
Risk teams are on the rise, and Google Cloud’s cyberdefense unit Mandiant is monitoring 3,500 of them, with 900 added final 12 months, together with 265 first recognized throughout Mandiant’s investigations in 2022.
Mandiant’s M-Traits 2023 report on the worldwide cybersecurity panorama discovered organizations confronted intrusions by superior teams together with government-sponsored entities from China and Russia, financially motivated menace teams and 335 uncategorized menace teams.
The most important proportion of teams — almost half of these adopted by Mandian — sought monetary achieve, in accordance with the report.
Soar to:
‘Dwell time’ plummets worldwide
Dwell time, the variety of days an adversary lurks in a goal community earlier than detection, dropped final 12 months. In response to the M-Traits report, the worldwide median dwell time was 16 days, the shortest such time for all reporting durations because the M-Traits report launched 14 years in the past, and down from 21 days in 2021.
Exterior notifications of incidents rise
The agency famous a rise in proactive notification efforts by safety companions. The report stated organizations within the Americas have been notified by an exterior entity in 55% of incidents, in comparison with 40% of incidents in 2021, the very best proportion of exterior notifications the Americas have seen over the previous six years.
Organizations in Europe, the Center East and Africa (EMEA) have been alerted of an intrusion by an exterior entity in 74% of investigations in 2022 in comparison with 62% in 2021. Within the Asia Pacific area, organizations have been alerted by exterior companions in 33% of investigations.
The examine, primarily based on Mandiant Consulting investigations of focused assault exercise between Jan. 1 and Dec. 31, 2022, discovered an rising variety of new malware households.
Ransomware assaults drop
The report confirms earlier analysis by TechRepublic noting drops in ransomware assaults: In 2022, 18% of Mandiant’s world investigations concerned ransomware in comparison with 23% in 2021. This represents the smallest proportion of Mandiant investigations associated to ransomware previous to 2020, in accordance with the corporate.
“Whereas we don’t have knowledge that implies there’s a single trigger for the slight drop in ransomware-related assaults that we noticed, there have been a number of shifts within the working surroundings which have seemingly contributed to those decrease figures,” stated Sandra Joyce, VP, Mandiant Intelligence at Google Cloud, in an announcement.
She stated disruption of ransomware assaults by authorities and regulation enforcement pressured actors to retool or develop new partnerships.
BEACON prevails amongst malware strains
The most typical malware household recognized by Mandiant in investigations final 12 months was BEACON, recognized in 15% of all intrusions investigated by Mandiant, which stated the malware has been deployed by teams aligned with China, Russia and Iran; monetary menace teams; and over 700 UNCs. Others have been SystemBC, Metasploit, Hivelocker, Qakbot, Alphv, LockBit and Basta (Determine A).
Determine A
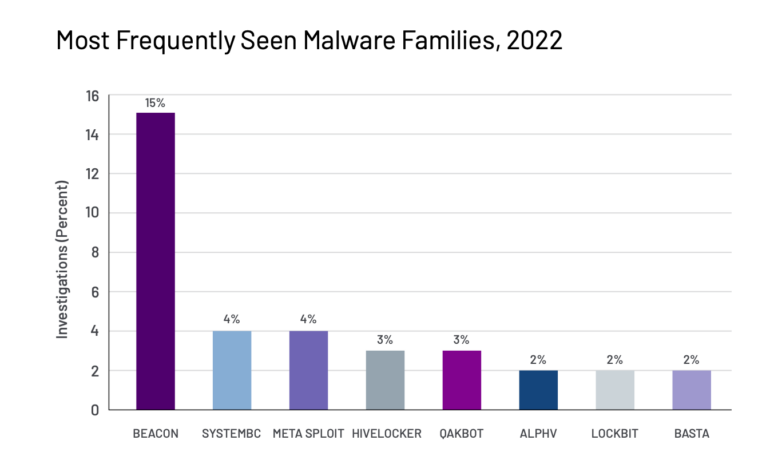
The report stated that of the 588 new malware households Mandiant tracked final 12 months:
- Thirty-four p.c have been backdoors.
- Fourteen p.c have been downloaders.
- Eleven p.c have been droppers.
- Seven p.c have been ransomware.
- 5 p.c have been launchers (Determine B).
Determine B

“Mandiant has investigated a number of intrusions carried out by newer adversaries which can be turning into more and more savvy and efficient,” stated Charles Carmakal, CTO Mandiant Consulting at Google Cloud, including that the actors use knowledge from underground cybercrime markets to run social engineering campaigns geared toward shifting laterally into enterprise networks.
Software program exploits lead assault vectors
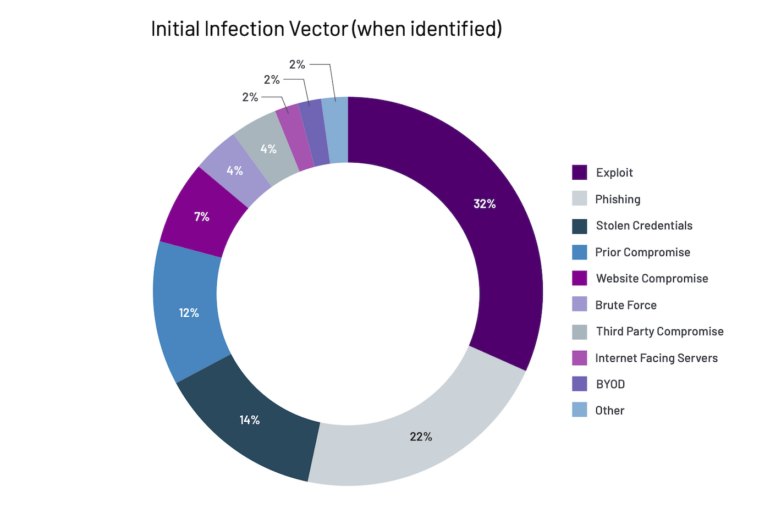
In response to the Mandiant report, for the third 12 months in a row, exploits, equivalent to SQL injection or cross-site scripting have been the most typical assault vector, utilized by 32% of attackers, down from 37% such intrusions in 2021. Phishing at second place, represented 22% of intrusions in comparison with 12% in 2021.
Mandiant reported that in its investigations it noticed proof that in assaults involving no less than one exploit in opposition to a vulnerability, they have been profitable in 36% of investigations in 2022 in comparison with 30% of investigations from 2021. It additionally experiences that perimeter gadgets uncovered to the wild of the web equivalent to firewalls, virtualization options and Digital Personal Community gadgets are fascinating targets for attackers.
Notable vulnerabilities have been Log4j1, which represented 16% of investigations, whereas the second and third most notable vulnerabilities recognized have been associated to F5 Huge-IP2 and VMware Workspace ONE Entry and Id Supervisor.
Poor digital hygiene fuels credential theft
Mandiant additionally reported a rise in credential theft and buying final 12 months, with a rise in incidents through which credentials have been stolen exterior of the group’s surroundings after which used in opposition to the group, probably as a consequence of reused passwords or use of private accounts on company gadgets.
Risk actors used stolen credentials in 14% of assaults final 12 months versus 9% in 2021 in investigations the place the preliminary an infection vector was recognized.
The agency additionally reported that 40% of intrusions in 2022 concerned knowledge exfiltration, a rise in using the approach from current years.
Mandiant investigations uncovered an elevated prevalence in each using widespread info stealer malware and credential buying in 2022 when in comparison with earlier years. In lots of instances, investigations recognized that credentials have been seemingly stolen exterior of the group’s surroundings after which used in opposition to the group, probably as a consequence of reused passwords or use of private accounts on company gadgets (Determine C).
Determine C
Phishing is 2nd commonest vector
Final 12 months, phishing represented 22% of intrusions the place the preliminary an infection vector was recognized making it the second most utilized vector, and a rise from 12% of intrusions in 2021.
Microsoft most attacked
Home windows malware was by far the most typical newly tracked and noticed exploit, with 92% of newly recognized malware households and 93% of noticed malware capable of run on Home windows, in accordance with the report. Different findings comply with:
- Malware households efficient on a number of working programs have been extra prevalent than malware designed to concentrate on just one working system.
- Malware efficient on just one working system was more than likely to focus on Home windows OS.
- Malware efficient on Linux decreased from 18% in 2021 to fifteen%
- Malware designed to use the VMWare created working system VMkernel was reported for the primary time.
On the final merchandise, Mandiant famous that whereas the amount is small, defenders ought to concentrate as a result of VMWare is broadly used.
“These kind of working programs don’t have vital functionality for Endpoint Detection and Response instrument monitoring. Because of this, monitoring and investigations into the platform may be difficult for defenders,” famous the report.
New cybercriminals use frequent strategies to nice impact
Amongst teams concentrating on main companies with high-profile assaults have been Lapsus, which Mandiant tracks as UNC3661, and one other Mandiant labeled UNC3944. Each uncharacterized teams, or UNCs, are noteworthy as a result of, whereas missing within the sophistication of nation-aligned actors, they have been nonetheless extremely efficient.
“These incidents underscored the menace posed to organizations by persistent adversaries keen to eschew the unstated guidelines of engagement,” stated Mandiant, which famous that the actors used knowledge garnered from underground cybercrime markets, intelligent social engineering schemes and even bribes. In addition they had no qualms about bullying and threatening their targets, in accordance with the agency.
UNC3661 began with South American targets, then went world, apparently bent on damaging reputations by stealing supply code and mental property.
“Their actions throughout intrusions spoke broadly to a need for notoriety, slightly than being optimized to extend earnings,” the agency stated, including that the group, after demanding IP as supply code, would conduct polls in Telegram chats to find out which group to focus on subsequent.
SEE: Telegram common bazaar for darkish net menace ecosystem
Mandiant reported that, in contrast to Lapsus, UNC3944, which appeared final Could, is a financially motivated menace cluster that positive aspects entry utilizing stolen credentials obtained from SMS phishing operations.
Of notice: Neither group depends on zero-day vulnerabilities, customized malware, or new instruments. “It is necessary organizations perceive the potential ramifications of this new, extra outspoken menace and alter each protections and expectations accordingly,” stated the report.


