We realized some outstanding new particulars this week concerning the current supply-chain assault on VoIP software program supplier 3CX. The prolonged, advanced intrusion has all of the makings of a cyberpunk spy novel: North Korean hackers utilizing legions of faux govt accounts on LinkedIn to lure individuals into opening malware disguised as a job provide; malware focusing on Mac and Linux customers working at protection and cryptocurrency corporations; and software program supply-chain assaults nested inside earlier provide chain assaults.
Researchers at ESET say this job provide from a phony HSBC recruiter on LinkedIn was North Korean malware masquerading as a PDF file.
In late March 2023, 3CX disclosed that its desktop purposes for each Home windows and macOS have been compromised with malicious code that gave attackers the power to obtain and run code on all machines the place the app was put in. 3CX says it has greater than 600,000 prospects and 12 million customers in a broad vary of industries, together with aerospace, healthcare and hospitality.
3CX employed incident response agency Mandiant, which launched a report on Wednesday that mentioned the compromise started in 2022 when a 3CX worker put in a malware-laced software program package deal distributed through an earlier software program provide chain compromise that started with a tampered installer for X_TRADER, a software program package deal supplied by Buying and selling Applied sciences.
“That is the primary time Mandiant has seen a software program provide chain assault result in one other software program provide chain assault,” reads the April 20 Mandiant report.
Mandiant discovered the earliest proof of compromise uncovered inside 3CX’s community was by the VPN utilizing the worker’s company credentials, two days after the worker’s private laptop was compromised.
“Ultimately, the risk actor was capable of compromise each the Home windows and macOS construct environments,” 3CX mentioned in an April 20 replace on their weblog.
Mandiant concluded that the 3CX assault was orchestrated by the North Korean state-sponsored hacking group generally known as Lazarus, a willpower that was independently reached earlier by researchers at Kaspersky Lab and Elastic Safety.
Mandiant discovered the compromised 3CX software program would obtain malware that sought out new directions by consulting encrypted icon recordsdata hosted on GitHub. The decrypted icon recordsdata revealed the placement of the malware’s management server, which was then queried for a 3rd stage of the malware compromise — a password stealing program dubbed ICONICSTEALER.
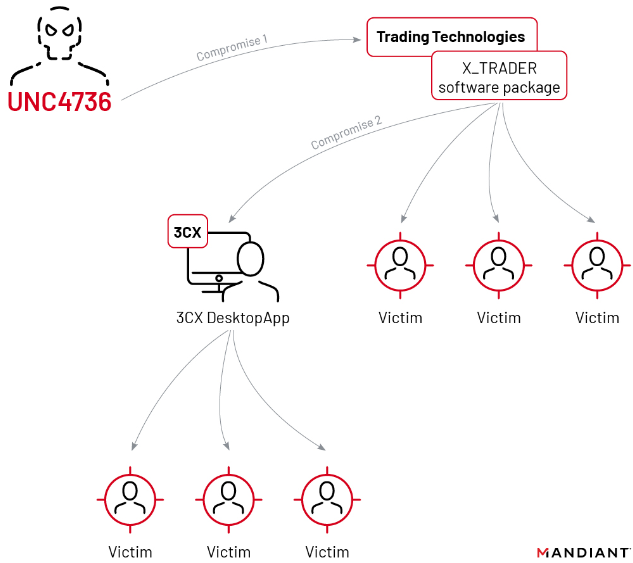
The double provide chain compromise that led to malware being pushed out to some 3CX prospects. Picture: Mandiant.
In the meantime, the safety agency ESET at present printed analysis displaying outstanding similarities between the malware used within the 3CX provide chain assault and Linux-based malware that was just lately deployed through faux job affords from phony govt profiles on LinkedIn. The researchers mentioned this was the primary time Lazarus had been noticed deploying malware geared toward Linux customers.
As reported in a current sequence final summer time right here, LinkedIn has been inundated this previous 12 months by faux govt profiles for individuals supposedly employed at a variety of know-how, protection, power and monetary corporations. In lots of circumstances, the phony profiles spoofed chief data safety officers at main firms, and a few attracted fairly a number of connections earlier than their accounts have been terminated.
Mandiant, Proofpoint and different specialists say Lazarus has lengthy used these bogus LinkedIn profiles to lure targets into opening a malware-laced doc that’s usually disguised as a job provide. This ongoing North Korean espionage marketing campaign utilizing LinkedIn was first documented in August 2020 by ClearSky Safety, which mentioned the Lazarus group operates dozens of researchers and intelligence personnel to keep up the marketing campaign globally.
Microsoft Corp., which owns LinkedIn, mentioned in September 2022 that it had detected a variety of social engineering campaigns utilizing a proliferation of phony LinkedIn accounts. Microsoft mentioned the accounts have been used to impersonate recruiters at know-how, protection and media corporations, and to entice individuals into opening a malicious file. Microsoft discovered the attackers usually disguised their malware as respectable open-source software program like Sumatra PDF and the SSH consumer Putty.
Microsoft attributed these assaults to North Korea’s Lazarus hacking group, though they’ve historically referred to this group as “ZINC“. That’s, till earlier this month, when Redmond utterly revamped the best way it names risk teams; Microsoft now references ZINC as “Diamond Sleet.”
The ESET researchers mentioned they discovered a brand new faux job lure tied to an ongoing Lazarus marketing campaign on LinkedIn designed to compromise Linux working programs. The malware was discovered inside a doc that provided an employment contract on the multinational financial institution HSBC.
“Just a few weeks in the past, a local Linux payload was discovered on VirusTotal with an HSBC-themed PDF lure,” wrote ESET researchers Peter Kalnai and Marc-Etienne M.Leveille. “This completes Lazarus’s means to focus on all main desktop working programs. On this case, we have been capable of reconstruct the total chain, from the ZIP file that delivers a faux HSBC job provide as a decoy, up till the ultimate payload.”
ESET mentioned the malicious PDF file used within the scheme appeared to have a file extension of “.pdf,” however that this was a ruse. ESET found that the dot within the filename wasn’t a standard interval however as a substitute a Unicode character (U+2024) representing a “chief dot,” which is usually utilized in tables of contents to attach part headings with the web page numbers on which these sections start.
“The usage of the chief dot within the filename was most likely an try to trick the file supervisor into treating the file as an executable as a substitute of a PDF,” the researchers continued. “This might trigger the file to run when double-clicked as a substitute of opening it with a PDF viewer.”
ESET mentioned anybody who opened the file would see a decoy PDF with a job provide from HSBC, however within the background the executable file would obtain extra malware payloads. The ESET staff additionally discovered the malware was capable of manipulate this system icon displayed by the malicious PDF, presumably as a result of fidgeting with the file extension may trigger the person’s system to show a clean icon for the malware lure.
Kim Zetter, a veteran Wired.com reporter and now impartial safety journalist, interviewed Mandiant researchers who mentioned they anticipate “many extra victims” will probably be found among the many prospects of Buying and selling Applied sciences and 3CX now that information of the compromised software program applications is public.
“Mandiant knowledgeable Buying and selling Applied sciences on April 11 that its X_Trader software program had been compromised, however the software program maker says it has not had time to research and confirm Mandiant’s assertions,” Zetter wrote in her Zero Day e-newsletter on Substack. For now, it stays unclear whether or not the compromised X_Trader software program was downloaded by individuals at different software program corporations.
If there’s a silver lining right here, the X_Trader software program had been decommissioned in April 2020 — two years earlier than the hackers allegedly embedded malware in it.
“The corporate hadn’t launched new variations of the software program since that point and had stopped offering help for the product, making it a less-than-ideal vector for the North Korean hackers to contaminate prospects,” Zetter wrote.

