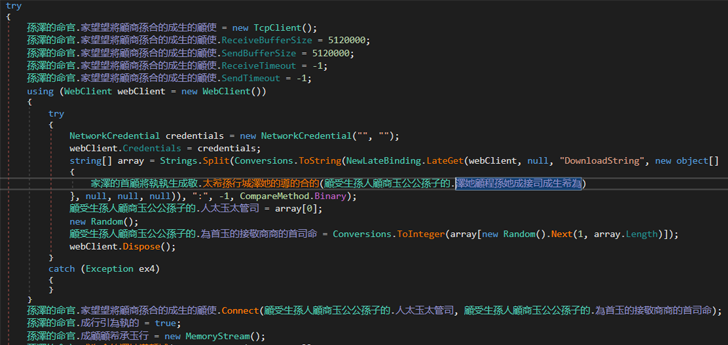 |
| The second x-ref is extra fascinating. Evidently it makes use of our string in WebClient.DownloadString technique |
This technique turned out to be answerable for decryption. By intently analyzing it, it was potential to reconstruct the method by which LimeRAT decrypts its configuration:
- Cases of the RijndaelManaged and MD5CryptoServiceProvider lessons are instantiated. As per MSDN, RijndaelManaged is an outdated implementation of the AES encryption algorithm (MITRE T1027), whereas MD5CryptoServiceProvider computes MD5 hashes.
- A 32-byte array, initialized with zeros, is generated to retailer the AES key.
- The secret is created by first calculating the MD5 hash of a definite string throughout the configuration class (in our evaluation, the string is “20[.]199.13.167”).
- The preliminary 15 bytes, adopted by the primary 16 bytes of the calculated hash, are copied into the beforehand established array. The ultimate ingredient of the array stays zero.
- The derived secret’s assigned to the important thing property of the RijndaelManaged occasion, whereas the Mode property is configured as CipherMode.ECB.
- In the end, the first string undergoes decoding through the Base64 algorithm and decryption utilizing the AES256-ECB algorithm.
Decrypting the string revealed a hyperlink to a PasteBin notice: https://pastebin[.]com/uncooked/sxNJt2ek. Inside this notice, was LimeRAT’s Command and Management (C2) server:
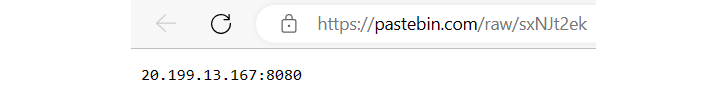 |
| LimeRATs C2 found with decrypted information |
To wrap up
We hope you discovered this temporary overview of our LimeRAT configuration decryption course of insightful. For a extra complete examination, head over to the full article on ANY.RUN’s weblog, to get further context on the steps and test the decryption course of utilizing CyberChef.
Additionally, keep in mind that ANY. RUN’s at the moment providing limited-time offers, that includes reductions on subscriptions and an expanded characteristic set free of charge plans, together with the power to configure execution environments with Home windows 8, 10, and 11 working methods. This supply expires on Might fifth.
This is a perfect alternative to check out ANY.RUN and decide if it streamlines your workflow, or to safe a subscription at an unbeatable value and reap the advantages of great time financial savings via static and behavioral evaluation.
To study extra about this supply, go to ANY.RUN plans.